Why does SIEM need to scale differently for cloud and hybrid environments?
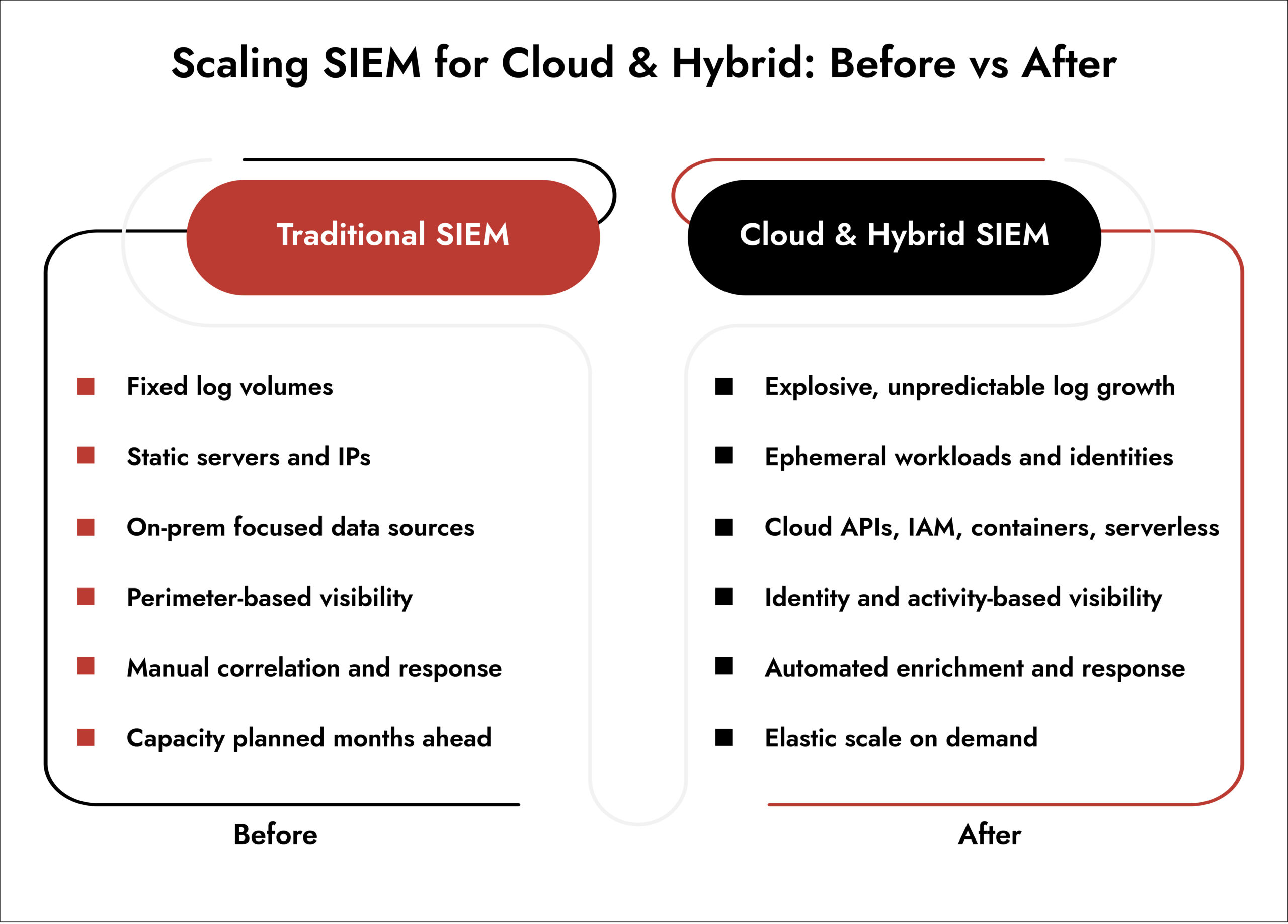
Cloud and hybrid environments introduce unpredictable log volume, distributed workloads, and fragmented visibility. Scaling cloud SIEM security in these environments is less about adding storage and more about handling data velocity, cloud-native logs, and cross-environment correlation. This shift forces changes in SIEM architecture, performance expectations, and how security teams monitor and respond to threats.
Your infrastructure moved to the cloud. Your security tools? Still stuck in the data center era.
Traditional SIEM wasn’t built for cloud environments. It was designed when servers lived in rows of metal racks, and log volumes were predictable. Now you’re dealing with ephemeral containers, auto-scaling workloads, and data spread across AWS, Azure, your private cloud, and that legacy system nobody wants to touch.
The old playbook doesn’t work anymore. Let’s talk about what actually changes when you scale SIEM for cloud and hybrid environments.
The Core Problem: Volume and Velocity
Here’s what happens when you move to the cloud. Your log volume explodes. Not gradually, but overnight.
Every API call generates logs. Every microservice interaction creates data. Your Kubernetes cluster spawns and kills containers constantly, each one chattering away. What used to be 500GB of logs per day becomes 5TB. Then 15TB when you spin up that new region.
Traditional SIEM security software chokes on this. The architecture wasn’t designed for it. You’re paying for storage you can barely search, running queries that time out, and missing threats because your system can’t keep up.
Cloud SIEM security takes a different approach. It separates storage from the computer, uses object storage instead of expensive disk arrays, and processes data in parallel across distributed systems. This isn’t just faster; it fundamentally changes what’s possible.
What One of the Main Security Challenges Actually Looks Like
Ask any security team what keeps them up at night in cloud environments, and visibility tops the list.
Your attack surface expanded without asking permission. Shadow IT deployed resources you don’t know about. DevOps teams spun up environments that bypass your monitoring. Someone configured an S3 bucket with public access, and you found out three months later during an audit.
The main security challenge isn’t technology, it’s context. You have logs from 47 different services, each with its own format, scattered across regions and accounts. Making sense of this requires cloud-based log management that understands cloud architectures natively.
You need to see:
- Who accessed what resource from where
- Which identity assumed which role and why
- What configuration changed and who approved it
- Where data moved between services and regions
Traditional log management treats cloud resources like servers with IP addresses. Cloud log management understands IAM policies, service meshes, and the permissions model that actually matters.
Why Hybrid Makes Everything More Complicated
Most organizations aren’t fully cloud. You’re hybrid, whether you planned it or not.
Your ERP runs on-premises. Your customer portal lives in AWS. Your analytics platform sits in Azure. Your security team needs to monitor all of it from one place, with consistent policies and unified threat detection.
This is where cloud and hybrid SIEM becomes critical. You can’t run separate systems for cloud and on-prem. Context gets lost. Attackers move laterally across environments, and you’re blind to it because your tools don’t talk to each other.
The benefits of a hybrid and multi cloud approach are real. You get flexibility, avoid vendor lock-in, and optimize costs by running workloads where they make sense. But security becomes more complex. You’re managing identity across multiple systems, enforcing policies in different control planes, and correlating events from sources that barely speak the same language.
A proper cloud and hybrid SIEM bridges this gap. It ingests logs from legacy syslog sources and modern cloud APIs. It normalizes data so a Windows login and an AWS AssumeRole event can be correlated. It applies the same detection rules whether the threat appears in your data center or your cloud environment.
Choose the Right SIEM with Confidence
Evaluate vendors using a comprehensive, expert-built checklist.
Identify must-have SIEM features for complete visibility and faster detection.
Compare capabilities to ensure scalability, automation, and integration.
Make informed decisions with NetWitness’ proven SIEM guidance.

SIEM Performance at Cloud Scale
Performance isn’t about speed anymore, it’s about relevance.
When you’re processing terabytes of logs daily, running every query against every record is pointless. You need intelligence built into the system. This means:
Smart indexing that understands your data structure and creates searchable metadata without storing everything twice.
Tiered storage where hot data lives in fast storage for real-time analysis, warm data sits in cheaper storage for investigations, and cold data archives to object storage for compliance.
Query optimization that pushes filtering down to the storage layer instead of pulling millions of records into memory first.
SIEM performance in the cloud is about architecture choices. Can your system scale horizontally when log volume spikes? Does it handle bursty workloads from auto-scaling applications? Will it maintain sub-second query response times when your dataset grows 10x?
These aren’t theoretical questions. Your security team needs answers now, not after the next incident when they’re trying to investigate under pressure.
Can SIEM Be Used for Cloud Security? (Yes, But Different)
SIEM in cybersecurity absolutely works for cloud security, but the implementation looks nothing like traditional deployments.
Cloud SIEM focuses on different data sources. Instead of firewall logs and IDS alerts, you’re ingesting:
- CloudTrail events showing who did what in AWS
- Azure Activity Logs tracking resource changes
- GCP Cloud Audit Logs capturing API calls
- Container runtime logs from Kubernetes
- Serverless function invocations from Lambda
The detection logic changes too. You’re not looking for port scans and exploit attempts. You’re hunting for:
- Privilege escalation through IAM policy changes
- Data exfiltration via misconfigured storage buckets
- Compromised credentials making unusual API calls
- Lateral movement between cloud services
SIEM monitoring in the cloud is about understanding cloud-specific attack patterns. Attackers don’t hack cloud environments the same way they breach networks. They abuse legitimate cloud features, exploit misconfigurations, and move through your infrastructure using your own tools and permissions.
How You Actually Manage Security in Hybrid Cloud
Managing security across hybrid environments requires a shift in thinking. You’re not protecting a perimeter anymore because there isn’t one.
Start with identity. Every access request, whether it’s hitting an on-prem database or a cloud API, needs to authenticate and authorize through a consistent system. Your SIEM needs visibility into this identity layer across all environments.
Standardize your logging. Define what events matter and ensure every environment sends them. This doesn’t mean forcing cloud services to log like servers, it means translating cloud logs into a common schema your security team can work with.
Automate response. When your SIEM detects a threat, it should trigger workflows that work across environments. Disable a compromised account in Active Directory and revoke its cloud access tokens. Block an IP address at your firewall and update your cloud security groups. Do it automatically, in seconds, not manually after a ticket gets escalated.
This is where siem security software earns its keep. The right system doesn’t just collect and alert, it orchestrates response across your entire infrastructure.
Cloud-Native SIEM and the Scalability Question
How does cloud-native SIEM improve scalability? By being cloud-native from the ground up.
Traditional SIEM was retrofitted for the cloud. Vendors took their on-prem product, wrapped it in containers, and called it cloud-ready. That’s not the same thing.
True cloud-native SIEM uses:
- Object storage for unlimited retention at low cost
- Serverless processing that scales automatically with load
- Distributed search that parallelize queries across hundreds of nodes
- API-first architecture that integrates with cloud services natively
This architecture eliminates the scaling bottlenecks that plague traditional systems. You don’t provision capacity, you consume it. Logs spike during a traffic surge? The system absorbs it. You need to search six months of data? Processing scales up automatically.
The cost model changes too. Instead of paying for peak capacity that sits idle most of the time, you pay for what you use. Storage costs drop 90%. Processing becomes variable based on actual workload.
Automation: The Only Way Forward
What role does automation play in scaling SIEM? Everything.
You cannot scale security operations linearly with your infrastructure. If your cloud footprint grows 5x, you can’t hire 5x more analysts. You need automation to multiply your team’s effectiveness.
Automation in cloud SIEM means:
- Enriching alerts with context automatically so analysts don’t hunt for it
- Triaging incidents based on actual risk, not just severity scores
- Orchestrating response playbooks that execute without human intervention
- Learning from analyst decisions to improve detection over time
The boring, repetitive work gets automated. Your team focuses on actual threats, not false positives that could have been filtered automatically.
How NetWitness Approaches SIEM in Cloud and Hybrid Environments
NetWitness is designed to support organizations operating across complex hybrid environments, where on-premises systems and cloud workloads must be monitored together without losing context. Rather than treating cloud as a separate security domain, NetWitness extends a unified SIEM model across environments, enabling consistent log ingestion, normalization, and correlation across on-prem, private cloud, and public cloud SIEM deployments.
This approach helps security teams maintain centralized visibility and investigation workflows as infrastructure evolves. By integrating cloud service logs, identity activity, and traditional enterprise telemetry into a single analytics and investigation layer, NetWitness enables SOC teams to detect and respond to threats that move across environments, without fragmenting tools or processes.
Making the Transition
Moving to cloud and hybrid SIEM isn’t a lift-and-shift project. It’s a rethinking of how security monitoring works at scale.
Start by understanding your data. What logs matter? Where are they? How much volume are you really dealing with? Most organizations guess wrong on this.
Choose architecture over features. The fanciest detection rules won’t help if your system can’t ingest the data or query it fast enough to matter.
Plan for growth. Your log volume next year will be higher than today. Your SIEM should scale with your business, not become a constraint on it.
Cloud changes everything about how we build and run applications. Security has to change too. The question isn’t whether to scale your SIEM for cloud and hybrid environments. It’s whether you’ll do it before or after the next breach forces your hand.
Frequently Asked Questions
1. What is one of the main security challenges in cloud and hybrid environments?
Lack of visibility and context. Cloud and hybrid environments generate massive volumes of fragmented logs across accounts, regions, and services. The challenge isn’t collecting data, it’s correlating identity activity, configuration changes, and workload behavior fast enough to spot real threats before damage is done.
2. What are the benefits of a hybrid and multi-cloud approach?
Hybrid and multi-cloud models give organizations flexibility, resilience, and cost optimization. Teams can run workloads where they make the most sense, avoid vendor lock-in, and scale faster. The tradeoff is security complexity, which requires unified monitoring, consistent policies, and cross-environment correlation to manage risk effectively.
3. Can SIEM be used for cloud security?
Yes, but it must be implemented differently. Cloud SIEM focuses on cloud-native telemetry like API activity, identity usage, configuration changes, and service-to-service behavior. Effective cloud SIEM security looks for abuse of permissions and misconfigurations, not just traditional network attacks.
4. How do you manage security in a hybrid cloud environment?
You manage hybrid security by centralizing visibility while respecting architectural differences. That means standardizing logging, monitoring identity across environments, and using SIEM monitoring to correlate events from on-prem systems and cloud platforms in one investigation workflow. Automation is critical to respond consistently across both worlds.
5. How does cloud-native SIEM improve scalability?
Cloud-native SIEM improves scalability through distributed processing, object storage, and elastic compute. It scales automatically with log volume, handles bursty workloads from auto-scaling applications, and avoids the capacity limits that slow down traditional SIEM performance as data grows.
Top SIEM Use Case for Threat Detection
-Uncover hidden threats with unified log and event analysis.
-Centralize security monitoring across endpoints, network, and cloud.
-Speed up detection and streamline incident response with correlated alerts.
-Empower your SOC with actionable insights and compliance-ready reporting






