What Is Situational Awareness in Cybersecurity?
The term “Cyber Security Situational Awareness” is an organization’s ability to have an ongoing understanding of the various types of cyber threats and the potential effects of these threats on the organization’s network, endpoints, cloud environments, and identities at all times. This ongoing understanding is built from a combination of visibility, context and situational intelligence. When security teams see their entire environment, they can find threats faster. They can also understand the incident better and respond to the attack before it causes more damage.
Introduction
In most incidents of cybersecurity intrusion, there are often warning signs. Most enterprise breaches do include warning signs that were visible prior to detection of the incident. In a situation where organizations do not have a good cyber situational awareness, the warning signs will likely remain hidden (due to ‘noise’ or ”siloization‘) and will eventually escalate from a minor anomaly to a major incident over time.
Cyber situational awareness has evolved and is now used in areas beyond the military. In a cyberspace context, cyber situational awareness enables organizations to respond effectively to cybersecurity incident responses. If you do not know what is happening on your networks, endpoints, and cloud environments, you cannot respond properly. Your responses will be based on guesses instead of real facts.
What Is Situational Awareness in Cybersecurity?
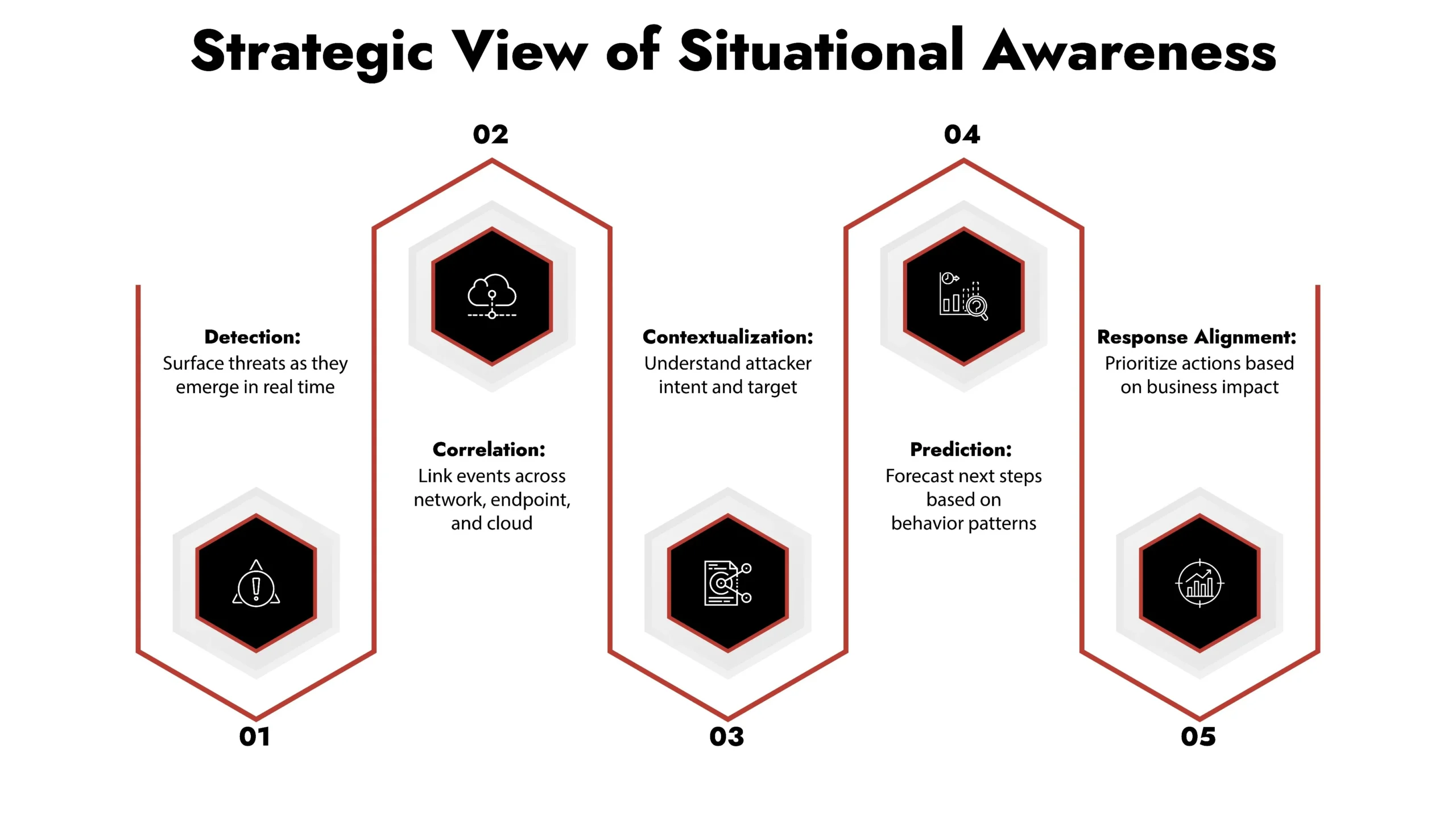
Situational awareness is having the ability to assess incoming cyber threats on a continuous basis and providing information about the context of those threats at the point they are detected as well as the expected outcomes of the activity that is ongoing or about to happen in the very near future.
Situational awareness can be thought of as measuring activity similar to a radar system that can not only measure the direction, speed, and intent of a moving object but also communicate this data back to the monitoring entity within a business. The same concept goes for cybersecurity situational awareness, where the element of vision and situational intelligence allows cyber security teams to utilize this information for a more accurate response as opposed to just responding with urgency.
At the heart of cyber situational awareness is:
- Developing a baseline understanding of normal user behavior and usage patterns across all networks
- Understanding how the business’s critical assets communicate with each other
- Understanding who has access to and is using privileges within the organization
- Monitoring attack techniques and patterns of behavior as they occur and developing mitigation strategies based on that information
- Assessing and documenting the acceptable level of risk as a result of an incident getting worse because the incident response was not handled in a timely manner.
With this level of insight, the Incident Response Process shifts from being totally reactive and containment-based to becoming more controlled.
Why Situational Awareness Comes Before Containment
Containment is not simply about stopping activity. It is about regaining control of the environment while minimizing risk to operations and evidence. Without cyber security situational awareness, containment actions are often misdirected or incomplete.
Common outcomes include isolating the wrong systems, overlooking lateral movement, or failing to recognize diversionary tactics such as ransomware used to mask data exfiltration.
With effective situational awareness tools, response teams can:
- Isolate compromised systems without unnecessary disruption
- Detect lateral movement across hybrid environments
- Confirm which identities and credentials are affected
- Identify patient zero and map the attack sequence
- Inform forensic analysis and response strategy
The result is a structured, deliberate response rather than an improvised one.
Core Components of Cyber Situational Awareness
1. Full Visibility Across All Domains
You can’t defend what you cannot see. True situational awareness requires telemetry from:
- Network traffic (north-south and east-west).
- Endpoints (EDR or native OS logs).
- Cloud workloads and containers.
- Authentication and identity data.
- Threat intelligence feeds.
The objective is to reduce blind spots caused by encryption, unmanaged devices, or fragmented tooling.
2. Behavioral Analytics and Anomaly Detection
Indicators of compromise (IOCs) are often detected late in the attack lifecycle. Behavioral analytics surface earlier signals by identifying deviations from established patterns.
Examples include:
- Atypical login behavior
- Unexpected privilege changes
- Unusual data movement
- Abnormal protocol usage
When correlated through situational awareness tools, these signals provide early and reliable detection.
3. Threat Intelligence Integration
Internal telemetry gains value when enriched with external context. Situational intelligence helps security teams understand who is targeting their organization, which techniques are being used, and how similar attacks have progressed elsewhere.
This context enables prioritization based on relevance and risk, not volume.
4. Asset and Identity Context
Not all systems carry equal risk. Cyber situational awareness requires understanding asset criticality and identity privileges to assess impact accurately.
Security teams must know:
- Which systems are business critical
- Who can access them
- How attackers might move toward them.
Rapid, Expert Response with NetWitness® Incident Response Services
-Accelerate threat containment with experienced IR specialists.
-Investigate effectively using advanced forensics and analytics.
-Minimize business impact with fast, guided remediation.

Situational Awareness in Action
Consider a spike in DNS traffic from an internal host to an unfamiliar domain. Without cyber security situational awareness, the activity may be dismissed or addressed too late.
With it:
- Network data links the destination to known command-and-control infrastructure
- Endpoint logs show suspicious scripting activity
- Identity data confirms elevated access
- Asset context highlights proximity to sensitive systems
The response team isolates the host, resets credentials, and captures forensic evidence quickly, reducing exposure time and limiting impact.

Where Containment Ends, Expulsion and Remediation Begins
Containment is a strategic phase of incident response. It requires informed decision-making under pressure, often with incomplete information.
Here, cyber situational awareness guides judgment by clarifying:
- The attacker’s level of access
- The scope of compromise
- The risks associated with immediate action
Effective containment preserves visibility, stabilizes operations, and prepares the environment for eradication. Once the attacker is fully expelled, remediation can proceed, including vulnerability closure, credential resets, detection updates, and system restoration.
How NetWitness Supports Incident Response with Situational Awareness
NetWitness Incident Response is designed to strengthen cyber security situational awareness across the entire incident lifecycle. By unifying network, endpoint, cloud, and identity telemetry, it provides responders with consistent context and evidence.
Key capabilities include:
- Integrated NDR, EDR, and UEBA telemetry
- Behavioral analytics for early threat detection
- Session reconstruction for detailed investigation
- Expert IR services for guided or managed response
- Advanced threat hunting and forensic support
These capabilities enable faster containment and more confident remediation through mature situational awareness tools. 
Conclusion
Situational awareness is foundational to effective incident response. Without cyber situational awareness, containment is speculative. With it, organizations respond with clarity, control, and intent.
That distinction determines whether an incident becomes a learning opportunity or a prolonged disruption.
Frequently Asked Questions
1. Can situational awareness be fully automated?
No. Automation improves speed and correlation, but analyst judgment remains essential.
2. Why do enterprises struggle with situational awareness despite multiple tools?
Because tools operate in silos. Without integrated situational awareness tools, context is lost.
3. How does NetWitness improve containment speed?
By consolidating visibility, applying behavioral analytics, and supporting teams with expert IR services.
4. How does situational awareness reduce dwell time?
Cyber security situational awareness enables earlier detection and accurate scoping, significantly reducing attacker dwell time.
5. How should containment effectiveness be measured?
Metrics include time-to-contain, number of affected systems, lateral movement extent, and whether containment occurred before exfiltration or disruption.
Factors to Consider While Investing in an Incident Response Retainer
Evaluate incident response readiness and expert coverage before incidents occur.
Understand cost vs. risk reduction to optimize security budgets.
Align retainer services with detection, investigation, and response needs.
Balance internal capabilities with external expertise for faster recovery.