Explaining Network Forensics
Analyzing the flow of data over a network helps security teams determine how a system was attacked and how attackers moved laterally through the system. Network forensics helps reconstruct a time-line of when events occurred during multi-stage attacks; identifies which systems were involved in the attack; determines what kind of attacker activity occurred when systems communicate; detects advanced threats; supports incident response; meets compliance requirements; and generates useful threat intelligence that could be used by organizations to protect their networks from other attacks, regardless of whether they are located on a server or in a cloud environment.
Introduction
Most security breaches leave behind incomplete stories. Endpoint protection may catch malware on a workstation, but it rarely explains how attackers moved between systems. Firewall logs show blocked connections, yet they often miss the quiet activity that defines advanced attacks.
Network forensics in cyber security fills this gap. It examines conversations between systems to reveal how attacks unfold across the network. Instead of isolated alerts, security teams see the full sequence of events.
As attackers rely on multi-stage techniques, network traffic forensics has become critical. Rather than focusing on single devices, it tracks communication flows and data movement. This gives security teams the context they need to investigate incidents, understand attacker behavior, and reduce future risk.
What is Network Forensics?
Network forensics involves the collection, analysis, and interpretation of digital communications to explore security events and system activity. It emphasizes the movement of data among computers, servers, and interconnected devices.
Conventional computer forensics examines single systems. Network traffic forensics adopts a wider perspective. It examines how systems engage throughout the whole ecosystem. When attackers infiltrate several systems, obtain data, or sustain prolonged access, they generate evidence in network traffic that analysts can scrutinize.
This area facilitates real-time observation as well as post-incident analysis. Security teams employ network forensics analysis to identify ongoing threats, comprehend attack techniques, and gather evidence that could be utilized in legal actions. This adaptability makes it an essential element of contemporary cybersecurity operations. 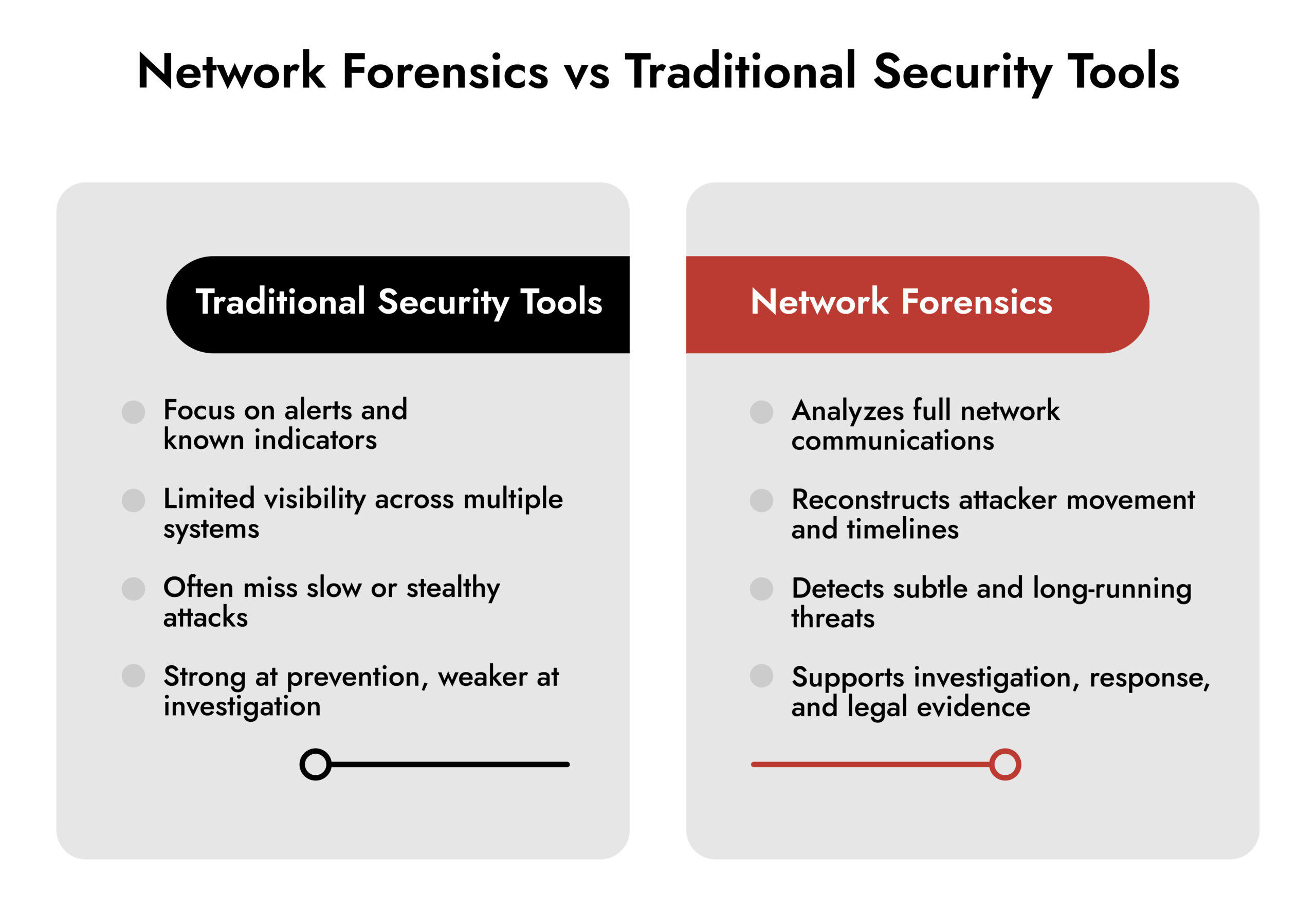
Role of Network Forensics in Digital Investigations
The function of network forensics in cyber security investigative work encompasses various areas within information security and incident management. Network forensics provides support in the areas of threat hunting, malware analysis, compliance auditing, incident response, and threat detection.
Although each use case will utilize a unique set of techniques and network forensics tools to analyze network communications to determine what has occurred.
How Network Forensics Analysis Works
Network forensics analysis follows a structured process designed to ensure accuracy and legal integrity. Most investigations move through the following stages.
Identification
The investigation scope is defined. Teams determine which network segments matter and select appropriate network forensics tools based on the incident.
Preservation
Critical network data is protected from loss or tampering. Investigators create valid copies of packet captures, flow records, and logs while maintaining a chain of custody.
Collection
Data is gathered from routers, switches, firewalls, and monitoring platforms. Every source, method, and timestamp is documented to preserve evidence of quality.
Examination
Captured data is reviewed using PCAP analysis and monitoring tools. Investigators look for unusual traffic patterns, suspicious communications, and indicators of compromise.
Analysis
Findings are connected to a clear timeline. This network forensics analysis explains how the attack occurred, how it spread, and what impact it had.
Presentation
Results are documented in clear reports for both technical and non-technical audiences. These include evidence of summaries, attack timelines, and security recommendations.
Response
Insights are used to contain threats, fix weaknesses, and prevent similar incidents. This step ensures investigations lead to real security improvements.
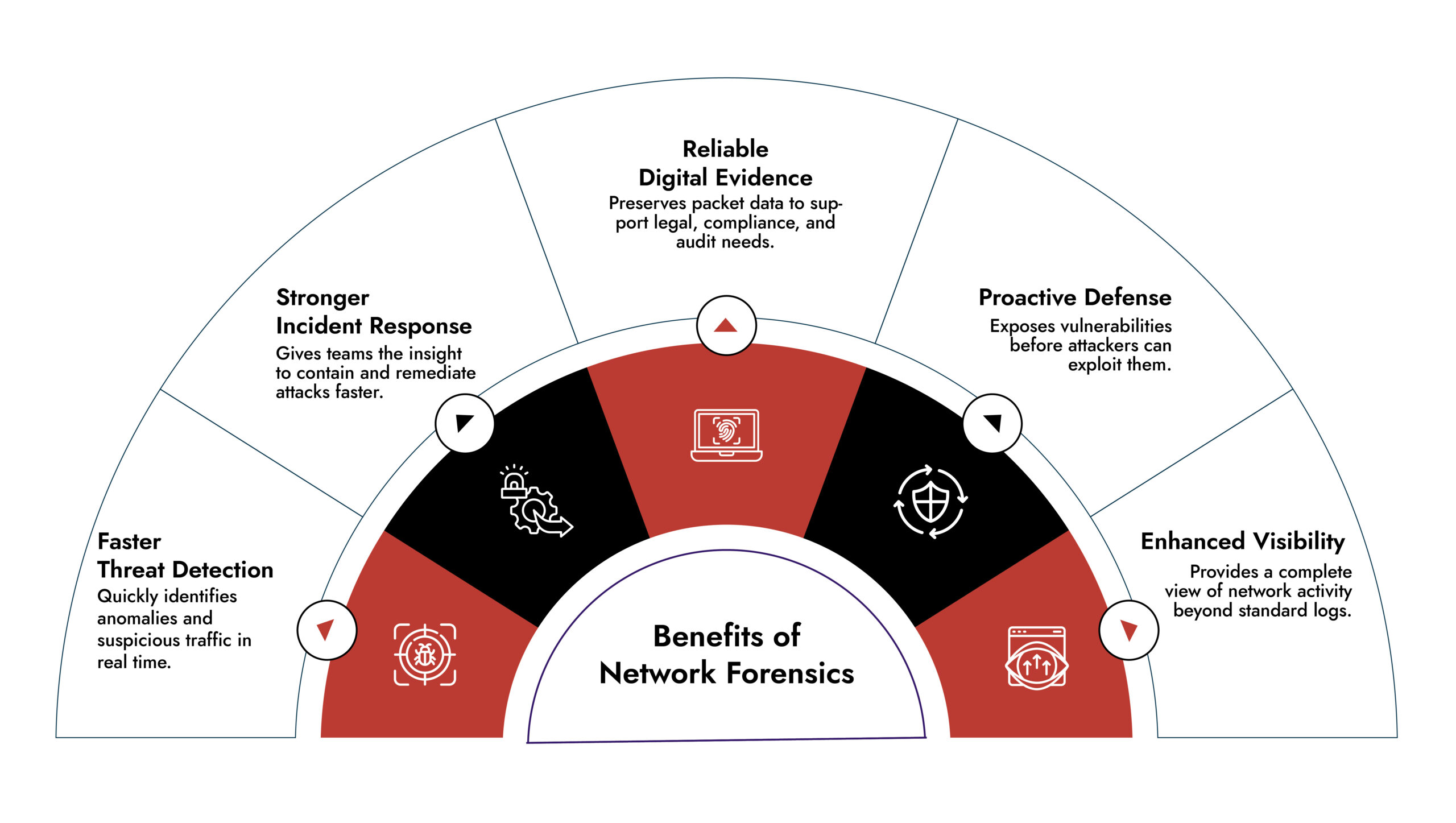
Why is Network Forensics Important in Cybersecurity?
Network forensics in cyber security addresses gaps that many traditional tools cannot. Modern attacks often span multiple systems, remain hidden for long periods, and avoid signature-based detection.
Advanced Threat Detection
Attackers often blend into normal traffic. Network traffic forensics exposes these threats by analyzing behavior patterns rather than relying on known signatures.
Stronger Incident Response
Detailed timelines help response teams understand the full scope of compromise. Network forensics analysis often reveals affected systems missed by other tools.
Compliance and Legal Support
Many industries require network monitoring and investigation capabilities. Healthcare, finance, and government organizations rely on network forensics to meet regulatory and legal obligations.
Threat Intelligence Development
Analyzing network activity helps teams understand attacker tactics and techniques. This intelligence improves future defenses.
Data Loss Prevention
Unauthorized data transfers can be detected during live monitoring or after an incident. Network forensics tools show how sensitive data left the organization.
Network Forensics Analysis Techniques
Network forensics examination utilizes various methods to derive significant insights from network information.
- Traffic Flow Analysis– Studies communication trends to detect abnormal behavior. Analysts examine how often connections occur, the volume of data, the timing, and the end points.
- Protocol Examination- Analyzes the utilization and misuse of protocols. This involves examining headers, payloads, and communication sequences.
- Behavioral Analysis– Establishes a standard of typical behavior and highlights anomalies. This is effective for insider threats and sophisticated ongoing threats.
- Timeline Reconstruction- Arranges events to demonstrate the evolution of an assault and the activities of intruders within the network.
- Correlation Analysis- Combines network forensics data with SIEM, endpoint, and threat intelligence sources for a complete understanding.
- Pattern Recognition- Uses statistical methods and machine learning to detect recurring actions linked to identified attack types
See Every Threat, Stop Every Attack
Gain complete visibility across cloud, on-prem, and virtual networks with NetWitness® Network Detection and Response. Detect and investigate threats faster with real-time analytics and forensic-grade session reconstruction.

Network Forensics Tools
Effective investigations depend on the right network forensics tools.
- Packet Capture Tools– Wireshark remains the most widely used PCAP analyzer. TCPDump supports command-line capture, while Arkime enables large-scale packet analysis.
- PCAP Analysis Tools– NetworkMiner extracts files and credentials from captures. Xplico reconstructs web pages, emails, and application data. These tools turn raw traffic into usable evidence.
- Comprehensive Packet Capture Solutions- Platforms such as NetWitness document entire network sessions at scale, allowing for thorough network forensics examination in high-volume settings.
- Flow Analysis Tools- Tools like SolarWinds and ManageEngine evaluate flow records to identify lateral movement and data theft.
- SIEM and Log Analysis Platforms– Splunk and the ELK Stack integrate data from various sources, incorporating network forensics into extensive security processes.
- Specialized Forensic Solutions- Comprehensive platforms such as NetWitness integrate capture, analysis, and reporting within a unified interface designed for investigators
Real-World Applications of Network Forensics
Network forensics supports investigations across industries.
- Financial Services: Fraud detection and breach investigations
- Healthcare: HIPAA violation analysis and patient data protection
- Government: National security and state-sponsored attack detection
- Manufacturing: Intellectual property theft investigations
- Law Enforcement: Cybercrime investigations and legal evidence collection
Challenges and Best Practices of Network Forensics
Encrypted Traffic- Encryption limits deep packet inspection. Teams rely on metadata, certificates, and behavior analysis instead.
Scale and Performance- High traffic volumes require scalable platforms and smart filtering.
Cloud Environments- The ever-changing infrastructure makes it challenging to maintain visibility and gather data. Optimal strategies include robust retention policies, network segmentation, skilled personnel, and compatibility with current tools.
Legal and Privacy Issues- Investigations need to adhere to privacy regulations while upholding standards for evidence.
Skills and Training- Network forensics necessitates proficiency in networking, investigative techniques, and managing legal evidence
Industry Research and Expert Validation
Industry standards reinforce the role of network forensics in cyber security as a core investigation capability, not an optional add-on. The National Institute of Standards and Technology (NIST) has long emphasized the importance of forensic readiness within incident response programs.
NIST Special Publication 800-86, Guide to Integrating Forensic Techniques into Incident Response, outlines how forensic capabilities should be embedded into security operations before an incident occurs. It highlights evidence preservation, investigation workflows, and coordination between detection and response teams. These principles align directly with modern network forensics analysis, where packet data, session records, and timelines are essential to understanding how attacks unfold across interconnected systems.
In parallel, NIST Special Publication 800-92, Guide to Computer Security Log Management, establishes best practices for collecting, retaining, and analyzing logs across infrastructure. Effective log management is foundational to network traffic forensics, particularly when correlating packet-level data with SIEM alerts, endpoint telemetry, and authentication events. Without reliable log collection and retention, forensic investigations lose context and evidentiary value.
Together, these standards validate the operational need for network forensics tools and network forensics software that support structured investigations, legal defensibility, and integration with incident response and SIEM platforms. They also reinforce that visibility, evidence integrity, and correlation are not product features but baseline requirements for mature cybersecurity programs.
Challenges and Best Practices of Network Forensics
- Encrypted Traffic- Encryption limits deep packet inspection. Teams rely on metadata, certificates, and behavior analysis instead.
- Scale and Performance- High traffic volumes require scalable platforms and smart filtering.
- Cloud Environments- The ever-changing infrastructure makes it challenging to maintain visibility and gather data. Optimal strategies include robust retention policies, network segmentation, skilled personnel, and compatibility with current tools.
- Legal and Privacy Issues- Investigations need to adhere to privacy regulations while upholding standards for evidence.
- Skills and Training- Network forensics necessitates proficiency in networking, investigative techniques, and managing legal evidence
Conclusion
Network forensics has developed into an essential cybersecurity function. With the increase in complexity of attacks, organizations require insight into network communications to effectively identify threats and examine incidents.
Network forensics analysis exposes patterns of how attacks traverse infrastructure, which other tools frequently overlook. From real-time detection to after-incident analysis, it provides teams with the perspective required to react with assurance.
Entities that allocate resources to network forensics tools, proficient analysts, and organized procedures are more equipped to manage incidents, assist in legal actions, and safeguard essential assets in a network-oriented threat environment
Frequently Asked Questions
1. What is network forensics in cybersecurity?
Network forensics in cyber security is the process of analyzing network traffic to investigate security incidents. It focuses on how systems communicate, rather than individual devices, to uncover attack paths, data theft, and attacker behavior across the network.
2. What is the role of network forensics in digital investigations?
The role of network forensics in digital investigations is to reconstruct events during a cyber incident. It helps investigators understand how an attack started, how it spread, which systems were affected, and what data may have been accessed or exfiltrated.
3. How is network forensics different from endpoint forensics?
Endpoint forensics analyzes data stored on individual devices like laptops or servers. Network traffic forensics examines communications between systems. This makes network forensics essential for detecting lateral movement, command-and-control traffic, and multi-system attacks.
4. What does network forensics analysis involve?
Network forensics analysis includes capturing packets, reviewing flow data, analyzing protocols, and correlating events over time. The goal is to identify suspicious behavior, build attack timelines, and support incident response and remediation.
5. What are common network forensics tools?
Common network forensics tools include packet capture tools like Wireshark and TCPDump, PCAP analysis tools such as NetworkMiner and Xplico, flow analysis platforms, SIEM integrations, and full packet capture solutions like NetWitness.
6. Why is network forensics important for incident response?
Network forensics gives incident response teams visibility beyond alerts. It shows the full scope of compromise, including hidden systems and delayed attacker activity, allowing teams to contain threats faster and prevent repeat attacks.
Rolling the Dice: Ransomware in the Gaming Industry
Discover how ransomware attacks hit gaming companies, how attackers moved laterally, and why network visibility is key. Learn real-world lessons and strategies to detect, respond, and protect critical systems.






