NDR Integration Best Practices
Effective network detection and response solutions depend on integrations that add context and speed up response. Instead of treating NDR as a standalone sensor, integrations should support how investigations and containment actually happen across the security stack.
Key best practices include:
- Integrating NDR with SIEM to correlate network activity with logs, identities, and historical behavior
- Connecting NDR to SOAR platforms to automate enrichment, investigation, and response actions
- Aligning NDR with EDR tools to link network traffic to specific endpoints and processes
- Using curated threat intelligence feeds to prioritize detections based on active threats
- Integrating with network security management and enforcement controls for faster containment
Introduction
Most organizations don’t struggle because they lack tools. They struggle because their tools don’t work together.
That problem shows up clearly with NDR solutions. On paper, Network Detection and Response promises deep visibility and faster threat detection. In reality, many deployments underperform because NDR runs in isolation, disconnected from the systems that provide context, response, and operational scale.
Here’s the thing. NDR only delivers value when it integrates into how security teams already detect, investigate, and respond. Without the right integrations, even the most capable NDR platform becomes another alert generator competing for attention.
NDR technologies are estimated to save businesses an average of $1.9 million and identify threats 108 days faster than traditional methods by 2025.
This article breaks down the integrations that separate effective NDR solutions from expensive shelfware.
Why Integrations Define NDR Performance
Detection without context is noise. NDR solutions analyze network behavior at a scale. But they don’t operate in a vacuum. They need identity data, endpoint telemetry, threat intelligence, and response workflows to turn signals into decisions.
According to NIST, organizations that correlate network, endpoint, and log data reduce mean time to detect by over 40 percent. Gartner research from 2024 also highlights integration depth as a top differentiator among enterprise network detection and response tools.
What this really means is simple. If your NDR integrations stop at basic log forwarding, you’re leaving most of the value on the table.
Which Integrations are Essential for an Effective NDR Solution?
NDR technology emerged in the early 2010s to identify and stop evasive network threats that couldn’t be easily blocked using known attack patterns or signatures.
SIEM, SOAR, EDR, threat intelligence, and network security management systems – these five integrations form the operational backbone of modern NDR security. Each plays a distinct role and skipping anyone creates blind spots.
Let’s break them down.
SIEM Integration: The Detection Multiplier
How does NDR integration with SIEM improve threat detection? It improves correlation, confidence, and coverage.
An NDR platform sees traffic patterns, protocol behavior, and session-level anomalies. A SIEM sees logs, identities, authentication events, and historical patterns. When you integrate the two, detection quality improves immediately.
Effective Network Detection and Response integrations with SIEM enable:
- Correlation of network anomalies with authentication events
- Validation of suspicious traffic against historical log behavior
- Faster triage through shared timelines and evidence
Without SIEM integration, NDR solutions flag activity. With it, they explain the activity.
SOAR Integration: Turning Detection into Action
What is the benefit of integrating NDR with SOAR? It closes the gap between detection and response.
NDR identifies suspicious behavior. SOAR operationalizes it. Together, they reduce response time and analyst fatigue.
A well-integrated NDR platform feeds high-confidence detections into SOAR playbooks that can:
- Enrich alerts with threat intelligence and asset context
- Trigger containment actions through firewalls or access controls
- Standardize investigation steps across teams
According to IBM’s 2024 Cost of a Data Breach Report, organizations using automated response workflows reduce breach of lifecycle costs by an average of $1.76 million.
Without SOAR, NDR solutions depend on manual follow-up. That doesn’t scale.
EDR Integration: Network and Endpoint, Aligned
How does NDR work with EDR tools? It fills visibility gaps EDR cannot reach.
EDR excels at endpoint behavior. NDR excels in network behavior. Modern attacks span both. Integration is non-negotiable.
When NDR solutions integrate with EDR:
- Network anomalies gain endpoint attribution
- Suspicious sessions map to specific hosts and processes
- Analysts confirm lateral movement and command-and-control activity faster
This integration matters even more in hybrid environments where unmanaged devices, IoT, and OT assets exist. EDR can’t see what it can’t install on. NDR can.
CISA’s 2024 advisories repeatedly emphasize layered detection across endpoint and network telemetry for advanced threat detection.
Threat Intelligence Integration: Context That Matters
Why is threat intelligence integration important for NDR? Because behavior alone doesn’t tell you intent.
Threat intelligence gives NDR security external context. It helps teams distinguish between unusual behavior and known malicious activity.
Strong NDR integrations with threat intelligence support:
- IOC enrichment for suspicious sessions
- Risk scoring based on active campaigns
- Prioritization aligned to real-world threats
The key is selectivity. High-quality intelligence sources outperform large feeds filled with stale indicators. NIST guidance updated in 2024 stresses relevance and validation over volume.
Threat intelligence doesn’t replace behavioral detection. It sharpens it.
Network Security Management Integration: Operational Reality
Visibility without enforcement limits impact. NDR solutions detect threats, but enforcement lives elsewhere. Firewalls, network access controls (NAC), and segmentation platforms execute policy.
Integration with network security management enables:
- Faster containment of confirmed threats
- Policy validation against observed traffic
- Reduced manual configuration errors
In complex enterprise networks, this integration prevents detection-response disconnects. It also supports auditability and compliance reporting, especially for regulated industries.

What are the Best Software Solutions for Integrating NDR Systems?
The best network detection and response tools integrate at the data, workflow, and response layers. API access alone doesn’t guarantee effectiveness.
Look for NDR solutions that support:
- Bidirectional data exchange, not one-way forwarding
- Session-level and artifact-level context sharing
- Customizable workflows aligned to your SOC model
This matters more than the number of integrations listed on a product page.
Unify IT and OT Threat Detection with NetWitness® and DeepInspect
-Correlate IT and OT telemetry for end-to-end operational visibility.
-Detect advanced threats across industrial and enterprise networks with protocol-level intelligence.
-Accelerate investigations using enriched OT context and unified analytics.
-Reduce blind spots and strengthen response across converged IT/OT environments.
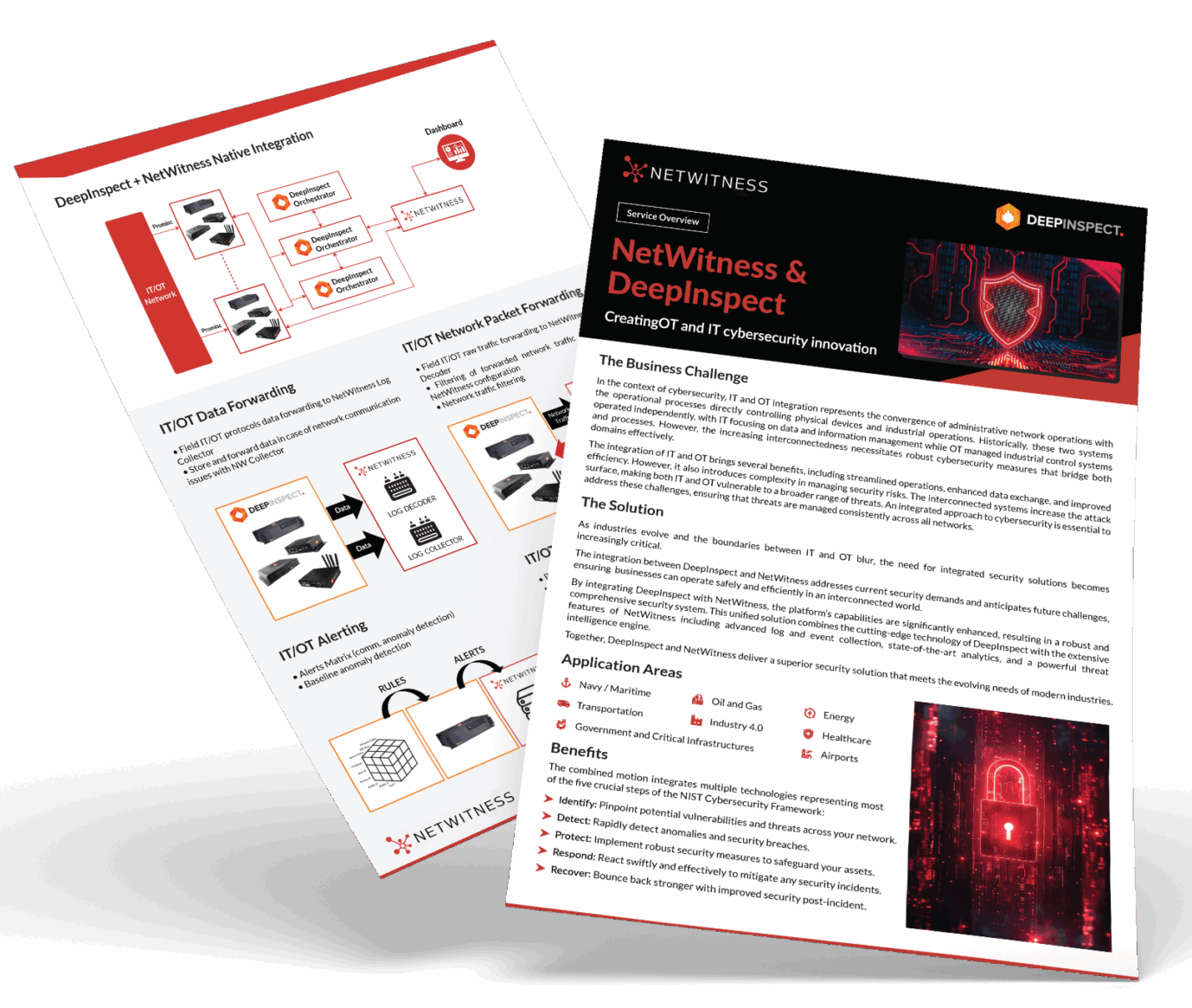
NetWitness Perspective: Integration as a Design Principle
NetWitness approaches NDR integrations as a core design requirement, not an add-on.
The NetWitness NDR module focuses on deep network visibility, session reconstruction, and artifact extraction. That depth allows meaningful integration with SIEM, SOAR, EDR, and threat intelligence without losing context.
Rather than treating integrations as simple connectors, the platform emphasizes shared investigation workflows and evidence of continuity across the security stack. This approach aligns with NIST and CISA recommendations around integrated detection and response architectures.
The goal isn’t more alert. It’s fewer, better decisions.

Measuring Integration Success in NDR Security
Effective NDR security integrations show up in metrics that matter:
- Reduced mean time to detect and respond
- Higher alert confidence and lower false positives
- Faster root-cause analysis
If integrations don’t move these numbers, they’re cosmetic.

Conclusion: Integration is the Real Differentiator
NDR solutions no longer win on detection claims alone. Every serious platform can spot anomalies. The difference lies in what happens next.
Integrations determine whether NDR becomes a trusted detection layer or another dashboard teams to avoid. SIEM, SOAR, EDR, threat intelligence, and network security management aren’t optional add-ons. They define performance.
If your NDR platform integrates deeply, detection becomes actionable. If it doesn’t, the risk stays the same. The smartest teams don’t ask what an NDR tool detects. They ask how it fits.
Frequently Asked Questions
1. Which integrations are essential for an effective NDR solution
Essential integrations for an effective NDR solution include SIEM for context and correlation, SOAR for response orchestration, EDR for endpoint visibility, threat intelligence for enriched detection, and network security management systems for enforcement. These integrations ensure detection connects with investigation and action.
2. How does NDR integration with SIEM improve threat detection?
NDR integration with SIEM correlates network telemetry with logs, identities, and event history, increasing detection fidelity and reducing false positives. This layered view helps teams spot advanced threats that neither system sees alone.
3. What are the benefits of integrating NDR with SOAR?
When an NDR platform feeds into SOAR, alerts become coordinated response actions. Playbooks can automate enrichment, containment, and escalation, shrinking investigation time and analyst workload without losing context.
4. How does NDR work with EDR tools?
NDR and EDR work together by combining network behavior with endpoint telemetry. NDR flags suspicious traffic patterns, and EDR adds host-level evidence, improving root-cause clarity and response confidence across both sensor domains.
5. Why is threat intelligence integration important for NDR?
Threat intelligence integration gives NDR context about known bad actors, active campaigns, and emerging TTPs. It helps prioritize what matters most and differentiates benign anomalies from actionable threats.
6. What are the best software solutions for integrating NDR systems?
The best solutions emphasize deep API-level integrations that share session data, artifacts, and context rather than simple alerts. Look for platforms that support bidirectional workflows with SIEM, SOAR, EDR, and threat feeds to ensure meaningful security operations outcomes.
Proactive Network Threat Detection with NetWitness® NDR
-Spot threats fast with AI-driven analytics.
-See everything across your network and cloud traffic.
-Investigate efficiently with built-in forensic tools.
-Adapt and scale to meet growing security needs.






