Key Takeaways
- Security orchestration cuts out manual, repetitive work by pulling data from every tool and automating early triage, enrichment, and response, which speeds up the entire security lifecycle.
- Playbooks create consistency. Every incident follows the same well-defined workflow, reducing errors, removing bottlenecks, and making analysts far more efficient.
- When orchestration connects SIEM, SOAR, endpoint, cloud, and network tools, the business gets better ROI from its existing stack and eliminates repetitiveness of effort across teams.
- By reducing alert fatigue, shrinking dwell time, and improving investigation quality, orchestration boosts overall business efficiency, lowers operational costs, and helps security teams scale without adding headcount.
Introduction
Most organizations assume security orchestration is just about speed. And yes, accelerating investigations is a big win. But when you look closer, real value runs deeper. Enterprise security orchestration reshapes how teams work, how decisions get made, and how efficiently the entire business operates. It gives security operations a backbone that scales without drowning analysts in manual steps or fragmented tools.
Let’s break down what enterprise security orchestration actually does, how it connects with SIEM, and why it changes the efficiency equation for modern enterprises.
What Security Orchestration Really Means
Security orchestration refers to the business of coordinating and automating security work between tools, people, and environments. It unites SIEM alerts, endpoint information, network indicators, cloud events, and threat intelligence and directs all the information over coordinated workflows that eliminate the manual lifting of analysts.
It is practical to consider it in the following way. Consider a SOC that has received a suspicious login. In the absence of orchestration, an analyst jumps between identity logs, endpoint agents, and network security tools, cloud consoles and threat intel feeds, attempting to assemble the story. All that is done automatically with a security orchestration platform. The system gathers context, verifies risk, enriches the alert, and initiates initial response steps. The analyst intervenes only in cases where an action really requires human intervention.
Security orchestration integrates data, tools and individuals into coherent workflows that operate in a clean way up to the end. It minimizes the manual efforts, minimizes the errors, and accelerates all the steps of the security lifecycle. To large organizations that must handle thousands of alerts daily, it is this change that transforms chaos into order, smooth operations.
Why Enterprise Security Orchestration Matters Now
Modern security operations face math problems. Alerts keep increasing, while analyst time doesn’t. Every time the organization expands its cloud footprint or deploys new applications, the volume of threats, false positives, and contextual data goes up.
Security orchestration benefits the business by reducing the cognitive load on analysts and compressing the time it takes to navigate all this information. It standardizes decision making, removes inconsistencies, and ensures incidents get handled the same way every time.
There is also a strategic angle. When you automate the routine work, analysts can focus on complex investigations, hunting, and long term improvements that actually move the needle. This creates measurable efficiency at a business level, not just within the SOC.
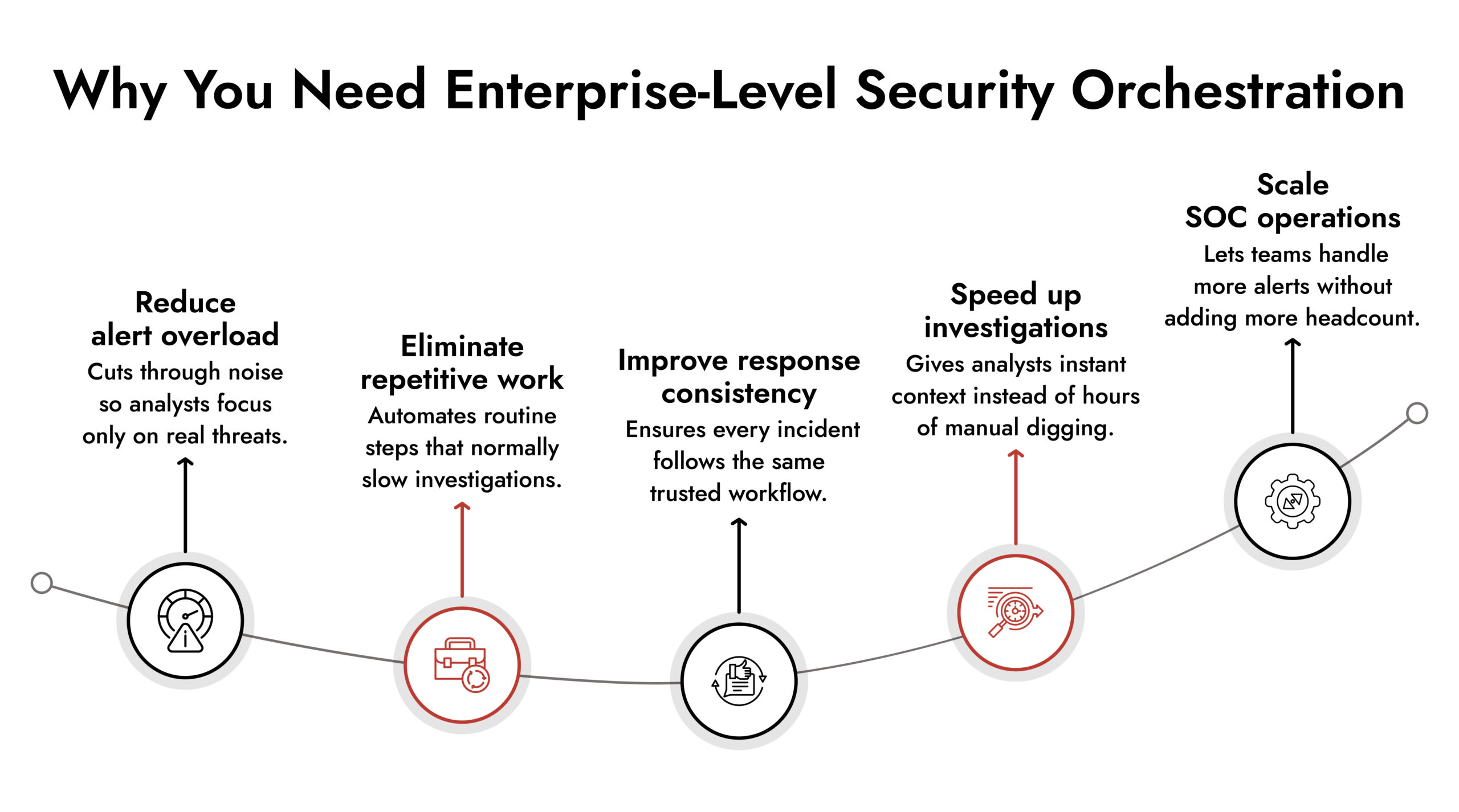
How Enterprise Security Orchestration Improves Business Efficiency
1. Faster Triage and Fewer Bottlenecks
Speed is the most visible benefit. With orchestration, triage becomes a mostly automated workflow. The platform enriches alerts with threat intel, user identity, asset value, and event history. It determines which alerts matter and which ones can be closed. Analysts stop spending hours gathering data and instead start with context already laid out.
This alone reduces dwell time, limits operational waste, and frees teams to focus on work that actually requires human judgment.
2. Consistent and Predictable Response
Without orchestration, every analyst handles incidents differently. One might check identity logs. Another might skip them. Someone else might delay the escalation. This inconsistency slows everything down and introduces risk.
Enterprise security orchestration enforces structured playbooks. These playbooks guide every step, ensure repeatability, and remove guesswork. When your SOC works with consistency, the business gains reliability and predictability.
3. Reduced Dependency on Tribal Knowledge
In many organizations, the fastest analyst becomes the bottleneck because everyone needs their input. Knowledge gets locked inside minds instead of processes. That becomes a problem during scaling, turnover, or staffing shortages.
Orchestration captures this knowledge and embeds it into workflows. New analysts onboard faster. Senior analysts stop acting as human routers. Operations become scalable in a way manual processes can never support.
4. Stronger SIEM and SOAR Integration
A SIEM security is powerful for detection and correlation. A SOAR security is powerful for orchestration and response. When you combine the two, workflow efficiency improves dramatically.
SIEM and SOAR integration lets you:
- Trigger relevant playbooks automatically when alerts fire
- Enrich SIEM, EDR, NDR alerts with context
- Trigger automated response actions directly from detections
- Map alerts to business priorities
- Close or suppress low value alerts automatically
This turns a reactive SOC into an active decision engine. The business sees fewer disruptions, quicker incident closures, and reduced operational overhead.
5. Better Use of Existing Security Tools
Most organizations already have dozens of tools across network security orchestration layers, endpoint, identity, cloud, and email. Without orchestration, these tools operate like islands. Analysts spend more time navigating tools than responding to threats.
An enterprise security orchestration platform acts as a connective tissue. It unifies actions across:
- Firewalls and network detection tools
- Cloud security platforms
- Threat intelligence feeds
- Vulnerability scanners
- Ticketing and knowledge systems
This improves tool ROI and prevents overlap, redundancy, and wasted spending.
6. Higher Quality Investigations
Once orchestration reduces repetitive work, investigations get better. Analysts have more time to run deep checks instead of rushing through alerts. Playbooks handle the basics while humans handle the nuance.
This leads to:
- More accurate root cause findings
- Stronger incident documentation
- Better containment actions
- Fewer repeated mistakes
- More opportunities for proactive threat hunting
Better investigations reduce long-term risk and support more informed security investments.
7. Reduced Operational Costs Across the Board
Business efficiency is not only about speed. It is about cost reduction, smarter resource allocation, and minimizing downtime.
Security orchestration supports all three:
- Analysts spend less time on manual tasks
- Tools work more effectively together
- Incidents get resolved earlier, reducing impact
- False positives no longer drain hours of energy
- Compliance audits become easier and faster
- Containment can be performed automatically until the analyst can research the incident to minimize the damage
Over time, efficiency gains compound. Even small improvements in response time translate to meaningful reductions in risk exposure.
8. Improved Visibility and Reporting
Executives want clarity. They want to know what threats matter, how the SOC is performing, and where investment is needed. When data lives in different systems, reporting becomes a painful exercise.
A security orchestration automation and response platform centralizes incident data and workflow outcomes. This makes reporting cleaner and more accurate. Decision makers get insight into trends, bottlenecks, workload distribution, and long-term patterns.
Better reporting means better decisions. Better decisions mean more efficient operations.
Establish Incident Response consistency, speed, and scale with NetWitness® Orchestrator

Why Playbooks Matter
Playbooks are the backbone of orchestrated security operations. They turn strategy into action. Instead of relying on gut instinct, the SOC follows defined steps for each incident type.
Playbooks help the business by:
- Standardizing workflows
- Reducing errors
- Accelerating response
- Making training easier
- Improving compliance readiness
- Minimizing handoff delays
When multiple teams, tools, and decision points are involved, playbooks create a unified flow that keeps everyone aligned.
How Security Orchestration Drives Business Efficiency
Enterprise security orchestration does more than automated tasks. It changes how teams’ function. It eliminates unnecessary friction. It improves cross-tool communication and helps analysts focus on high-value work.
For the business, this means:
- Less downtime
- Lower operational costs
- Faster triage and response
- Better use of existing investments
- Stronger security outcomes with the same or fewer resources
Security becomes an enabler, not a drain.
Conclusion
Security orchestration is not just an SOC upgrade. It is a business efficiency upgrade. When you combine structured playbooks, deep SOAR and SIEM integration, automated enrichment, and coordinated response actions, the entire security lifecycle becomes stronger and faster.
The organization gains stability. The SOC gains time back. Analysts gain clarity. And the business gains confidence that its security operations can scale without sacrificing quality of service.
Frequently Asked Questions
1. What is security orchestration and automation?
It is the coordination and automation of security processes, tools, and actions through a centralized platform that manages both workflow and response.
2. What is the enterprise orchestration platform?
It is a security orchestration platform designed for large scale environments, integrating multiple tools across network, cloud, endpoint, and identity to streamline operations.
3. How does security orchestration improve business efficiency?
It reduces manual work, accelerates response, standardizes workflows, improves tool integration, and enables analysts to focus on higher level tasks instead of repetitive steps.
4. What is the role of playbooks in security orchestration?
Playbooks define the step by step workflows used to triage, investigate, and respond to incidents. They ensure consistency, reduce errors, and speed up operations.
5. What tools typically integrate with enterprise security orchestration?
SIEM platforms, firewalls, EDR tools, cloud security services, threat intel feeds, ticketing systems, vulnerability scanners, and network detection solutions.
Make Way for the Intelligent SOC with NetWitness®
-Turn data overload into actionable intelligence.
-Accelerate detection with AI-driven insights.
-Empower analysts with enriched, contextual decision-making.
-Build a smarter, faster, more resilient SOC.






