SIEM Integration Explained
SIEM integration connects security tools, systems, and data sources to a centralized Security Information and Event Management (SIEM) platform, enabling unified visibility, threat detection, and faster incident response across an organization’s IT environment.
Introduction
Security Information and Event Management (SIEM) integrations are an essential part of any organization’s security arsenal. By connecting SIEM networking to other systems, organizations can ensure that all available logging data is monitored for potential threats and drive a more efficient response when a breach occurs. SIEM integrations also help organizations detect malicious activity quickly, allowing them to take action before damage is done.
In this article, we will explore the different types of SIEM integrations, as well as how they can be used to better protect your organization from cyberattacks and why you should contact NetWitness to get started. We’ll also talk about some challenges and benefits of SIEM integration, so if you’re ready to start, let’s dive into SIEM integrations at NetWitness.
What Is SIEM Integration?
SIEM integration is the process of connecting multiple security tools and data sources such as firewalls, endpoints, servers, and cloud platforms to a centralized SIEM platform. Proper SIEM integration strengthens overall SIEM security by enabling unified monitoring, analytics, and incident response. It also enhances SIEM network monitoring by giving security teams a single view of activity across the environment.
What Is SIEM Technology?
Security Information and Event Management software (SIEM technology) can be used to detect, investigate, respond to, and monitor security threats or suspicious activity. SIEM solutions allow organizations to collect log data from various sources such as network devices, applications, databases, operating systems, users, and other sources in order to analyze potential threats. This data can then be used to identify and respond to potential threats, as well as build a better understanding of the organization’s security posture.
Some threats that SIEM technology can help monitor throughout your organization are malware, ransomware, phishing, DoS (Denial of Service), and many more. As the digital age evolves, more cyberattacks are being introduced by threat actors. Using NetWitness as your cyber security provider will help you stay ahead of the attacks as they surface. Protecting your bottom line is our top priority. Keep reading to learn more about NetWitness and SIEM integration. 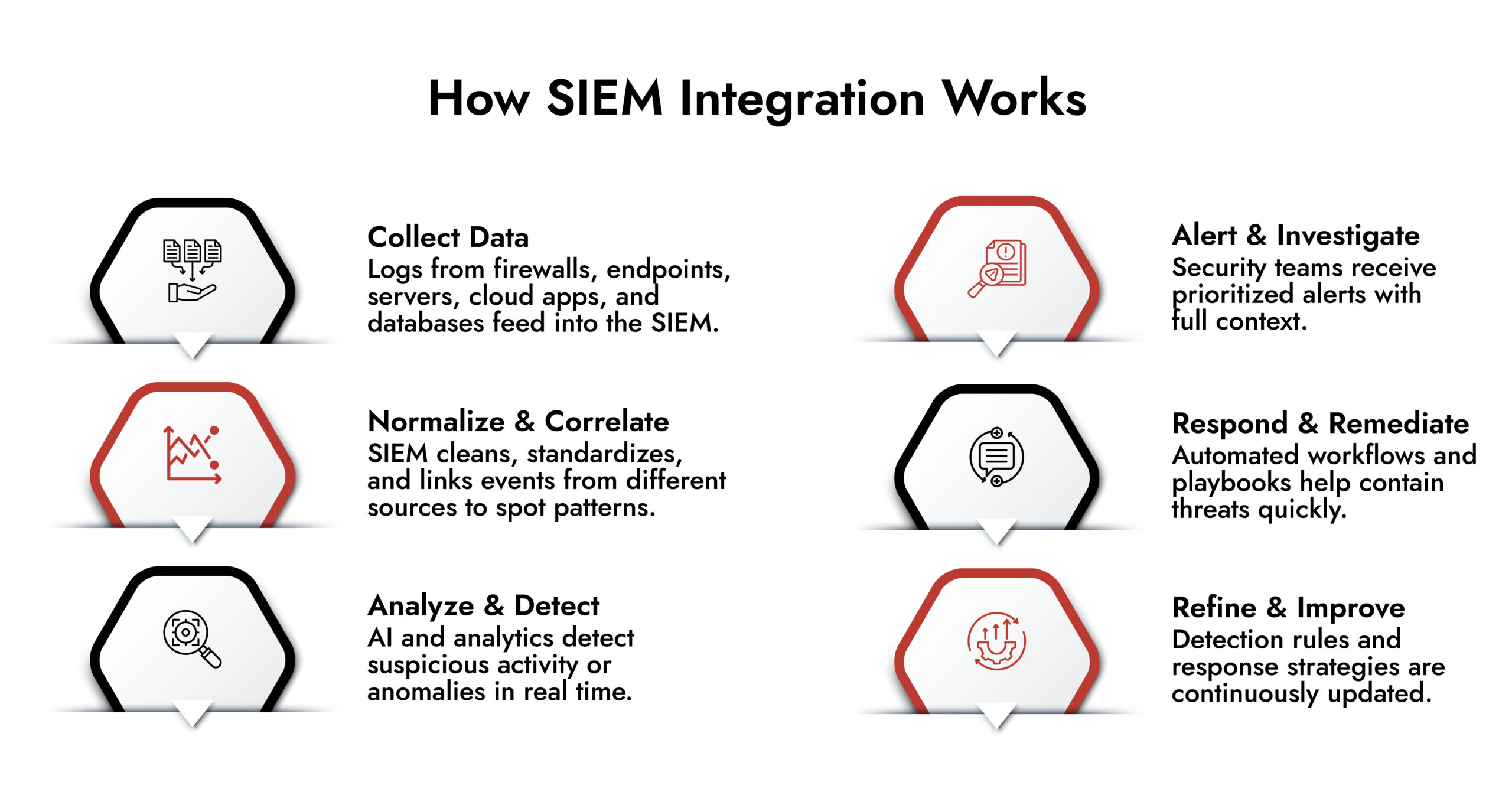
What Makes SIEM Integrations Essential to a Strong Security System?
SIEM integration is the process of connecting various security tools, systems, and data sources – like firewalls, endpoints, servers, and cloud platforms to a centralized SIEM platform for unified monitoring, analysis, and response. In today’s modern world, having a comprehensive security system is essential for businesses of all sizes. With the right security system in place, organizations can protect their assets and data from malicious activities such as hacking or theft. Moreover, by integrating the latest technology, such as SIEM integrations, businesses can improve the effectiveness of their security system and keep their operations running smoothly.
How Does SIEM Integrations Help Secure Your Data?
SIEM integrations provide businesses with an additional layer of protection for their data. By connecting systems together to share information across different applications in real time, it becomes much harder for unauthorized entities such as hackers or criminals to access or manipulate sensitive information. By using the latest technologies like artificial intelligence (AI) and machine learning (ML), organizations can improve their security systems and stay updated on emerging threats.
Advanced Detection Capabilities
Another benefit of implementing a comprehensive security system with SIEM integrations is the advanced detection capabilities it provides. By connecting existing systems together into a single platform, businesses can leverage powerful analytics tools to detect potential threats before they become an issue. For example, if there is suspicious activity on one system or application, responders in the security operations center (SOC) can be alerted immediately.
What Can SIEM Integrations Do?
SIEM software solutions are used to provide visibility across the environment to detect cyber threats and to maintain the operational health of systems. It leverages log management capabilities and techniques to detect anomalies within your environment that could signify malicious activity.
1. Log Management
Log management is the process of collecting log-based data from various sources within a system in order to identify potential security risks or incidents. This is a core capability of SIEM networking and allows real-time monitoring and audit trail creation.
2. SIEM Network Monitoring and Analysis
SIEM network monitoring allows organizations to track network activity in real time and understand traffic behavior across the environment.
3. Endpoint Detection and Response (EDR) Integration
Endpoint detection and response visibility becomes more powerful when endpoint telemetry is brought into a SIEM integration.
4. User and Entity Behavior Analytics (UEBA)
UEBA within SIEM uses machine learning models to identify anomalous behavior and accelerate investigation timelines.
5. Event Correlation
Event correlation connects activity across multiple systems to identify threats that would otherwise remain hidden, a core strength of SIEM integrations.
6. Intrusion Detection and Prevention
IDS and IPS SIEM integrations provide early warning and prevention of unauthorized access attempts.
SIEM integrations are essential for keeping networks secure from potential cyber threats by leveraging connections with log management, network monitoring and analysis, event correlation, and intrusion detection and prevention solutions. By understanding how each type of integration works together, security professionals, IT administrators, and tech startups will be able to better protect their systems against malicious actors who are looking to gain unauthorized access or cause harm through other means. With SIEM integrations in place, organizations will have peace of mind knowing their networks are safe from harm while still being able to keep up with the ever-changing landscape of cyber threats out there today.
What Are the Key Benefits of SIEM Integrations?
For any business to succeed in the digital age, it must have a robust security infrastructure in place. One of the most important tools for achieving this is SIEM. SIEM integrations with other tools in your security arsenal are designed to provide organizations with increased visibility into their overall security posture as well as improved incident response times. In this section, we will discuss some of the key benefits that SIEM integrations have to offer.
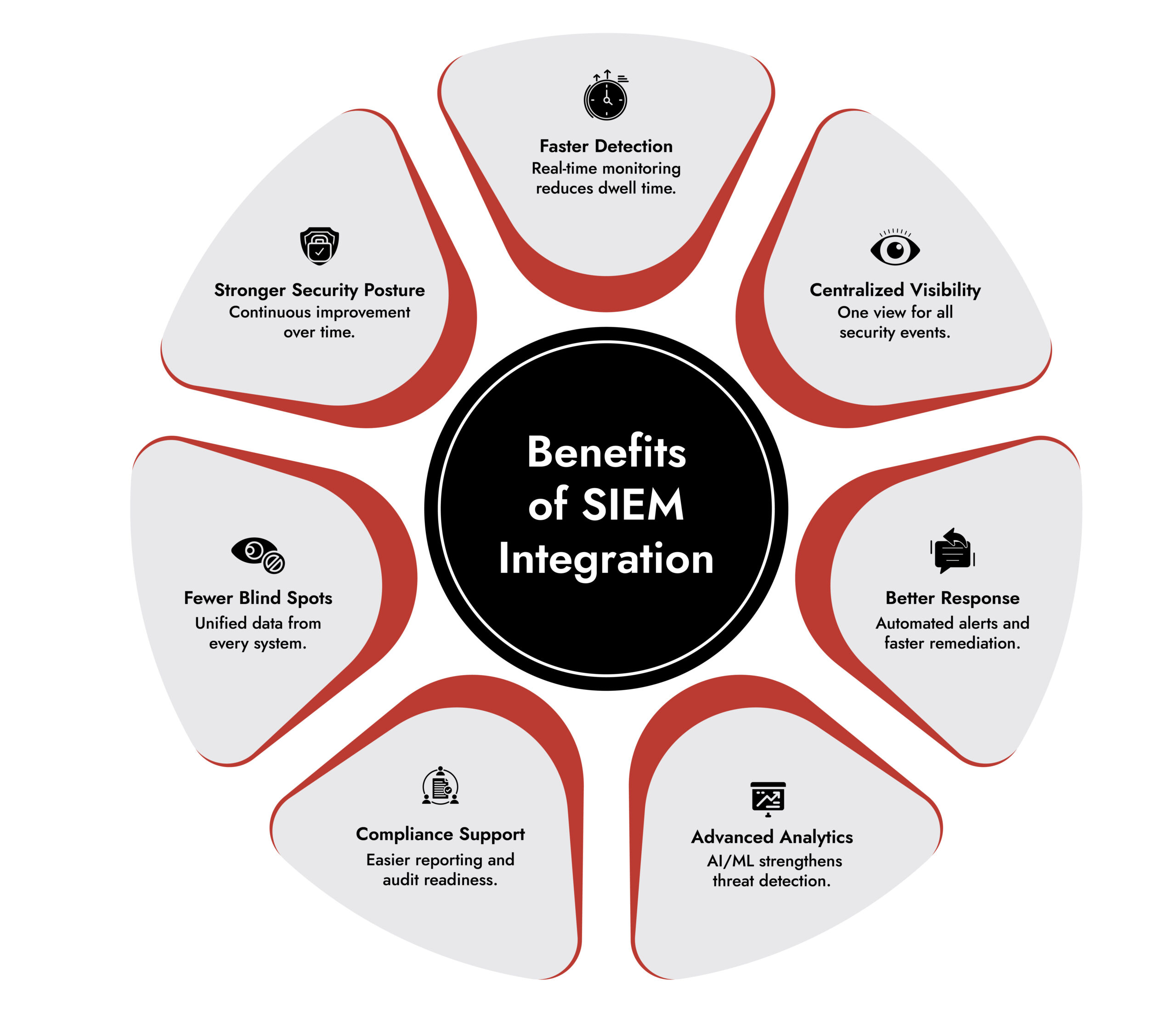
1. Improved Incident Response Times
One of the primary benefits of SIEM integrations is improved cyber incident response times. By having an integrated platform that can quickly detect and respond to potential threats, organizations can drastically reduce the amount of time it takes to detect and respond to incidents and minimize the damage caused by them.
2. Increased Visibility into Security Events
Another benefit of SIEM integration is increased visibility into security events. By integrating multiple sources of data, such as log files from systems, applications, databases and other sources, organizations gain a comprehensive view of their environment, which helps them identify potential threats more quickly and accurately. Having this level of visibility also allows organizations to prioritize security incidents based on their severity so they can address the most urgent ones first.
In short, SIEM integrations provide businesses with improved incident response times, increased visibility into security events, and automation of various security processes and responsibilities, which ultimately leads to a more secure environment for your organization. If you are looking for ways to strengthen your organization’s cybersecurity posture, then consider investing in an integrated SIEM solution. It could be just what you need.
Choose the Right SIEM with Confidence
Evaluate vendors using a comprehensive, expert-built checklist.
Identify must-have SIEM features for complete visibility and faster detection.
Compare capabilities to ensure scalability, automation, and integration.
Make informed decisions with NetWitness’ proven SIEM guidance.

What Are Some Challenges of SIEM Integrations?
SIEM technology is a powerful tool for organizations to have when it comes to protecting their environments and monitoring activity within them. However, there are some challenges associated with SIEM integrations that can make the process more difficult than anticipated. These challenges include the cost of implementation and maintenance, the complexity of deployment and operation, and the difficulty integrating new technologies. Let’s take a look at these challenges in more detail.
1. Cost of Implementation and Maintenance:
The cost associated with implementing a SIEM integration can be quite high due to the complexity of the environment itself. This is especially true if an organization has not previously used or deployed such a system before. Additionally, once implemented, maintaining a SIEM solution can also be costly due to the need for regular updates and upkeep, which often requires personnel dedicated solely to this task. As such, it is important for organizations to consider the cost of implementation and maintenance prior to deciding if this is the right solution for them.
2. Complexity of Deployment and Operation:
Another challenge that organizations face when considering a SIEM integration is the complexity associated with deploying and operating the SIEM system itself. This includes understanding how it works as well as setting up rules for alerting on potential threats or anomalies detected within the broader environment. Additionally, organizations must also understand what data sources will be utilized in order to obtain accurate information regarding collected logs. All of these steps must be taken prior to having an effective security monitoring solution in place.
3. Difficulty Integrating New Technologies:
Finally, another challenge associated with SIEM integrations is the difficulty integrating new technologies into existing systems or networks. As SIEM technology advances over time, so do threats, which means that organizations must ensure they are keeping up with these changes to remain secure. This may involve updating software or hardware as well as learning how to integrate new solutions into existing systems or networks, which can be quite difficult if not done properly. A common failure point for some SIEM platforms occurs where a monitored log source is updated to a new version and the SIEM networking no longer recognizes the new log format. As such, organizations should take extra care when considering any type of integration into their existing security solutions in order to avoid potential risks or vulnerabilities down the road.
Real-World SIEM Integration Use Case: Defense Contractor
A U.S. defense contractor experiencing frequent targeted attacks, including ransomware, advanced persistent threats, and insider risk, found that its legacy SIEM could not detect a real infiltration, creating a blind spot in its security posture. After evaluating multiple solutions, the organization chose the NetWitness Platform for its advanced threat detection, correlation, and response capabilities.
Once implemented, the NetWitness SIEM integration delivered immediate operational impact. The security team gained deeper visibility into what they could see and, more importantly, what they weren’t seeing before. With improved data correlation and real-time analytics, their ability to detect and investigate attacks improved dramatically.
To ensure rapid optimization and ongoing success, the organization engaged NetWitness to tune the SIEM environment to its specific needs, accelerate incident response workflows, and support ad hoc forensic tasks. According to the company’s information security manager, this partnership was critical in elevating their overall security operations and advancing their cybersecurity maturity.
Now, the organization is expanding data sources into the platform and considering replacing other standalone security tools with NetWitness solutions, thanks to the platform’s scalability and enhanced visibility.
Frequently Asked Questions
1. What is the meaning of SIEM security?
SIEM security refers to using Security Information and Event Management tools to collect, analyze, and respond to security events across IT environments.
2. What are the steps in SIEM integration?
Assess data sources, define use cases, configure log ingestion, set correlation rules, test alerts, and optimize continuously.
3. What is SIEM integration?
A SIEM integration connects multiple security tools and data sources into one SIEM platform for unified monitoring and response.
4. How does SIEM network monitoring help?
SIEM network monitoring provides real-time insight into traffic patterns, anomalies, and intrusion attempts.
5. Why is SIEM integration critical for cybersecurity?
It centralizes security data, improves detection speed, and enables coordinated incident response.
Top SIEM Use Case for Threat Detection
-Uncover hidden threats with unified log and event analysis.
-Centralize security monitoring across endpoints, network, and cloud.
-Speed up detection and streamline incident response with correlated alerts.
-Empower your SOC with actionable insights and compliance-ready reporting






