Why do SOC teams map SIEM capabilities to MITRE ATT&CK?
Mapping SIEM capabilities to the MITRE ATT&CK framework helps SOC teams move from collecting data to proving detection coverage. It shows which attacker techniques your SIEM platform can actually detect, where gaps exist across the kill chain, and how well threat detection aligns with real-world attack behavior.
Most SIEM programs fail for one simple reason: they collect everything, but they do not prove what they can actually detect.
Leadership asks, Are we covered? The SOC answers with dashboards, ingestion numbers, and a long list of rules. But none of that explains whether your SIEM platform can spot real attacker behavior from first touch to impact.
That’s where MITRE ATT&CK comes in. When you map your SIEM capabilities to the MITRE ATT&CK framework and line it up across the cyber kill chain, you move from “we have detections” to “we can stop these techniques at these points, with this evidence, at this speed.”
You are not here to learn what SIEM is. You are here to pressure test your threat detection, expose gaps, and turn your security incident and event management program into a measurable detection engine.
What ATT&CK mapping actually means in a SIEM
ATT&CK mapping is the discipline of tying each detection, alert, correlation rule, analytic, or hunting query to:
- A specific ATT&CK technique (and ideally sub-technique)
- The telemetry your SIEM needs to see it
- The logic that turns telemetry into a signal
- The response path after it fires
When done right, it becomes your coverage contract. It tells you what your SIEM capabilities can catch, what they cannot, and what to do next.
The SIEM capabilities you need before mapping is even worth it
If your SIEM platform cannot do the basics below, mapping becomes theater.
Core SIEM capabilities that matter for ATT&CK alignment:
Normalized ingestion across control planes
Logs, endpoint telemetry, identity events, cloud audit trails, DNS, proxy, email, network telemetry, vulnerability context.
Entity context and enrichment
Asset criticality, user risk, geolocation, threat intel, known bad infrastructure, vulnerability exposure.
Correlation across time and sources
Single events are rarely enough. ATT&CK techniques often show up as sequences.
Behavioral analytics and baselining
Many techniques are “normal” until you see them in the wrong context.
Investigation workflow and case management
Detections without investigation paths create alert fatigue.
Automation hooks
Ticketing, SOAR actions, containment, blocking, isolation, access revocation.
This is also where cybersecurity awareness and cybersecurity risk assessment intersect with detection. Mapping does not replace training or governance. It makes your operational controls measurable.
Map ATT&CK to the kill chain so your coverage reads like an attacker story
ATT&CK is organized by tactics and techniques. The kill chain is organized by attacker progression. Combining them gives you a practical view: where can we detect and disrupt, and how early?
Below is a kill chain view with the most common ATT&CK-aligned detection opportunities and what your SIEM should be doing at each stage.
1) Reconnaissance: weak signals, strong context
What attackers do: scan, enumerate, research identities and exposed services.
ATT&CK tactics often involved: Reconnaissance (TA0043), Resource Development (TA0042)
SIEM capabilities that matter:
- Internet-facing telemetry plus identity context
- Rate and anomaly detection
- External exposure context from your cybersecurity risk assessment program
Detection examples to map:
- Abnormal spikes in authentication attempts against a specific app
- Enumeration patterns in VPN, SSO, or cloud identity logs
- Unexpected discovery activity from newly seen IP ranges
Best practice: treat recon detections as risk signals, not “incidents.” They should raise visibility, tighten controls, and inform prioritization.
2) Weaponization and Resource Development: catch the setup
What attackers do: register domains, acquire infrastructure, build payloads, stage phishing kits.
ATT&CK tactics often involved: Resource Development (TA0042)
SIEM capabilities that matter:
- Threat intel enrichment
- Domain and certificate reputation context
- Email and web telemetry correlation
Detection examples to map:
- Newly registered domains communicating with employees
- Lookalike domains sending email to high value roles
- Repeated connections to suspicious hosting providers
This is where cybersecurity awareness pays off. If users report suspicious emails and your SIEM can connect that report to telemetry, you cut time to detection dramatically.
3) Delivery: make “initial touch” visible
What attackers do: deliver the lure via email, drive-by, supply chain, remote services.
ATT&CK tactics often involved: Initial Access (TA0001)
SIEM capabilities that matter:
- Email security logs, proxy logs, DNS, endpoint events
- Correlation that connects message to click to execution
Detection examples to map:
- Email with malicious indicators followed by URL click, then new process creation
- Download of an executable from a suspicious domain followed by privilege prompts
- Rare file types delivered to specific departments
If you cannot correlate email to endpoint behavior, your SIEM security capabilities are not complete for BOFU-grade threat detection.
4) Exploitation: focus on behavior, not only signatures
What attackers do: exploit a vulnerability, abuse misconfigurations, execute code.
ATT&CK tactics often involved: Execution (TA0002), Privilege Escalation (TA0004)
SIEM capabilities that matter:
- Vulnerability exposure context
- Endpoint process telemetry and command line visibility
- Cloud control plane visibility for misconfig abuse
Detection examples to map:
- Suspicious parent-child process chains after a known vulnerable service is touched
- Abnormal PowerShell usage tied to a user that never runs it
- Cloud role assumption from unusual devices or impossible travel patterns
This is where ATT&CK mapping forces honesty. If you have no endpoint telemetry, you cannot claim meaningful coverage for execution and escalation techniques.
5) Installation and Persistence: the part attackers bet you will miss
What attackers do: plant persistence, create accounts, add services, schedule tasks, deploy backdoors.
ATT&CK tactics often involved: Persistence (TA0003), Defense Evasion (TA0005)
SIEM capabilities that matter:
- Endpoint changes, registry events, service creation
- Identity governance logs
- Baselines for administrative behavior
Detection examples to map:
- New scheduled task created shortly after a suspicious login
- Service installation from temp directories
- Creation of new admin accounts outside approved workflows
- Endpoint security tampering attempts
A clean ATT&CK mapping here should include both detection logic and response logic, because persistence is where containment matters more than classification.
6) Command and Control: prove you can see covert communication
What attackers do: beacon, tunnel, use proxies, blend into common protocols.
ATT&CK tactics often involved: Command and Control (TA0011)
SIEM capabilities that matter:
- DNS, proxy, firewall, network metadata, and ideally packet context
- Detection of beaconing patterns and rare destinations
- TLS and certificate visibility where possible
Detection examples to map:
- Periodic outbound connections with fixed intervals
- Rare JA3 & JA4 like client fingerprints across multiple hosts (if you have that telemetry)
- DNS requests with high entropy subdomains
- Long lived outbound connections to new infrastructure
This is where many SIEM platforms look good on paper and fail in practice. If you are missing network context, your C2 detection becomes guesswork.
Elevate Threat Detection and Response with NetWitness® SIEM
-Correlate data across users, logs, and network for unified visibility.
-Detect advanced threats with AI-driven analytics and behavioral insights.
-Accelerate investigations using automated enrichment and guided workflows.

7) Actions on Objectives: tie detections to business impact
What attackers do: exfiltrate data, encrypt systems, manipulate transactions, sabotage operations.
ATT&CK tactics often involved: Exfiltration (TA0010), Impact (TA0040)
SIEM capabilities that matter:
- Data movement visibility, cloud storage logs, DLP signals if available
- Correlation with privilege changes and unusual access paths
- Strong alert prioritization based on asset criticality
Detection examples to map:
- Sudden bulk access to sensitive repositories
- Unusual encryption activity combined with security tool disablement
- Data staging on endpoints followed by outbound transfer
This is where the board cares. Your mapping should show which techniques you can detect early, and which ones you only see at impact. That gap is the real story.
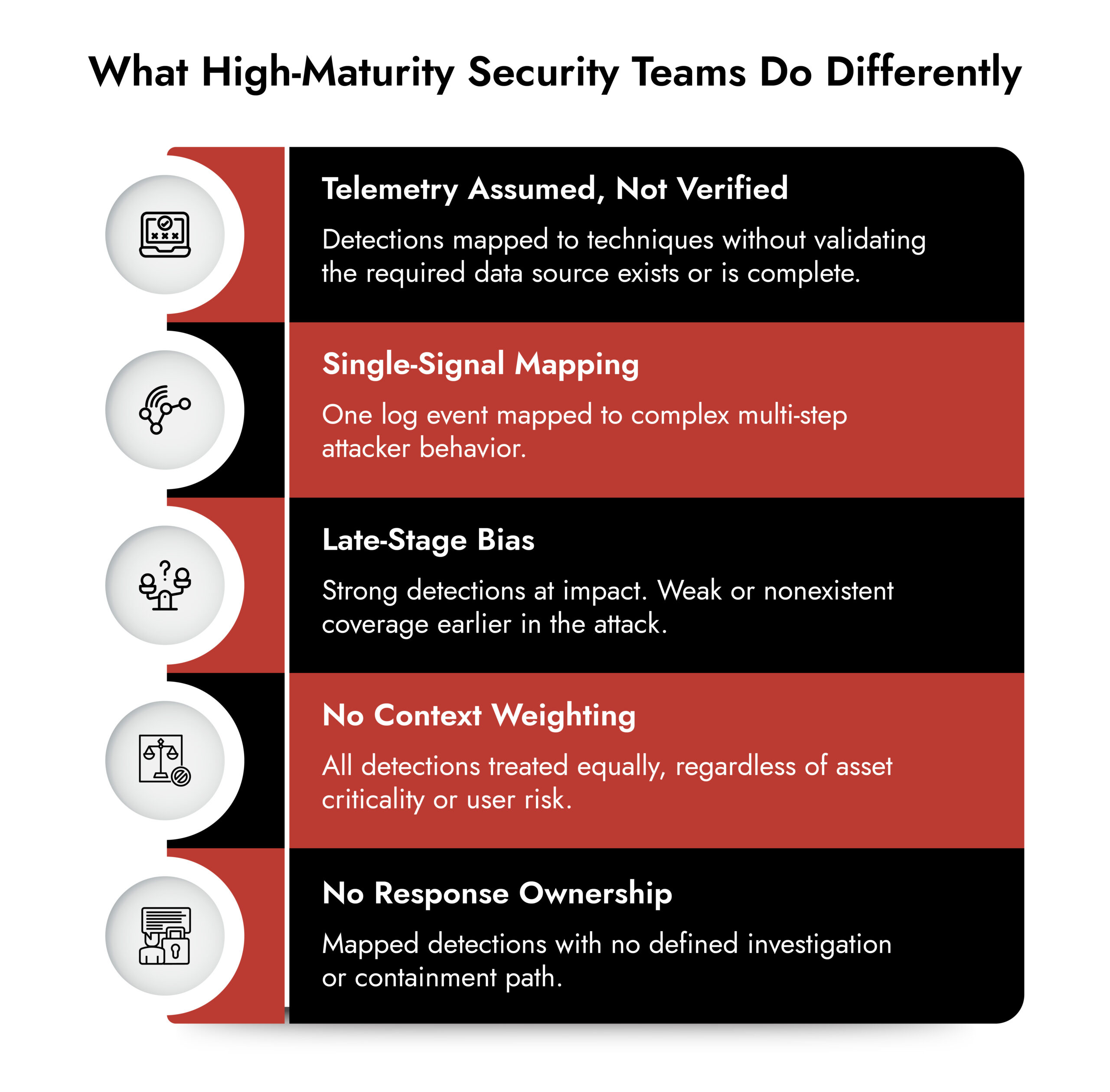
How to build an ATT&CK coverage matrix that actually improves outcomes
Here’s a practical workflow SOC teams can run in weeks, not quarters.
Step 1: Inventory detections as they exist today
Export every rule, correlation, analytic, and high-confidence hunt query. Include source, owner, severity logic, and dependencies.
Step 2: Map each detection to ATT&CK technique IDs
One detection can map to multiple techniques, but be conservative. If it is “suspicious PowerShell,” do not map it to half the framework. Map what you can prove.
Step 3: Attach telemetry requirements
For each mapped technique, document required sources:
- Endpoint
- Identity
- Cloud
- Network
- Application logs
This step exposes SIEM capability gaps instantly.
Step 4: Score coverage quality
Use a simple 0–3 scale:
- 0: no visibility
- 1: partial visibility, low confidence
- 2: reliable detection, needs tuning
- 3: high confidence with response playbook
Step 5: Align to the kill chain and prioritize earlier disruption
If you only have strong coverage at impact, your maturity is lower than you think. Move detections earlier by adding missing telemetry and improving correlation.
Step 6: Operationalize it in weekly cadence
ATT&CK mapping is not a one-time exercise. Every new integration, new environment, and new threat needs updates.
This is how you turn ATT&CK mapping into SOC maturity, not a slide deck.
What to look for when evaluating a SIEM platform for ATT&CK-driven detection
If you are buying or modernizing a security incident and event management stack, evaluate whether the SIEM platform can:
- Ingest and normalize at scale without breaking fields and context
- Correlate across endpoint, network, identity, and cloud in one investigation path
- Provide flexible detection engineering workflows
- Support ATT&CK tagging and reporting so coverage is measurable
- Speed up investigation with session timelines and entity pivots
- Automate response actions or integrate cleanly with SOAR security
Most vendors will say yes. Your proof is whether they can demonstrate detections mapped to MITRE ATT&CK across the kill chain using your real telemetry patterns.
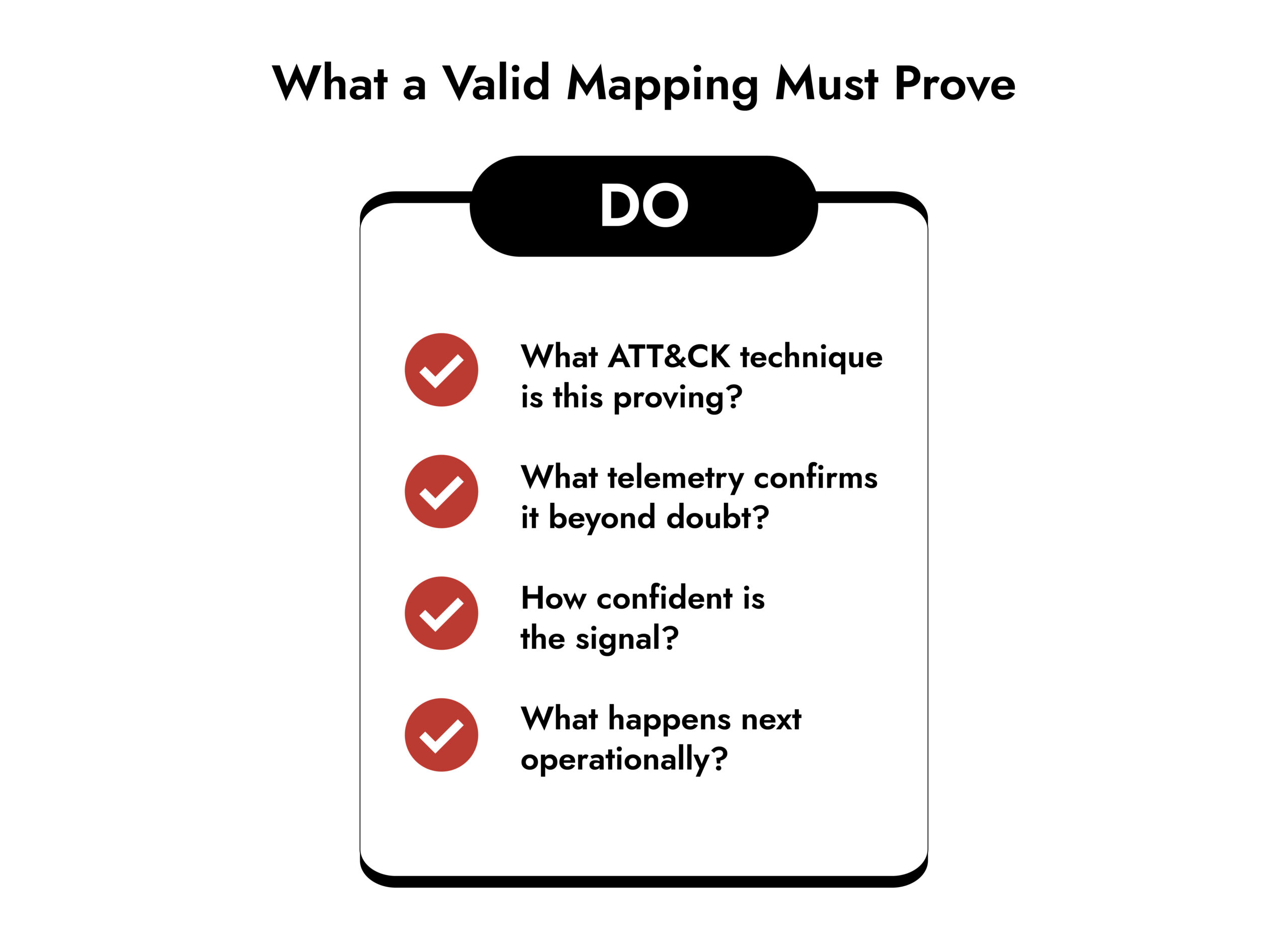
Conclusion: turn mapping into measurable threat detection
ATT&CK mapping is not about compliance. It is a forcing function.
It forces you to define your SIEM capabilities in terms of what attackers actually do. It forces clarity about telemetry, detection logic, and response. And it gives you a defensible way to explain risk reduction, improvements, and gaps in plain language.
If you are operating or evaluating a SIEM platform like NetWitness, the goal is straightforward: unify logs, endpoint, and network context so your threat detection is not a collection of alerts, but a connected story across the entire kill chain. Once you can map that story to the MITRE ATT&CK framework, you can tune faster, respond earlier, and mature your SOC with evidence instead of assumptions.
Frequently Asked Questions
1. Why is MITRE ATT&CK important for SIEM detection? IEM?
Because it turns detection into a measurable capability. Instead of saying your SIEM detects threats, you can show which attacker techniques you can detect, what telemetry supports it, and where you have gaps.
2. Can SIEM detect early-stage attacks using ATT&CK mapping?
Yes, if the SIEM has the right visibility and correlation. ATT&CK mapping helps you prioritize early-stage techniques like initial access, execution, and persistence, then build detections that connect email, identity, endpoint, and network signals.
3. How does ATT&CK mapping improve SOC maturity?
It improves maturity by making coverage explicit, repeatable, and improvable. Teams stop arguing about alert counts and start managing detection quality, response speed, and coverage depth across the kill chain.
4. What tools help map SIEM detections to MITRE ATT&CK?
Most mature SIEM platforms support ATT&CK tagging and reporting directly or through integrations. Teams also use detection engineering workflows, coverage matrices, and purple team validation to confirm mappings and reduce false confidence.
5. How does SIEM support detection across the cyber kill chain?
A strong SIEM supports detection across the kill chain by correlating signals at each stage: recon and delivery through identity, email, and web logs; exploitation and persistence through endpoint telemetry; C2 through network and DNS analytics; and impact through data movement and behavior patterns tied to critical assets.
FIN13: Inside a Fintech Cyber Attack
FIN13 is one of today’s most disruptive threat groups targeting fintech organizations with precision and persistence. This whitepaper breaks down their full attack chain—from reconnaissance and credential theft to lateral movement, data exfiltration, and evasion techniques. Gain insights into their TTPs, discover detection opportunities across the kill chain, and learn how NetWitness empowers faster response and mitigation.






