What is SOAR in cyber security?
SOAR stands for Security Orchestration, Automation, and Response. SOAR solution provides comprehensive SOAR security orchestration and automation to improve your organization’s security operations center’s efficiency and effectiveness. SOAR cyber security gives an enhanced threat visibility into security threats and helps security operations teams manage and respond to cyber threats more efficiently.
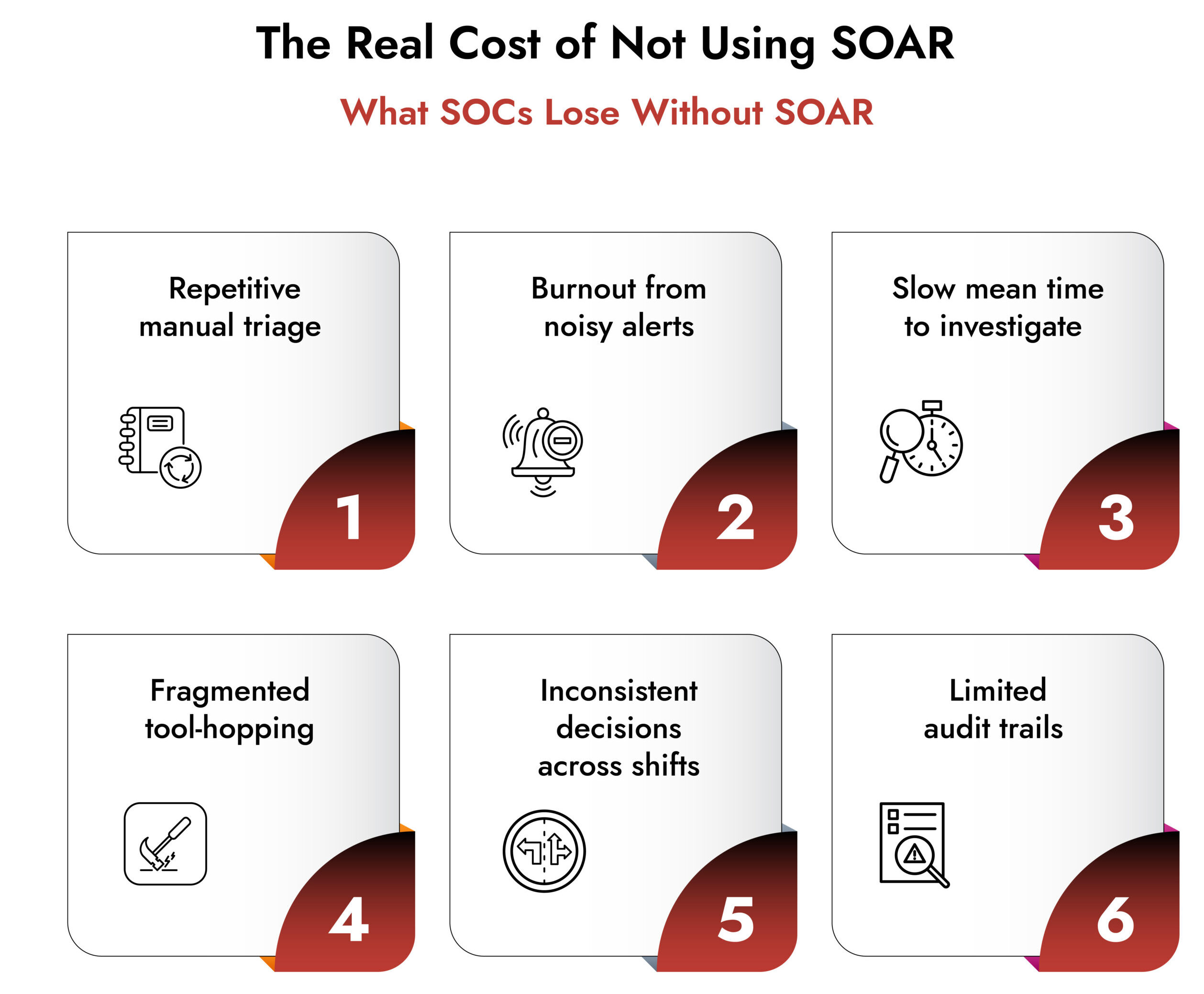
Security teams today are stuck in a strange place. The threat landscape keeps expanding, but the tools meant to protect organizations often work in isolation. Analysts jump between consoles, copy data by hand, chase false positives and try to piece together incidents without a unified picture. It’s slow, exhausting and risky.
This is where SOAR steps in.
Security Orchestration, Automation and Response have become the backbone of modern cyber security operations. Instead of adding yet another platform to the stack, SOAR brings everything together. Alerts, workflows, threat intel and response actions all flow through one system that helps analysts move faster and think clearly.
If you’ve ever wondered how SOCs reach higher speeds without burning out their teams, the answer almost always involves SOAR.
How SOAR Works ?
1. Security Orchestration:
Security orchestration brings many security tools, processes, and technology into a coherent workflow to empower businesses to quickly identify potential threats and respond to them swiftly.
2. Automation:
Automation is an integral part of any modern security strategy. It helps minimize frequent manual tasks undertaken during an incident response, such as following specific steps in a specific order for any given SOAR use case. Automation also helps reduce human error by ensuring that tasks are completed consistently and accurately every time. By automating routine tasks, businesses can free up resources to focus on more complex tasks such as threat analysis and incident triage and forensics.
3. Response:
When a cyber-attack occurs, it is essential to have a detailed plan of action in place so that you can respond swiftly and effectively. A well-defined response plan should include steps such as isolating affected systems, restoring backups, conducting forensic investigations into the incident, establishing communication channels with stakeholders, monitoring systems for further activity or intrusion attempts, updating policies and procedures to improve response time and even prevent future incidents from occurring, and more. Having a detailed response plan in place before an attack occurs ensures that you are prepared for any eventuality and can effectively mitigate damage from any attacks or intrusions.
Security orchestration, automation, and response are essential components of any strong cybersecurity strategy. By leveraging these elements together in an integrated platform, businesses can ensure their networks remain secure against potential threats while minimizing manual labor required for maintenance or operational activities, as well as activities carried out during an attack.
Benefits of Using SOAR Solution Security
1. Improved Efficiency:
Perhaps the most obvious benefit of using SOAR in cyber security is improved efficiency. By automating certain tasks related to incident response, organizations can reduce the amount of time spent on mundane activities such as logging data or reporting incidents. This allows organizations to focus more resources on responding quickly and effectively to potential threats. Additionally, by automating these processes, it reduces the chances of human error, which could lead to costly mistakes or even data breaches down the line.
2. Improved Visibility:
Another benefit of using SOAR in cyber security is improved visibility into your organization’s cybersecurity posture. By automating certain processes related to threat detection and response, you can gain better insight into how your organization is responding and what areas need improvement. This allows you to take proactive steps towards improving your cybersecurity posture before a potential breach occurs rather than waiting until after an incident has occurred.
3. Informed Decisions:
Finally, with better visibility into your organization’s cybersecurity posture, you can make more informed decisions when it comes time to invest resources into new technologies or services that will help improve your overall security posture. That way you can help protect your business from ever-evolving threats.
In summary, using a SOAR system provides numerous benefits for organizations looking for ways to improve their cybersecurity posture without sacrificing efficiency or visibility into their operations. By automating certain tasks related to threat detection and response, organizations can ensure that they are able to respond quickly and efficiently while gaining better insight into their operations at the same time.
Advantages of SOAR Solution
SOAR security is an increasingly popular cybersecurity technology that offers several advantages over traditional security solutions. SOAR is a technology platform designed to help organizations quickly detect, respond to, and remediate cyber threats. It provides the ability to automate manual processes for a more efficient incident response. Below we will discuss some of the key advantages of using the best SOAR tools in your organization’s cybersecurity strategy.
1. Automation to Enhance Efficiency and Productivity:
One of the major benefits of SOAR security orchestration is its ability to automate manual processes. This can save time and money by freeing up resources from mundane tasks, allowing them to focus on more complex security issues.
2. Easy Integration With Existing Systems and Platforms:
SOAR security is designed to be easily integrated with existing security systems and platforms, such as SIEMs, firewalls, endpoint protection solutions, threat intelligence platforms, and more. This can provide visibility into threats detected across multiple systems in real time.
3. Faster Incident Response Times:
Security Orchestration Automation and Response can help organizations to reduce their incident response times. By automating manual processes and orchestrating responses to complex security threats, SOAR security can help organizations reduce the time required for investigation and resolution.
4. Keeps You Compliant:
Finally, using the best security orchestration tools for security operations helps demonstrate compliance with regulatory mandates and standards. By automating manual processes, organizations can quickly show that they are taking all necessary steps to protect their data and systems from potential cyber threats.
Disadvantages of Doing SOAR Security Yourself
SOAR security is a crucial component of any organization’s cyber defense strategy. It allows companies to automate response to security threats, making it easier for them to protect their systems and data from malicious actors. However, while security automation and orchestration tools can be an effective tool in the fight against cybercrime, its implementation can be difficult and costly if done independently. Below we will look at some of the potential disadvantages of doing your own SOAR security instead of outsourcing it to an experienced provider. We will also discuss how you can ensure that your organization gets the most out of its SOAR solution by working with a reliable partner who knows what they’re doing.
1. Costly Setup Process:
SOAR security implementation can be a costly and complicated process, from developing policies to integrating with existing systems. If you’re not careful, it can take months or even years to get everything up and running properly. This means that the cost of implementing SOAR solution yourself can quickly add up if you do not have access to the right resources or expertise.
Also, you will have to employ and vet an in-house staff to maintain this security measure which is something that you may not fully understand enough to hire the right person(s). New employees will need training, and if they’re entry level, they may not know where to start with SOAR solution. Finding the right professionals can be a difficult task that could be made easier by outsourcing your SOAR security.
2. Integration Can Be Challenging:
SOAR in cybersecurity is well known for its ability to integrate between platforms and while that is convenient, it can be difficult to implement. If you do not have the right technicians that know how to set it up and integrate it with your system, it might be easier to have a professional cybersecurity team take on SOAR security for your company.
3. Finding Your Weaknesses:
Implementing security orchestration automation and response is one thing, but finding the weak spots in your company’s defenses is another. You have to optimize your security posture which SOAR by itself doesn’t do. Often a business that manages their own cybersecurity focuses too much on detection and prevention, and not enough on the foundation of building a strong defense system.
SOAR security implementation can be a costly and complex process, but one that can be invaluable for organizations looking to protect their systems from malicious actors. However, without the right resources or expertise, it can be difficult to ensure that your organization gets the most out of its solution. This is why it is important to work with an experienced partner who knows how to set up and maintain SOAR security in order to maximize effectiveness while minimizing risk. By leveraging the power of SOAR solutions and working alongside experts, you can rest assured knowing your data will remain safe and secure.
Establish Incident Response consistency, speed, and scale with NetWitness® Orchestrator
– Comprehensive security operation and automation technology
– Leveraged playbooks and integrated threat intelligence to automates analyst workflow
– Integrates NetWitness Platform XDR and security operations team’s entire security arsenal

What Does SOAR in Cyber Security Protect Against?
In today’s digital world, cyber threats are something that all computer users must be aware of. From identity theft to ransomware, there is no shortage of threat actors out there looking for vulnerable systems. It is important to understand what these threats are so that you can protect yourself and your data from harm. Let us take a look at some of the most common types of cyber threats.
1. Malware:
Malware is short for “malicious software,” and it refers to any kind of program or code designed to cause damage, steal data, or otherwise disrupt a system. There are many different types of malware out there, including viruses, worms, trojans, rootkits, spyware, adware, and ransomware. Each type has its own unique characteristics and methods of attack. However, they all have one thing in common — their purpose is malicious in nature. When malware is present, SOAR can initiate an automated triage process based on aggregation of alerts generated by your detection and response tools.
2. Phishing Scams:
Phishing scams refer to attempts by criminals to obtain sensitive information such as usernames, passwords, and credit card details by disguising themselves as trustworthy entities in electronic communication. Phishing scams often take the form of fake emails or websites that appear legitimate but are actually designed to steal confidential information from victims. The best way to protect yourself from phishing scams is to never give out personal information online unless you are certain it is coming from a legitimate source. By aggregating alerts and other details from your existing security technology stack, SOAR can launch a predefined workflow when a phishing scam is detected to guide the responder to a faster resolution.
3. Insecure Networks:
Insecure networks can leave your computer vulnerable to attack by hackers or other malicious actors. It is important to make sure your business network (both wired and wireless) is secure and up to date with the latest security patches and settings to protect against potential attacks. Additionally, be sure not to connect your devices (such as laptops or mobile phones) to public Wi-Fi networks without using a VPN service first — this will help keep your data safe from prying eyes.
4. Ransomware Attacks:
Ransomware is a type of malicious software that locks the user out of their device and demands payment to regain access. It can be spread through email attachments, fake downloads, or other sources — and once installed, it will encrypt all the data on your computer until you pay a ransom. Protect yourself from ransomware by ensuring your system is up to date with the latest security patches and using an antivirus solution. Implementing SOAR can improve threat detection and incident response times.
5. Distributed Denial of Service (DDoS):
Distributed denial of service attacks is a type of attack where malicious actors send large amounts of traffic to your website or server in order to overwhelm it and make it unavailable. These types of attacks can have serious repercussions for businesses, as they can result in lost revenue due to downtime. The best way to protect yourself from DDoS attacks is by using SOAR security. SOAR security provides automated workflows to identify and triage DDoS attacks, empowering your team to quickly react to the threat in order to minimize any damage done. By using SOAR security, you can ensure your networks and systems are better protected from potentially devastating DDoS attacks.
6. Corporate Account Takeover (CATO):
Corporate account takeover (CATO) is a type of attack where malicious actors gain access to corporate accounts and use them for their own purposes. CATO attacks can have serious consequences, including financial loss, data theft, and reputational damage. To protect against CATO attacks, businesses should always ensure that their employees are using strong passwords and two-factor authentication for all corporate accounts. Additionally, businesses should regularly monitor their accounts for any suspicious activity and take steps to ensure that only authorized personnel have access to sensitive data. And ideally, you will have any response procedures fully defined and automated to improve response time. Or you can leave the automation to SOAR security.
By following best practices such as using strong passwords, implementing two-factor authentication, and utilizing security orchestration automation and response security, businesses can better protect themselves from malicious attacks. Additionally, businesses should ensure their employees are educated on the risks posed by cyber-attacks and the steps necessary to protect themselves from them. With these steps in place, businesses can help ensure that their data and systems remain secure.
Implementing Security Orchestration Automation and Response (SOAR) Security
In the ever-evolving world of cyber security, one of the latest developments is the SOAR security system. This system helps businesses quickly and effectively respond to security incidents with minimal disruption. To ensure that your business is well protected and up to date, here are the requirements for setting up a SOAR security system.
1. Integration of Existing Security Tools:
In the ever-evolving world of cyber security, one of the latest developments is the SOAR system. This system helps businesses quickly and effectively respond to security incidents with minimal disruption. To ensure that your business is well protected and up to date, here are the requirements for setting up a SOAR security system:
2. Advanced Automation Capabilities
Another key requirement for a successful SOAR security implementation is advanced automation capabilities. The goal here is to automate as much of the response process as possible so that your organization can respond quickly in the event of an attack without having to manually go through every step of the process. By automating certain processes, such as alerting team members when an incident occurs and providing them with a runbook of steps to be taken, you can drastically reduce response times and minimize disruption.
3. Robust Reporting Features:
Finally, it is important that any SOAR software solution platform you implement has robust reporting features so you can track performance over time and make sure that everything is running smoothly. With detailed reports on security response times and remediation efforts, you can easily see which areas need improvement and take action accordingly. Additionally, these reports can be used to demonstrate compliance with industry regulations or standards if needed.
A successful SOAR security implementation requires the integration of existing security tools, advanced automation capabilities, and robust reporting features in order for it to be effective at responding appropriately and quickly before major damage is done. If your business does not currently have a SOAR solution system in place yet — or is not sure how best to set one up — it may be worth consulting with a cyber security specialist who can provide guidance on how best to protect your organization from potential attacks while still meeting industry regulations or standards.
Tips for Finding the Best SOAR Solution
1. Start by Researching Security Companies:
The first step in finding the right SOAR solution vendors is researching potential companies. Start by looking at online reviews and ratings from other customers. These should give you an idea of what kind of services each company offers and how satisfied their customers have been. You can also check out industry forums and blogs to see what people are saying about different providers. This research should give you a good idea of which companies offer the best services for your particular needs.
2. Understand Your Requirements:
Before deciding on the best SOAR solution, it is important to understand your specific requirements so that you can find a company that meets them all. Consider factors such as budget, scalability, and especially compatibility with existing systems, processes or workflows. Make sure you fully understand what kind of service you need from a SOAR solution vendor before making any decisions.
3. Look for Experience:
Experience is key when choosing a SOAR solution vendor, so look for companies that have been in business for several years or more and have worked with multiple clients in various industries. This is very important when you consider the processes your organization has in place when responding to incidents. Be sure to work with a SOAR security provider who can build out runbooks and processes which are not generic but designed specifically for your business. Companies with extensive experience are more likely to provide high-quality services and know exactly how to meet your needs.
Finding the right SOAR security provider does not have to be difficult if you follow these tips. Start by doing research on potential providers, understanding your requirements, and looking for experience in order to make sure you get the most out of your investment. Taking these steps will help ensure that you choose the best possible company for securing your business’s valuable data and systems from cyber threats.
SOAR Security Professionals at NetWitness
In today’s digital age, cyber security is a top priority. To protect your business from the latest threats, you need the industry’s best tools and technologies. That is why NetWitness has become the go-to SOAR solution for many organizations looking to secure their infrastructure. Let us take a look at why NetWitness is such an attractive option for cyber security.
1. Real-time Visibility and Analysis:
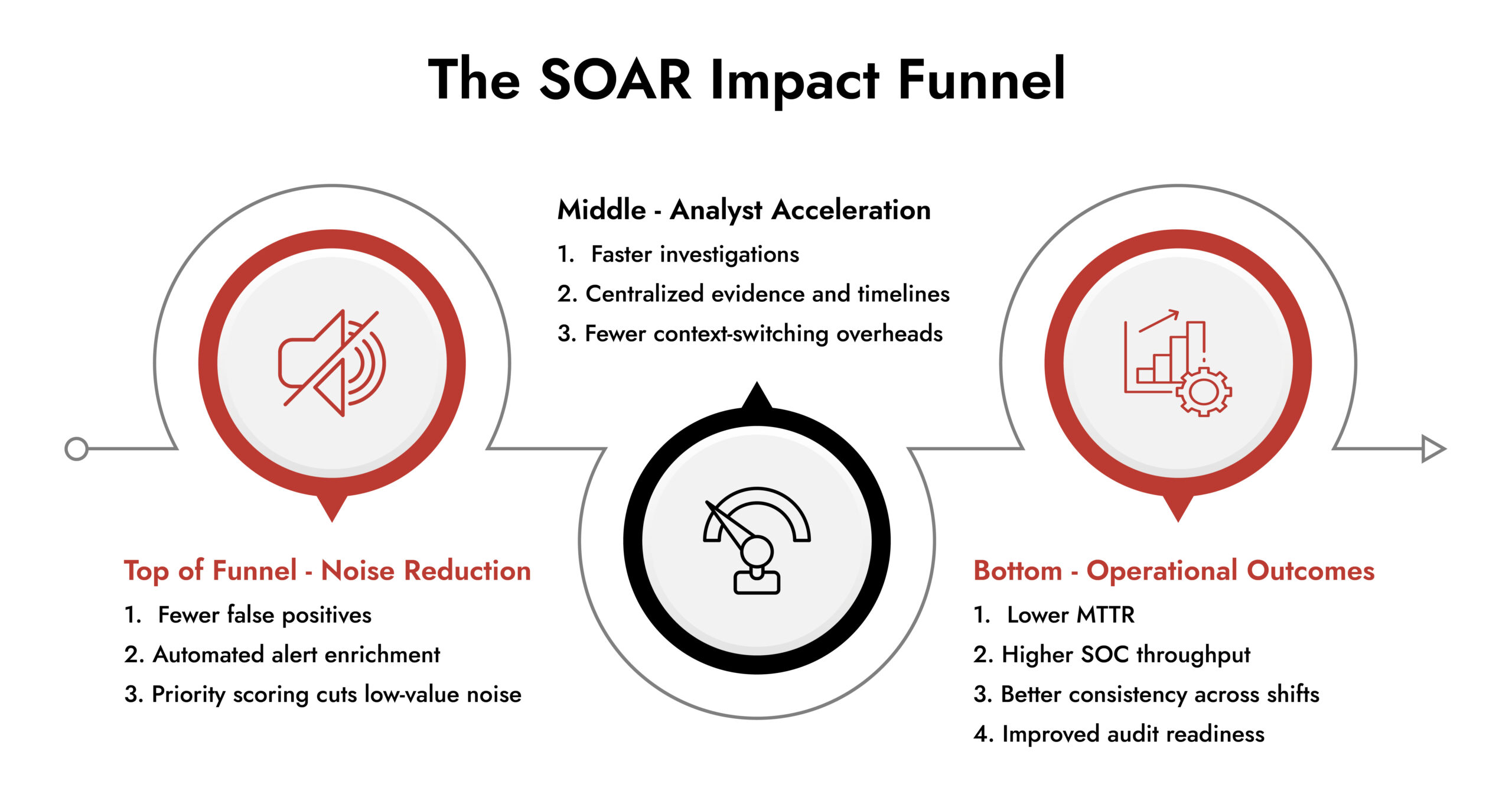
NetWitness provides real-time visibility across multiple networks and devices, giving you greater awareness of potential threats. It does this by collecting data from network traffic, log sources and endpoints and analyzing that data set for malicious activity in real-time. This allows you to quickly detect potential issues before they become serious problems, saving you time and money in the long run.
2. Productive Capabilities:
Our automation system lets our technicians prioritize and investigate threats fast. This allows the team to coordinate faster across the entire security team.
3. Fastest Threat Detection:
With NetWitness at your side, we’re able to detect cybersecurity threats faster and more smoothly than other platforms. And we’re able to view and determine the full scope of the attack so we can help you implement defenses as soon as possible.
4. Proactive Response and Prevention:
NetWitness also helps to proactively recognize and diagnose attacks by using threat intelligence to help identify suspicious indicators of compromise before they become an issue. This helps reduce the chance of experiencing a successful attack on your organization.
5. Threat Hunting and Investigation:
Finally, NetWitness makes it easy to investigate any suspicious activity that has been identified on your network or devices. It provides an intuitive analyst interface and detailed reports so you can quickly identify potential malicious activity or malware within your environment and take action accordingly. This makes it easier than ever before to investigate any potential threats and find out exactly where they originated from, reducing risk to your organization significantly in the process.
Why NetWitness SOAR Stands Out
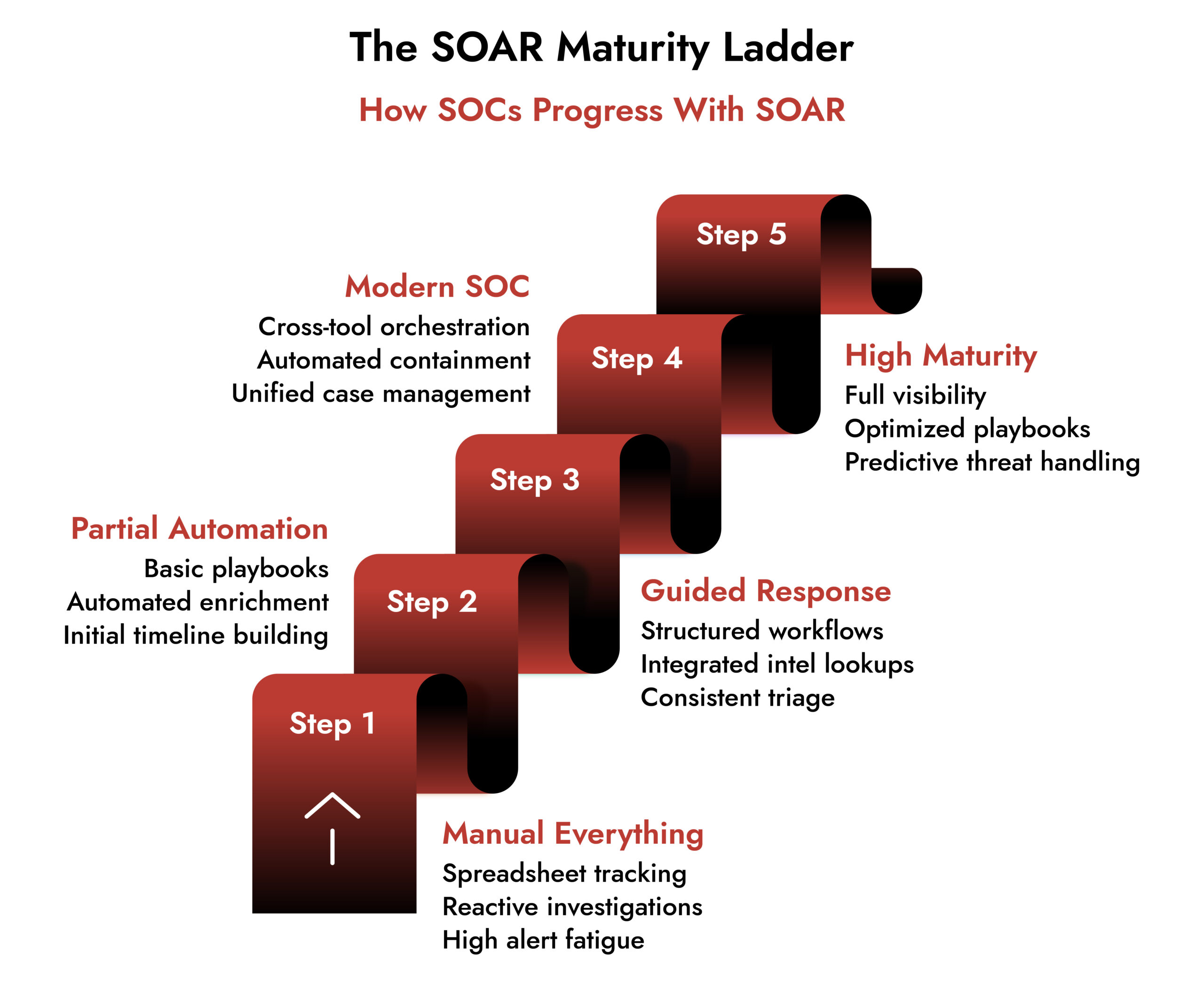
NetWitness SOAR extends the strength of the NetWitness Platform into the orchestration and response layer. It’s designed for SOCs that depend on deep context, accurate investigations and fast decision-making.
- Investigation-First Design: Instead of focusing only on automation, NetWitness SOAR puts investigation quality at the center. Analysts get timelines, context, evidence mapping and clear workflows built for complex incidents.
- Unified Visibility: Because it integrates natively with NetWitness SIEM and NDR, analysts see network, endpoint and log data in one place – a significant advantage during fast-moving investigations.
- Advanced Automation: NetWitness SOAR automates triage, enrichment, escalation, containment and analyst handoffs without sacrificing transparency.
- Playbooks That Improve Analyst Performance: Built-in playbooks bring best practices to the forefront and help analysts stay consistent, especially during high-pressure events.
- Enterprise-Ready Architecture: Designed for large environments, NetWitness SOAR handles scale without slowing down investigations or drowning analysts in noise.
Conclusion
SOAR has become the structural backbone that allows SOCs to move quickly and confidently. Whether your biggest challenge is alert overload, response delays or fragmented tools, SOAR helps bring order to chaos.
If your goal is not just to automate but to investigate smarter, respond faster and elevate your entire security operation, NetWitness SOAR delivers the visibility, workflow discipline and automation depth needed to get there.
Frequently Asked Questions
1. What is a SOAR in cyber security?
In cybersecurity, SOAR (Security Orchestration, Automation, and Response) is a software-based approach that integrates and automates security tools to streamline incident response and improve efficiency. SOAR platforms collect threat data from various sources, automate repetitive security tasks, and orchestrate the coordination of different security technologies to enable faster and more effective mitigation of cyber threats by reducing manual effort from security analysts.
2. What are common SOAR use cases?
Typical SOAR use cases include phishing detection and automated response, malware containment, DDoS attack mitigation, and incident response orchestration.
3. Which are the best SOAR solutions?
The best SOAR solutions like NetWitness provide automation, integration with existing security tools, advanced analytics, and compliance reporting to optimize incident response and security operations.
4. What are SOAR features?
SOAR features include automated playbooks, alert aggregation, threat intelligence integration, and real-time reporting.
Make Way for the Intelligent SOC
– Transform your Security Operations Center with AI-driven intelligence, automation, and context-rich detection to stay ahead of modern threats.
– Learn how to build a next-gen SOC that fuses threat intelligence, behavioral analytics, and orchestration for proactive defense.