What is threat hunting in cyber security?
Threat hunting in cyber security is a proactive threat hunting approach where security teams actively search for hidden threats across networks, systems, and endpoints. Unlike alert-based monitoring, cyber threat hunting focuses on abnormal behavior, network threat monitoring data, and attacker techniques to uncover risks that bypass traditional network security controls.
Introduction
Most attacks do not break in. They blend in.
That is the uncomfortable truth modern security teams live with. Firewalls, IDS, and SIEM alerts catch known patterns, but skilled attackers move slowly, reuse legitimate tools, and stay just quiet enough to avoid detection. By the time an alert fires, damage is often already done.
This is where threat hunting changes the equation.
Network threat hunting is not about reacting faster. It is about assuming compromise, questioning normal, and actively looking for adversaries hiding in plain sight. When done right, it reshapes how teams think about network security, detection coverage, and risk.
We will decode the three core types of threat hunting, explain how they work in real environments, and walk through best practices that separate mature cyber threat hunting programs from checkbox exercises.
What Is Threat Hunting in Cybersecurity?
Threat hunting in cybersecurity is a proactive practice where analysts actively search for threats that have evaded automated defenses. Instead of waiting for alerts, hunters look for weak signals, unusual behaviors, and patterns that do not align with how the network should behave.
What this really means is simple. Detection tools ask, “did something match a rule?” Threat hunters ask, “what should never happen here, even if no rule exists?”
This shift matters because attackers increasingly exploit trusted systems, misconfigurations, and legitimate credentials. According to multiple breach investigations, a large percentage of successful intrusions involve valid accounts and native tools. No alert fires if nothing looks obviously malicious.
Threat hunting fills that gap.
Why Proactive Threat Hunting Matters for Network Security
Network security is no longer just about blocking traffic. It is about understanding behavior across endpoints, users, workloads, and data flows.
Most threats to network security do not announce themselves. They appear as small deviations. A service account logging in at an odd hour. Internal traffic patterns that slowly change. Data moving laterally instead of externally.
Without proactive threat hunting, these signals get buried under normal noise.
Organizations that practice regular threat hunting tend to:
- Reduce dwell time significantly
- Discover misconfigurations before attackers exploit them
- Improve detection rules based on real attacker behavior
- Strengthen overall network management and visibility
Threat hunting turns assumptions into evidence. That alone makes it indispensable.
The 3 Types of Threat Hunting Explained
Threat hunting is not a single technique. It comes in different forms, each answering a different question about risk. Mature programs use all three.
1. Hypothesis-Driven Threat Hunting
This is the most structured form of cyber threat hunting.
Analysts start with a hypothesis based on threat intelligence, past incidents, or known attacker tactics. For example: “An attacker may be using PowerShell for lateral movement without triggering alerts.”
From there, hunters define what data to analyze, what behaviors to look for, and what would confirm or disprove the hypothesis.
This approach works well when teams have:
- Good threat intelligence
- Strong network threat monitoring data
- Clear visibility across endpoints and logs
The strength of hypothesis-driven hunting is focus. You are not boiling the ocean. You are testing specific attacker behaviors against your environment.
The limitation is that it depends on what you already know. If the hypothesis is wrong or incomplete, some threats may still slip through.
2. Intelligence-Driven Threat Hunting
Intelligence-driven hunting starts outside your network.
Here, hunters use external threat intelligence such as attacker techniques, malware families, and active campaigns to guide their searches. If intelligence reports show increased abuse of VPN appliances or credential stuffing attacks, hunters pivot their analysis accordingly.
This type of threat hunting helps bridge the gap between global threats and local exposure.
It is especially valuable for network security teams managing large or distributed environments, where new threats emerge faster than internal rules can adapt.
The key advantage is relevance. You are hunting for what is actually happening in the wild, not theoretical risks.
The challenge lies in context. Raw intelligence without strong network management and telemetry can lead to false assumptions. Intelligence must be translated into environment-specific behaviors to be effective.
3. Anomaly-Based Threat Hunting
This is the most exploratory and data-heavy approach.
Anomaly-based threat hunting focuses on deviations from normal behavior. Instead of asking “is this known bad?” hunters ask, “why is this different?”
Examples include:
- Unusual east-west traffic inside the network
- Rare process executions on critical servers
- Unexpected authentication paths or privilege escalations
This type of network threat hunting relies heavily on baselining, historical data, and strong analytics.
Its biggest strength is discovery. It can uncover novel attacks, insider threats, and misconfigurations that no intelligence feed will ever flag.
The tradeoff is effort. Anomaly-based hunting requires mature data collection, good statistical understanding, and analysts who can separate signal from noise without chasing ghosts.
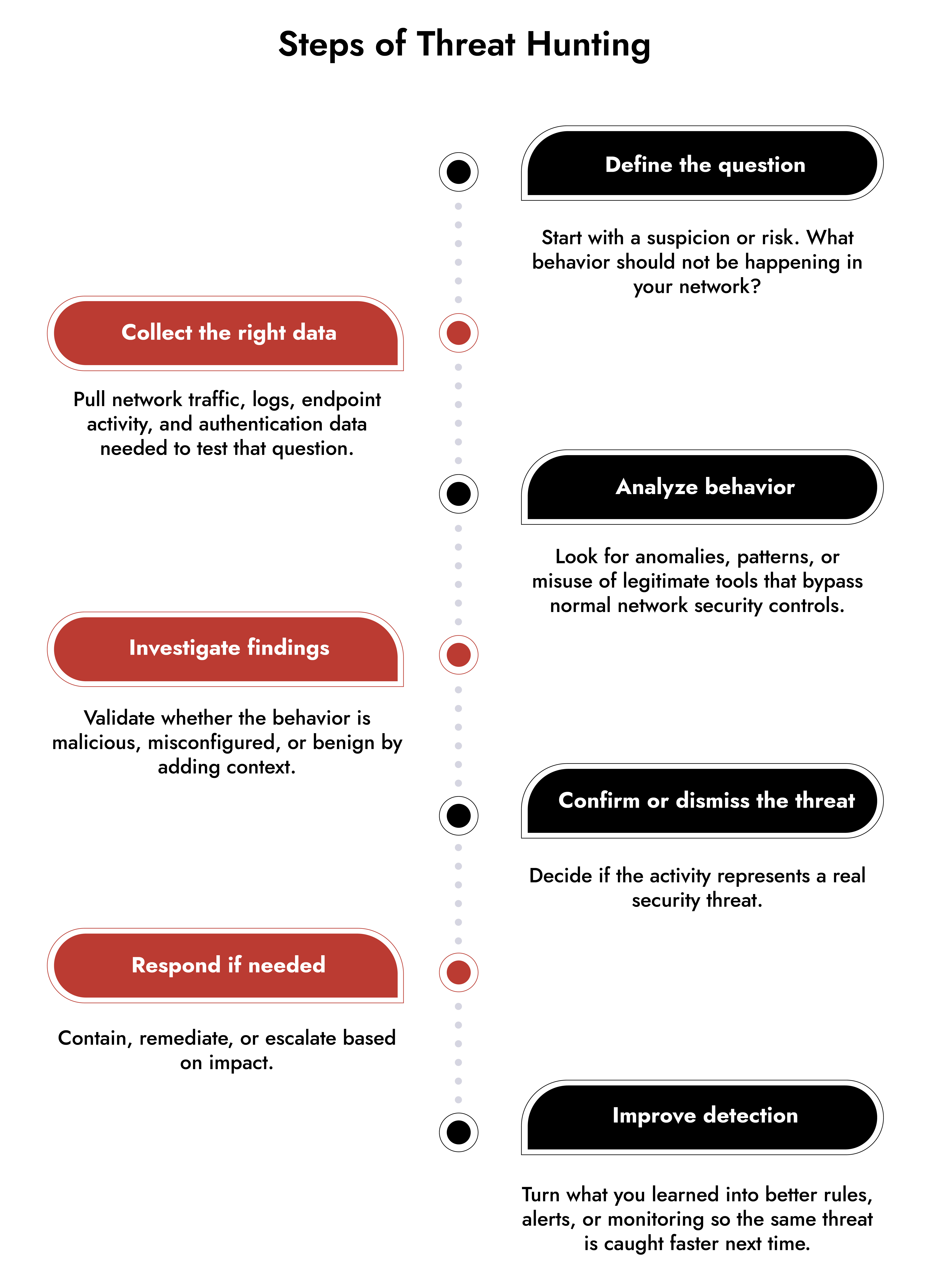
How Network Threat Hunting Fits Into Network Management
Threat hunting does not replace traditional network management. It enhances it.
Effective network management focuses on availability, performance, and configuration. Threat hunting overlays a security lens on top of that foundation. It asks how attackers might abuse what network teams already manage.
For example:
- Network segmentation becomes a hunting surface for lateral movement
- Traffic baselines support anomaly-based hunting
- Configuration data exposes weak points attackers love
When network and security teams collaborate, threat hunting becomes faster, more accurate, and far more actionable.
Strengthen Network Visibility with NetWitness® Network Traffic Security Assessment
-Uncover hidden threats through deep packet inspection and analytics.
-Identify vulnerabilities and blind spots before they’re exploited.
-Enhance detection and response with NDR-driven intelligence.

Critical Best Practices for Effective Threat Hunting
Many organizations claim to do threat hunting. Few do it well.
These best practices make a difference.
Start With Visibility, Not Tools
Threat hunting fails without data. Period.
Before investing in hunting workflows, ensure visibility across:
- Authentication events
- Endpoint activity
- Cloud and IoT assets where applicable
Network threat monitoring should feed hunters with high-quality, normalized data. Partial visibility leads to partial conclusions.
Define Clear Hunting Objectives
Random hunting wastes time.
Each hunt should answer a question tied to real risk. Are you validating detection coverage? Searching for specific attacker behavior? Testing assumptions about network security controls?
Clear objectives keep hunts focused and measurable.
Document and Operationalize Findings
A hunt that finds nothing still has value if documented properly.
Every hunt should produce:
- New detection logic
- Improved baselines
- Updated hypotheses
- Insights into network weaknesses
This is how proactive threat hunting compounds over time.
Integrate Threat Hunting with Detection and Response
Threat hunting should not live in isolation.
Findings must feed SIEM rules, SOAR playbooks, and incident response processes. Otherwise, teams will keep rediscovering the same issues.
The goal is to hunt once and detect forever.
Build Analyst Skills, Not Just Dashboards
Tools help. People matter more.
Strong threat hunters understand attacker behavior, network protocols, and how real environments operate. Investing in training and cross-team collaboration often delivers more value than adding another platform.
Advantages of Cyber Security Threat Hunting
When threat hunting is done consistently, the benefits stack up fast.
Organizations gain:
- Faster detection of stealthy threats
- Reduced attacker dwell time
- Improved confidence in network security posture
- Better alignment between security and network management teams
- Fewer surprises during incident response
In short, cyber security threat hunting turns unknown risk into known risk. That alone changes how leaders think about security maturity.
Advanced Threat Detection and Protection with NetWitness
Threat hunting only works when hunters have visibility, context, and the ability to pivot fast. This is where many programs stall. Data exists, but it is fragmented. Signals are there, but they lack narrative.
NetWitness is built to support proactive threat hunting at scale by unifying network, endpoint, log, and cloud telemetry into a single investigative layer. Instead of chasing alerts across disconnected tools, analysts can follow attacker behavior end– to– end.
For network threat hunting, NetWitness provides deep packet inspection and metadata analysis that exposes lateral movement, command-and-control activity, and abnormal internal traffic patterns. This is critical for identifying threats that bypass perimeter defenses and blend into normal network operations.
From a cyber threat hunting perspective, NetWitness enables hypothesis-driven and anomaly-based hunts by allowing analysts to pivot across sessions, users, hosts, and applications in real time. Hunters can test assumptions, validate intelligence, and uncover stealthy behaviors without waiting for predefined alerts.
NetWitness also strengthens network threat monitoring by continuously analyzing traffic and activity against known attacker techniques while preserving the flexibility to explore unknown threats. This balance between automated detection and human-led investigation is what makes threat hunting sustainable over time.
For security teams managing complex environments, NetWitness bridges the gap between network management and security operations, turning raw data into actionable insight.
Conclusion
Here’s the thing. Threat hunting is not about finding more alerts. It is about finding the right questions.
Decoding the three types of threat hunting makes one thing clear. There is no single approach that works everywhere. Hypothesis-driven hunting brings focus. Intelligence-driven hunting brings relevance. Anomaly-based hunting brings discovery. Together, they form a complete strategy for modern network security.
But tools and techniques alone are not enough. Effective threat hunting depends on visibility, disciplined processes, and analysts who understand how attackers actually operate inside networks. When proactive threat hunting becomes part of daily operations, security teams stop reacting to incidents and start shaping outcomes.
In a world where attackers move quietly and patiently, the advantage belongs to organizations that hunt first.
Frequently Asked Questions
1. What tools are essential for threat hunting in cyber security?
Essential tools include network traffic analysis platforms, endpoint detection and response tools, centralized log management, and analytics platforms that support advanced queries. The most important factor is not the tool itself, but whether it provides reliable visibility and historical data to support threat hunting workflows.
2. How to choose a network threat hunting platform for mid-sized companies?
Mid-sized companies should prioritize platforms that offer strong network threat monitoring, easy data integration, and manageable operational overhead. Look for solutions that balance depth of visibility with simplicity, so small teams can hunt effectively without needing dedicated data engineers.
3. What are the advantages of cyber security threat hunting?
Cyber security threat hunting helps organizations detect threats that bypass automated controls, reduce dwell time, validate security assumptions, and improve detection logic. Over time, it strengthens overall network security and reduces reliance on reactive alerts.
4. What is threat hunting in cyber security?
Threat hunting in cyber security is a proactive approach where analysts actively search for hidden threats within an environment. It focuses on identifying abnormal or suspicious behavior rather than waiting for alerts triggered by known indicators.
5. Is cyber threat hunting a realistic practice with the IoT?
Yes, but it requires adjusted expectations. IoT environments generate unique traffic patterns and often lack traditional agents. Effective cyber threat hunting in IoT-heavy networks relies on strong network visibility, behavior baselining, and network-level analytics rather than endpoint-based controls.
Proactive Network Threat Detection with NetWitness® NDR
-Spot threats fast with AI-driven analytics.
-See everything across your network and cloud traffic.
-Investigate efficiently with built-in forensic tools.
-Adapt and scale to meet growing security needs.






