What are the essential features of a Modern SOAR platform?
- A modern SOAR platform is built on five core capabilities: automated playbooks, centralized case management, integrated threat intelligence, real-time collaboration, and actionable analytics. These features work together to help security teams cut down response times, reduce manual effort, and improve investigation quality.
- While most SOAR solutions cover the basics, platforms like NetWitness SOAR push these capabilities further with deeper automation, unified investigation workflows, richer intelligence context, and flexible customization options. This gives SOC teams clearer visibility, faster decision-making, and stronger operational resilience.
The Problem That SOAR Tools Solve
The security teams are drowning in a sea of alerts, tools and manual triage, and even the best skilled SOC teams are struggling to keep up with response times. That’s where SOAR tools comes in the answer to the chaotic security landscape.
SOAR tools brings order to chaos by connecting all the existing security tools, automating the boring stuff and letting the analysts focus on the real threats. But the question isn’t really whether or not an organization needs SOAR, it’s which features really matter.
Let’s take a closer look at the top five features of a top-notch SOAR solution that will give SOCs a solid edge over the rest.
Top 5 SOAR Tools_’ Features That’ll Save Your SOC
1. Playbook Automation:
A SOAR platform is essentially useless if it can’t automate playbooks and that’s because playbooks are the heart of the SOC response. They define the workflow that the team follows every time a security incident occurs – from blocking malicious IPs to quarantining endpoints with no option of manual intervention.
Think about it, every second saved during an incident can literally be the difference between data loss and a quick fix. And that’s exactly what playbooks do – they codify the best practices so that SOCs respond consistently, regardless of who’s shifting.
SOAR security solution brings a few clear advantages to the table:
- It takes the repetitive work off your analysts so they can focus on real investigations.
- It cuts down the mistakes that slip in when everything is done manually.
- It ensures every incident is handled the same way every time.
- It lets your team handle more volume without adding headcounts.

2. Centralized Case Management:
SOAR solutions should be able to handle the actual workflows of the SOC, not just automate the repetitive tasks. Centralized case management does that and that means that you can manage all your incident data, context and workflow in one console.
That sounds simple, but it’s a total game-changer for your SOC. You no longer have to juggle multiple tools or lose context between systems. Everything stays linked to a single case ID, and that means that your analysts can get on with what they do best – investigating security threats.
This is huge for collaboration, accountability and compliance reporting too:
- You get streamlined collaboration across your team.
- You get a full audit trail for compliance reporting.
- You get integrated ticketing and escalation.
- And you get cross-team visibility across incidents.
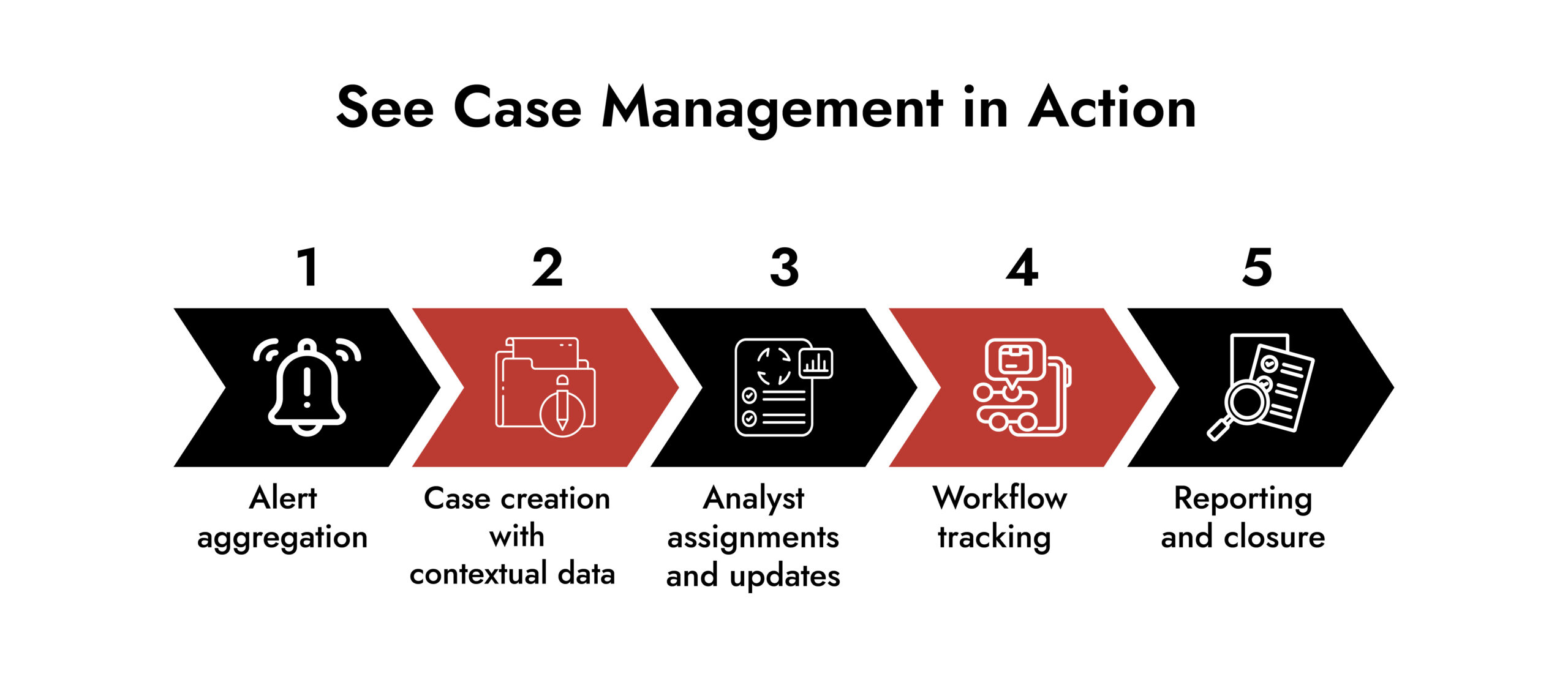
3. Threat Intelligence Integration:
The thing is that threat intelligence integration is what turns your SOAR solution into a real powerhouse. When you integrate threat intelligence feeds, you get real-time indicators of compromise (IOCs) and reputation data, which means that you can enrich your alerts and separate signals from noise.
That means that every action your SOAR takes is now data-driven, not just guesswork. You get to automate correlation between inbound alerts and known malicious actors or campaigns, which means that you can cut down on false positives and improve threat prioritization.
That’s huge for your SOC and for your bottom line:
- You get faster triage with enriched context.
- You get improved detection accuracy.
- You get a unified view of the threat landscape.
- You get adaptive response playbooks based on the latest intel.

4. Real-Time Collaboration and Workflow Orchestration:
Your SOAR solution isn’t just about automation, it’s also about orchestration. That means that it needs to be able to orchestrate all your security tools – from firewalls and EDRs to incident response platforms, so that they all act in sync.
And that means that you need real-time collaboration and workflow orchestration – which is exactly what your SOAR solution should provide. This lets your analysts comment, assign and approve actions directly within the platform, so that the entire workflow is logged and traceable.
That’s huge for your SOC and for your confidence:
- You get to reduce communication lag during critical incidents.
- You get to improve response coordination across security tiers.
- You get to enhance auditability and knowledge sharing, which strengthens decision-making by sharing the same frame of reference.
A well-oiled machine of a response environment turns separate tools into a cohesive, smoothly running SOC ecosystem.
Establish Incident Response consistency, speed, and scale with NetWitness® Orchestrator

5. Performance Analytics and Continuous Improvement:
The top SOAR software solutions come with analytics dashboards that look at performance metrics – mean time to detect (MTTD), mean time to respond (MTTR), and automation coverage. These dashboards take raw activity data and turn it into real insight for your security team.
They can identify where things are getting clogged up, make adjustments to playbooks, and measure the return on investment, essentially doing their job a whole lot better. At the end of the day, analytics ensure your SOAR in cybersecurity isn’t static, it’s always changing, adapting as threats and workflows change.
Key metrics to keep an eye on:
- What’s the incident volume by type and source?
- How well is the automation working?
- How are the analysts’ workloads distributed?
- What’s the pattern in response times over time?
By combining analytics with automation, SOCs start to learn, move faster, and always stay on the ball in terms of resilience.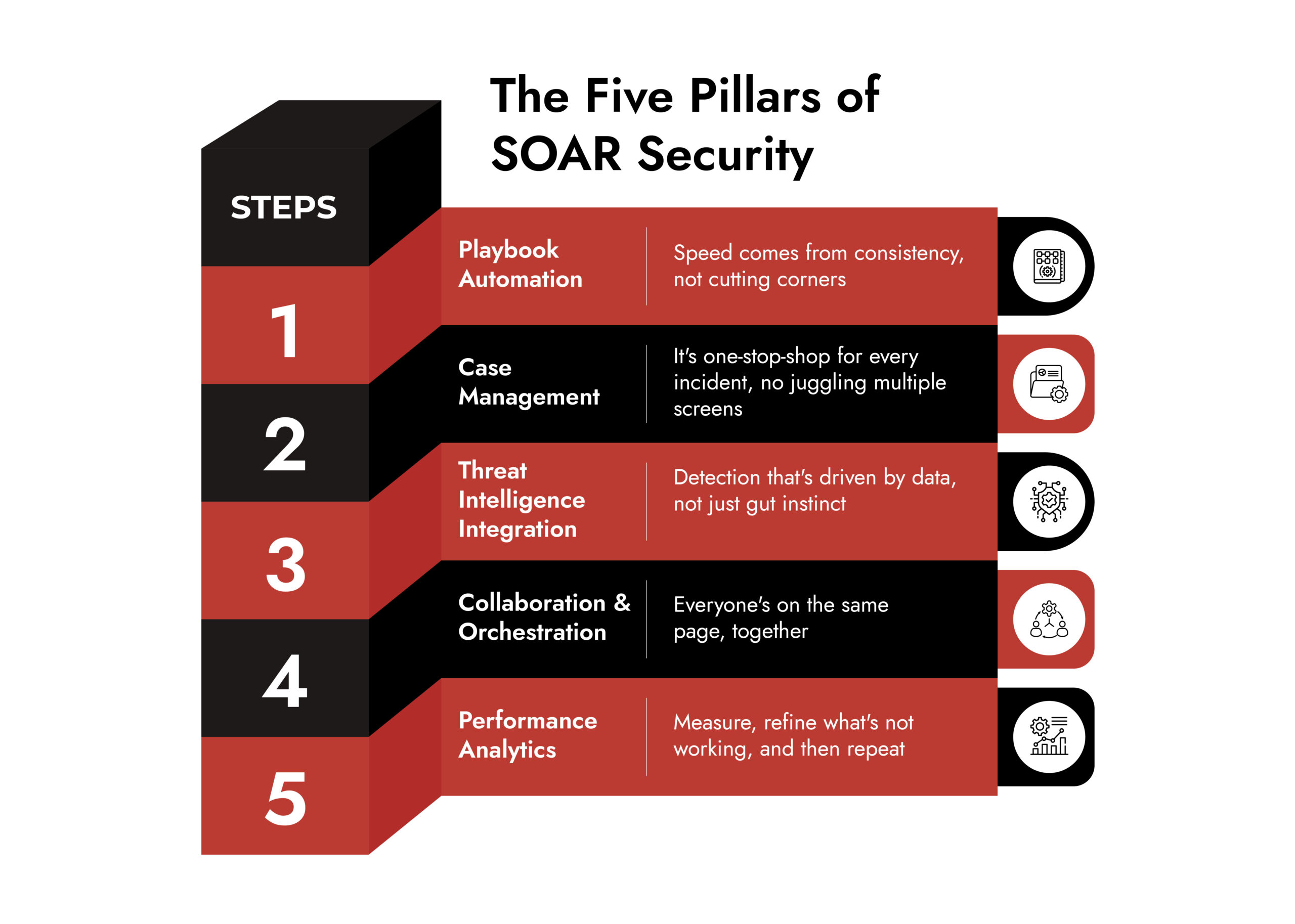
Conclusion
Having the right technology won’t make a SOC efficient on its own. What really moves the needle is how well everything works together. The real value shows up when your systems don’t just automate tasks but actually keep people aligned and informed.
Here’s what actually defines a strong SOAR setup:
- Playbook automation that removes repetitive work and keeps responses consistent.
- Centralized case management so analysts aren’t juggling tools or losing context.
- Threat intelligence integration that adds real-world context to every alert.
- Real-time collaboration so teams don’t have to deal with going back-and-forth.
- Analytics and reporting to see what’s working, what’s lagging, and where optimization is still needed.
If your team is currently assessing or upgrading SOAR tools, it is worth looking at how NetWitness SOAR has all of these features integrated. It will help you improve investigation and response time, simplify workflows, and improve the resiliency of your entire operation.
Frequently Asked Questions
1. What are the key features of a SOAR platform?
Playbook automation, case management, threat intelligence integration, collaboration tools, and performance analytics. These features automate repetitive tasks, enrich alerts, and accelerate incident responses.
2. How does SOAR help a SOC team?
SOAR automates alert triage, standardizes response workflows, reduces manual overhead, centralizes visibility, improves coordination, and speeds up incident containment.
3. How do I choose the best SOAR solution?
Look for SOAR platforms that integrate with SIEM, support custom playbooks, provide analytics dashboards, scale efficiently, and offer strong vendor support.
4. What is the main purpose of SOAR?
To automate and orchestrate security operations, enabling faster, more consistent, and accurate responses to complex threats.
5. What are the top 5 SIEM use cases?
Threat detection, compliance reporting, insider threat monitoring, anomaly detection, and integration with SOAR tools for automated response workflows.
Make Way for the Intelligent SOC with NetWitness®
-Turn data overload into actionable intelligence.
-Accelerate detection with AI-driven insights.
-Empower analysts with enriched, contextual decision-making.
-Build a smarter, faster, more resilient SOC.





