Key Takeaways
- Cybersecurity threat intelligence provides the context detection tools lack.
By enriching raw alerts with adversary behavior and campaign insights, cybersecurity threat intelligence helps teams understand which threats in cybersecurity actually matter and why. - Cyber threat intelligence services improve detection accuracy at scale.
When cyber threat intelligence services feed real-time context into TDR workflows, false positives drop and advanced threat protection becomes both faster and more reliable. - A threat intelligence platform turns external knowledge into operational value.
Integrated with detection systems, a threat intelligence platform connects global intelligence to internal activity, strengthening cyber threat security without increasing alert noise. - Threat intelligence tools elevate cyber threat monitoring from visibility to understanding.
Instead of tracking isolated events, threat intelligence tools enable cyber threat monitoring that recognizes attack patterns, intent, and likely next moves. - Advanced threat protection depends on context-driven response, not more alerts.
Accurate detection and high-quality response come from combining intelligence, automation, and TDR to contain threats in cybersecurity before damage escalates.
Introduction
Most detection failures don’t happen because teams lack alerts. They happen because alerts arrive stripped of meaning.
Security tools are excellent at telling you that something happened. They’re far less reliable at explaining whether it matters, why it matters, and what you should do next. That gap between signal and understanding is where attackers hide.
This is exactly where threat intelligence and Threat Detection and Response (TDR) intersect. Not as separate layers, but as a feedback loop. When intelligence feeds detection with context, accuracy improves. When detection feeds intelligence with real-world observations, response quality jumps. Together, they change how security teams operate under pressure.
Let’s break down how this actually works and why it matters more now than ever.
The Accuracy Problem in Modern Detection
Most security teams are drowning in telemetry. Logs, network traffic, endpoint events, and cloud activity. Visibility isn’t the problem anymore.
Interpretation is.
A single alert without context answers one question: Did something unusual occur?
It doesn’t answer the harder questions:
- Is this tied to a known threat actor or campaign?
- Is this behavior normal for this environment?
- Has this tactic appeared elsewhere in our infrastructure?
- What is the likely next move?
Without answers, analysts fall back on manual investigation. That slows response, increases fatigue, and creates inconsistency across incidents. Accuracy suffers because decisions are made with partial information.
This is why standalone detection engines struggle. They see all manner of events and activity. But the intent isn’t always understood.”
What Threat Intelligence Really Adds to TDR
Cybersecurity threat intelligence is often misunderstood as a static feed of indicators. IPs, domains, hashes. Useful, but limited.
In the context of TDR, intelligence becomes valuable when it provides operational context that helps systems and analysts interpret activity correctly.
At its best, threat intelligence answers four critical questions:
- Who might be behind the activity
- Why they behave the way they do
- How they typically operate
- What usually happens next
When this information is fused directly into detection logic, alerts stop being generic and start becoming situational.
Instead of “suspicious outbound connection,” you get “communication pattern consistent with a known data-exfiltration framework used in recent finance-sector attacks.”
That difference changes everything.
From Raw Signals to Contextual Detection
Threat detection and response platforms are designed to correlate signals across multiple layers: network, endpoint, identity, cloud, logs. But correlation alone isn’t enough. Correlation tells you that events are related. Context tells you whether they’re dangerous.
Here’s how threat intelligence improves detection accuracy at each stage.
1. Enrichment at Ingestion
When telemetry is enriched at the moment it’s collected, detection improves immediately.
Threat intelligence tools and platforms can add:
- Reputation scores for IPs, domains, and certificates
- Known associations with malware families or campaigns
- Historical prevalence across industries or regions
- Confidence levels based on multiple intelligence sources
This prevents low-confidence indicators from triggering high-priority alerts and reduces noise before it reaches analysts.
2. Behavioral Context Over Static Indicators
Indicators of compromise are snapshots. Attackers know this. They rotate their infrastructure tactics and techniques constantly
What doesn’t change as easily is behavior.
Threat intelligence provides patterns of behavior tied to specific adversaries or tools:
- Beaconing intervals
- Protocol misuse
- Lateral movement preferences
- Data staging techniques
When TDR systems look for behaviors instead of just indicators, detection becomes resilient to evasion. The system doesn’t care if the IP is new. It recognizes the playbook.
3. Campaign-Level Correlation
A single event might look benign in isolation. Multiple events aligned with a known campaign tell a different story.
Threat intelligence enables campaign awareness by connecting:
- Initial access techniques
- Follow-on activity
- Typical dwell times
- End goals like ransomware deployment or espionage
This allows threat detection and response workflows to escalate threats earlier, before damage occurs.
4. Vulnerability Mapping for Focused Detection
Context also connects threat intelligence directly to known weaknesses.
By mapping intelligence to:
- Unpatched vulnerabilities
- Exposed services
- Misconfigured systems
TDR platforms can focus on detection and monitoring where exploitation is most likely to occur. This shifts detection from broad coverage to strategic depth, improving accuracy without increasing noise.
Why IOCs Alone No Longer Work
IOCs still matter, but relying on them alone is a losing strategy.
Here’s why they fall short in modern environments:
- They’re reactive. Indicators usually appear after compromise elsewhere.
- They’re easy to evade. Infrastructure churn invalidates them quickly.
- They lack intent. An IP address doesn’t explain attacker goals.
- They generate false confidence. Blocking known bad doesn’t stop unknown bad.
In contrast, contextual intelligence focuses on how threats operate, not just where they appear. This is what allows TDR to detect threats earlier in the kill chain.
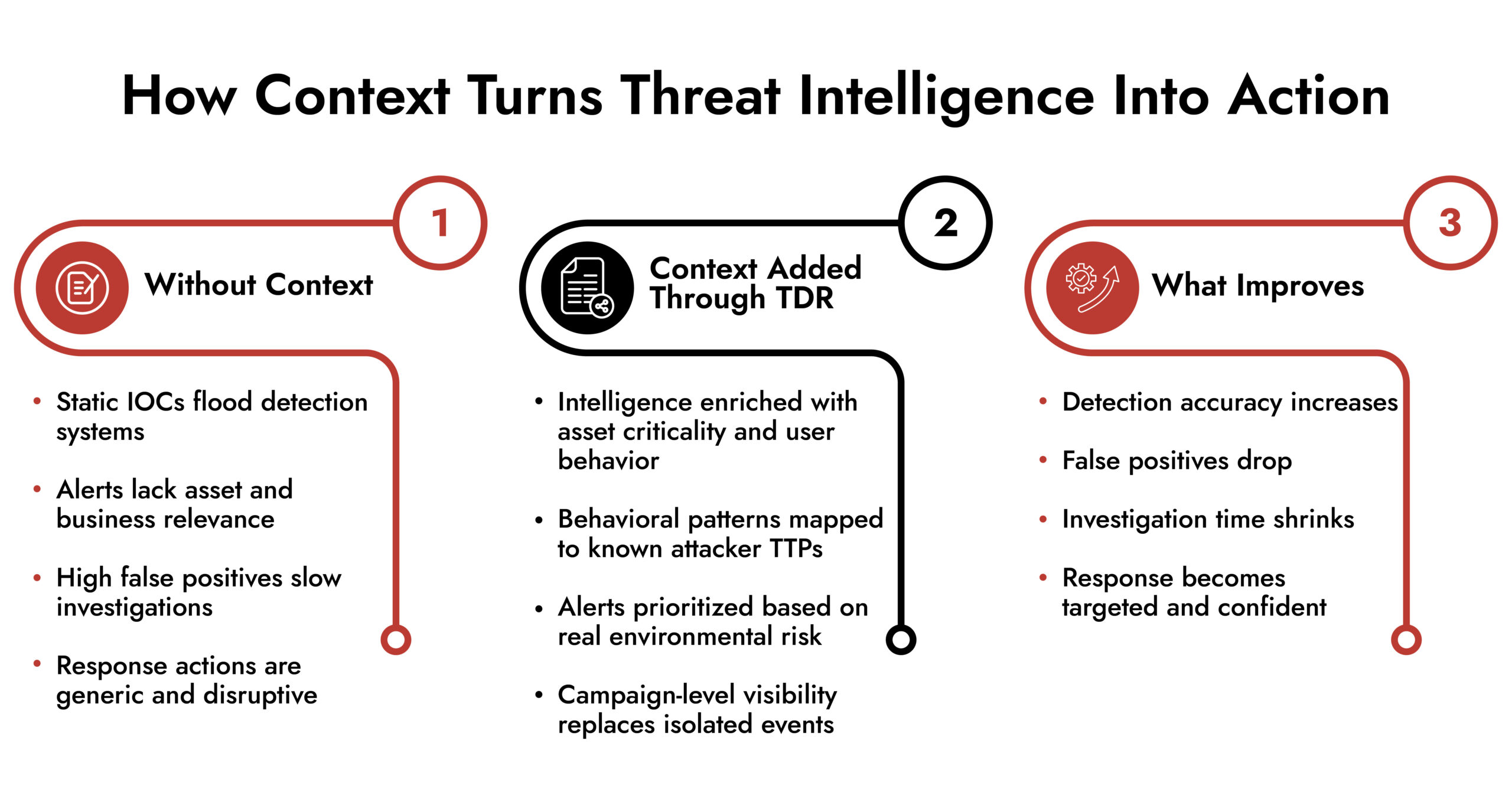
Response Quality Depends on Context
Detection accuracy is only half the equation. Response quality determines outcomes.
Without context, response actions tend to be blunt:
- Isolate the host
- Block the IP
- Reset credentials
Sometimes that’s enough. Often it’s not.
Threat intelligence improves response by informing how and when to act.
Faster, More Precise Containment
Context enables rapid incident scoping.
Instead of asking “what might be affected?”, analysts can immediately see:
- Which systems communicated with the threat
- How far lateral movement progressed
- Which users or services were involved
This allows containment actions to be surgical. Compromised systems are isolated without disrupting unrelated business operations, reducing both risk and downtime.
Informed Decision-Making Under Pressure
Not every incident requires the same response path. Context helps teams assess impact quickly by revealing:
- The sensitivity of affected data
- The criticality of impacted systems
- The likelihood of regulatory or legal exposure
With this insight, security leaders can make informed decisions about escalation, legal involvement, or breach notification timelines instead of reacting blindly to alert volume.
Proactive Threat Hunting With Purpose
Threat intelligence tells you what attackers are doing globally. TDR tells you where to look locally.
When combined, context allows threat hunters to focus on:
- Adversaries targeting their industry
- Campaigns active in their region
- Techniques relevant to their technology stack
This replaces random log searching with targeted hunting, increasing the chances of uncovering stealthy threats before alerts ever fire.
Strategic Hardening After the Incident
Context doesn’t stop being useful once the incident is closed.
Post-incident analysis that combines intelligence and detection data reveals:
- Systemic control gaps
- Recurring weak points
- Delayed detection patterns
These insights inform long-term improvements such as tighter segmentation, better patch prioritization, refined detection logic, and more resilient security architecture. Over time, each incident strengthens the organization instead of merely interrupting it.
Threat Intelligence: The Key to Higher Security Operation Performance
Unlock the full potential of your Security Operations Center with deeper visibility, faster detection, and smarter response. This whitepaper explores how modern threat intelligence elevates SOC maturity and helps organizations stay ahead of evolving adversaries.

Automating Threat Intelligence in TDR Workflows
Manual intelligence consumption doesn’t scale. The real power comes from automation.
Modern cyber threat intelligence services integrate directly into TDR pipelines to:
- Automatically enrich alerts with threat context
- Adjust severity based on confidence and relevance
- Trigger response playbooks when high-risk patterns appear
- Suppress alerts tied to low-confidence or stale indicators
Automation doesn’t remove human judgment. It removes unnecessary human effort.
Analysts spend less time validating noise and more time investigating real threats.
Threat Intelligence Platforms as Force Multipliers
A threat intelligence platform acts as the connective tissue between external knowledge and internal telemetry.
Its role in TDR includes:
- Aggregating intelligence from multiple sources
- Normalizing and scoring indicators and behaviors
- Mapping intelligence to detection logic
- Feeding response automation with confidence data
When properly integrated, it ensures intelligence isn’t just collected. It’s applied where it matters.
Context Is What Turns Data Into Defense
Cyber threat monitoring without context is surveillance. It tells you what’s happening but not what it means.
Threat intelligence supplies meaning. TDR supplies action.
Together, they create a system that doesn’t just react faster but reacts smarter. Accuracy improves because detections are informed. Response quality improves because decisions are grounded in real-world adversary behavior.
What this really means is simple. Security teams don’t need more alerts. They need better understanding at machine speed.
That’s what threat intelligence plus TDR delivers.
Why Choose NetWitness for Context-Driven TDR
NetWitness Threat Detection and Response is built for environments where context matters more than raw alert volume. It correlates threat intelligence in real time across logs, network, and endpoint data, allowing detections to be evaluated based on behavior, asset criticality, and environmental relevance, not just static indicators.
This context-first approach improves accuracy and response quality by reducing false positives and surfacing the activity that actually puts the business at risk. For large, complex enterprises, NetWitness turns threat intelligence into an operational advantage rather than another feed to manage.
The Big Picture
Threat intelligence provides awareness. TDR provides action. Context is what makes both effective.
Without context, intelligence is additional noise and detection is guesswork. With it, accuracy improves, response sharpens, and security teams operate with confidence instead of urgency.
This is how modern defense scales. Not by adding more tools, but by making the ones you already have smarter and enriched.
Frequently Asked Questions
1. What role does threat intelligence play in TDR?
Threat intelligence provides the context that helps TDR systems interpret raw detection signals. It enriches alerts with information about adversaries, campaigns, and behaviors, improving accuracy and guiding response decisions.
2. What types of threat intelligence are most valuable for TDR?
Behavioral intelligence, campaign intelligence, and adversary TTPs are the most valuable. These provide insight into how threats operate, not just where they appear.
3. Why are IOCs alone insufficient for modern threat detection?
IOCs are reactive, easy to evade, and lack intent. Attackers change infrastructure frequently, but their behaviors remain consistent. Contextual intelligence focuses on those behaviors.
4. Can threat intelligence be automated in TDR workflows?
Yes. Modern TDR platforms automate intelligence enrichment, alert scoring, and response triggering. Automation reduces noise and speeds up accurate decision-making.
5. How does context improve detection accuracy?
Context helps systems distinguish malicious activity from normal behavior by adding intent, history, and relevance. This reduces false positives and surfaces real threats earlier.
Autonomous AI Defenders for a Smarter SOC






