Blog Summary
- What makes an incident response plan practical, not theoretical
- Essential habits that help teams reduce damage and recovery time
- Why preparation, time-to-response, documentation, and scoping matter
- How visibility gaps limit response quality (and how XDR fills them)
- Where NetWitness strengthens investigation and orchestration
Why Incident Response Needs More Than a Document
Here’s the thing. A strong incident response plan isn’t paperwork. It’s a living system that shapes how quickly your organization spots an issue, contains it, and gets back to normal. Detecting early warning signs, coordinating the right people, and recovering efficiently all depends on a mix of preparation, clarity, and continuous improvement.
What this really means is, you can’t improvise your way through a breach. The threat landscape moves too fast for that.
Let’s break down the practices that consistently make response teams sharper and better prepared.
1. Build Awareness and Preparedness Early
Incident response plans often exist somewhere. But people outside the security team rarely know what’s in them. The first fix is simple: make IR a shared muscle across the business.
Annual tabletop exercises are the most effective starting point. They create muscle memory, especially when you involve more than just your security responders. Legal, compliance, marketing, IT, and leadership all have a role during a live incident, so leaving them out of the practice to run creates blind spots that show up when it matters most.
These simulations often stretch over several days and include scenario walkthroughs and playback of past incidents. Less mature teams may lean on external partners; mature teams typically run these in-house. Either way, the value becomes painfully clear when a real disruption hits and everyone realizes who actually knows what to do. 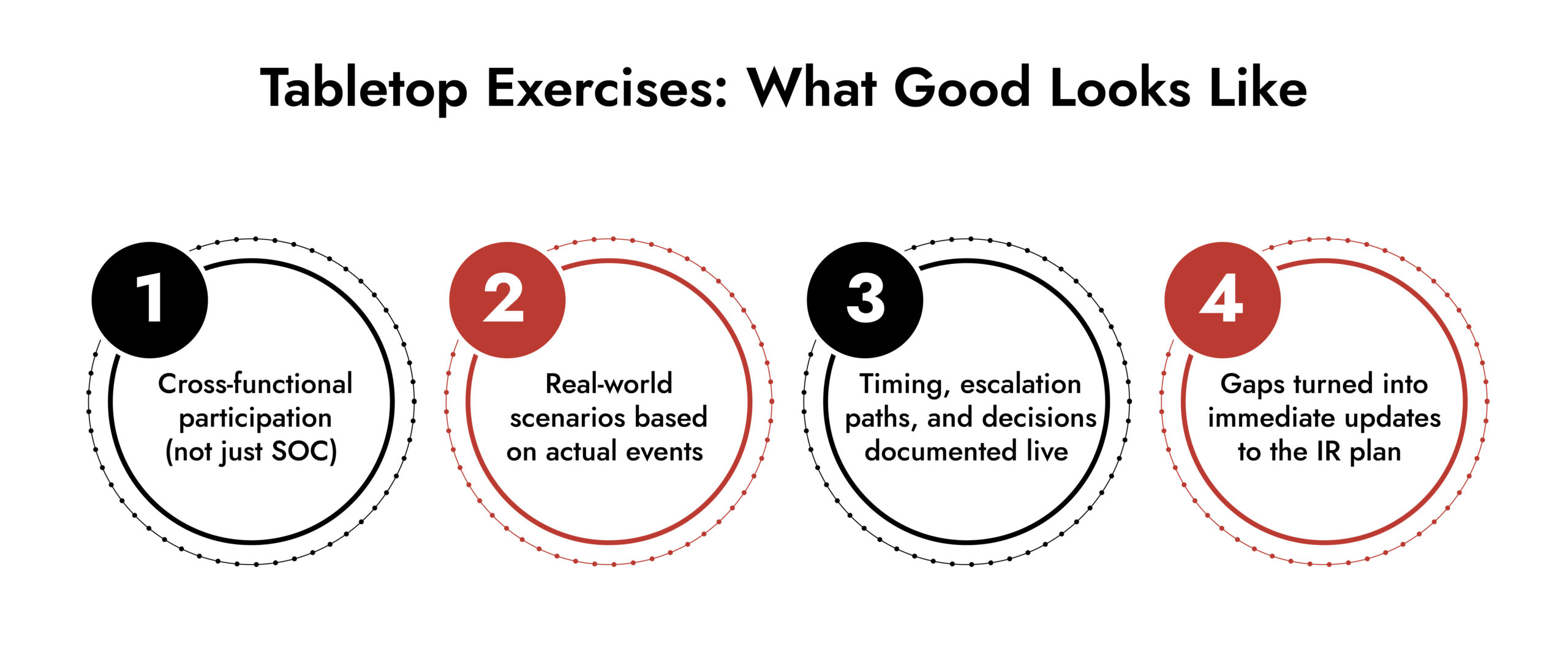
2. Treat Time as a Strategic Advantage
Every minute counts and not in a dramatic, cinematic sense. Real-world IR comes down to detection and containment time. The faster a team can orient itself, the less impact the attacker can make.
This is where a well-documented incident response plan pays off. Under pressure, people forget even simple steps. Clear guidance keeps the team coordinated and reduces panic-driven decisions.
Fast detection helps avoid:
- Exposure of sensitive information
- Financial losses
- Reputational fallout
- Operational downtime
A delayed response guarantees the opposite: more damage, more hours, more cleanup.
3. Align the Organization with the SOC
Your organizational incident response plan and the SOC’s technical playbook should fit together tightly, even if they don’t look identical.
The SOC focuses on:
- Detection
- Deep forensic analysis
- Technical containment
- Escalation triggers
The broader organization focuses on:
- Communications
- Legal and regulatory response
- Stakeholder updates
- Business continuity decisions
The two perspectives must align. When they don’t, responses become fragmented, and a relatively small incident can spiral.
4. Scope Before You Act
Scoping defines the size, impact, and nature of the incident. It’s one of the most overlooked parts of IR, yet it shapes every downstream decision.
Scoping determines:
- Which systems are affected
- How far the adversary has moved
- Resource allocation
- Whether regulatory reporting is required
- How deep the investigation needs to go
And when the dust settles, proper scoping fuels honest postmortems. Skipping post-mortems because everyone is busy is a classic mistake and a fast way to repeat the same errors.
Rapid, Expert Response with NetWitness® Incident Response Services
-Accelerate threat containment with experienced IR specialists.
-Investigate effectively using advanced forensics and analytics.
-Minimize business impact with fast, guided remediation.

5. Elevate Documentation from Admin Task to Critical Step
Good documentation isn’t paperwork. It’s your narrative, evidence, and audit trail.
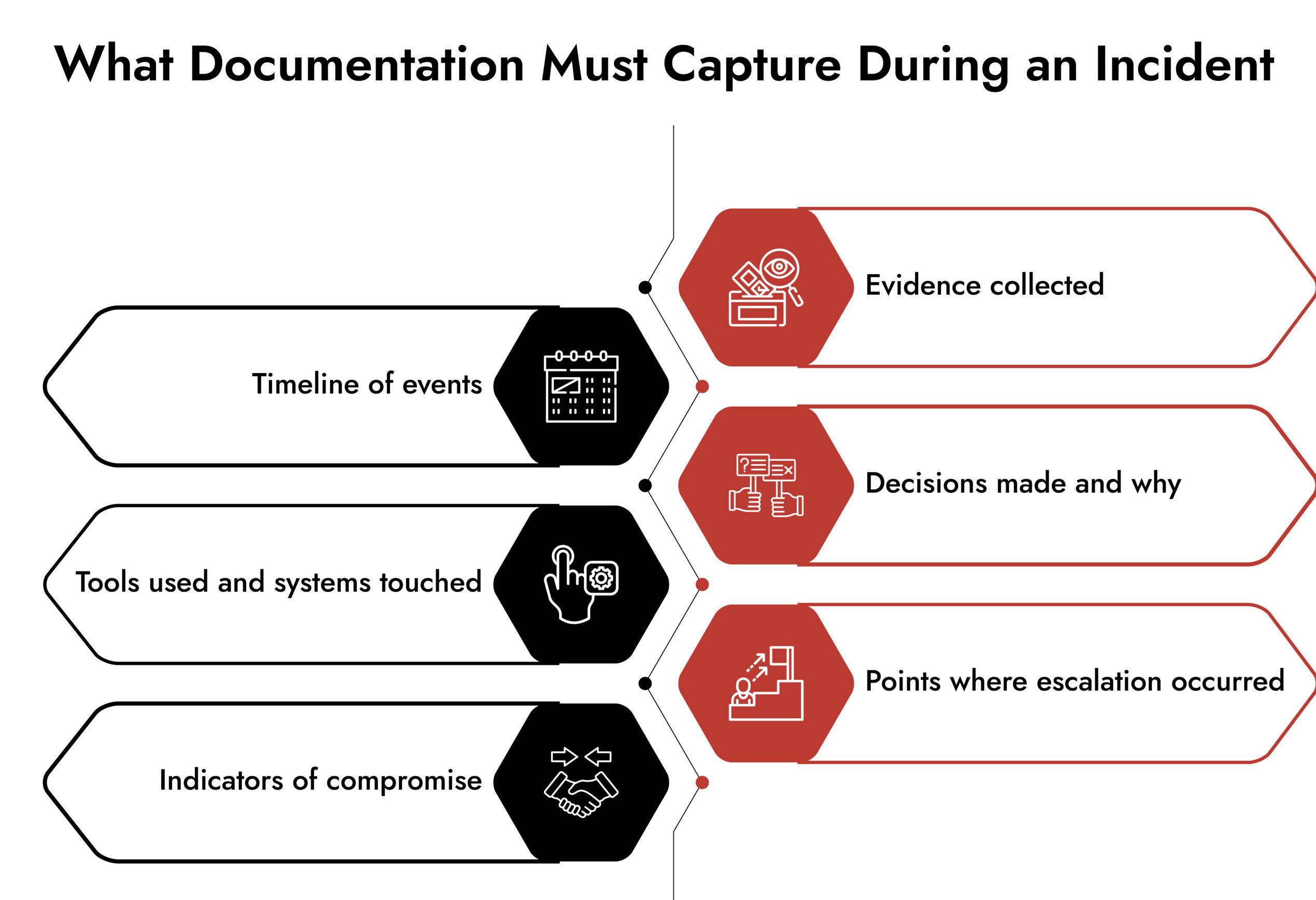
During an incident, this includes:
- Timeline of events
- Actions taken
- Decisions made
- Tools and systems used
- Initial findings and updated assessments
This becomes essential for legal, compliance, insurance, and long-term improvements. But documentation only helps if you do it right.
Best practices that protect the documentation process:
- Use secure communication channels: Email is risky during an active incident. If the adversary has access to inboxes or collaboration systems, they have full visibility in your response. Use secure or out-of-band channels for IR communication.
- Keep the plan and evidence digital: Physical documentation gets lost or damaged. Digital plans support faster access, updates, and version control.
- Update the plan regularly: At least once a year or more often if your organization evolves quickly.
- Protect backup integrity: Good documentation helps you verify which backups are useful, which are corrupted, and what data was stored where.
- Connect your Incident Response Plan to your DR and BCP: IR, disaster recovery, and business continuity shouldn’t be separate islands. Documentation ties them together.
6. Expand Visibility Beyond Logs
Many organizations lean heavily on their SIEM. SIEM in cybersecurity is important, but it sees only part of the picture. When incidents move laterally, hide in encrypted traffic, or exploit endpoints, logs alone aren’t enough.
To diagnose fast and respond intelligently, responders need:
- Endpoint telemetry
- Log correlation
- Analytics (UEBA)
- Automated workflows (SOAR)
This is where an XDR approach becomes practical, not theoretical.
Why fine-tuning alerts matters
Too many false positives burn out analysts, while too few alerts hide real threats. Alert tuning is never one-and-done, it evolves with the environment. Mature organizations often assign dedicated team members to this mission. 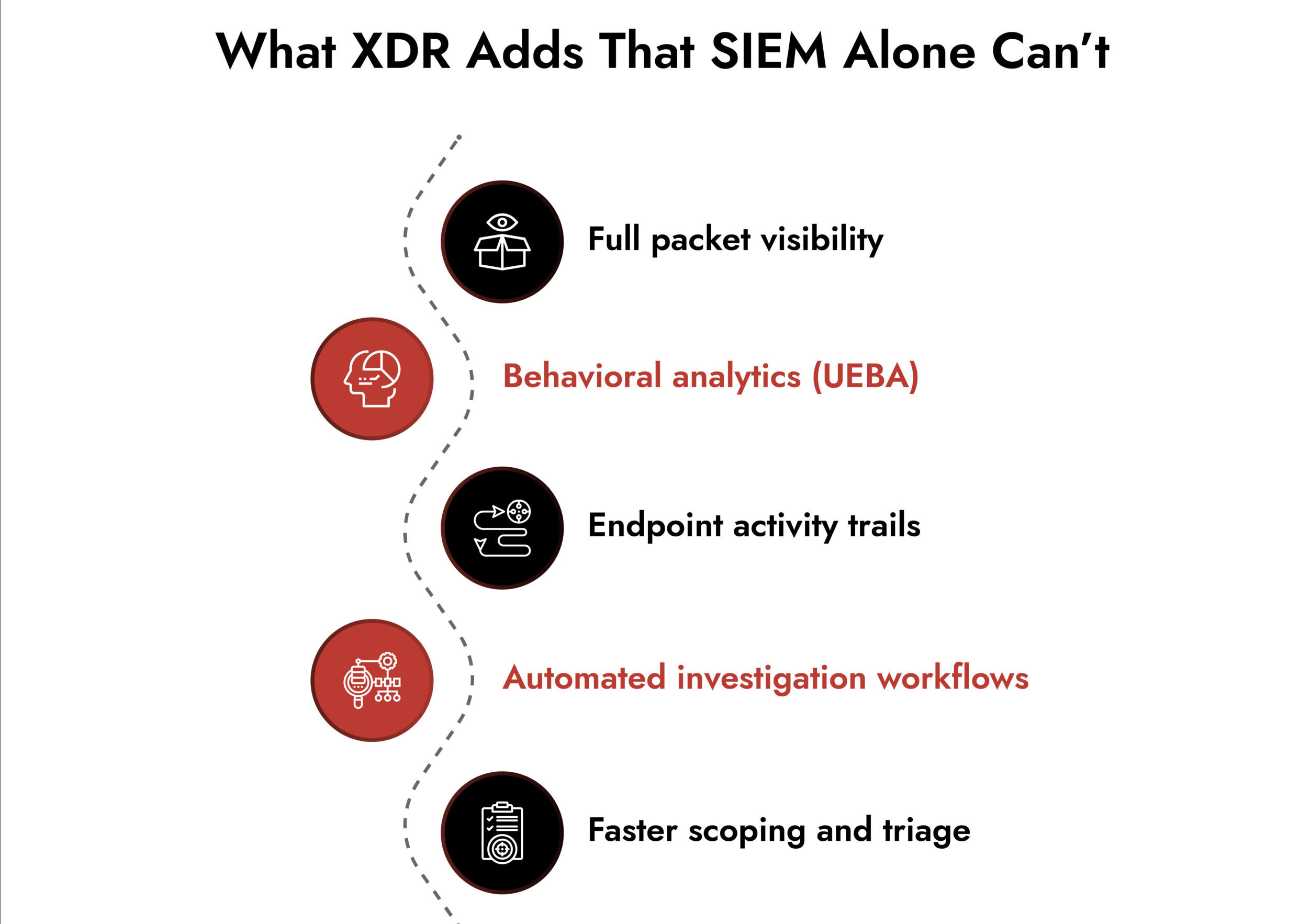
7. Build an IR System That Matches Your Organization
Every environment is different. Every team has its own maturity level. But the essentials stay the same: look for the breadcrumbs.
An XDR platform that stores logs, network data, and endpoint history over long time windows gives responders what they need to reconstruct an attack path. There’s no shortcut here. Modern security always involves multiple vendors, tools, integrations, and workflows.
Mastering IR isn’t a one-week project. It’s a long-term discipline that evolves with your threat surface.
How NetWitness Strengthens Incident Response
NetWitness enhances IR capabilities across investigation, orchestration, and threat intelligence.
- Investigation- Advanced forensic workflows, enriched metadata, fast query capabilities, and visual tools help analysts triage and understand incidents quickly.
- Orchestration- SOAR capabilities streamline response with automated playbooks, case management, and collaboration features that keep teams aligned.
- Threat Intelligence Integration- Combines external and internal feeds to improve detection of accuracy, threat understanding, and decision-making.
- Customization and Scalability- Adapts to your organization’s complexity, tools, and processes, essential for long-term incident response maturity.
Learn more about how NetWitness can support your IR strategy and schedule a demo today.
Frequently Asked Questions
1. How to get better at incident response?
Run annual tabletop exercises, improve detection and containment speed, extend visibility with XDR, tune alerts regularly, and conduct mandatory post-incident reviews.
2. What is an incident checklist?
A structured guide that standardizes notifications, evidence handling, communication channels, and recovery steps across teams.
3. Why is the incident response lifecycle important?
It sets clear protocols, clarifies roles, and builds continuous improvement loops, strengthening overall resilience.
4. What are effective containment strategies?
Scope the incident thoroughly, isolate compromised systems fast, use orchestration tools for automation, document everything, and communicate through secure channels.
5. What is the role of threat intelligence in IR?
Threat intelligence provides context on attacker behaviors, enabling faster correlation, smarter prioritization, and more decisive actions.





