Why is SIEM critical to Zero Trust architecture?
Zero Trust requires continuous verification based on real-time context. SIEM provides that context by correlating identity, device, network, and application activity into a unified risk view. It enables dynamic trust decisions, prioritizes suspicious behavior, and triggers automated enforcement, turning Zero Trust from a policy model into an operational security system.
The security perimeter is gone. Workforces are global, cloud workloads are everywhere, and attackers don’t need to break in anymore because trusted identities, APIs, and devices are already inside. Zero Trust stepped forward as the answer to this chaos. But here’s the thing: Zero Trust isn’t just a philosophy. It’s an enforcement model that depends on real-time data, context, and machine-driven decision making. That’s exactly why Security Information and Event Management (SIEM) has become the operational engine behind it.
The relationship between Zero Trust architecture and next-generation SIEM solutions is no longer optional. It’s becoming a full convergence. By 2026, SIEM will act as the central intelligence hub of Zero Trust environments, building continuous verification loops powered by AI and automation. If Zero Trust is the rulebook, SIEM is the referee that never sleeps.
Let’s break down what this looks like and why it matters.
How Identity Became the Control Plane for Zero Trust
Traditional network boundaries don’t exist anymore. Cloud-first architectures, SaaS adoption, BYOD culture, and remote work have dissolved the perimeter. That shift forced organizations to rethink trust entirely.
Zero Trust security flips the model: trust nothing until proven otherwise. Every identity, device, application, or service must validate its intent at every interaction. And that validation has to happen continuously. Static authentication doesn’t cut it.
Key emerging trends defining Zero Trust in 2026 include:
Identity as the control plane
Everything now ties back to who or what is making a request. IAM, continuous authentication, and conditional access are no longer side projects. They are Zero Trust foundations.
AI-driven policies
Machine learning models analyze patterns and assign risk scores dynamically. Humans don’t manually update access rules anymore. The system learns and reacts on its own.
Micro-segmentation everywhere
Environments are broken into granular zones, limiting the blast radius of breaches. Attackers can’t laterally move or pivot without triggering enforcement.
Securing non-traditional ecosystems
IoT, OT systems, and API ecosystems have become primary attack vectors. Zero Trust is expanding beyond users and endpoints to guard every data-producing entity.
The takeaway? Zero Trust needs real context, not static controls. And context doesn’t magically appear. It’s collected, correlated, and interpreted. That’s SIEM territory.
SIEM Is No Longer Just a Log Bucket
Old SIEM products functioned like archives, storing logs until someone queried them. Today’s SIEM cyber security platforms have evolved into real-time security brains.
Their trajectory now includes:
AI-Driven Analytics – Patterns, anomalies, and outliers are spotted before they materialize into breaches. Predictive analytics forecasts threats based on identity behavior, network signals, and system posture.
Cloud-native architectures – Modern workloads produce mountains of telemetry. Cloud-native SIEM security platforms scale without breaking or lagging.
Risk-centric intelligence – Future SIEMs don’t stop at detection. They correlate vulnerabilities, identities, and business impact. They don’t ask what happened; they answer why it matters.
Tight integration with SOAR and XDR – Routine tasks get automated. Response playbooks execute without analyst intervention. SIEM doesn’t just alert. It acts.
This shift positions SIEM as more than a monitoring tool. It becomes the decision engine Zero Trust needs.
Elevate Threat Detection and Response with NetWitness® SIEM
-Correlate data across users, logs, and network for unified visibility.
-Detect advanced threats with AI-driven analytics and behavioral insights.
-Accelerate investigations using automated enrichment and guided workflows.

How SIEM Powers Zero Trust Networking
A Zero Trust environment functions like a living organism—every interaction is scrutinized. The organism stays alive only if it has a central nervous system interpreting signals.
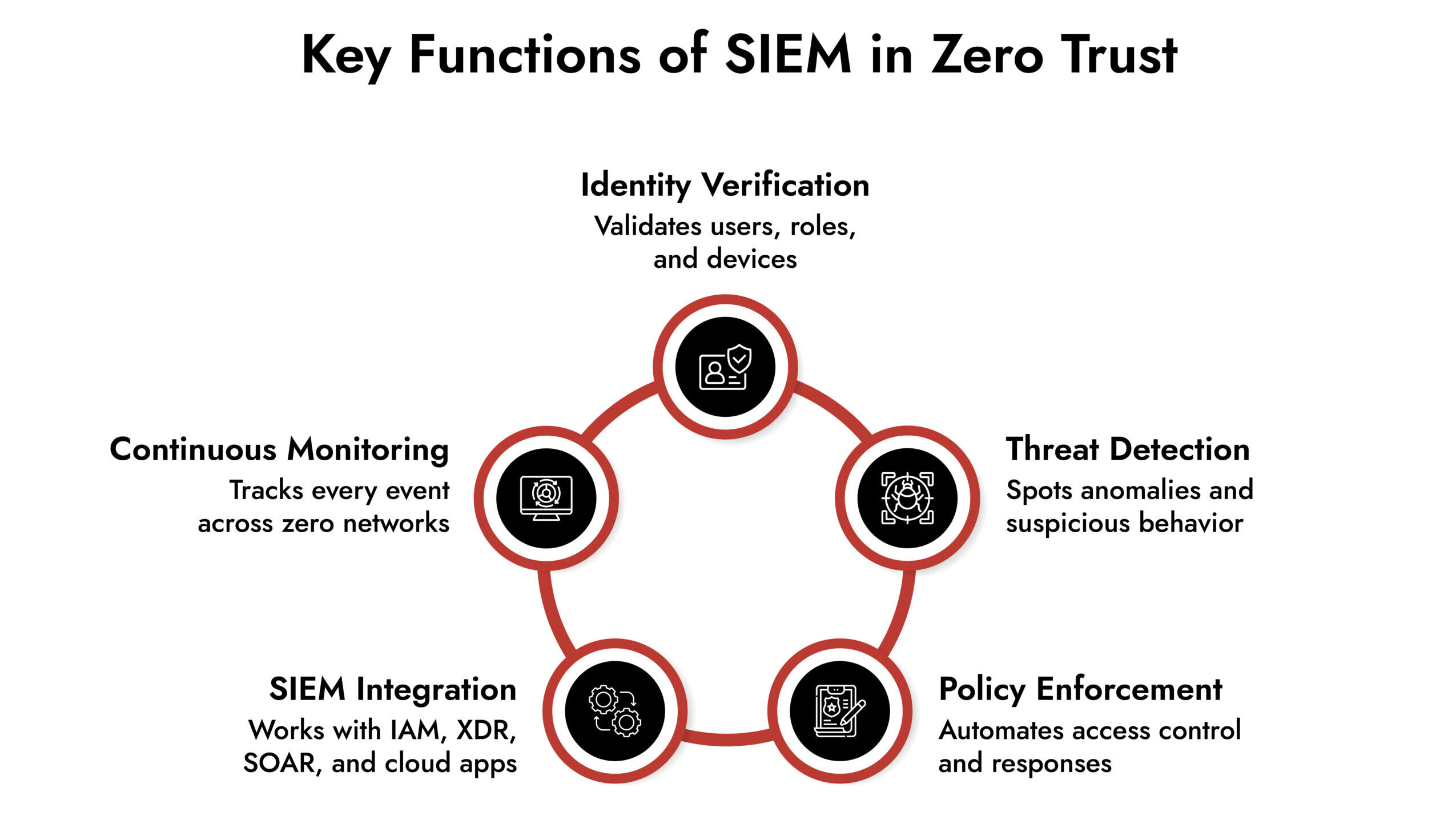
SIEM performs four critical functions:
1. Continuous Verification
Zero Trust demands ongoing authentication, not one-time checks. SIEM collects identity logs, device status, location data, behavioral baselines, and access patterns. If something deviates, access changes instantly.
2. Threat Detection at Identity Speed
Zero Trust assumes a breach already exists. SIEM validates that assumption through behavioral analytics, identifying suspicious activity inside trusted accounts before damage spreads.
This is where threat detection becomes the difference between a security posture and a breach headline.
3. Policy Enforcement Through Automation
A Zero Trust model is pointless without enforcement. SIEM integration with IAM, XDR, and SOAR lets the system:
- revoke access.
- isolate workloads.
- terminate sessions.
- restrict privileges.
All based on context, not assumptions.
4. Unified Visibility Across Zero Networks
Today’s enterprise is a distributed mesh of services, devices, identities, and APIs. Without SIEM, Zero Trust has blind spots the size of data centers. With SIEM, every interaction is tracked, analyzed, and risk-scored.
The Convergence: SIEM Becomes the Zero Trust Brain
We’ve reached the point where zero trust networking and SIEM are no longer separate initiatives. The convergence is happening for three reasons:
1. Zero Trust Requires Real-time – Insights You can’t enforce least-privilege access if you can’t see what identities are doing.
2. SIEM Needs Context to Prioritize Risk – Blind alerting is noise. Risk-based context is strategy.
3. AI Binds Them Together – Machine learning transforms excessive telemetry into actionable trust decisions.
SIEM evolves into a continuous validation system where identity risk, device posture, behavior, and access history form a live trust score. Policies aren’t static; they shift based on real-time assessments.
Zero Trust doesn’t succeed because you bought tools. It succeeds because your SIEM platform becomes intelligent enough to enforce trust dynamically.
The Future: Zero Trust Powered by Autonomous Security
By 2026 and beyond, the most advanced SOCs will function like self-regulating ecosystems. Analysts won’t approve every access request or policy update. SIEM-driven AI will:
- map identity behavior across environments.
- assign trust scores automatically.
- detect insider threats proactively.
- block malicious activity without human input.
- constantly refine access policies.
Security stops being reactive. It becomes adaptive.
Organizations that fail to embrace this convergence won’t just lag. They’ll operate blind in environments where attackers move faster and identities outperform firewalls.
Frequently Asked Questions
1.What is Zero Trust in cybersecurity?
Zero Trust is a security model based on the principle of never trusting any user, system, or device by default. Every access request must be authenticated, authorized, and continuously validated.
2. What are the three main concepts of Zero Trust?
Verify every identity, enforce least-privilege access, and continuously monitor user activity and device behavior.
3. Can SIEM automate Zero Trust responses?
Yes. Modern SIEM platforms integrate with SOAR, IAM, and network controls to automatically revoke access, isolate systems, or adjust policies based on real-time risk.
4.What challenges does SIEM solve in Zero Trust adoption?
SIEM removes visibility gaps, consolidates telemetry, eliminates alert fatigue, and provides context for identity-based access decisions.
5. Can SIEM detect insider threats in a Zero Trust environment?
Absolutely. SIEM uses behavioral analytics and correlation rules to identify abnormal patterns, privilege misuse, and internal data movement.
Choose the Right SIEM with Confidence






