Most security teams don’t realize their log management security setup is the problem until it’s too late.
Threats slip through. Alerts pile up. Investigations drag on. At some point, it stops being a tool and becomes a bottleneck.
That’s where security log management software comes in or should. It’s supposed to be the foundation for detecting threats, running investigations, and meeting compliance standards. But not all tools are built for the scale, speed, and complexity of today’s threat landscape.
If your team is already under pressure, the last thing you need is log management software that adds more work instead of removing it.
Here are five clear signs that your security log management system is due for retirement.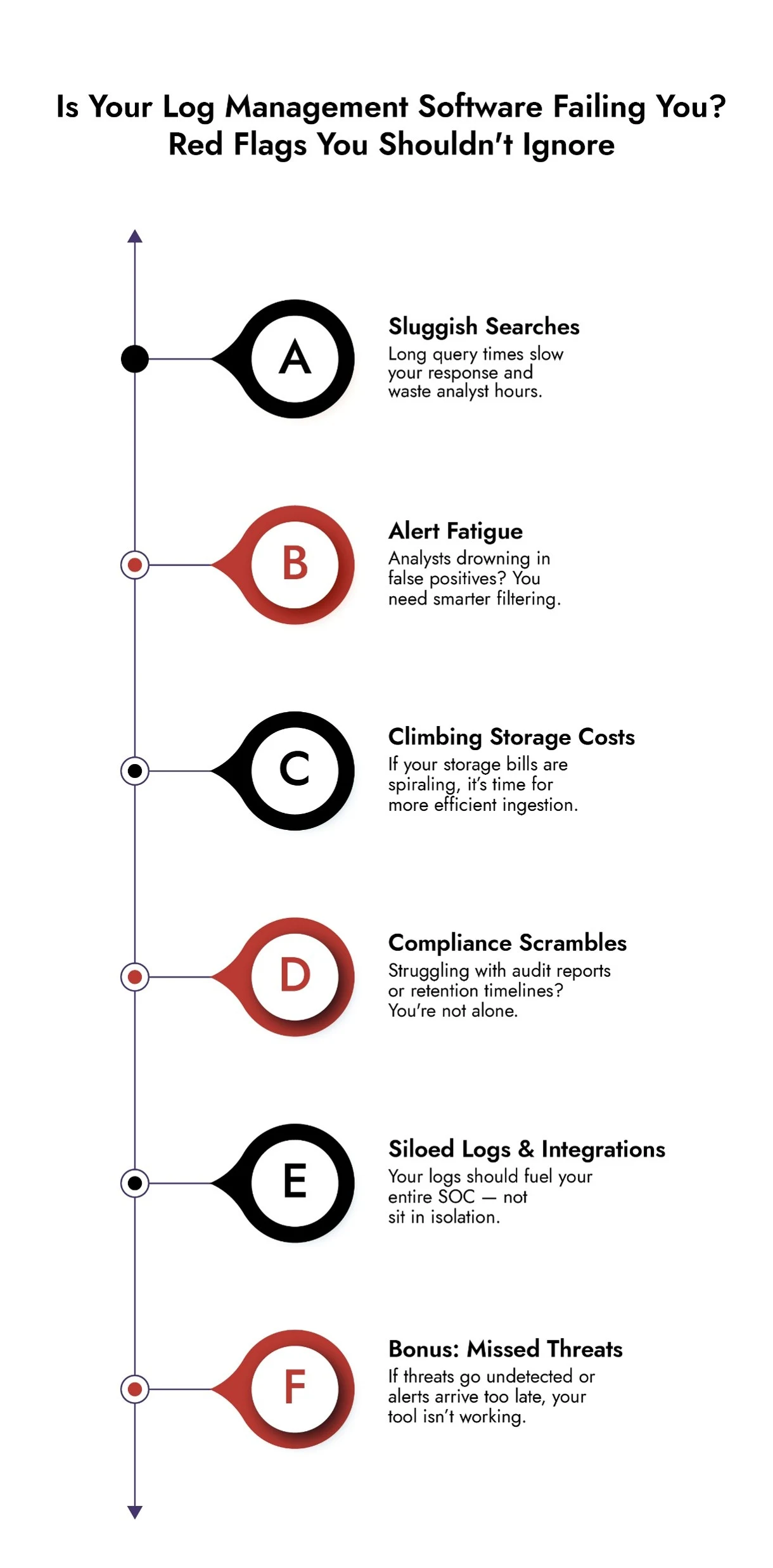
What is Security Log Management Software and Why it Matters?
Security log management software collects and centralizes data from across your IT environment. It’s essential for detecting threats, conducting investigations, and maintaining compliance.
However, not every solution can handle the scale or complexity of modern hybrid networks. The right log management software should do more than store logs, it should help you interpret them, detect anomalies, and automate responses.
1. Missing Threats? Your Log Management Security May Be Outdated
Log tools are only useful if they surface the right signals. But outdated security log management software often lacks the ability to correlate logs across systems, detect anomalies, or highlight suspicious behavior in real time.
It’s not enough to collect logs anymore, you need context. You need to know about alerts that matter. And sometimes the problem isn’t just the tool, it’s whether you’re fully deployed and collecting all the data you need. Gaps in coverage mean gaps in visibility.
Modern log management SIEM platforms use behavior analytics and automation to cut through noise and zero in on actual threats before they escalate.
If your current log management software only shows you what happened after the fact, you’re already behind.
2. Why Slow Searches and Delayed Responses Signal Poor Log Management
Time is everything in incident response. If your team has to wait minutes or worse, hours, for search results, it’s not just frustrating. It’s dangerous.
Slow platforms, limited query capabilities, and missing context all delay response. That’s when attackers get time to move laterally or dig deeper into your systems.
Up-to-date SIEM log software offers fast search, enriched data, and guided investigations that make response workflows faster and sharper.
If your analysts must export logs just to make sense of what happened, the tool is not working for them.
3. Rising Storage Costs? Your Log Management Software May Be the Culprit
More logs. More storage. More bills. It’s a common trap. As your organization grows, so does your data volume and suddenly, your security log management software can’t keep up without blowing the budget.
With cloud SIEMs, it’s not just storage – compute costs spike during major incidents when analysts run heavy queries, leading to unpredictable expenses.
Legacy tools often force you to retain everything or worse, guess what to keep. And as cloud workloads expand, so do ingestion fees.
Newer log management SIEM platforms solve this with dynamic storage, smart filtering, and compression that keeps things lean without sacrificing visibility.
If you’re deleting logs to save space or holding off on ingesting new sources to cut costs, you’re sacrificing visibility. That’s a risk you can’t afford.
4. Failing Compliance Audits? It’s Time to Rethink Your Log Management Security
If every audit feels like a fire drill, you’re not alone.
Meeting today’s compliance standards takes more than just storing logs. You need retention rules, access controls, audit trails and fast reporting, none of which should require hours of manual work.
Older log management security tools often lack the flexibility or automation to make this easy. That leads to late reports, missed requirements, and avoidable risk.
Modern security log management platforms automate compliance workflows, create audit-ready reports in seconds, and make it easy to prove you’re doing what the regulators expect.
If you’re barely scraping through audits, or dreading the next one, you need something better.
5. Integration Issues? Your Security Log Management Software Is Working in a Silo
SIEMs don’t work in isolation. They need to integrate with the rest of your security stack: EDR, NDR, firewalls, identity tools, threat intel feeds, and orchestration platforms.
If your security log management software needs constant custom scripts or manual workarounds to connect with other tools, it’s not a system, it’s a silo.
That lack of interoperability slows down everything from investigations to reporting. It also prevents you from building automated, efficient workflows across your stack.
Modern SIEM log software uses open APIs, modular architecture, and prebuilt integrations to fit into any environment.
If connecting your tools feels like duct taping a puzzle together, your current setup is due for retirement.
Simplify Log Management and Threat Detection with NetWitness® Logs
-Centralize and analyze logs from across your environment in one platform.
-Detect threats faster with real-time visibility and automated correlation.
-Reduce noise through advanced filtering and context-driven analytics.

When Your SOC Team Hates the Tool, It’s Time to Upgrade
Here’s a test: ask your SOC team what they think of the current system. If the words “clunky,” “slow,” “incomplete,” or “useless” come up, it’s not just annoying, it’s hurting your defense.
Good security log management software should support your team, not frustrate them. It should reduce alert fatigue, surface meaningful insights, and simplify the day-to-day work of security analysts.
When the tool becomes something your team avoids or works around, it’s already failed.
How NetWitness Simplifies and Strengthens Log Management Security
If even a few of these points sound familiar, it might be time to consider a stronger foundation.
NetWitness offers a modern approach to log monitoring and management, designed to help teams detect threats faster, investigate smarter, and stay ahead of compliance demands. Its security log management software provides full visibility across your infrastructure, correlates data in real time, and integrates seamlessly with the rest of your security stack.
From enriched threat intelligence to built-in automation, NetWitness helps you eliminate the blind spots and bottlenecks your current system can’t fix.
Want to see how NetWitness transforms your log management security? Schedule a demo to see NetWitness in action, or review our datasheet to discover how Evolved SIEM brings unified visibility, real-time analytics, and automated investigations to your SOC.
Frequently Asked Questions
1. What is security log management software and why is it important?
Security log management software collects, stores, and analyzes log data from across your IT environment. It helps detect threats, investigate incidents, and maintain compliance by providing visibility into system activity.
2. How do I know if my log management tool is outdated?
If your log management software struggles with slow searches, alert fatigue, high storage costs, or limited scalability, it’s likely outdated and may need replacing a modern SIEM log solution.
3. What is the difference between SIEM and log management?
The difference between SIEM and log management lies in capability. Log management focuses on storing and organizing logs, while SIEM adds correlation, threat detection, and real-time analytics for proactive response.
4. Can outdated security log management software affect compliance?
Yes. Legacy systems often lack the automation, retention capabilities, and search efficiency needed for compliance with regulations like GDPR or NIS2. Upgrading ensures that your log management security platform can meet audit demands.
5.How often should I review or upgrade my SIEM log software?
It’s best to assess your SIEM log software at least annually, especially if your data volume, threat landscape, or compliance requirements have changed. Frequent reviews help ensure your security log management software stays effective and scalable.




