Why SOAR Security Needs More Than Just Automation
IT teams are increasingly adopting security orchestration automation and response (SOAR) tools to improve security operations’ efficiency. Often, when debating SOAR solutions, security personnel focus on the automation and orchestration aspects. However, some of the best SOAR solutions fall short by not properly leveraging the vast amount of threat intelligence available. Open-source threat feeds, subscribed threat feeds, abstracting data from blogs or research data, internally acquired threat intelligence and even crowdsourced intelligence can all be used to guide security operations and train SOAR security to properly identify, prioritize, investigate and resolve potential incidents.
Applying threat intelligence to decision-making helps security teams become more predictive, empowering them to see the likeliest threats and use that visibility to prioritize how they’ll protect their organization using intelligent SOAR security. When a previously unseen threat presents itself, it places your security team in reactive mode. But if you’re only reacting, analysts are stuck playing a never-ending game of catch-up and clean-up.
When you strategically introduce threat intelligence into a security program and integrate it with advanced SOAR solutions, it gives you a more holistic view of what’s happening outside your organization and allows you to map that external information to your organization’s own threat landscape.
Another way of putting it is finding threat intelligence about current threats, aggregating it, analyzing it, and using it to identify the most relevant threats is applicable to your business. 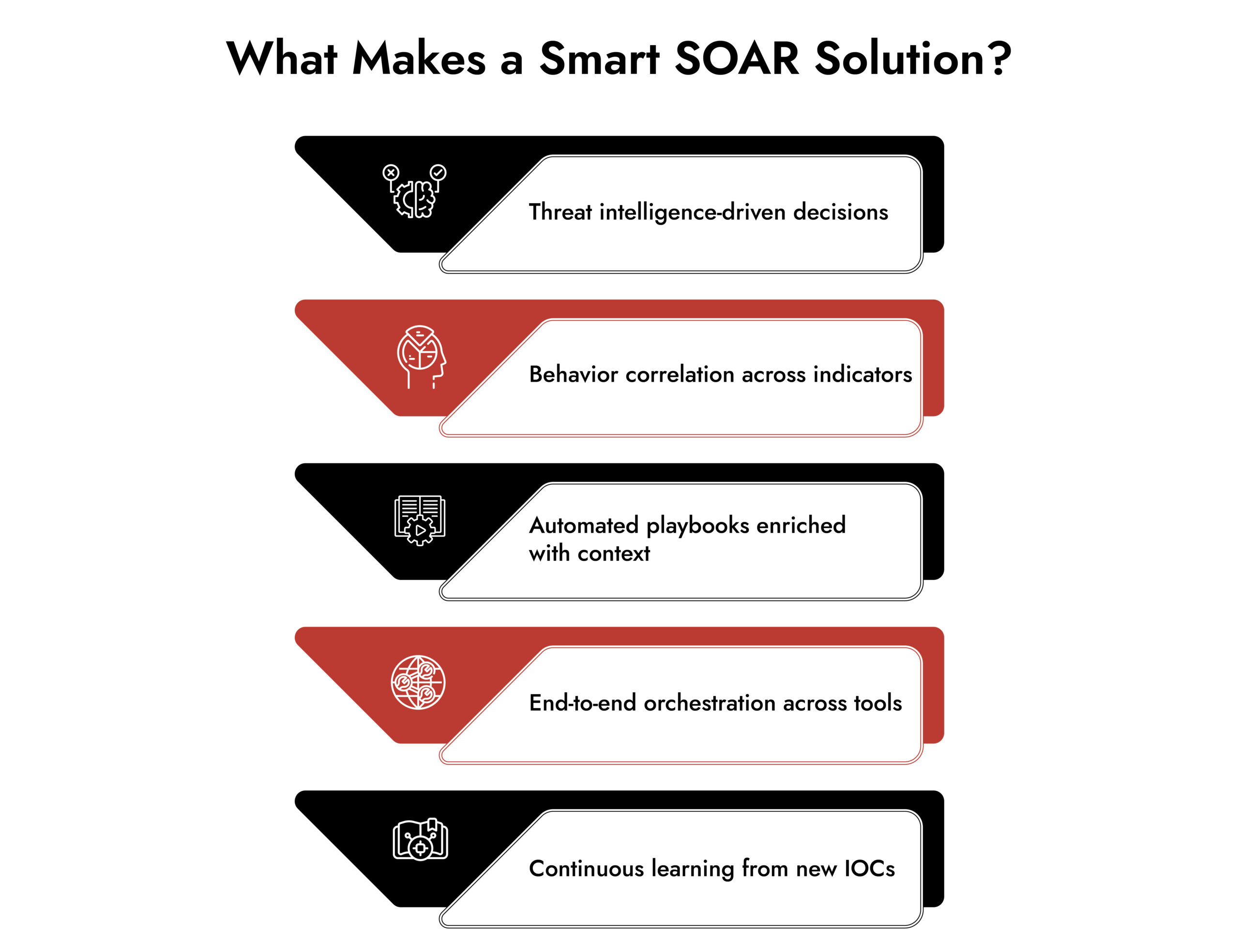
How Threat Intelligence Strengthens SOAR for Detection and Response
Threat intelligence gives SOAR the context it needs to move from alert handling to decisive action. Instead of treating every alert the same, it helps security teams understand what truly matters and respond with speed and confidence.
- Enriches alerts with contextual threat intelligence so analysts can validate incidents instead of reacting to raw IOCs.
- Helps prioritize alerts by linking IPs, domains, and file hashes to known threats, actors, and campaigns.
- Embeds intelligence directly into the analyst workflow, enabling faster decisions on severity and impact.
- Supports accurate automation by allowing validated indicators to trigger predefined SOAR responses.
- Feeds new intelligence back into the security program, improving future detections and response logic.
- Automatically informs security controls such as firewalls, proxies, and antivirus systems to prevent repeat attacks.
- Reveals relationships between related indicators, expanding investigations beyond a single alert.
- Helps uncover the full scope of an attack by identifying connected behaviors across the environment.
Establish Incident Response consistency, speed, and scale with NetWitness® Orchestrator

Practical SOAR Use Cases for Security Automation Teams
Modern organizations leverage SOAR solutions and other security automation and orchestration tools for versatile tasks across cybersecurity. Common SOAR security use cases include:
- Phishing detection and response.
- Endpoint detection and response.
- Incident alert triage.
- Vulnerability management.
- Threat hunting.
- Case management.
- Automated playbooks.
SOAR tools continually increase the efficiency and effectiveness of these operations by blending automation, orchestration, and threat intelligence.
What makes NetWitness SOAR’s Threat Intelligence Different
- Built on a strong foundation – evolved from a proven threat intelligence platform with deep heritage and knowledge base.
- Continuously adapts in real time – threat intelligence loses value as it ages, so the system constantly updates with emerging indicators, actors, and campaigns at scale.
- Provides full context for accuracy – analysts see not just what’s suspicious, but how and who reported it, since not all intelligence carries equal weight.
- Enables automated threat hunting – analysts can hunt based on known threat actors and campaigns without manual effort.
- Connects intelligence directly to action – the system sweeps environments for behaviors tied to threat intelligence and surfaces high-value alerts worth investigating.
- Automates end-to-end workflows – from remediation to IT ticketing to implementing preventative controls.
SOAR Benefits for Modern Security Teams
Organizations deploying SOAR solutions enjoy clear benefits, including:
- Accelerated incident response.
- Reduction in manual effort.
- Lowered risk and human error.
- Unified threat intelligence.
- Enhanced visibility across tools.
- Compliance and audit readiness.
- Improved collaboration.
These SOAR benefits make a substantial impact on both the effectiveness and the efficiency of security teams.
 Final Thoughts
Final Thoughts
It is a critical piece of the incident detection and response puzzle, but the way TI is applied can vary from solution to solution. SOAR solutions will continue to evolve to better leverage threat intelligence throughout the incident response lifecycle to detect and properly prioritize incidents and speed analysis and evidence collection – which ultimately equates to faster resolutions and more efficient security operations. Learn more about NetWitness SOAR.
Frequently Asked Questions
1. What are SOAR solutions?
SOAR solutions are platforms designed to automate, orchestrate, and respond to security incidents while integrating threat intelligence and other tools.
2. How does SOAR differ from SIEM?
SIEM collects and analyzes security data; SOAR orchestration uses that data to coordinate tools, automate responses, and streamline workflows.
3. What are common SOAR use cases?
Phishing response, incident triage, vulnerability management, automated threat hunting, and case management.
4. How can SOAR benefit my organization?
Through automation, efficiency, reduced manual work, and better visibility across tools.
5. Are there SOAR platforms for different kinds of organizations?
Yes, with options tailored for enterprise SOCs, MSSPs, mid-market teams, and more.
Make Way for the Intelligent SOC with NetWitness®
-Turn data overload into actionable intelligence.
-Accelerate detection with AI-driven insights.
-Empower analysts with enriched, contextual decision-making.
-Build a smarter, faster, more resilient SOC.






