Key Takeaways:
- Cybersecurity awareness in enterprises is not evolving as fast as the threat landscape
- It is not the number of training courses that matters, but whether the training prepares employees for real-world threats
- For effective cyber awareness, ownership from leaders is key
- Investing in comprehensive learning modules, like the ones offered by NetWitness, can strengthen cyber awareness skills and enhance detection capabilities.
The threat landscape has fundamentally shifted – from predictable, signature-based adversaries to sophisticated, autonomous, and intelligent ones. Ideally, cybersecurity awareness should evolve just as dynamically. But the reality is that many companies still use old ways to teach people about cybersecurity.
A 2024 study by Proofpoint found that almost three-quarters of the Chief Information Security Officers (CISOs) they talked to think that human error is still the biggest threat to the cybersecurity of their organization. This does not mean that employees are careless, but that the awareness programs and cybersecurity services have not been kept up with modern attacks.
According to the industry leaders at NetWitness, to close this gap, enterprises need to rethink cybersecurity awareness tied to cybersecurity risk awareness as a strategic capability, not a training initiative. Let’s look at key insider tips to boost cybersecurity awareness in 2026.
How can Organizations Improve Cybersecurity Awareness Effectively in 2026?
1. Redefine Cybersecurity Awareness Training
In 2026, training the employees will be really important. The leadership will have to look very closely at what the employees are learning. Training cannot be limited to phishing simulations, basic social engineering prevention, and annual compliance modules. It must include practice exercises that are like real-life scenarios, focused on
- How attackers exploit user credentials despite cybersecurity technologies
- How subtle behavioral anomalies signal system compromise
- How threats evolve after initial access
Enterprises should broaden awareness training from the basic “don’t click” guidance to helping employees, security teams, and leadership recognize early indicators of compromise across identity, cloud, and network environments.
2. Make Your Organization Detection-Aware
In today’s digital age, as more organizations move to the cloud, the attack surface often expands faster than the organization’s ability to defend it. Therefore, prevention is no longer a realistic success metric. Organizations should assume breach and design a more resilient strategy supported by cybersecurity solutions that focuses on:
- Recognizing behavioral anomalies as opposed to relying on known indicators
- Understanding attacker patterns, such as privilege escalation
- Encouraging escalation of suspicious activity.
When awareness is aligned with detection, organizations can successfully reduce dwell time and, in turn, the incident counts.
3. Make Identity Risk a Priority
For attackers nowadays, the easiest way to get in is by using employee identity. They pose as legitimate users by stealing credentials, tweaking privileges sneakily, or exploiting unprotected service identities.
To protect against identity theft, enterprise cybersecurity awareness programs must educate stakeholders on:
- Best practices for identity and access management
- Why identity misuse is harder to detect than malware
- How authentication anomalies mean a compromised system
Identity risk is rarely prioritized because it is poorly understood. But it requires attention and proper funding to strengthen cybersecurity.
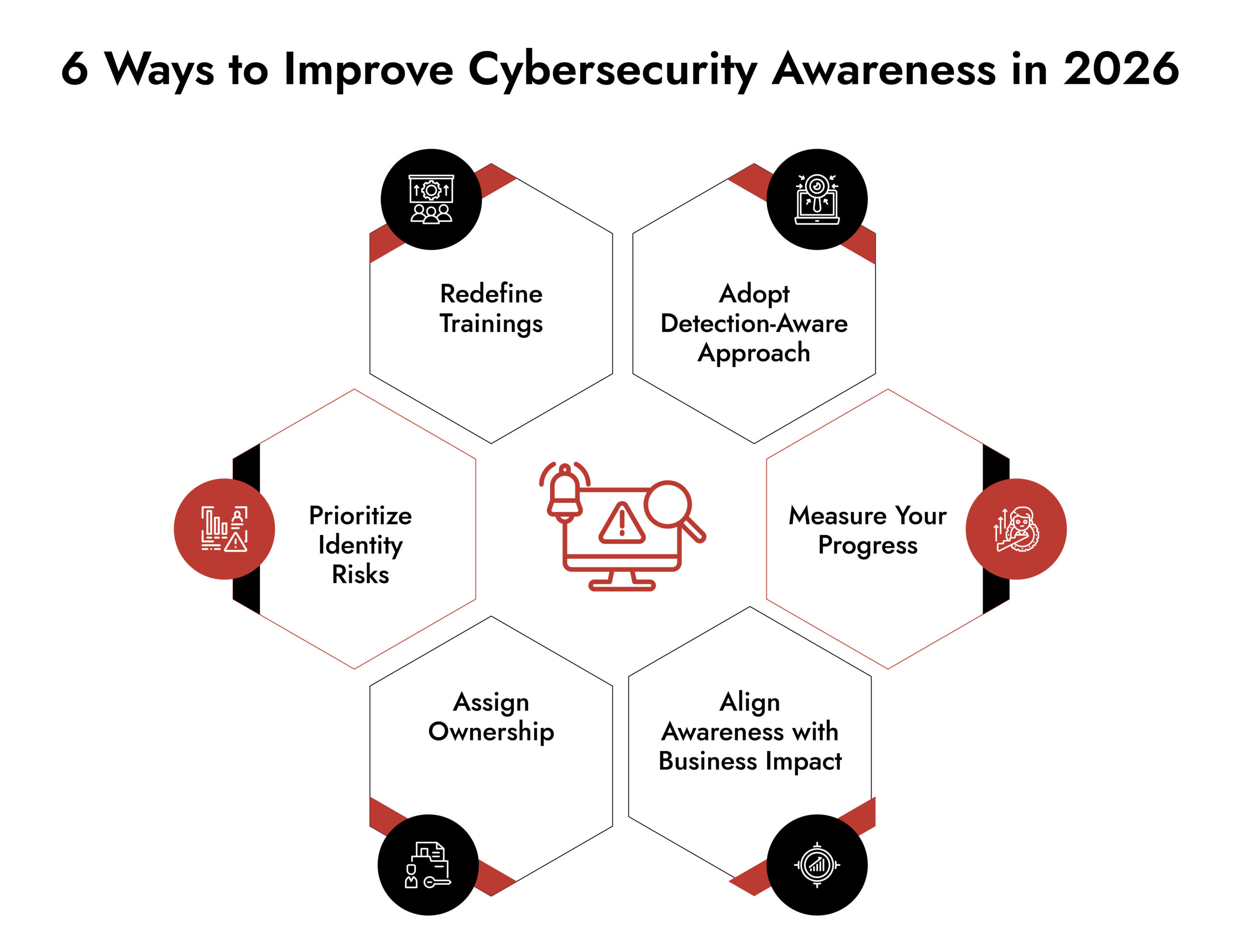
4. Align Cyber Awareness with Business Impact
Cyber awareness becomes meaningful for stakeholders when they understand the impact of cyber-attacks expose gaps in cybersecurity solutions. The training modules should go beyond the technical jargon and explain how a single attack can affect business operations, revenue, and reputation. Training material for awareness should:
- Translate attack scenarios into business outcomes
- Report awareness gaps as risk exposure, not training failures
- Tie detection delays to financial and operational consequences
It is important to understand that cybersecurity awareness is an ongoing activity and a long-term responsibility shared by everyone in the organization.
Unmask GenAI Threats — Get Ahead of the Curve

5. Measure Awareness by Readiness
Cybersecurity awareness in an organization is measured through training completion percentages and test scores. But the real question is, do these training courses prepare people for real threats? Most often, not! Therefore, awareness effectiveness should be measured by operational readiness. A few meaningful indicators include:
- Speed of recognizing anomalies
- Clarity in incident escalation
- Confidence in threat detection
These metrics offer insights into how effective awareness translates into action when needed.
6. Assign Ownership
Having an owner for any project is important if you want it to do well. When someone is in charge and responsible, the project works better. Enterprises should:
- Assign clear leadership ownership for cyber risk awareness
- Review awareness outcomes at organizational levels
- Treat awareness as an ongoing strategic activity
With ownership and accountability, cyber awareness can evolve at par with the threat landscape.
In Conclusion
In 2026, cybersecurity awareness should go beyond adding a certain number of training sessions to employee calendars. It should be about empowering them to detect threats and respond to incidents.
The organizations that treat cyber awareness as a strategic advantage will stand stronger against cyber threats.
How NetWitness Helps?
NetWitness offers comprehensive cybersecurity training programs designed to strengthen skills and detection capabilities. These programs help enterprises build a more informed, prepared, and resilient workforce.
Key features of our training modules include:
- Purpose-built training modules for real-world cyber challenges
- Role-based learning for security teams
- Flexible delivery formats
- Expert instructors and hands-on labs
- Certifications to validate skills
Frequently Asked Questions
1. What is cybersecurity awareness?
Creating cybersecurity awareness means educating every employee as part of the cybersecurity risk assessment and cybersecurity solutions strategy to identify, prevent, and respond to threats.
Cybersecurity awareness involves training employees to make secure choices during everyday digital interaction, be it sending emails, sharing documents, or accessing remote systems.
2. What are the biggest cybersecurity awareness challenges today?
The biggest cybersecurity awareness challenges today are:
- Keeping the training relevant to the rapidly evolving threat landscape
- Combating human error and social engineering tactics
- Addressing the skills gaps and staff shortages
3. Can you recommend tools for cyber threat awareness?
Tools for cyber threat awareness are of two types: technical tools for monitoring and human-focused tools.
The cybersecurity technical tools that help organizations monitor threats such as data breaches, phishing attacks, and malware attacks are:
- Firewalls
- Encryption
- Antivirus software
- Packet sniffers
- Vulnerability scanners
- Network intrusion detectors
- Anti-malware software
- Penetration testing
The common human-focused tools for cyber threat awareness are:
- Security awareness training programs like NetWitness Security Awareness and Cyber Defense Programs
- Policies and frameworks such as NIST, ISO 27001 & 27002, GDPR, etc
4. Can you recommend frameworks for cyber threat awareness?
The recommended frameworks to strengthen cyber threat awareness in organizations include:
- National Institute of Standards and Technology (NIST) Cybersecurity framework
- International Organization for Standardization’s ISO 27001 & ISO 27002 frameworks
- Service Organization Control (SOC) Type 2 framework
- North American Electricity Reliability Corporation-Critical Infrastructure Protection (NERC-CIP) framework
- Health Insurance Portability and Accountability Act (HIPAA) framework
- General Data Protection Regulation (GDPR) framework
- Federal Information Security Management Act (FISMA)
FIN13: Inside a Fintech Cyber Attack
FIN13 is one of today’s most disruptive threat groups targeting fintech organizations with precision and persistence. This whitepaper breaks down their full attack chain—from reconnaissance and credential theft to lateral movement, data exfiltration, and evasion techniques. Gain insights into their TTPs, discover detection opportunities across the kill chain, and learn how NetWitness empowers faster response and mitigation.






