Why Organizations Need Zero Trust Networks
Organizations need zero trust networks because traditional perimeter-based security no longer reflects how modern environments operate. A zero trust network removes implicit trust and continuously verifies users, devices, and applications, even after access is granted. Through zero trust networking, access is limited to specific resources rather than broad network connectivity, while zero trust network segmentation reduces lateral movement and constrains the impact of compromise. Together, these controls strengthen zero trust network security by aligning security decisions with identity, context, and behavior instead of location. For enterprises operating across cloud, SaaS, and hybrid environments, zero trust security provides a practical model for reducing risk in systems where trust can no longer be assumed.
Introduction
Zero-trust networks are no longer an emerging concept. For most enterprises, they are an architectural inevitability.
The perimeter is gone. Identity has become the primary control plane. Applications, users, and data are distributed across cloud, SaaS, and on-prem environments. In this reality, trust based on network location is not just outdated; it is dangerous.
But here’s the hard truth: many zero-trust initiatives fail to deliver their promised risk reduction.
Not because zero-trust is flawed, but because enterprises underestimate what it takes to operate, zero-trust at scale.
This blog goes beyond the basics. It examines how zero-trust networks actually work in enterprise environments, where implementations commonly break down, and what security leaders should evaluate before committing to a zero-trust architecture.
What Zero-Trust Networks Mean at Enterprise Scale
At a conceptual level, zero-trust networks operate on the principle of never trust, always verify. At enterprise scale, that principle translates into something more demanding:
- No implicit trust between users, devices, workloads, or applications
- Access decisions made continuously, not at login
- Network access replaced by application-level connectivity
- Segmentation enforced everywhere, not just at the perimeter
- Security controls informed by real behavioral and traffic data
A zero-trust network is not a product. It is a distributed enforcement model spanning identity, access, network segmentation, monitoring, and response.
Enterprises that treat zero-trust as an access control project usually discover gaps later, often during an incident.
Why Traditional Network Security Collapses Under Modern Enterprise Conditions
Traditional network security assumes that if something is “inside,” it is trustworthy. That assumption fails across every modern enterprise’s condition.
Structural weaknesses of legacy models
Implicit trust enables lateral movement
VPNs and flat internal networks give attackers exactly what they want after credential compromise: freedom to explore.
Visibility stops at the perimeter
Most legacy controls prioritize north-south traffic. East-west activity remains largely opaque.
Encrypted traffic hides malicious behavior
Attackers increasingly operate inside TLS. Appliance-based inspection does not scale well enough to see it.
Cloud and SaaS break network-centric controls
When applications are not on your network, network trust becomes irrelevant.
Zero-trust networks exist because these limitations are structural, not fixable with incremental tooling.
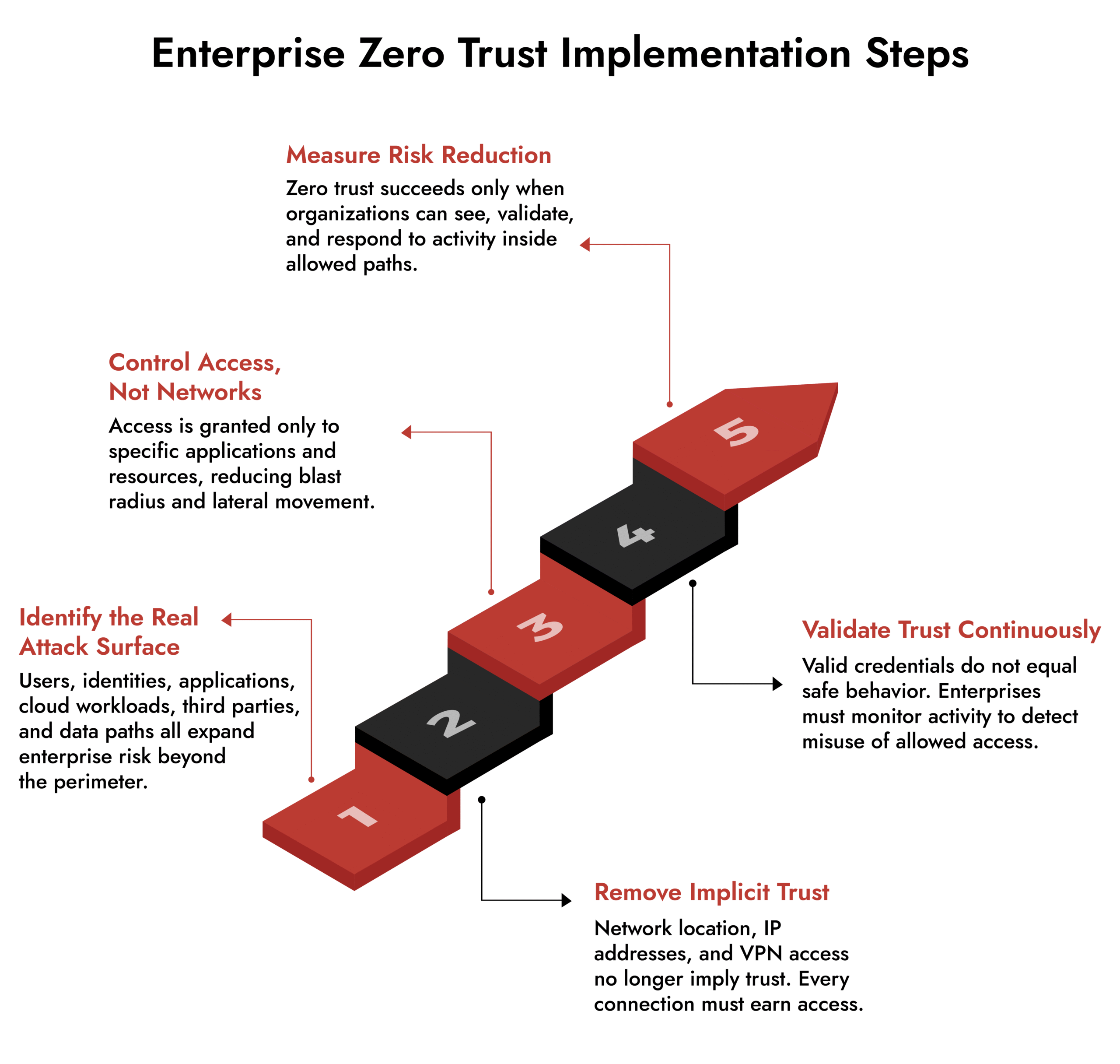
Core Zero-trust Principles That Actually Matter in Practice
Most enterprises can recite zero-trust principles. Fewer operationalize them consistently.
At scale, five principles determine whether a zero-trust network reduces risk or simply redistributes it.
1. No implicit trust, anywhere
Trust is never inherited from network location, IP address, or previous access.
2. Least-privileged, resource-level access
Users and systems connect to applications, not networks. Broad connectivity is eliminated.
3. Context and behavior matter as much as identity
Credentials are insufficient. Access decisions must factor in behavior, device posture, and anomalies.
4. Continuous verification, not one-time authorization
Trust must be reassessed throughout a session, not only at entry.
5. Segmentation without blind spots
Segmentation must be observable. Otherwise, it becomes a false sense of control.
The last point is where many enterprises’ zero-trust strategies quietly fail.
How Zero-trust Networks Work in Real Enterprise Architectures
At a high level, zero-trust networking replaces perimeter enforcement with continuous, policy-driven access decisions.
In practice, a typical enterprise zero-trust flow looks like this:
- An entity requests access to a specific application or service
- Identity is authenticated via an IdP
- Device posture and security state are validated
- Contextual risk is calculated
- Policy is enforced per session
- Direct application access is established
- Activity is monitored continuously
What matters is not this flow itself.
What matters is what feeds it and what validates it.
Zero-trust Network Segmentation: Control Without Visibility Is a Liability
Zero-trust network segmentation is often positioned as the primary defense against lateral movement. That is true, but incomplete.
Segmentation defines where traffic is allowed. It does not explain what that traffic is doing.
In enterprise environments, segmentation typically spans:
- Application tiers
- Business units
- Sensitivity levels
- Cloud and on-prem workloads
Where segmentation fails in practice
- Allowed paths are rarely inspected deeply
- East-west traffic goes unanalyzed
- Encrypted traffic obscures intent
- Policy drift creates unknown exposure
Attackers do not break segmentation rules, instead they abuse the ones that are allowed.
A mature zero-trust network must be able to:
- Observe traffic within segments
- Detect abnormal behavior inside allowed access
- Correlate identity with network activity
- Validate that segmentation policies actually reduce risk
Without this, segmentation becomes a static design assumption.
Proactive Network Threat Detection with NetWitness® NDR
-Spot threats fast with AI-driven analytics.
-See everything across your network and cloud traffic.
-Investigate efficiently with built-in forensic tools.
-Adapt and scale to meet growing security needs.

Zero-trust Networks and the Remote Workforce Reality
Remote access is where zero-trust promises immediate value and often delivers it, partially.
Replacing VPNs with identity-based access reduces exposure dramatically. However, remote work also increases dependency on credentials and SaaS access.
Enterprises must answer:
- What does normal remote access behavior look like?
- How do we detect abuse of valid credentials?
- Can we investigate incidents without network visibility?
Zero-trust controls access. Operations teams still need insight after access is granted.
Where Enterprise Zero-Trust Implementations Break Down
Most zero-trust programs fail quietly, not catastrophically.
Common breakdown points include:
- Zero-trust access without behavioral monitoring
- Segmentation without east-west visibility
- Identity signals without network context
- Alerting without investigation depth
- Policy enforcement without validation
At this stage, enterprises realize zero-trust has shifted the problem, not solved it.
This is the point where security leaders start evaluating detection and response platforms to operationalize zero-trust.
Operationalizing Zero-Trust With Detection and Network Visibility
To function as a security model rather than an access framework, zero-trust networks require:
- Continuous monitoring of segmented traffic
- Behavioral detection across users and applications
- Correlation between identity, network, and activity
- Rapid investigation when trust assumptions fail
Platforms such as NetWitness are commonly introduced at this stage, not to control access, but to validate and enforce zero-trust outcomes.
In mature architectures:
- Zero-trust defines access boundaries
- Detection platforms observe what happens inside those boundaries
- Response workflows close the loop when policy is abused
This combination turns zero-trust from a design philosophy into an operational security strategy.
Business Outcomes Enterprises Expect from Mature Zero-trust Networks
When zero-trust is implemented and operationalized correctly, enterprises see measurable outcomes:
Reduced breach impact
Attackers cannot move freely, and abnormal behavior is detected earlier.
Lower dwell time
Visibility into east-west traffic accelerates investigation and containment.
Better risk governance
Access policies are continuously validated against real behavior.
Scalable security operations
One architectural model supports cloud, SaaS, and remote access.
Improved executive confidence
Security decisions are backed by evidence, not assumptions.
What Enterprises Should Evaluate Before Committing to Zero-trust
For decision-stage buyers, the question is no longer “should we adopt zero-trust?”
The real questions are:
- How do we detect misuse of allowed access?
- Can we see encrypted east-west traffic?
- How do we investigate incidents in segmented environments?
- What validates that zero-trust policies actually reduce risk?
- How do security operations adapt after zero-trust is deployed?
Zero-trust networks succeed or fail based on how well these questions are answered.
Final Perspective
Zero-trust networks redefine how trust is granted. They do not eliminate the need to observe, detect, and respond.
At enterprise scale, zero-trust without visibility is incomplete. Zero-trust without detection is fragile. Zero-trust without operational validation is a design exercise.
The organizations that succeed with zero-trust are the ones that treat it not as a control, but as a continuously tested security model.
Frequently Asked Questions
1. What are zero-trust networks and how do they improve cybersecurity?
Zero-trust networks remove implicit trust and require continuous verification, reducing attack surfaces and limiting lateral movement.
2. How does zero-trust differ from traditional network security?
Traditional security trusts users once inside the network. Zero-trust networking verifies every access request continuously.
3. Why is zero-trust important for enterprises?
Enterprises operate across hybrid, cloud, and remote environments where perimeter-based security no longer works.
4. How does Zero Connect improve network security?
Zero Connect provides application-level access instead of network-level access, reducing exposure and attack surface.
5. What is the best zero-trust network providers for enterprise security?
Enterprises often combine zero-trust access providers with visibility and detection platforms to fully operationalize zero-trust.
6. How do zero-trust networks work with remote workforce setups?
Zero-trust secures remote access through identity and context-based controls while limiting network exposure.
DORA Compliance with NetWitness® Network Detection & Response (NDR)
Strengthen Digital Operational Resilience with Deep Network Visibility
Meet EU DORA requirements with continuous network monitoring, advanced threat detection, and automated response across complex financial environments.






