Key Insights
- Network segmentation focuses on limiting damage. It divides a flat network into smaller areas, ensuring that when an issue arises, it remains limited rather than proliferating widely.
- Contemporary settings do not depend on one form of control. Segmentation today isn’t just a checklist, it’s about bringing together firewalls, VLANs, subnets, and access rules across on-site systems, cloud environments, and remote users. Major incidents like WannaCry and Colonial Pipeline, along with tighter regulations such as PCI DSS 4.0 and NIS2, have made it clear that segmentation is essential.
- This guide outlines the genuine essence of network segmentation, its present importance, and methods to implement it without leading to operational disruptions
Introduction
Most breaches don’t start with a total takeover. They start small, then spread quietly across flat networks that were never designed to contain failure. That’s where network segmentation comes into play.
Fundamentally, network segmentation determines which parties can communicate with each other, the circumstances under which they can do so, and the reasons behind it. It divides essential systems, restricts excessive access, and transforms internal networks from free-flowing highways into regulated intersections. In 2024, with hybrid settings, operational technology, and widespread encrypted traffic, segmentation is essential. It’s a baseline for internal network security.
What this really means is simple: when attackers get in, segmentation determines whether they stall out or move freely.
What is Network Segmentation?
Network segmentation is a security method that divides an internal network into separate parts. This limits access, reduces the spread of attacks, and improves internal network security.
Network segmentation entails dividing a network into smaller, separate network segments and enforcing stringent communication policies between them. These segments can be based on:
- Business function
- Risk level
- Data sensitivity
- User role
- Device type
The goal isn’t complexity. The goal is control.
When implemented correctly, network segmentation security ensures that a compromise in one segment does not automatically expose the rest of the environment.
Why Network Segmentation Matters for Security
Network segmentation limits damage by blocking attackers from moving freely across the network. It reduces their speed, restricts side movement, and maintains the impact within the bounds.
The 2024 recommendations from CISA and NIST emphasize this point clearly. The majority of serious violations occur not due to a failure of the perimeter. They intensify because internal networks were overly accessible once that initial foothold was gained. They intensify because internal access was not monitored. Segmentation addresses this by applying least-privilege principles where it truly matters, within the network. After attackers overcome the initial defenses, flat networks facilitate the remaining harm.
Network segmentation security changes that equation.
It helps organizations:
- Contain ransomware before it spreads
- Isolate compromised credentials
- Protect crown-jewel assets
- Maintain operational continuity during incidents
In short, segmentation buys time. And in incident response, time matters.
Advantages of Network Segmentation in Modern Enterprises
The true benefit of network segmentation extends far beyond merely halting attacks. It ensures that systems remain accessible during events, simplifies the process of demonstrating compliance, and provides structure to complex settings that would otherwise be difficult to manage or comprehend.
Core advantages of network segmentation
- Reduced blast radius: Attacks stay local instead of becoming systemic.
- Improved internal network security: Fewer implicit trust paths.
- Faster investigations: Clear traffic boundaries simplify analysis.
- Policy clarity: Access rules align with business intent.
- Operational resilience: Critical services remain available during incidents.
Gartner’s 2024 recommendations emphasize that segmentation is effective only when you can consistently monitor and manage activities occurring within the network.
These are not theoretical benefits. They show up in mean time to detect, mean time to respond, and real incident cost reduction.
Network Segmentation vs. Traditional Network Design
Traditional networks prioritize connectivity. Network segmentation prioritizes controlled communication.
Legacy designs assume internal trust. Modern threats exploit that assumption.
| Traditional Networks | Segmented Networks |
| Flat or loosely separated | Clearly defined network segments |
| Implicit trust | Explicit policy enforcement |
| Perimeter-focused | Internal network security focused |
| Limited containment | Built-in breach containment |
Segmentation doesn’t eliminate breaches. It makes them survivable.
Network Segmentation Best Practices That Actually Work
Effective network segmentation relies on visibility, policy precision, and continuous validation.
Network segmentation best practices
- Start with visibility- You can’t segment what you don’t understand. Full traffic visibility across north-south and east-west flows matters.
- Segment by risk, not convenience- Group assets based on exposure and impact, not org charts.
- Enforce least privilege- Default deny between segments. Allows only required communication.
- Design for OT and IT segmentation- OT environments require segmentation without disrupting availability or safety.
- Continuously monitor and validate- Segmentation fails when policies drift or exceptions accumulate.
NIST SP 800-207 and SP 800-53 updates in 2024 emphasize continuous monitoring as a requirement, not a nice-to-have.
OT and IT Segmentation: Why It’s Non-Negotiable
OT and IT segmentation prevent business systems from becoming attack paths into critical operations.
Industrial environments face unique constraints:
- Legacy protocols
- Safety requirements
- Limited patch cycles
A single flat network connecting IT and OT systems invites catastrophe. OT and IT segmentation isolates control systems while still enabling required visibility and monitoring.
This approach aligns with CISA’s Cross-Sector Cybersecurity Performance Goals updated in 2024, which explicitly calls out segmentation for critical infrastructure protection. 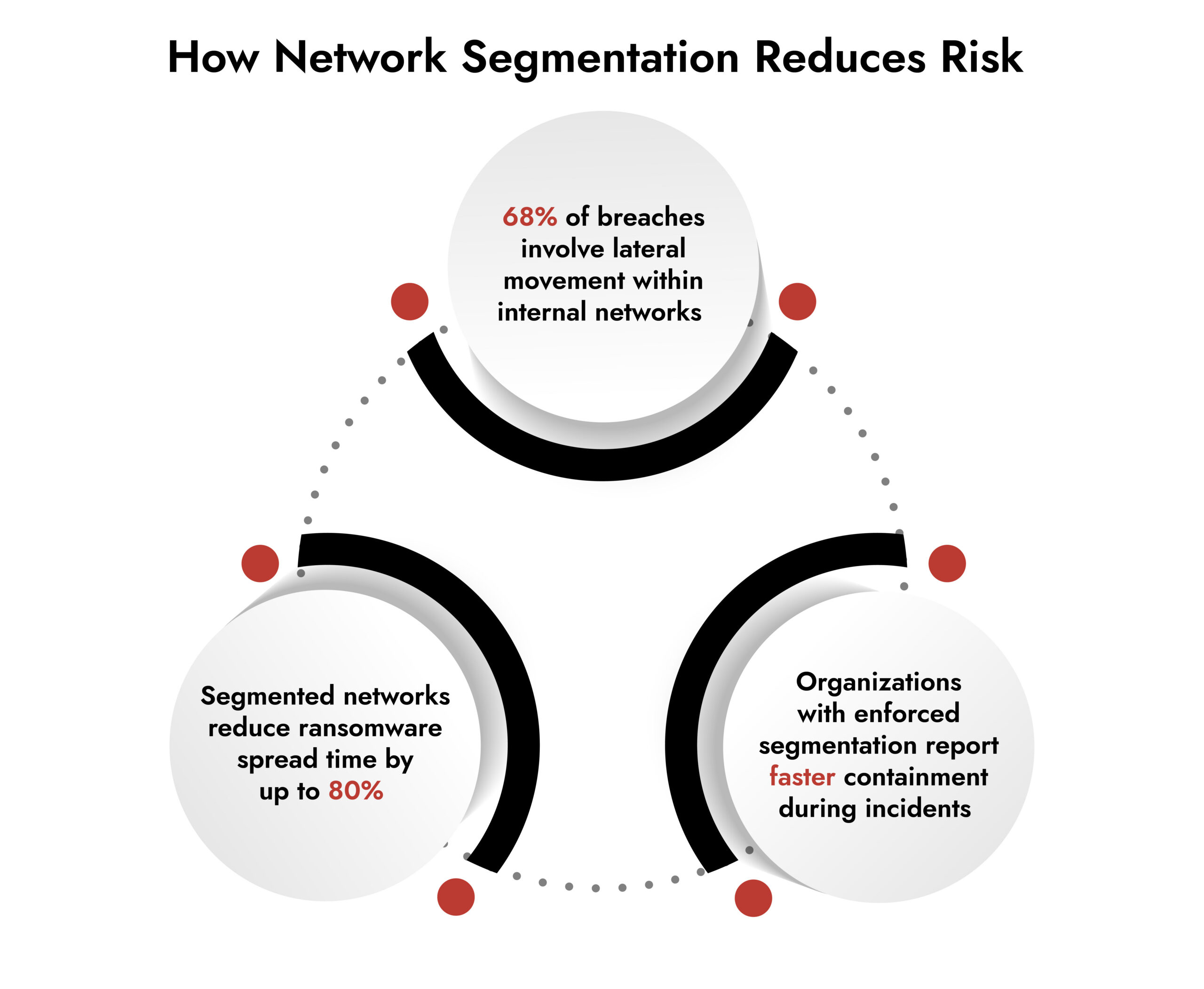 Network Segmentation Tools: What Actually Matters
Network Segmentation Tools: What Actually Matters
Network segmentation tools must combine visibility, policy enforcement, and detection across all network segments.
Key capabilities to look for:
- Full packet or enriched session visibility
- Support for encrypted network traffic analysis
- Policy validation across hybrid environments
- Integration with detection and response workflows
Segmentation without monitoring creates blind spots. Monitoring without segmentation creates noise. Mature environments combine both.
Unify IT and OT Threat Detection with NetWitness® and DeepInspect
-Correlate IT and OT telemetry for end-to-end operational visibility.
-Detect advanced threats across industrial and enterprise networks with protocol-level intelligence.
-Accelerate investigations using enriched OT context and unified analytics.
-Reduce blind spots and strengthen response across converged IT/OT environments.
Where Network Detection and Response Fits In
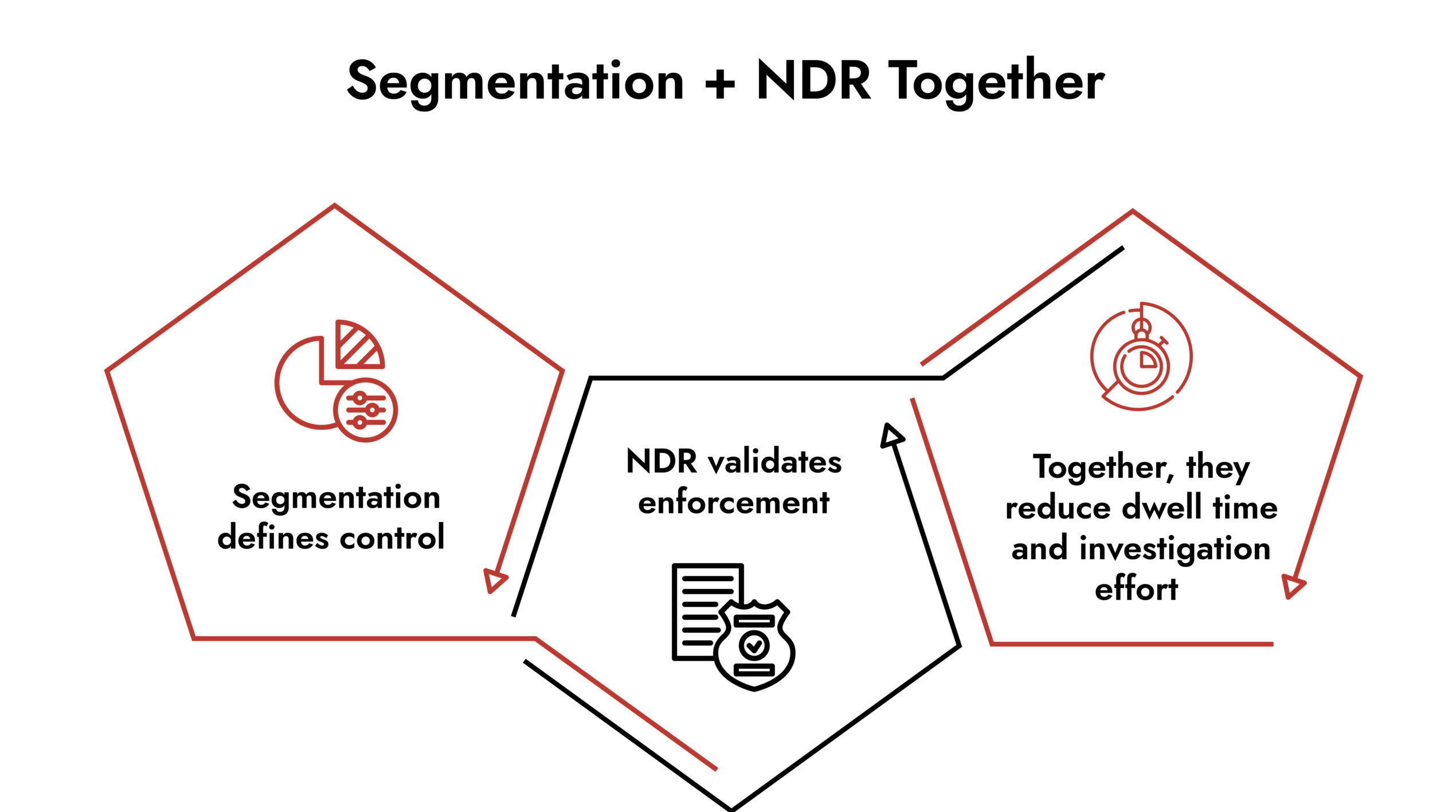
Segmentation defines boundaries. Network Detection and Response (NDR) validates that those boundaries hold under real-world conditions.
Common NDR challenges enterprises face
- Data integration across segmented environments
- Visibility gaps in encrypted or OT traffic
- Operational overhead during deployment
- Compliance validation across segments
Improving NDR deployment in segmented networks
- Standardize telemetry sources early
- Align NDR policies with segmentation logic
- Use services to accelerate tuning and onboarding
- Validate compliance requirements by segment
Managed services often help organizations stabilize NDR deployments faster, especially in regulated industries where tuning errors carry real consequences.
Network Segmentation Security in Compliance-Heavy Industries
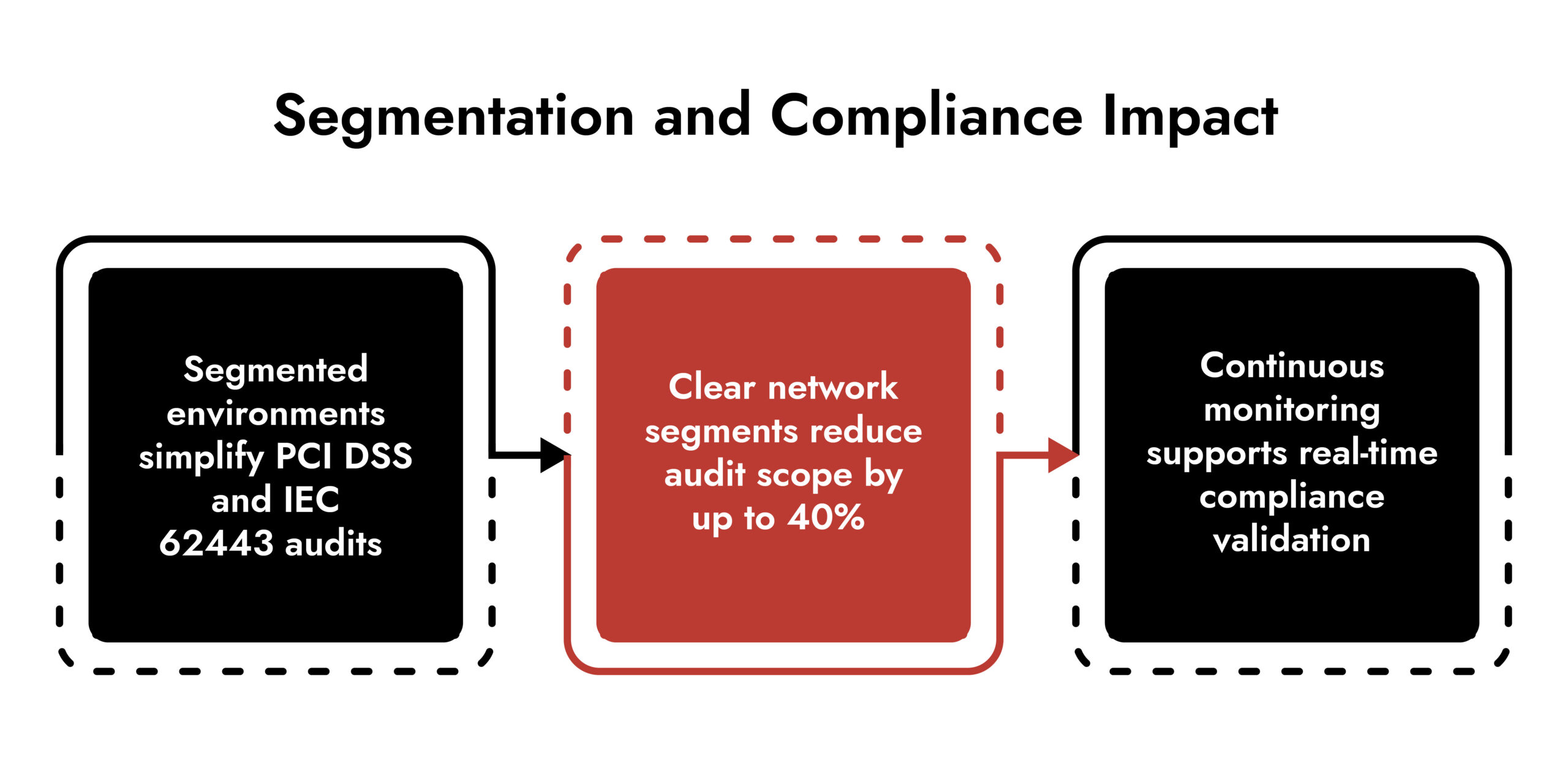
Network segmentation supports compliance by limiting audit scope and enforcing enforceable controls.
Regulated industries rely on segmentation to:
- Separate regulated data environments
- Enforce access controls with evidence
- Reduce compliance drift over time
Standards including NIST, ISO 27001, and industry-specific frameworks consistently reference segmentation as a control that auditors expect to see implemented and maintained.
How NetWitness Supports Network Segmentation Security
Network segmentation succeeds or fails based on visibility and validation.
NetWitness Network Detection and Response provides assurance that segmentation behaves as designed under real world conditions. This is true even if the traffic is encrypted or linked to OT systems.
Rather than replacing segmentation controls, NetWitness strengthens them by exposing what actually happens inside the network. That feedback loop matters when segmentation evolves across hybrid and operational environments.
“During active incidents, segmentation questions are rarely theoretical. Security teams need to know which segments were touched, how traffic moved, and whether boundaries were crossed. NetWitness delivers that clarity by reconstructing network activity within and between segments, turning segmentation from a static design into a measurable, defensible security control.”
— Nolan Ross, Sales Engineer, NetWitness
 Conclusion
Conclusion
Network segmentation isn’t a theoretical architecture choice. It’s a practical decision about how much damage you allow when something goes wrong.
Flat networks fail quietly until they fail catastrophically. Segmented networks fail loudly and locally. That difference shapes outcomes.
As environments get more complex, segmentation only works when it’s backed by continuous visibility. Teams that treat it as an ongoing control, not a one-time setup, contain threats faster and limit real damage.
If you’re questioning how well your segmentation holds up today, start by validating what you can actually see. Explore how deeper network visibility with NetWitness can strengthen segmentation and internal security.
Frequently Asked Questions
1. Why is network segmentation important for security?
Network segmentation restricts lateral movement by separating systems into regulated network segments. It minimizes attack proliferation, enhances internal network protection, and boosts containment during events.
2. What are the benefits of network segmentation in compliance-heavy industries?
Network segmentation aids compliance by narrowing audit scope, implementing least privilege, and offering clear proof of access controls. Regulated settings depend on segmentation to isolate sensitive systems and information.
3. Which vendors provide automated network segmentation solutions?
Numerous security and infrastructure companies provide automated network segmentation tools that come with integrated policy enforcement and monitoring capabilities. Choice is based on visibility depth, OT assistance, and operational intricacy.
4. What are the best network segmentation solutions for enterprise security?
The most effective network segmentation strategies integrate policy management, insight, and ongoing verification. Businesses focus on options that facilitate hybrid settings and connect with detection and response systems.
5. What tools support effective network segmentation?
Tools for effective network segmentation comprise firewalls, identity-driven access controls, and network detection and response systems. They jointly implement segmentation policies and validate real-world actions.
6. How does network segmentation support OT and IT security?
OT and IT segmentation isolates operational systems from business networks, reducing risk while maintaining availability. It prevents IT-based attacks from cascading into critical infrastructure.
Proactive Network Threat Detection with NetWitness® NDR
-Spot threats fast with AI-driven analytics.
-See everything across your network and cloud traffic.
-Investigate efficiently with built-in forensic tools.
-Adapt and scale to meet growing security needs.






