What Strong NDR Security Performance Actually Means
Good NDR security does not mean more alerts, more dashboards, or more machine learning labels. It means consistent, explainable detection across north–south and east–west traffic, high-fidelity visibility into sessions and artifacts, and faster investigation without guesswork. High-performing NDR security platforms close visibility gaps, reduce dwell time, and integrate cleanly with existing security operations without adding operational drag. If detection does not change outcomes, it is not good for detection.
Why “Detection” is the Wrong Word to Obsess Over
Most teams say they want better detection. What they actually need is better outcomes.
NDR security sits at the center of that gap. When it works, it exposes attacker behavior that endpoint tools miss, cloud controls can’t see, and logs fail to explain. When it fails, it floods analysts with alerts that look impressive and deliver nothing.
Here’s the uncomfortable truth: many organizations evaluate NDR security performance using the wrong metrics. Alert volume. Model accuracy. Feature checklists. None of those answer the only question that matters: Did the platform help you understand, contain, and eradicate a real threat faster?
Let’s break down what good detection actually looks like, how to measure it, and where most NDR deployments go off the rails.
What “Good Detection” Really Means in NDR
Good detection reveals attacker behavior with context, precision, and speed, without relying on guesswork or blind trust in automation.
Strong Network Detection and Response platforms focus on behavior over signatures, evidence over assumptions, and visibility over labels. They show you what happened, how it happened, and where to act next.
Good detection delivers three things consistently:
- High-confidence signals rooted in real network activity
- Explainable evidence analysts can validate
- Operational relevance that drives response, not noise
If your NDR security platform cannot reconstruct sessions, extract artifacts, and correlate activity across time, it is detecting symptoms, not threats.
The Core Metrics That Actually Measure NDR Security Performance
Measure NDR security performance by how well it reduces uncertainty, investigation time, and attacker dwell time. Forget vanity metrics. Focus on outcomes.
Key indicators that matter:
- Time to clarity: How quickly analysts understand what actually happened
- Detection fidelity: Ratio of actionable detections to false positives
- Visibility coverage: Percentage of network segments, protocols, and environments observed
- Investigation depth: Ability to pivot from alert to packet, session, and payload
- Response acceleration: Reduction in time to containment
According to the 2024 Verizon DBIR, organizations with strong network visibility reduced investigation time by over 30 percent in advanced intrusion cases. That is NDR security performance that changes outcomes.
Visibility is the Foundation of Network Threat Detection
Without full network visibility, NDR security performance collapses, no matter how advanced the analytics look. Many tools claim visibility. Few deliver it.
True NDR visibility includes:
- Full packet capture where it matters
- Protocol-agnostic inspection
- North-south and east-west coverage
- On-prem, cloud, and hybrid environments
This is where network performance monitoring and network performance management intersect with security.
Network performance monitoring tools already collect telemetry. High-performing NDR security platforms extend that telemetry into deep behavioral analysis, not just health metrics.

Common Technical Challenges in Implementing NDR Security
Most NDR deployments struggle due to visibility gaps, data overload, and operational complexity, not weak analytics.
The most common challenges include:
- Encrypted traffic blind spots without proper inspection strategies
- Overreliance on machine learning without analyst context
- Tuning fatigue caused by noisy detections
- Storage and scale constraints for packet-level data
These challenges directly degrade NDR security performance, even when the platform itself is capable.
Proactive Network Threat Detection with NetWitness® NDR
-Spot threats fast with AI-driven analytics.
-See everything across your network and cloud traffic.
-Investigate efficiently with built-in forensic tools.
-Adapt and scale to meet growing security needs.

Improving Data Integration During NDR Implementation
Integration succeeds when NDR feeds evidence, not just alerts, into the broader security stack.
To improve integration:
- Normalize NDR outputs before SIEM ingestion
- Pass session context, not just detection labels
- Align NDR detections with SOAR playbooks early
- Treat NDR as a source of truth, not a secondary signal
Strong network performance tools already integrate operational data. High-performing NDR security platforms apply the same discipline to threat data.
Managed Services and Deployment Support Matter More Than Features
NDR security performance improves dramatically when deployment, tuning, and ongoing management receive expert oversight. Many organizations underestimate this.
Services that improve outcomes include:
- Sensor placement strategy
- Detection tuning aligned to business risk
- Ongoing validation against real attacker techniques
- Analyst training focused on investigation workflows
For regulated industries, managed services also help address compliance challenges around data retention, inspection policies, and audit readiness. 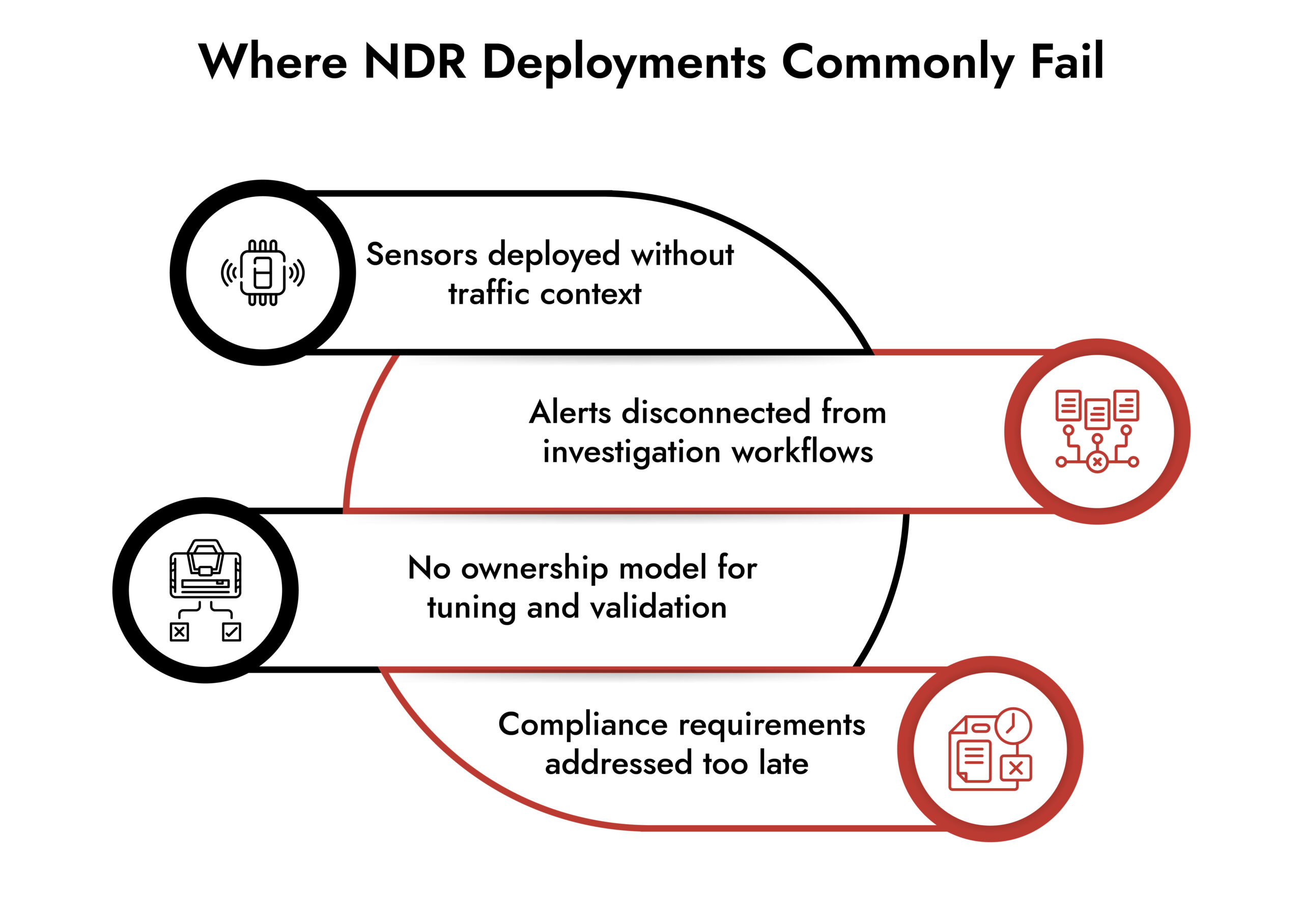
Compliance and Encrypted Traffic: The Hard Problems
Effective NDR security balances visibility with compliance and privacy without sacrificing detection quality.
In regulated environments, key challenges include:
- Inspecting encrypted traffic without violating policy
- Retaining packet data within regulatory limits
- Proving detection decisions during audits
Modern network threat detection approaches rely on selective decryption, metadata enrichment, and behavioral correlation to maintain compliance while preserving insight.
Where NetWitness Fits in High-Performance NDR Security
NetWitness approaches NDR security from an evidence-first perspective.
Instead of abstract detections, it focuses on:
- Full-session reconstruction across protocols
- Artifact extraction for direct validation
- Visibility across hybrid and complex networks
- Analyst-driven investigation paths
This approach aligns detection with investigation and response, improving NDR security performance without increasing operational burden. The result is fewer assumptions and faster certainty. 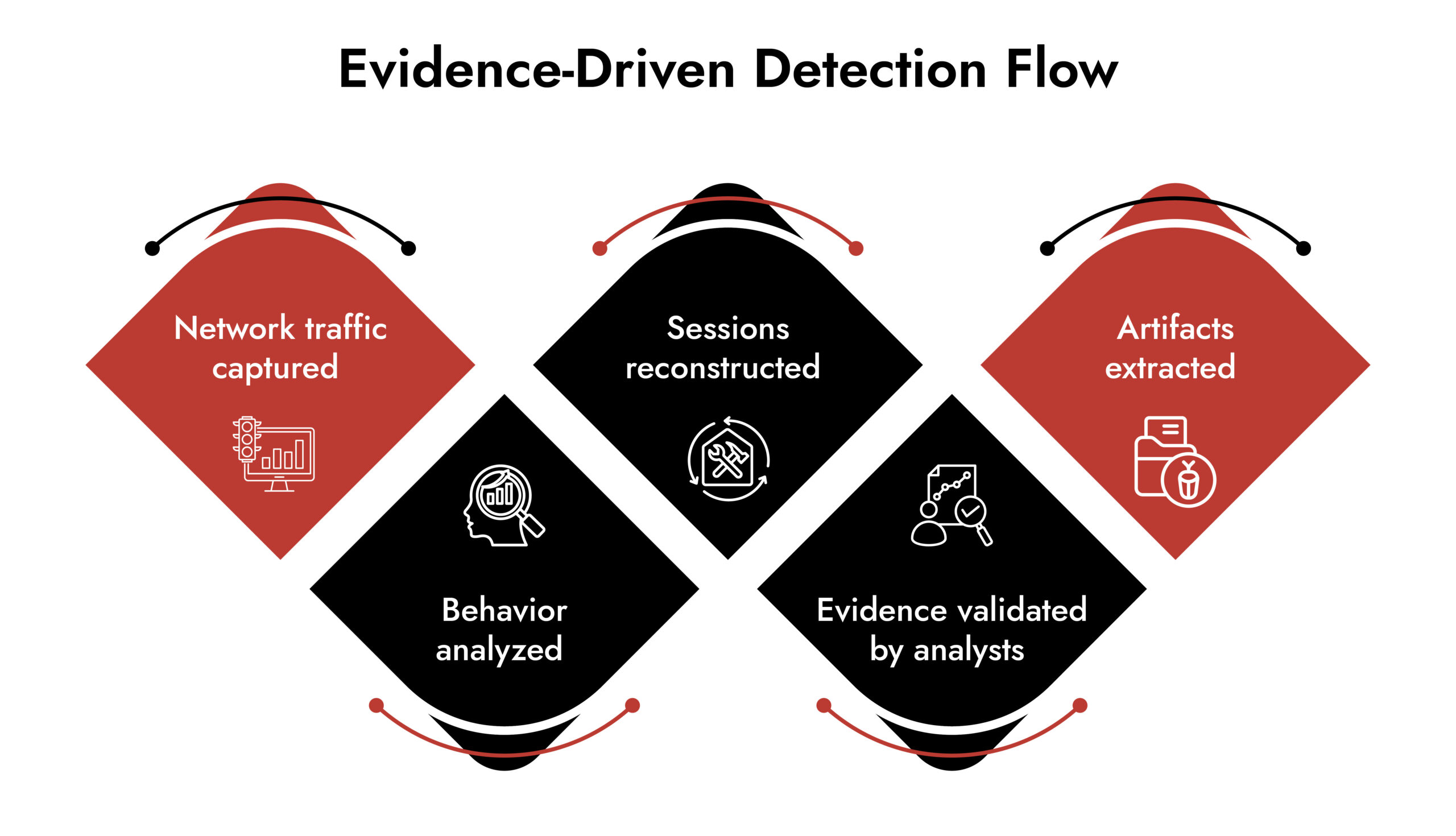
Conclusion
Good detection does not impress dashboards. It empowers people.
High-performing NDR security reduces uncertainty, accelerates response, and gives defenders confidence in their decisions. It replaces guesswork with evidence and noise with clarity.
If your NDR platform does not help you understand the story behind the traffic, it is time to reassess what you define as “good detection.”
Frequently Asked Questions
1. How to measure NDR security performance?
Measure NDR security performance by reduced investigation time, improved detection fidelity, and broader network visibility. Focus on outcomes, not alert volume. Strong performance shows up in faster containment and clearer incident understanding.
2. What does “good detection” look like in an NDR platform?
Good detection in Network Detection and Response provides explainable alerts backed by session and packet evidence. Analysts can validate findings without relying on opaque scores. The detection directly supports response actions.
3. How does NDR integrate with SIEM and SOAR for better performance?
NDR integrates best when it feeds contextual evidence into SIEM and triggers SOAR workflows based on validated detections. This improves response speed and reduces false positives. Integration quality directly affects NDR security performance.
4. What role does AI and machine learning play in NDR performance?
AI supports pattern recognition and prioritization in NDR security, but it does not replace visibility or analyst judgment. Machine learning works best when paired with evidence-driven workflows. Overreliance without context reduces trust.
5. Can NDR detect threats in encrypted traffic?
Yes. Modern network threat detection techniques use selective decryption, metadata analysis, and behavioral correlation. This approach maintains compliance while preserving visibility. Effective NDR security does not require full decryption everywhere.
6. Which services help with deployment and tuning of NDR security?
Deployment, tuning, and managed services significantly improve NDR security performance. These services ensure correct sensor placement, integration, and ongoing validation. They reduce operational friction and improve detection outcomes over time.
Unify IT and OT Threat Detection with NetWitness® and DeepInspect
-Correlate IT and OT telemetry for end-to-end operational visibility.
-Detect advanced threats across industrial and enterprise networks with protocol-level intelligence.
-Accelerate investigations using enriched OT context and unified analytics.
-Reduce blind spots and strengthen response across converged IT/OT environments.