How an Incident Response Retainer Works in 2026?
A cyber incident response retainer activates the moment a verified security incident occurs. Because escalation paths, pricing, and access permissions are already established, the incident response service team can begin investigation immediately.
This removes the delays typically seen when organizations attempt to secure incident response in cyber security during an active breach.
With a DFIR retainer in place, responders can:
- Initiate digital forensics and incident response analysis within hours
- Contain threats before they spread across environments
- Preserve forensic evidence for legal, compliance, and recovery efforts
- Support structured incident response management with documented procedures
This model reduces attacker dwell time and improves overall cybersecurity incident response effectiveness.
Introduction
A ransomware attack hits at 2 AM. Systems are encrypted. Customer data is at risk. The internal team is overwhelmed. Finding qualified incident response support during an active crisis means paying premium rates while critical hours slip away.
This scenario is no longer hypothetical.
Organizations that recover quickly from cyber incidents share one defining characteristic: they secured an incident response retainer before the crisis began.
A retainer does not prevent incidents. It prevents panic, delay, and costly missteps when incidents occur.
What Is an Incident Response Retainer
An incident response retainer is a pre-arranged agreement between an organization and a cybersecurity service provider. It guarantees access to expert cybersecurity incident response services during a breach and provides supplemental support to strengthen response readiness over time.
Under a cyber incident response retainer, organizations pay an annual fee to secure priority access to a dedicated cyber incident response team. In return, they receive:
- Guaranteed response times
- Pre-negotiated pricing
- A response team already familiar with their environment
Unlike emergency engagements during an attack, incident response retainer services operate with documented procedures, pre-established communication paths, and secure access already in place. This allows responders to begin containment within hours instead of days. That difference defines outcomes.
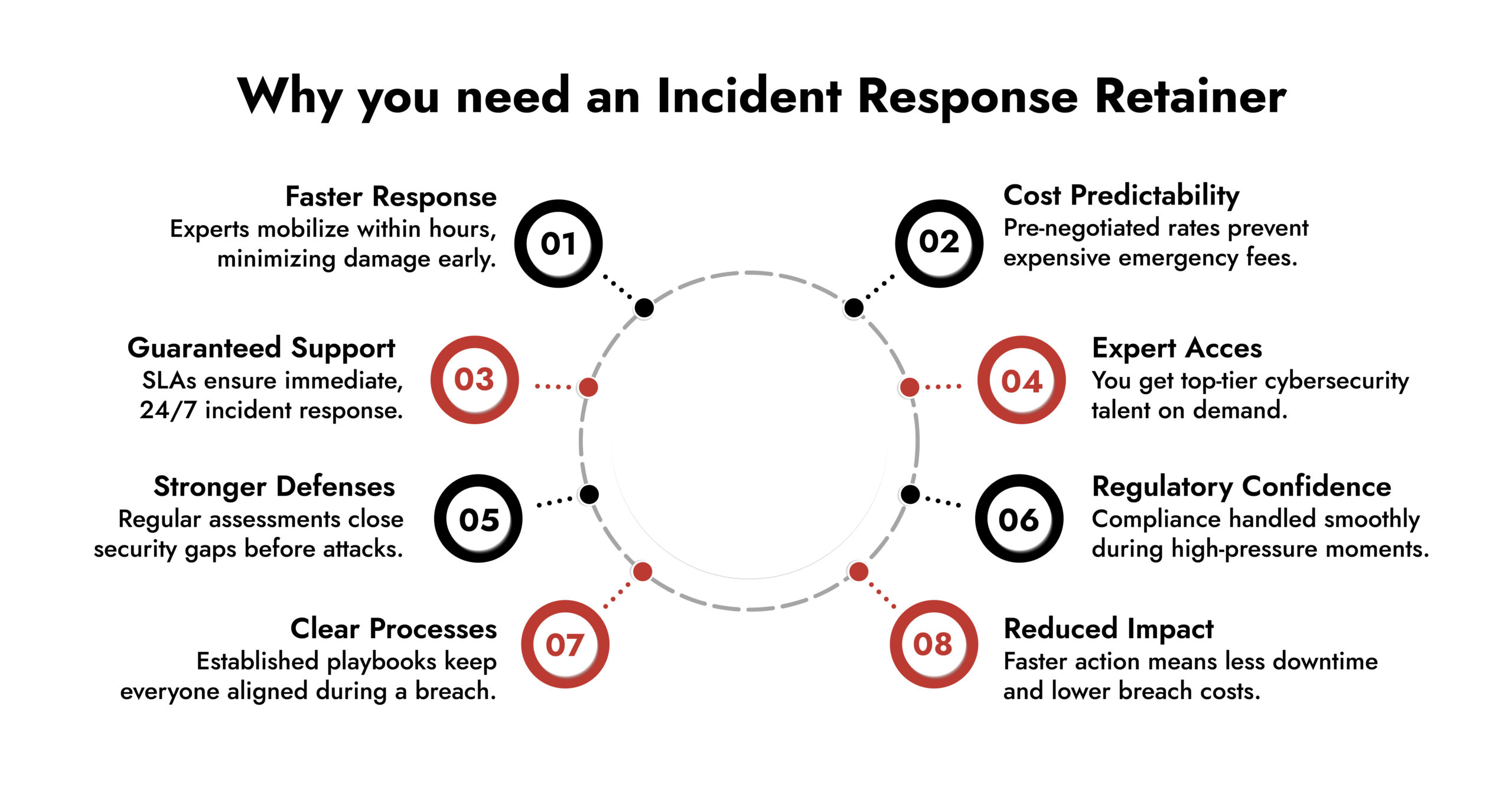
The Cost of Delayed Response in Cybersecurity Incident Response
Without an incident response retainer, organizations lose critical time during breaches.
Common delays include:
- Searching for available incident response service providers
- Legal and procurement approvals
- Emergency contract negotiations
- Environment onboarding and access setup
During these delays, attackers expand access, escalate privileges, and exfiltrate sensitive data.
Organizations without retainers often experience 2 to 15 days before meaningful investigation begins.
Organizations with incident response retainer services begin analysis within hours.
This difference dramatically reduces breach impact and recovery timelines.
Effective incident response management depends on preparation, not reaction.
What Incident Response Retainer Services Deliver in 2026
Incident response retainer services provide capabilities that most internal teams cannot scale on demand.
Pre-Incident Planning
Pre-incident planning ensures responders understand the environment before a crisis occurs. NetWitness Incident Response documents network architecture, identifies critical assets, maps data flows, and establishes secure remote access during onboarding.
When incidents happen, there is no learning curve.
Guaranteed Response Times
Service-level agreements define exactly when response begins and when initial analysis is delivered. Organizations are not waiting in queue behind other breaches.
Specialized Cybersecurity Incident Response Expertise
A dedicated cybersecurity incident response team brings forensic investigation, malware analysis, threat intelligence, and compliance knowledge. Analysts examine logs, network traffic, and host data to identify beaconing, lateral movement, command-and-control activity, and data exfiltration.
Regulatory and Legal Support
Experienced responders guide organizations through GDPR, HIPAA, and state notification requirements. Documentation and evidence of handling are built into the response process, not added later under pressure.
NetWitness Retainer Service Levels
Organizations select coverage matched to their risk profile:
| Level | Annual Hours | Initial Response SLA | Initial Analysis SLA | Key Deliverables |
| Silver | 60 hours | 6 hours | 24 hours | Preliminary analysis report |
| Gold | 120 hours | 3 hours | 12 hours | Preliminary analysis report |
| Platinum | 240 hours | 3 hours | 12 hours | Preliminary analysis, incident discovery report, executive board readout |
Silver retainers fit organizations with moderate risk and limited budgets. Gold supports higher threat exposure and faster response requirements. Platinum provides comprehensive coverage for critical operations and includes proactive compromise assessments.
All offerings are product agnostic and do not require specific security tools.
Unused hours can be applied to proactive services such as tabletop exercises, threat hunting, or security assessments. Custom retainers are available to support complex or multi-environment needs.
Complementary Cybersecurity Incident Response Services
NetWitness retainers integrate seamlessly with additional cybersecurity incident response services.
IR Discovery (Compromise Assessment) –
This service identifies adversary presence before alerts trigger. Consultants analyze logs, network data, and hosts, examine malware behavior, and answer critical questions:
- Are attackers already present?
- What systems are compromised?
- Has data been exfiltrated?
IR Rapid Engagement (Breach Response)
When incidents are confirmed, rapid engagement delivers immediate surge support. Analysts deploy tooling, perform live investigations, and coordinate executive leadership and legal counsel.
Both services include detailed findings and status reporting.
Why 70% Are Dissatisfied With Response Time
Research shows that 70% of organizations are dissatisfied with response speed. The reasons are consistent:
- Limited access to qualified responders during peak incident periods
- Long learning curves for unfamiliar environments
- Procurement delays during active breaches
- Insufficient internal forensic and compliance expertise
An incident response retainer addresses each issue through guaranteed access, preparation, and a standing critical incident response team.
Why Organizations Struggle With Incident Response Management
Many organizations lack sufficient incident response readiness.
Common challenges include:
- Limited access to digital forensics and incident response expertise
- Delays in engaging incident response services
- Insufficient internal forensic capabilities
- Lack of structured incident response management processes
Incident response retainer services eliminate these barriers.
Organizations gain guaranteed access to expert responders.
Rapid, Expert Response with NetWitness® Incident Response Services
-Accelerate threat containment with experienced IR specialists.
-Investigate effectively using advanced forensics and analytics.
-Minimize business impact with fast, guided remediation.

Integration With Security Operations
Retainers are not replacements for internal teams. They extend them.
Organizations with SOCs use retainers for surge capacity and advanced investigations. Smaller teams rely on retainers for broader cybersecurity incident response coverage.
NetWitness works directly with customer technical contacts, requiring appropriate system access, remote connectivity, and defined maintenance windows for investigative tooling.
The Real Cost of Being Unprepared for a Cyber Incident Response
Extended dwell time increases impact. Missed deadlines trigger penalties. Recovery stalls without confidence. Emergency consulting rates exceed retainer costs.
Global breach costs now average nearly $5 million. A breach is no longer a question of if. It is a question of readiness.
Making the Decision for a Cyber Incident Response Retainer
Organizations should evaluate:
- Risk profile based on industry targeting and data sensitivity
- Internal capabilities and forensic maturity
- Regulatory obligations and reporting timelines
- Service level alignment with business criticality
NetWitness maintains an accredited global cyber incident response team, supporting enterprises and government agencies against sophisticated attacks.
The Bottom Line
Incident response retainers compress timelines from days to hours. They reduce uncertainty, support compliance, and limit damage when incidents occur on attacker schedules.
NetWitness Incident Response Retainer operates as a product-agnostic service that strengthens existing security programs and often becomes the point of discovery during attacks.
Preparation determines outcomes. Retainers make preparation operational.
Frequently Asked Questions
1. What is an incident response retainer?
A pre-negotiated agreement guaranteeing immediate access to expert incident response and cybersecurity incident response services during a breach.
2. How much does an incident response retainer cost?
Pricing varies by service level, organization size, and risk exposure.
3. How does an incident response retainer help organizations?
It reduces response time, lowers breach of impact, and provides access to a specialized cyber incident response team.
4. How does an incident response retainer work during a breach?
Responders already familiar with the environment mobilize within hours to begin containment and investigation.
Fortify Cyber Defense with Threat Intel + Incident Response
Combine real-time threat intelligence with rapid incident response workflows.
Detect advanced threats before they strike — armed with enriched context and actionable alerts.
Respond faster and smarter with orchestrated, data-driven playbooks.
Build a resilient security posture that adapts to evolving cyber threats.






