Why Are NDR Platforms Critical for Enterprise Network Security?
NDR platforms for enterprises provide continuous visibility into network traffic to detect threats that bypass endpoints and logs. Enterprise Network Detection and Response solutions use behavioral analytics to uncover lateral movement, covert command-and-control, and hidden attacker activity, strengthening network security where traditional tools fall short.
Introduction
They don’t lock your files. They infiltrate your foundations. And if your enterprise relies on endpoint-only visibility, you’re already behind.
UNC3886 is a state-linked advanced persistent threat that exposes a growing visibility crisis in enterprise network security. Their operations highlight why traditional network security solutions, SIEMs, and endpoint tools are no longer enough on their own.
This shift demands enterprise Network Detection and Response (NDR). By delivering deep visibility across network traffic, NDR security enables organizations to detect threats hiding in infrastructure layers that most cybersecurity technologies never see.
What Makes UNC3886 Different
UNC3886 is an espionage-focused APT group assessed to be China-linked. Active since at least 2021, it has consistently targeted government, telecom, financial, and other critical infrastructure sectors, with growing activity in Asia-Pacific, particularly Singapore. Unlike ransomware gangs that rely on volume and chaos, UNC3886 operates in silence, persistence, and precision.
Their uniqueness lies not just in their stealth, but in their preference for lurking in infrastructure most enterprises barely monitor. These attackers bypass traditional controls and dwell in places where visibility is low and response is slow.
Their Tactics, Techniques, and Procedures (TTPs):
- Zero-day exploitation of Fortinet, VMware, and Juniper devices (e.g., CVE-2023-34048, CVE-2022-42475).
- Custom malware including VIRTUALSHINE, VIRTUALPIE, and rootkits like REPTILE and MEDUSA.
- Living-off-the-land techniques, leveraging legitimate admin tools and CLI access for malicious operations.
- Command-and-control over VMCI bus, evading standard network monitoring and firewalls.
- Tampering with logs and disabling audit trails to hinder investigations and break compliance dependencies.
They exploit the reality that most traditional defenses focus on endpoints and signatures, leaving a gaping hole in network-layer visibility. This is an adversary who knows where you’re not looking.
Where Traditional Detection Fails
Many enterprises still rely heavily on Endpoint Detection and Response (EDR), SIEM logs, and perimeter firewalls. These tools are valuable for detecting commodity malware, phishing attempts, and common privilege abuse, but they are far less effective when adversaries bypass endpoints entirely.
UNC3886 doesn’t need to compromise an employee laptop. They infiltrate the digital backbone – hypervisors, management consoles, and networking appliances – while blending into normal administrative traffic. Their malware hides in virtual machines, and their access trails are quickly erased.
Common enterprise network security blind spots:
- Infrastructure and hypervisors without agent coverage
- East-west traffic inside virtual networks
- Encrypted traffic that bypasses inspection
- Custom malware invisible to signatures
- Log manipulation that disrupts investigations
Without NDR network detection response capabilities, these blind spots become persistent breach paths.
How NDR Security Enables Enterprise Network Detection and Response
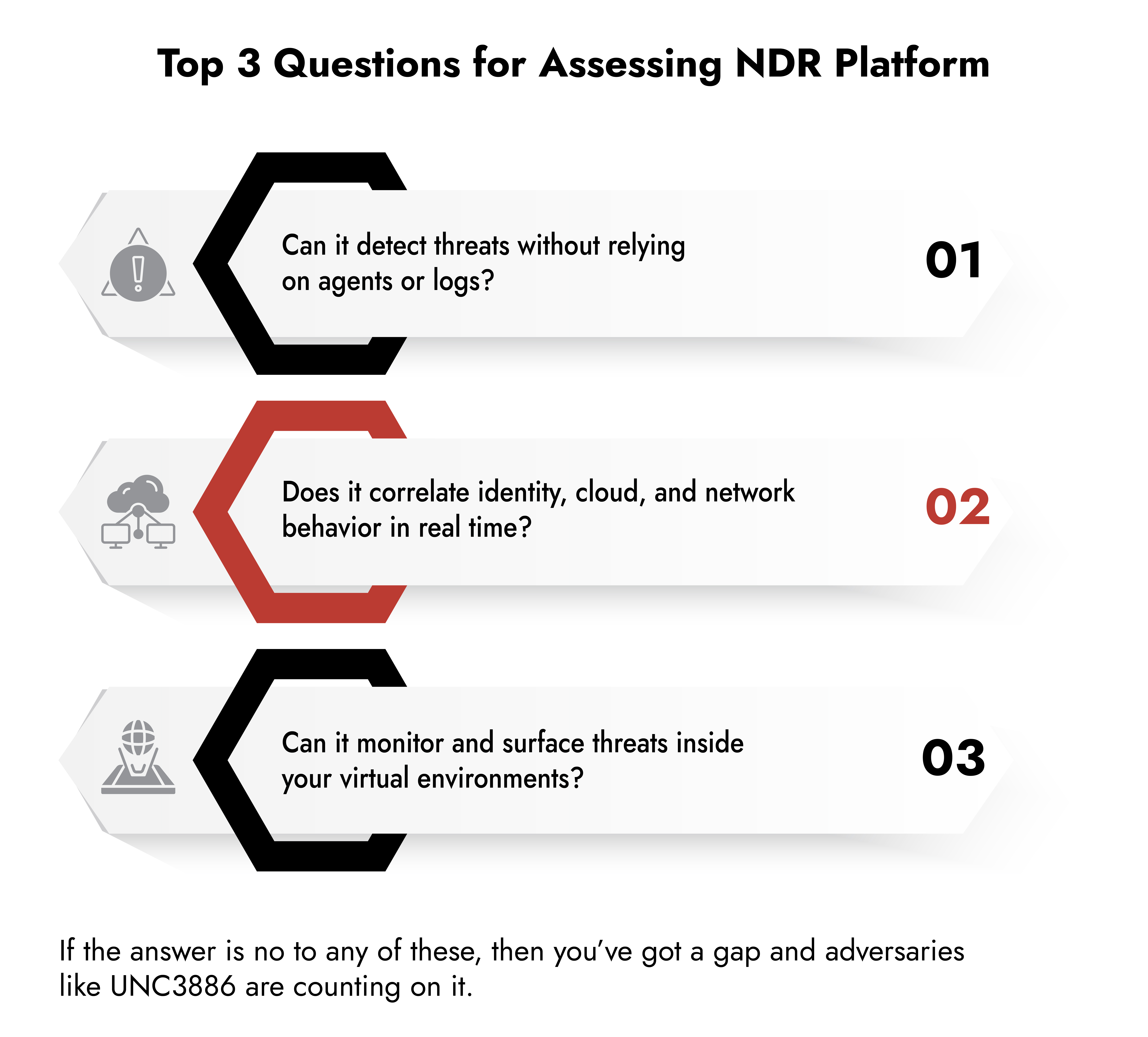
Unlike endpoint- or log-based systems, Network Detection and Response works by inspecting live network traffic in real time. It doesn’t rely on what the endpoint sees or what the logs say. It observes how systems behave, how identities move, and how unusual interactions unfold inside your infrastructure.
That makes enterprise Network Detection and Response solutions uniquely equipped to identify threats like UNC3886, even without endpoint agents or trustworthy logs.
Core Capabilities of NDR Solutions:
- Agentless deployment across cloud, hybrid, and on-prem infrastructure.
- Behavioral analytics to detect lateral movement, privilege escalation, and covert access
- Detection of covert C2 like VMCI bus traffic, DNS tunneling, and beaconing behavior.
- Real-time correlation of weak signals into prioritized, actionable alerts.
- Seamless integration with SIEM and SOAR platforms to drive fast, automated response.
In short, NDR security turns the blind spots UNC3886 exploits into well-lit corridors of visibility and defense. It surfaces what attackers work so hard to conceal.
Proactive Network Threat Detection with NetWitness® NDR
-Spot threats fast with AI-driven analytics.
-See everything across your network and cloud traffic.
-Investigate efficiently with built-in forensic tools.
-Adapt and scale to meet growing security needs.

NetWitness NDR Platform: Purpose-Built for Threats Like UNC3886
NetWitness Network Detection and Response (NDR) platform is built for enterprises that understand the stakes. It extends detection to where adversaries hide – inside the network, between virtual machines, and deep within encrypted sessions. They don’t. The modern enterprise attack surface spans cloud workloads, virtual networks, identity systems, and OT environments. Yesterday’s tools weren’t built for this sprawl.
Key Differentiators of the NetWitness NDR Solution:
- Full-packet capture with context-aware metadata provides analysts with deep insights on all network activity.
- East-west visibility across hybrid cloud and on-prem infrastructure.
- Encrypted traffic analysis without decryption, detecting anomalies even in TLS sessions.
- Integrated threat intelligence and behavior analytics to surface zero-day exploitation and unknown malware behavior.
- Rapid pivoting from alert to packet-level evidence, enabling decisive investigation and faster response.
It’s not just about detecting threats. It’s about understanding them well enough to shut them down fast. 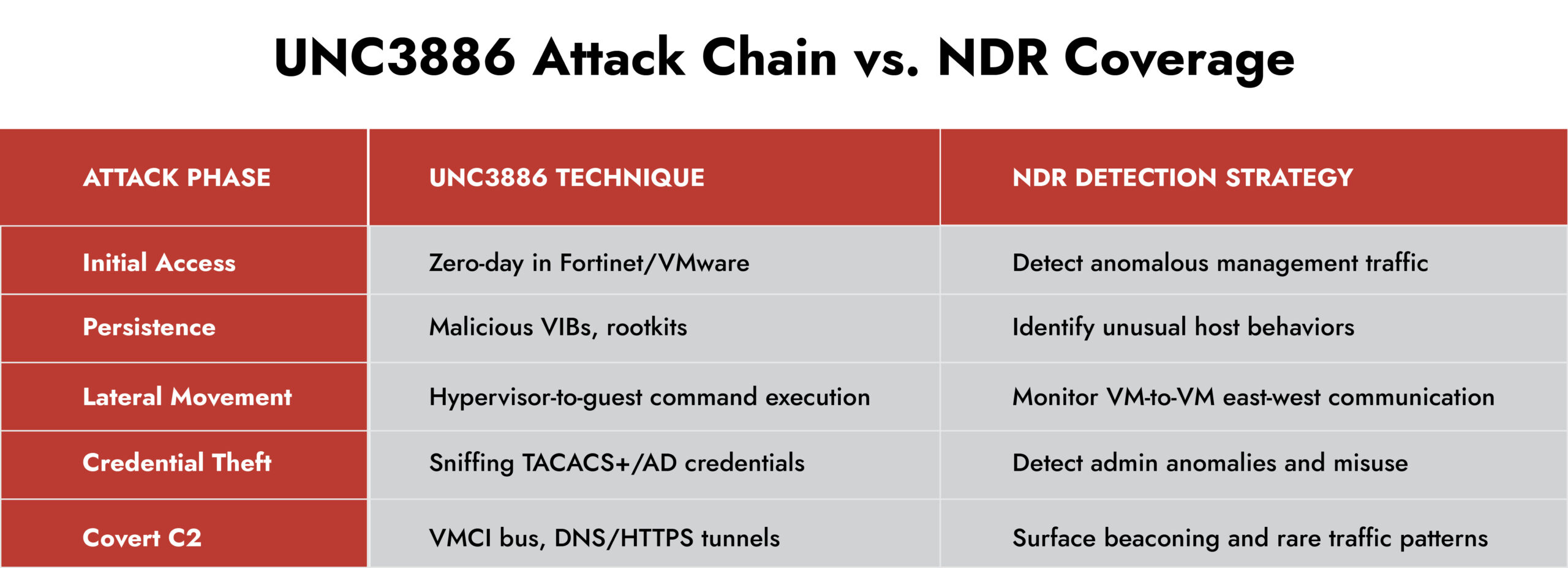
What CISOs Gain from NDR Solutions
For cybersecurity leaders overseeing critical workloads and infrastructure, NDR solutions are more than another tool. They deliver strategic clarity in places where traditional controls fall silent.
Key Benefits for Enterprises:
- Resilient visibility: Even when logs are erased or endpoints go dark, NDR continues to see everything.
- Better signal-to-noise ratio: By correlating weak signals into coherent attack narratives, NDR platform tools reduce noise and highlight true threats.
- Accelerated response: Security teams move from detection to investigation in minutes, not days.
- Proactive threat hunting: Continuous visibility into east-west traffic and lateral movement exposes threats before impact.
- Compliance alignment: Verifiable evidence trails support incident response and regulatory disclosure.
Conclusion: If You Can’t See It, You Can’t Stop It
UNC3886 didn’t expose a new technical weakness. It exposed a strategic oversight: the assumption that endpoints and logs tell the whole story.
They don’t. The modern enterprise attack surface spans cloud workloads, virtual networks, identity systems, and OT environments. Yesterday’s tools weren’t built for this sprawl.
Network Detection and Response (NDR) meet the moment. It fills the visibility gaps. It reduces detection delays. It gives defenders a fighting chance before breaches become public.
For organizations that take resilience seriously, NDR security is foundational.
Explore how our NetWitness NDR platform helps detect and respond to threats like UNC3886 before they become headlines.
Frequently Asked Questions
1. What is UNC 3886?
UNC 3886 is a China-linked APT group focused on cyber espionage. It targets critical sectors like government, telecom, and finance using stealthy methods that exploit network visibility gaps.
2. Why is UNC 3886 difficult to detect?
It hides in hypervisors and management consoles that lack endpoint visibility, often using custom malware and zero-day exploits that evade traditional defenses.
3. How does NDR help detect threats like UNC 3886?
Network Detection and Response security continuously monitors network traffic for abnormal behavior, uncovering stealthy command-and-control channels and lateral movement patterns.
4. How does UNC 3886 evade traditional security tools?
By tampering with logs, exploiting systems without agents, and hiding in east-west traffic – areas where EDR and SIEM have minimal reach.
5. Which blind spots in enterprise security does NDR help address?
Enterprise Network Detection and Response platforms expose blind spots in encrypted traffic, virtual machines, and unmanaged infrastructure, offering full visibility where other tools fail.
DORA Compliance with NetWitness® Network Detection & Response (NDR)
Strengthen Digital Operational Resilience with Deep Network Visibility
Meet EU DORA requirements with continuous network monitoring, advanced threat detection, and automated response across complex financial environments.






