What is the OT Threat Landscape?
The OT threat landscape refers to the evolving set of cyber risks targeting operational technology, including ICS, SCADA, PLCs, HMIs, industrial networks, and connected devices, driven by ransomware, legacy system exposure, IT/OT convergence, and increasingly sophisticated adversary tactics. This includes bold expansions such as OT threat detection, operational technology threats, and rising cyber threats for businesses across industries.
Why Operational Technology Security is Entering a New Era
If you’ve ever walked through a plant floor or stood inside a control room, you know the feeling – the quiet hum of machines, the screens full of green indicators, and the comforting sense that everything is running the way it should. Operational technology systems are the backbone of industries that keep society moving – power grids, manufacturing lines, logistics hubs, water facilities, and so much more.
Now picture someone sitting thousands of miles away, clicking a button that brings it all to a grinding halt. That’s the uncomfortable reality of 2026.
OT wasn’t designed with cyber threats in mind. These systems were built for reliability, predictability, and uptime. Security wasn’t even in the conversation. But today, attackers see operational technology as a direct path to disruption and they’re getting creative day by day, which is something to think about.
If you’re responsible for these environments, this is the moment to stop treating operational technology as a self-contained universe and start viewing it as part of your organization’s broader risk surface. The threats are real, and the consequences aren’t just digital, they’re physical.
This article walks through what’s shifting in operational technology cybersecurity and what defenders can do to tighten their posture without putting operations at risk, all while keeping pace with fast-changing OT cybersecurity trends.
What is Shaping OT Security in 2026
1. Operational Technology is Officially a Primary Target
There used to be a time when attackers mostly bothered the IT side of the house. That era is over.
In 2025, one major industrial cybersecurity report logged a 46% increase in ransomware attempts against industrial operators in a single quarter. On top of that, new threat groups focusing specifically on OT and ICS emerged, adding to an already long list of attackers with an appetite for disrupting physical infrastructure.
And why wouldn’t they target operational technology? When something goes wrong in these environments, the fallout isn’t just losing data. It could mean:
- halted production
- safety incidents
- water contamination
- grid instability or power outages
This shift means something important: assume your OT network will be tested, whether by opportunistic attackers, organized groups, or nation-state-linked actors. The question has quietly changed from “if” to “when.”
2. Legacy OT Systems Remain a Risk Hotspot
Many OT networks still rely on equipment old enough to remember life before smartphones. And attackers know it. Thousands of OT devices have been openly exposed on the internet in the past. Many with outdated firmware or known vulnerabilities. Some even spot the classic combo of default credentials and public-facing interfaces.
The catch is that these systems can’t just be patched on demand. Taking them down for updates often means stopping production, delaying shipments, or disrupting essential services. So, companies “live with” the vulnerabilities, hoping nothing happens.
But hope isn’t a strategy. If you’re running legacy OT, treat each unpatched or internet-reachable device as a potential entry point because attackers absolutely do. This is where OT vulnerabilities 2026 become a defining risk category for defenders.
3. Threat Actors are Diversifying Their Playbook
Attackers have moved on from the “one-size-fits-all ransomware” model. They’re experimenting with:
- phishing and social engineering
- malicious scripts
- supply-chain compromise
- purpose-built operational technology malware
- IT-to-OT lateral movement
Threat activity reports from 2025 show that industrial networks regularly block malicious documents, spyware, backdoors, and rogue scripts, many designed specifically to interact with OT protocols.
So, if anyone still believes their OT environment is “air-gapped,” this is a good time to retire from that assumption. Modern threats don’t care about boundaries. If IT and OT are connected (and they almost always are), attackers will navigate between them like rooms in the same building.
4. IT–OT Convergence is Expanding the Attack Surface
Digital transformation is great until it isn’t.
Remote monitoring, predictive maintenance tools, cloud dashboards, vendor access portals, and hybrid work policies have all made operations more efficient. But they’ve also erased the once-tidy line between IT and OT security.
Here comes the tricky part. OT wasn’t built with strong authentication, encryption, or segmentation in mind. So, when attackers get into IT, hopping into OT is often surprisingly simple.
Defending modern industrial environments means treating them with the same rigor as IT networks, but with the added pressure that downtime is rarely an option. This new reality requires frequent and honest OT risk assessment to ensure defenders know where their weakest links are.
FIN13: Inside a Fintech Cyber Attack
FIN13 is one of today’s most disruptive threat groups targeting fintech organizations with precision and persistence. This whitepaper breaks down their full attack chain—from reconnaissance and credential theft to lateral movement, data exfiltration, and evasion techniques. Gain insights into their TTPs, discover detection opportunities across the kill chain, and learn how NetWitness empowers faster response and mitigation.

A Practical OT Hardening Playbook for 2026
There’s no silver bullet for operational technology security. But there is a realistic path to dramatically lowering risk. Think of it as making your systems resilient rather than perfect because perfection isn’t possible.
Here’s what that path looks like:
- Inventory every asset- Know what’s in your environment – PLCs, SCADA servers, HMIs, gateways, IoT, vendor access tools. Unknown assets are attackers’ favorite entry points.
- Segment aggressively- OT shouldn’t casually mingle with IT. If convergence is necessary, restrict connectivity and monitor every doorway between the two.
- Monitor continuously- Systems change. Behavior shifts. Networks evolve. Monitoring OT-specific protocols and device behavior is essential to spotting subtle anomalies.
- Lock down remote access- Retire unsafe access paths. Require strong authentication. Limit vendor access windows. Remove outdated or forgotten entry points.
- Build an OT-specific incident response plan- Your IT playbook won’t work here. OT requires controlled shutdown procedures, safety considerations, and recovery steps that don’t disrupt operations.
- Use OT-aware detection and response platforms- Standard IT tools miss OT-specific signals. You need detection engines that understand industrial protocol behavior and operational constraints.
- Reinforce security culture- Human error is still a top threat vector. Train teams, restrict removable media, and encourage incident reporting without blame.
This isn’t about locking everything down. It’s about building an environment that can absorb threats, detect them early, and bounce back fast, especially as OT ransomware trends continue rising. 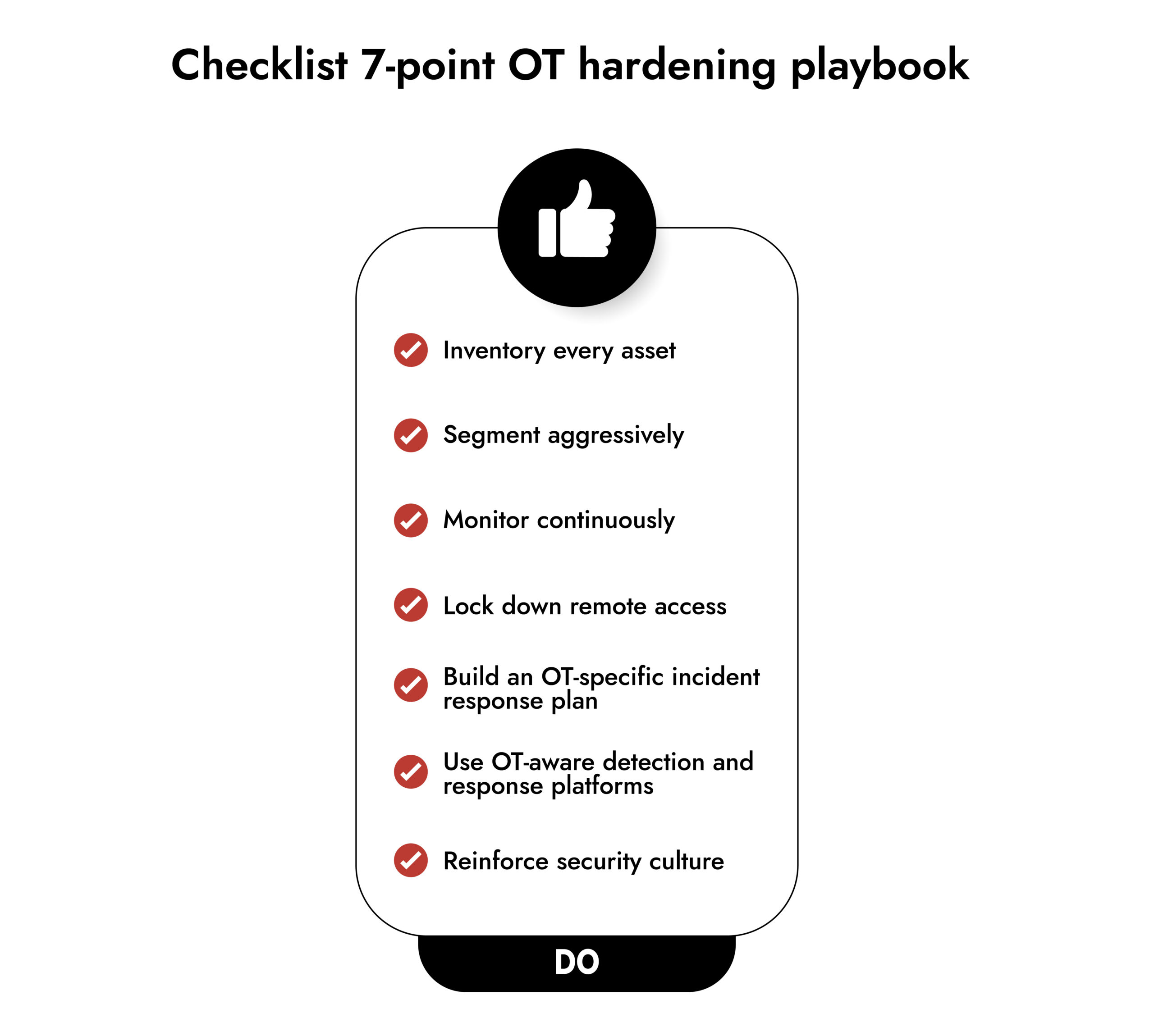 How NetWitness Strengthens OT Threat Detection and Response
How NetWitness Strengthens OT Threat Detection and Response
When it comes to securing OT, NetWitness doesn’t try to squeeze IT tools into a world they weren’t built for. Instead, it delivers a platform intentionally designed to understand industrial environments and the unique behaviors, signals, and risks within them.
Here is how NetWitness helps defenders stay ahead:
- Deep Protocol Analysis- NetWitness analyzes industrial protocols like ModbusTCP, DNP3, OPC-UA, and EtherNet/IP with precision. It catches unusual command patterns, unauthorized device interactions, and protocol manipulation attempts that generic tools overlook – a critical advantage for OT threat detection and high-risk operational technology threats.
- Behavioral Analytics for OT- The platform builds baselines for how devices normally behave. If a PLC suddenly issues unusual write commands or an actuator behaves differently than usual, the system flags it instantly.
- Cross-Domain Correlation- Events from IT and OT flow into a single detection engine. When identity anomalies in IT link to suspicious traffic in OT, analysts see the full story, not fragmented clues.
- Automated Response That Respects OT Constraints- NetWitness can isolate risky devices, reduce suspicious connections, enforce access controls, or trigger response workflows, all without disrupting critical uptime.
- Threat Intelligence for Industrial Environments- It enriches alerts with global threat intelligence and OT-focused indicators of compromise, helping teams prioritize what truly matters.
- Forensics and Post-Incident Visibility- With full packet capture and metadata for OT events, analysts can replay incidents, trace movement, and validate recovery steps with confidence.
The real value? NetWitness gives SOC and operational technology teams clear visibility and context, so they can detect threats earlier and respond before small problems turn into operational shutdowns – a major advantage as cyber threats for businesses grow more targeted and sophisticated.
Conclusion
Operational technology environments no longer operate in isolation. They’re intertwined with IT, exposed to modern threat actors, and increasingly targeted for the physical impact they can deliver.
As 2026 unfolds, organizations will face more pressure than ever:
- ransomware that halts production
- legacy exposure that refuses to disappear
- diversified attacker techniques
- a rapidly expanding hybrid attack surface
Operational technology is no longer isolated – it’s connected, exposed, and increasingly targeted. In 2026, organizations will face ransomware, legacy vulnerabilities, diversified attacker techniques, and an expanding hybrid attack surface.
Treat OT as “just running systems,” and incidents become firefighting. Treat it as a critical, interconnected part of your enterprise, and you gain the visibility and control to respond effectively. Organizations that prioritize detection, monitoring, response, and a strong security culture will be best positioned to avoid worst-case scenarios.
Frequently Asked Questions
1. What does the OT threat landscape entail?
It covers cyber risks targeting operational technology, including ICS, SCADA, PLCs, HMIs, and edge devices, through methods like ransomware, malware, phishing, remote-access exploitation, and supply-chain compromise.
2. What will be the leading OT cybersecurity trends in 2026?
Expect rising ransomware against industrial operators, widespread legacy exposure, more OT-specific malware, and significant risk from IT-OT convergence.
3. What function does ransomware serve in OT attacks?
Ransomware in OT environments isn’t just about data. It creates operational downtime, safety risks, and production disruption – all high-impact leverages for attackers.
4. Which detection tools are efficient for OT environments?
The most effective tools support hybrid IT/OT visibility, deep protocol inspection, behavioral anomaly detection, and integrated incident response workflows.
5. Which sectors face the greatest OT cyber threats?
Industries with heavy reliance on legacy OT systems – manufacturing, utilities, transportation, and critical infrastructure, face the highest exposure.
Autonomous AI Defenders for a Smarter SOC







