Key Takeaways
- Network behavior analysis spots the subtle anomalies that signature based tools miss, giving you early visibility into APTs, insider misuse, and hidden threats.
- Baselines built from real network activity help cut false positives and highlight deviations that actually matter.
- End to end visibility across cloud, on prem, remote, and IoT environments removes the blind spots attackers rely on.
- Real time detection and continuous learning reduce dwell time and stop threats before they escalate.
Introduction
Your network is talking. Every packet, every connection, every anomaly tells a story. The question is: are you listening?
Network behavior analysis in cybersecurity is how organizations move from blind defense to intelligent threat detection. Instead of waiting for alarms to go off after an attack, you’re watching for the subtle shifts that signal something’s wrong before real damage happens.
Here’s what this really means for your security posture.
What is Network Behavior Analysis?
Network behavior analysis is a form of network traffic behavior analysis that monitors and studies how data normally moves across a network. It builds a picture of expected behavior and flags deviations that may indicate a threat.
In simple terms, it creates a behavioral fingerprint of your entire network.
The system tracks:
- Who connects to what and when and where.
- How much data moves between systems.
- Which protocols get used.
- Where traffic flows internally and externally.
- Unusual spikes or drops in activity.
Once normal behavior is understood, network threat behavior analysis can detect abnormal activity, even if it has never been seen before. This is fundamentally different from signature-based tools that only look for known threats. 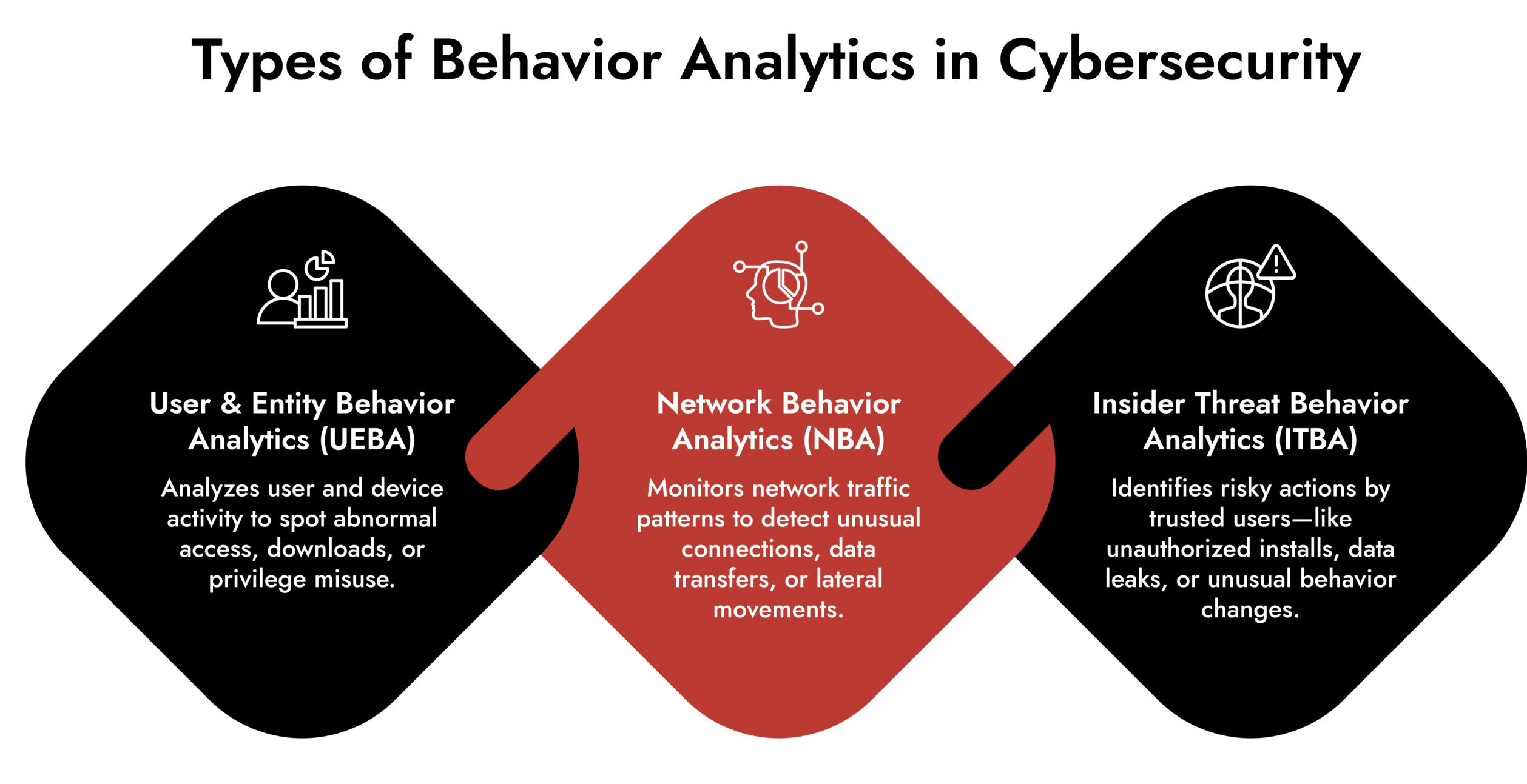
How Network Behavior Analysis Works
Network behavior analysis follows a clear, repeatable process that turns raw traffic into security insight.
Step 1: Data Collection and Aggregation
Network traffic monitoring collects raw data from every corner of your infrastructure:
- Firewall logs and router data.
- Application traffic patterns.
- Cloud connection metadata.
- Endpoint communications.
- DNS queries and responses.
- Protocol usage statistics.
Everything moving across the network is captured. Today, this process is fully automated and happens in real time.
Step 2: Baseline Establishment
Machine learning analyzes the collected data to build behavioral baselines. The system learns:
- Normal traffic volumes for different times of day.
- Typical communication patterns between systems.
- Standard protocol usage for each application.
- Regular data transfer sizes and frequencies.
- Expected geographic locations for connections.
This baseline isn’t static. Network visibility and analytics continuously updates as your environment evolves with new applications, users, and business processes.
Step 3: Anomaly Detection
Once baselines exist, the system looks for deviations. Network behavior analysis tools detect patterns such as:
- Traffic to unusual destinations or suspicious IPs.
- Unexpected protocol usage.
- Abnormal data transfer volumes.
- Connection attempts at odd hours.
- Lateral movement between systems.
These signals indicate activity that deserves investigation.
Step 4: Alert Generation and Response
When anomalies are detected, network behavior monitoring generates real-time alerts with context:
- What changed and where.
- Why it triggered an alert.
- Severity and potential impact.
- Recommended investigation steps.
This allows security teams to act before threats escalate.
Step 5: Continuous Learning
Network behavior analysis tools improve over time by:
- Adapt to emerging cyber threats.
- Reduce false positives over time.
- Refine detection accuracy.
- Adjust to legitimate changes in your environment.
The more data processed, the better the system becomes separating harmless anomalies from real threats.
Strengthen Network Visibility with NetWitness® Network Traffic Security Assessment
-Uncover hidden threats through deep packet inspection and analytics.
-Identify vulnerabilities and blind spots before they’re exploited.
-Enhance detection and response with NDR-driven intelligence.

Types of Threats Network Behavior Analysis Detects
Network threat behavior analysis reveals attacks that traditional tools often miss.
1. Advanced Persistent Threats (APTs):
APTs operate slowly and blend into normal traffic. They often use valid credentials and avoid obvious alerts.
Network traffic behavior analysis detects APTs by identifying:
- Gradual data access over long periods
- Connections during maintenance windows
- Slow privilege escalation
- Communication with command-and-control servers
2. Data Exfiltration:
Network behavior monitoring identifies unauthorized data movement such as:
- Large transfers to external systems
- Encrypted file uploads to personal cloud storage.
- Database dumps sent to unknown IPs.
- Gradual data leaking to avoid detection thresholds.
A sudden multi-gigabyte transfer at 3 AM is not normal. The system flags it immediately.
3. Distributed Denial of Service (DDoS) Attacks:
DDoS attacks create clear behavioral signals:
- Sudden traffic spikes
- Massive request volume increases
- Unusual protocol usage
- Traffic from many regions at once
Network behavior analysis detects these patterns early, before services fail.
4. Insider Threats:
Because insiders have legitimate access, their activity is harder to detect.
Network threat behavior analysis flags:
- Unusual lateral movement
- Access to unauthorized files
- Unexpected command execution
- Downloading sensitive data they’ve never accessed before.
5. Network Reconnaissance:
Attackers often probe before attacking. Network behavior monitoring detects:
- Network scanning
- Port scanning
- Service probing
- Resource enumeration
These are early warning signs of planned attacks.
6. Malware Communication:
Even encrypted malware creates patterns:
- Downloads from untrusted sources
- Beaconing to command servers
- Outbound connections on unusual ports
- DNS queries to known malicious domains
Network behavior analysis tools identify these signals without relying on signatures.
7. Zero-Day Exploits:
Zero-day attacks lack known signatures but still create abnormal traffic.
Network traffic behavior analysis detects the behavioral impact of these exploits, even when the vulnerability itself is unknown.
Key Benefits of Network Behavior Analysis
1. Proactive Threat Detection:
The importance of network behavior analysis is clear here. Threats are detected before damage occurs, not after cleanup begins.
2. Real-Time Response:
Network behavior monitoring delivers alerts instantly. Faster detection limits lateral movement, privilege escalation, and data theft.
3. Comprehensive Visibility:
Network behavior analysis provides visibility across:
- On-prem environments
- Cloud workloads
- Remote endpoints
- Third-party connections
Your perimeter is everywhere your data travels.
4. Reduced Alert Fatigue:
Network behavior analysis tools prioritize alerts based on risk and impact. Teams get context, not noise.
5. Compliance Support:
Behavioral analytics highlights unauthorized access and policy violations. Audit trails are built in, making compliance easier.
6. Cost Savings:
Early detection prevents costly breaches, legal exposure, and reputational damage. Preventing incidents is far cheaper than recovering from them.
Why Network Behavior Analysis is Critical for Modern SOCs
SOC teams face skilled attackers with limited time and resources. Network threat behavior analysis provides the visibility they need.
Traditional defenses assume attackers can be kept out. That assumption no longer holds.
Once inside, speed matters. Network behavior analysis tools detect threats across the entire environment, not just endpoints or logs.
- Endpoint tools show device activity
- SIEM correlates events
- Network behavior analysis shows how everything connects
Together, they create real defense in depth.
As cloud adoption and remote work grow, network behavior monitoring becomes even more critical, covering both east-west and north-south traffic.
The Bottom Line
Network behavior analysis is not optional anymore. You cannot defend what you cannot see.
Attackers use legitimate tools, encryption, and patience to evade detection. Network traffic behavior analysis adapts with them, without waiting for signatures or manual tuning.
What this comes down to is balance. Attackers need to succeed once. Defenders need to succeed every time.
The importance of network behavior analysis is that it restores that balance by making your network transparent to you and unpredictable to attackers.
Your network is still talking. With the right behavioral analysis in place, you are finally listening.
Frequently Asked Questions
1. What is network behavior analysis in cybersecurity?
Network behavior analysis monitors and analyzes network traffic patterns to establish baselines of normal activity, then detects deviations that could indicate threats. It uses machine learning to identify suspicious behaviors without relying on known attack signatures.
2. How does network behavior analysis help detect cyber threats?
It spots anomalies in traffic patterns, protocol usage, data transfers, and connection behaviors that indicate attacks. By learning what normal looks like for your environment, it can identify advanced threats, data exfiltration, insider attacks, and reconnaissance activities that traditional tools miss.
3. What are the benefits of using network behavior analysis?
Real-time threat detection, reduced alert fatigue through prioritization, faster incident response, comprehensive network visibility, better compliance documentation, and cost savings from preventing breaches. It also adapts continuously to your changing network environment.
4. How is machine learning used in network behavior analysis?
Unsupervised ML algorithms analyze massive amounts of network data to find patterns and establish baselines automatically. The system continuously learns and improves its detection capabilities, adapting to new threats and reducing false positives over time without manual rule updates.
5. What types of threats can network behavior analysis detect?
Advanced persistent threats, data exfiltration, DDoS attacks, insider threats, lateral movement, network reconnaissance, zero-day exploits, malware communications, credential abuse, and suspicious data transfers. It excels at catching threats that blend in with legitimate traffic.
6. Why is network behavior analysis important for modern SOCs?
SOCs need visibility across distributed, cloud-connected infrastructures with limited resources. Network behavior analysis provides that visibility, filling gaps between endpoint and SIEM tools while automatically prioritizing real threats. It’s essential for detecting attacks that bypass perimeter defenses and adapting to the reality that the network perimeter now extends everywhere data flows.
Proactive Network Threat Detection with NetWitness® NDR
-Spot threats fast with AI-driven analytics.
-See everything across your network and cloud traffic.
-Investigate efficiently with built-in forensic tools.
-Adapt and scale to meet growing security needs.






