What is NDR?
Network Detection and Response (NDR) offer a better way to watch over a network than old security tools. It can spot threats that regular methods might be missed. Instead of only searching for known attacks, NDR looks at user behavior. This helps find and react to new attacks that lack signatures or clear patterns, called zero-day attacks. NDR gives large organizations better visibility into their networks, including hybrid and cloud systems. Its services help security teams respond faster and with more confidence in threats.
Why Network Security Has Reached a Breaking Point
Organizations have recently seen a major jump in cyberattacks. In Q3 of 2024, organizations had an average of 1,876 cyberattacks, which is 75 percent more than the previous year. Because the threat environment is so intense, Chief Information Security Officers (CISOs) face a growing number of cyberattacks every quarter, requiring them to modify their security programs.
Traditional perimeter-based defenses and signature-based detection systems have been effective in mitigating risk from known threats; however, with today’s attackers travelling quietly and blending in with legitimate traffic, organizations need to leverage tools that provide greater visibility into their network traffic. Network Detection and Response Services are an answer to this need.
Unlike signature-based systems that only assist in identifying threats based upon the use of known signatures, Network Detection and Response Services utilize an organization’s existing technology stack to monitor an organization’s network in real-time by analyzing traffic patterns, behaviors, and anomalies. Detecting anomalous or behavior patterns assists in identifying unknown threats which would be concealed without this additional monitoring.
Simply put, if you do not know what is occurring throughout your network, you will not be able to defend against it.
The Core Security Challenges NDR Address
1. Advanced Persistent Threats and Zero-Day Exploits:
Modern-day threats involve attackers utilizing methods to avoid detection by using standard cyber security tools. For example, in 2023 alone, thousands of vulnerabilities were identified by cyber security experts as having been exploited, with many more being actively attacked on a regular basis. Advanced persistent threats and zero-day exploits are particularly alarming because they:
- Are not dependent on malware signatures that are publicly available
- Use tools and protocols that are fully permitted by the organization where they operate
- Go through a long escalation phase without being detected
NDR services provide an additional layer of detection against cyber-attacks by taking the focus off of signatures and placing it on the behavior of the data and systems being monitored. By understanding how data communicates, moves and creates traffic patterns, NDR platforms can identify even subtle indicators of compromise when the attack has not been previously identified as such.
2. Visibility Gaps Across Hybrid and Cloud Networks
One of the consequences of moving to hybrid/multi-cloud environments has been an increase in your attack surface but less visibility into your traffic across your hybrid/multi-cloud environment. Traditional monitoring solutions cannot provide consistent monitoring of network traffic across the following environments: The three main types of hybrid and multi-cloud environments include:
- On-Premises Data Centers
- Public/Private Cloud Platforms
- Remote/VPN connections
Since these areas of your network are not being monitored, hackers have the opportunity to gain lateral movement within your network without being detected.
A unified approach to network detection and response (NDR) will close off these opportunities by giving you a complete view of your entire network with a single solution, so that you can monitor all types of network traffic, including North/South and East/West network traffic. You will be able to quickly identify potential threats in your network, regardless of where they enter or how they move through your network.

3. Insider Threats and Compromised Credentials:
Insider threats remain one of the hardest problems in cybersecurity. Whether caused by malicious intent or stolen credentials, these attacks originate from trusted users and systems.
Traditional tools often miss them because:
- Access appears legitimate
- Activity blends into normal workflows
- No malware is involved
Network detection and response services identify insider threats by tracking deviations in user behavior, access patterns, and data movement. This makes NDR solutions especially effective for detecting credential abuse and account compromise.
How NDR Enhance Enterprise Security Operations
1. Real-Time Network Monitoring and Analysis:
Effective NDR security requires continuous monitoring at network speed. NDR platforms for enterprises analyze traffic in real time using:
- Metadata analysis
This real-time visibility dramatically reduces dwell time, the gap between initial compromise and detection. Faster detection leads directly to lower impact, faster containment, and reduced recovery costs.
2. Automated Threat Correlation and Response:
Security teams are overwhelmed by alerts from disconnected tools. Network detection and response services reduce this noise by correlating related events into clear attack stories.
Modern NDR solutions integrate with SOAR and SIEM platforms to:
- Automate routine response actions
- Prioritize high-risk incidents
- Reduce false positives
This allows security analysts to spend time investigating real threats instead of chasing alerts.
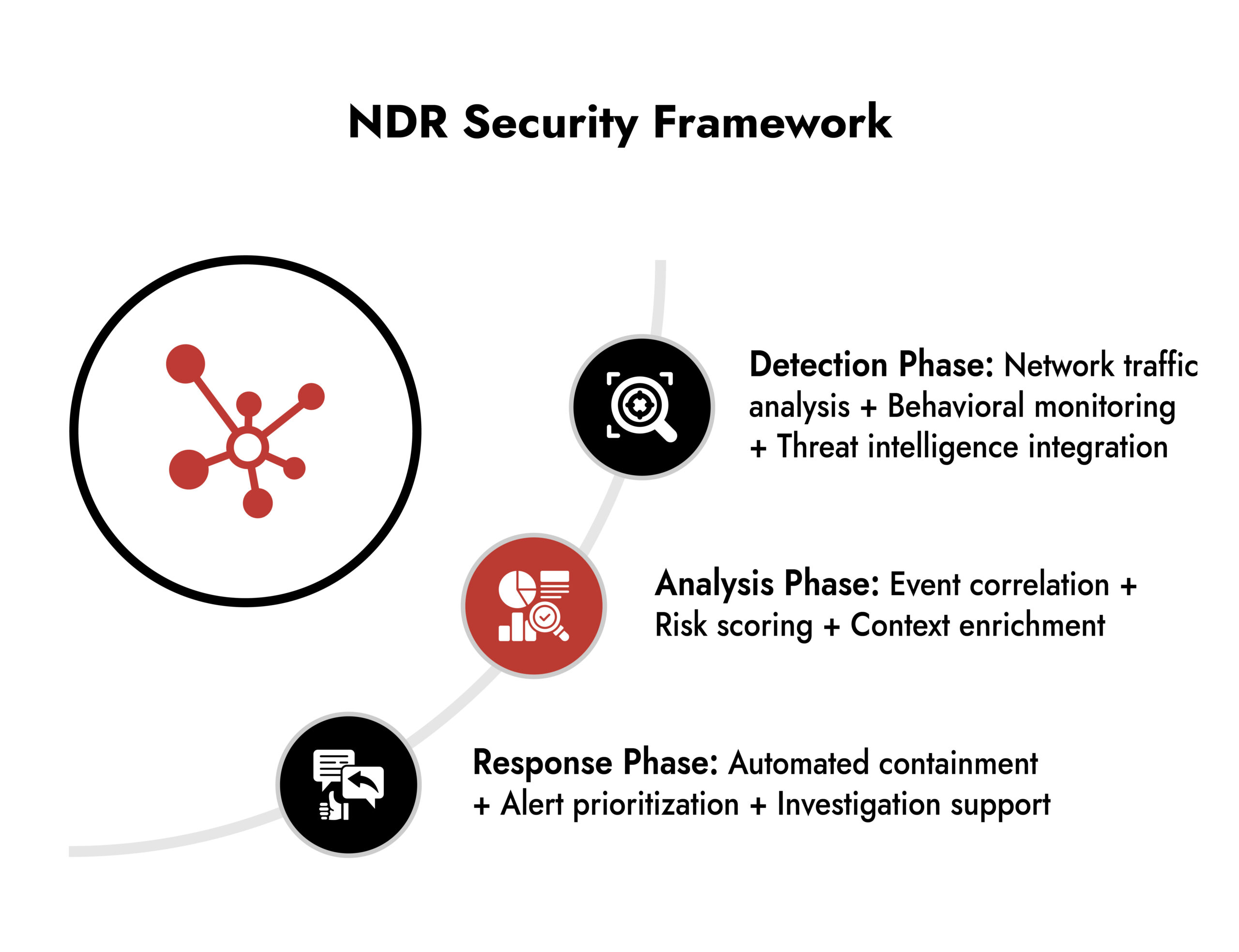
3. Integration with XDR and Existing Security Tools
Enterprise network detection and response work best as part of a broader cybersecurity architecture.
When integrated with EDR, SIEM, identity systems, and threat intelligence, NDR security enables:
- Full attack chain visibility
- Faster root cause analysis
- More confident response decisions
This level of correlation is critical for mature security operations.
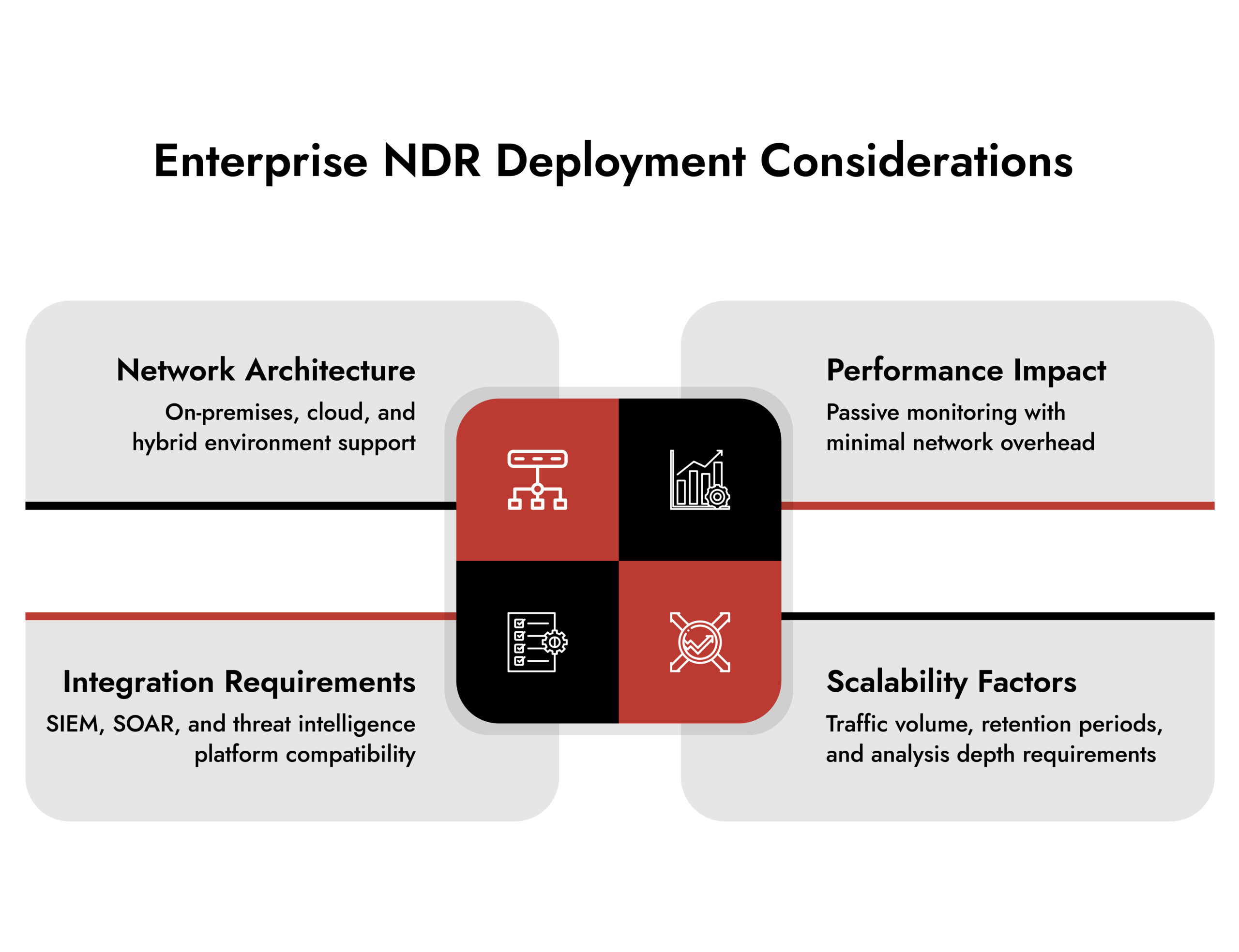
NetWitness NDR: Practical Implementation for Enterprise Security
NetWitness provides enterprise network detection and response that integrates into existing security operations without disruption.
The platform combines deep packet inspection and metadata analysis to deliver:
- Behavioral threat detection
- Scalable performance for large environments
As an NDR specialist, NetWitness supports hybrid cloud environments and high-throughput networks while maintaining consistent performance.
Key capabilities of this NDR service include:
- Detailed attack reconstruction
- Threat intelligence integration
- Advanced investigation workflows
This depth enables faster response and more accurate remediation.
The Strategic Value of NDR Security
NDR security is no longer optional for enterprises. The market is projected to grow rapidly as organizations recognize its impact on risk reduction.
From a business perspective, network detection and response services:
- Reduce breach costs
- Improve detection speed
- Strengthen regulatory posture
For leaders evaluating NDR solutions, the focus should be on visibility depth, behavioral analysis, and integration of flexibility.
Proactive Network Threat Detection with NetWitness® NDR
-Spot threats fast with AI-driven analytics.
-See everything across your network and cloud traffic.
-Investigate efficiently with built-in forensic tools.
-Adapt and scale to meet growing security needs.

NDR as Security Foundation
The evolving threat landscape demands security controls that adapt as fast as attackers do. NDR platforms for enterprises provide the essential visibility foundation needed to detect modern threats early, analyze network traffic including encrypted traffic, and respond effectively. By continuously monitoring raw network packets and leveraging behavioral analytics, machine learning, and artificial intelligence, NDR tools establish baselines of normal network behavior to identify suspicious traffic patterns and detect cyber threats that other security tools may miss.
For organizations asking, “How can I find trusted NDR solutions for improving threat visibility and network operations?”, look for an experienced NDR specialist with proven enterprise-scale deployments, advanced threat detection capabilities, and deep investigation workflows that integrate seamlessly with existing cybersecurity solutions such as SIEM, SOAR, and endpoint detection tools.
Frequently Asked Questions
1. What threats do network detection and response services detect that others miss?
Network detection and response services detect advanced persistent threats, insider threats, lateral movement, and encrypted command-and-control activity using behavioral analysis instead of signatures.
2. Does deploying an NDR service affect network performance?
Modern NDR solutions use passive monitoring and do not introduce latency or bandwidth overhead.
3. What integrations should enterprise NDR security solutions support?
Enterprise network detection and response platforms should integrate with SIEM, SOAR, EDR, and threat intelligence systems.
4. How fast can NDR detect network-based attacks?
NDR security often reduces detection time from weeks to hours through continuous monitoring and automated analysis.
5. What ROI can organizations expect from NDR solutions?
Organizations see ROI through reduced breach of impact, faster response, and lower operational overhead from automation.




