Key Takeaways
- Lateral Movement Detection reveals attacker intent after initial access, where most real damage occurs.
- Internal network behavior, not perimeter alerts, determines whether threats escalate or fail.
- Strong network visibility and network traffic monitoring are essential for modern threat detection and response.
- Identity misuse and trusted protocol abuse make lateral movement invisible without behavior-driven analytics.
- TDR programs that prioritize lateral movement consistently reduce dwell time and blast radius.
Introduction
Most security programs still measure success at the point of entry. Phishing blocked. Malware quarantined. An alert acknowledged. Yet breaches continue to escalate because attackers rarely win at the front door.
They win inside.
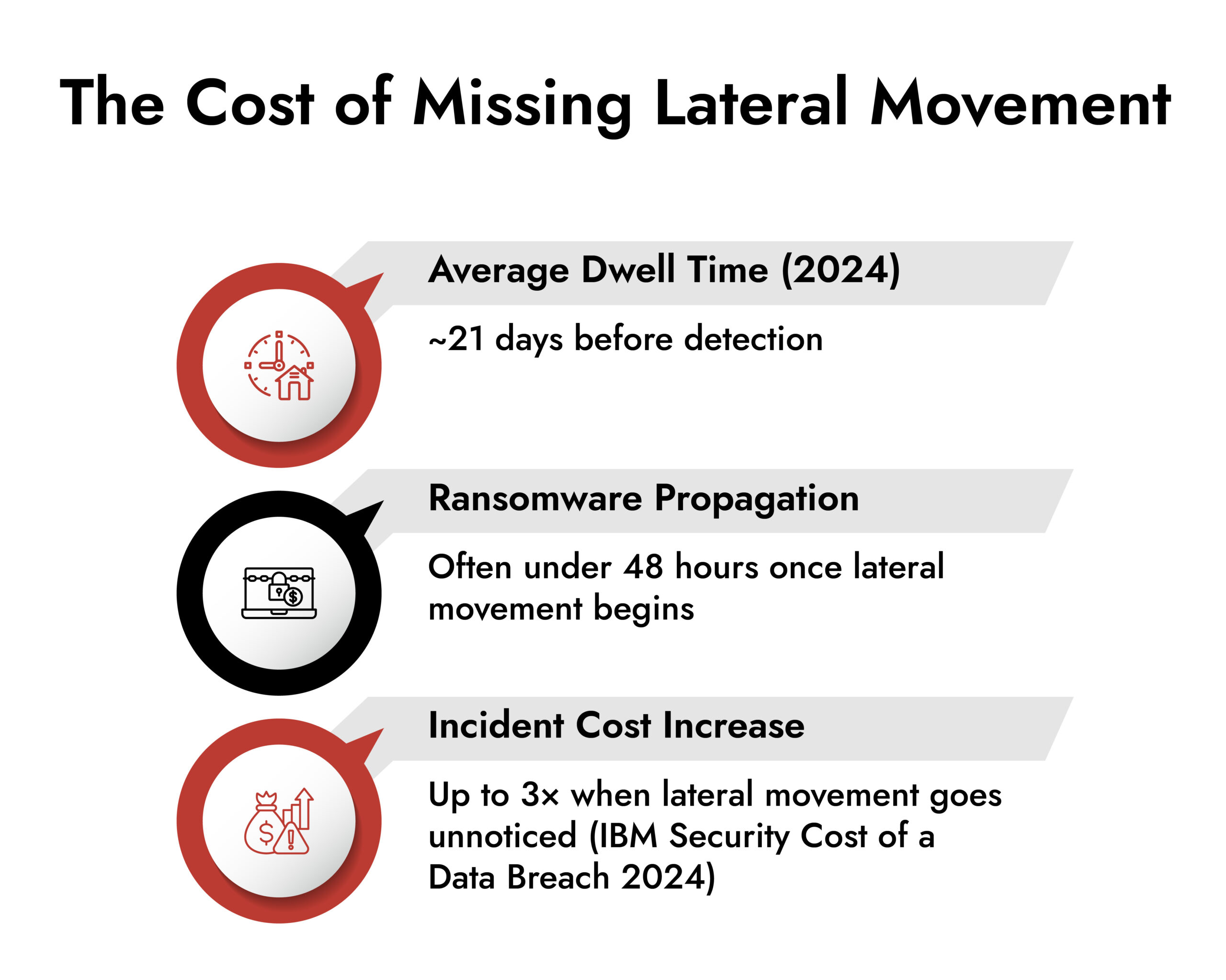
Once access exists, adversaries slow down. They observe. They move laterally. Lateral movement detection is the difference between containing a threat early and discovering it when systems are compromised, data is gone, or operations are down.
This is not a tooling problem. It is a visibility and prioritization problem. And it sits at the heart of effective threat detection and response.
Where Attacks Actually Take Shape
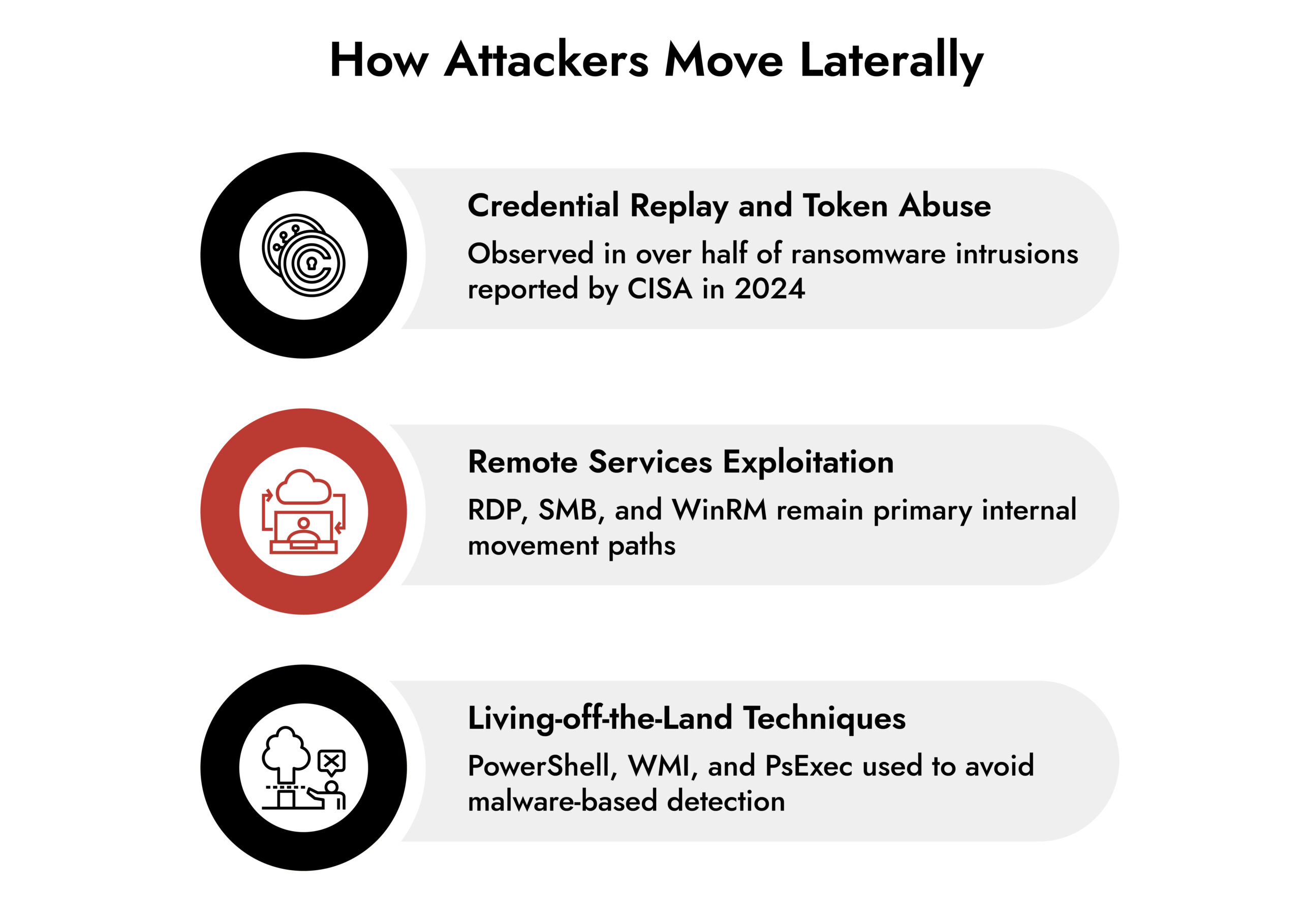
While many attacks attributed to nation-state actors involve highly sophisticated tradecraft, the initial foothold is often obtained through common techniques. The sophistication usually becomes evident during lateral movement and post-exploitation.
After gaining access, attackers focus on understanding internal trust relationships. They map credentials, identify high-value systems, and blend into routine traffic. By the time an incident escalates, the real work has already happened quietly across the network.
Public breach analysis continues to reinforce this. The 2024 Verizon DBIR shows credential abuse and internal misuse as dominant breach patterns. CISA advisories throughout 2024 and early 2025 describe attackers spending extended time moving laterally before triggering any visible disruption.
Without lateral movement detection, security teams respond to symptoms instead of causes.
Why Lateral Movement Blends in So Well
Internal networks were built on trust. That trust has not aged well.
Lateral movement relies on legitimate tools and expected behavior:
- Standard authentication flows
- Approved remote management protocols
- Native administrative utilities
- Service-to-service communication
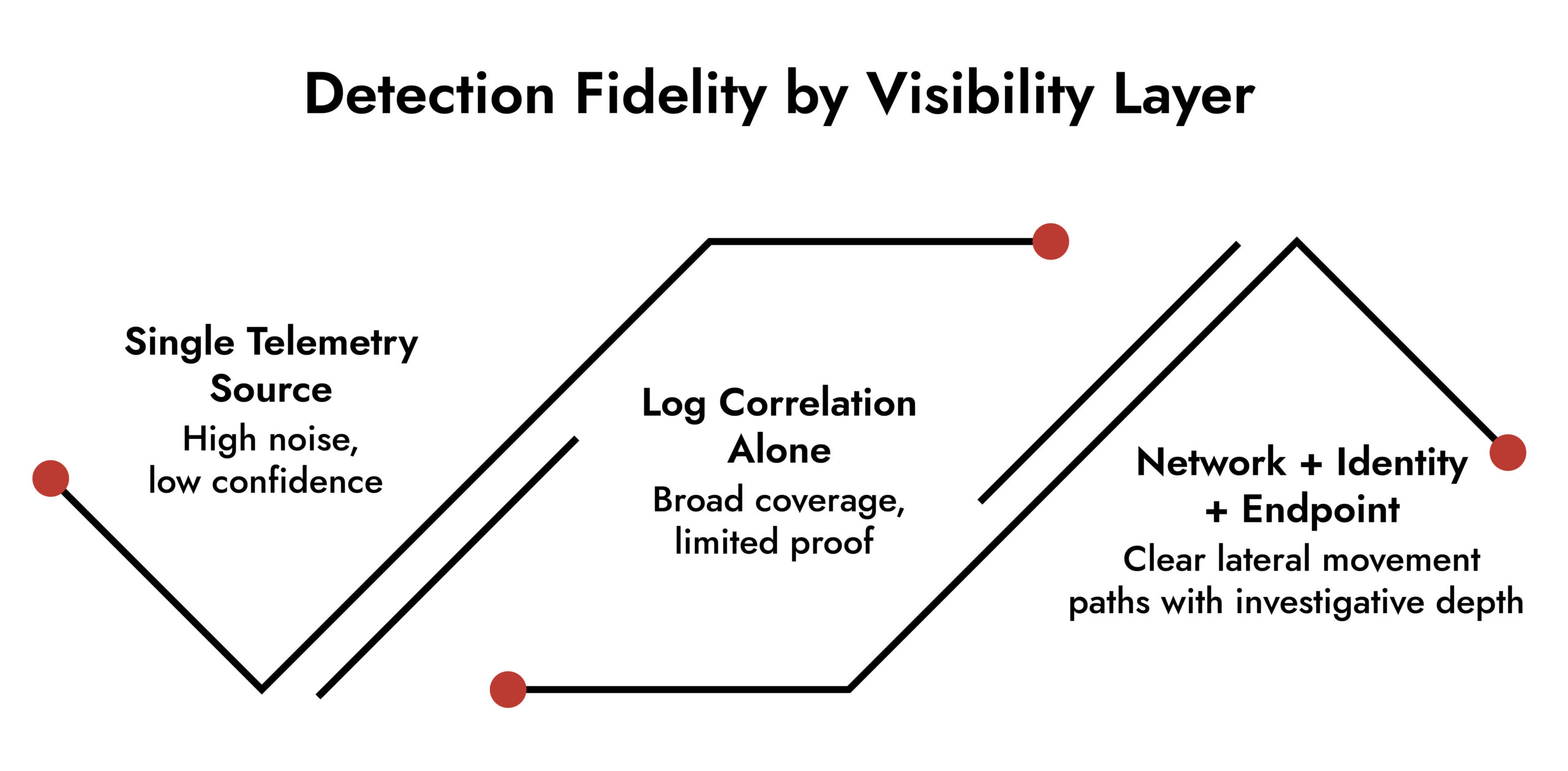
From a single system’s perspective, nothing looks wrong. From an identity log alone, nothing looks urgent. This is why isolated telemetry struggles to surface lateral movement.
What exposes it is context across systems. Patterns cross-time. Relationships across identities and traffic flows. This is where network behavior analysis becomes indispensable.
The TDR Blind Spot No One Can Ignore
Threat detection and response promise correlation. In practice, many programs still operate in silos.
Endpoints detect execution. Identity systems record authentication. Network tools monitor availability. Lateral movement lives between these layers, not inside one of them.
When lateral movement detection is weak, TDR teams face:
- Alerts without validation
- Investigations without evidence
- Containment decisions made too late
Gartner’s 2024 research on security operations maturity highlights internal traffic analysis as a defining factor between reactive and resilient programs. Not more alerts. Better understanding.
Network Visibility is the Foundation, Not an Add-On
There is no shortcut around visibility.
Lateral movement occurs primarily through east–west traffic. If that traffic remains opaque, detection becomes guesswork. Network traffic monitoring provides connective tissue that binds endpoint and identity signals together.
Effective visibility supports:
- Session reconstruction
- Credential misuse detection
- Protocol-level anomaly analysis
- Historical investigation
This depth of insight turns suspicions into conclusions. It gives threat monitoring substances instead of speculation.
Behavior Tells the Truth That Logs Cannot
Attackers avoid signatures. They cannot avoid behavior.
Network behavior analysis identifies deviations that tools and credentials cannot hide. It highlights when:
- Systems communicate outside normal peer groups
- Service accounts behave interactively
- Authentication patterns shift directionally
- Internal scanning precedes privilege escalation
NIST guidance updated in 2024 reinforces behavior-driven detection as a requirement for identifying advanced and persistent threats. This approach scales across environments without relying on fragile indicators.
In practice, it is the analytical engine behind reliable lateral movement detection.
Lateral Movement and the Insider Risk Problem
Not every lateral movement starts outside the organization.
Compromised insiders, malicious insiders, and abused service accounts generate patterns indistinguishable from external attackers once trust is misused. This is why insider threat detection depends heavily on internal visibility.
Indicators often include:
- Access inconsistent with job function
- Lateral expansion without operational need
- Privilege escalation followed by reconnaissance
- Sudden shifts in access timing or scope
When identity context intersects with network behavior analysis, intent becomes clearer without relying on assumptions.
360° Cybersecurity with NetWitness Platform
– Unrivaled visibility into your organization’s data
– Advanced behavioral analytics and threat intelligence
– Threat detections and response actionable with the most complete toolset

The Data That Makes Detection Credible
High-confidence lateral movement detection does not rely on a single signal. It emerges from correlation.
Critical sources include:
- Full packet data and metadata
- Authentication and directory services
- Endpoint execution context
- DNS and internal traffic flows
CISA’s 2025 detection engineering guidance emphasizes multi-source correlation as the backbone of accurate threat detection. Context reduces false positives. Evidence accelerates responses.
Automation Helps, But it Cannot Think for You
Automation has a place in TDR. It shortens response time and reduces fatigue. It does not replace judgment.
Automated workflows excel at:
- Enrichment
- Triage
- Initial containment
They fail when detection lacks certainty. Poor lateral movement detection amplified by automation only accelerates the wrong response.
The most effective programs automate decisively where evidence is strong and preserve analyst judgment where impact is high.
How NetWitness Approaches Lateral Movement Detection
NetWitness focuses on exposing behavior that attackers cannot avoid.
From a technical perspective, the platform emphasizes:
- Deep network visibility with packet-level inspection
- Correlation across network, endpoint, and identity data
- Session reconstruction for investigation and validation
- Support for threat detection and response across hybrid environments
This approach aligns with modern guidance from NIST and government advisories by prioritizing evidence-driven detection over alert volume. It strengthens lateral movement detection without relying on assumptions or black-box scoring.
Why This Matters More Now Than Ever
Attackers have not become noisier. They have become quieter.
Security teams that focus primarily on entry-point defense continue to absorb the cost of internal blind spots. Lateral movement detection addresses the phase of an attack where intent becomes unavoidable and intervention still matters.
It sharpens threat detection. It strengthens cyber threat security. It turns internal traffic into intelligence.
Conclusion
Threat detection and response only works when it mirrors how real attacks unfold. They move laterally. They exploit trust. They hide in normal operations.
Lateral movement detection exposes that reality. It provides the clarity needed to act early, respond confidently, and limit damage before it compounds.
Organizations that treat lateral movement as a core detection priority do not just detect faster. They understand better. And that understanding is what ultimately changes outcomes.
Frequently Asked Questions
1. What is lateral movement in cybersecurity?
Lateral movement describes how attackers expand access inside a network after initial compromise by abusing credentials, trust relationships, and standard protocols.
2. Why is lateral movement detection critical in TDR?
Lateral movement detection reveals attacker behavior that traditional threat detection misses, making it central to effective threat detection and response.
3. What data sources are essential for detecting lateral movement?
Reliable detection requires network traffic monitoring, identity data, endpoint telemetry, and authentication logs analyzed together.
4. Can automation improve lateral movement response?
Automation accelerates response actions, but accurate detection and human oversight remain critical for preventing unintended disruption.
5. Why is lateral movement difficult to detect?
Because attackers use legitimate tools and credentials, lateral movement often resembles normal activity without deep network visibility and behavior analysis.
6. How does lateral movement relate to insider threat detection?
Lateral movement patterns often expose insider misuse and compromised accounts when analyzed through network behavior and identity context.
Autonomous AI Defenders for a Smarter SOC






