How do SOC teams evaluate whether a SIEM system is actually effective?
SOC teams evaluate SIEM effectiveness by looking at outcomes, not alert volume. The focus is on whether siem logs lead to faster detection, cleaner alerts, and quicker response. Metrics like detection and response time, alert quality, and log monitoring coverage show if the SIEM is improving security monitoring or just adding operational noise.
Your SIEM SOC is drowning in alerts. Analysts are burning out. Management wants proof that the security monitoring investment is worth it. Sound familiar?
Here’s the thing: most organizations treat their SIEM cyber security software like a black box. Logs go in, alerts come out, and nobody really knows if it’s working until something breaks. That’s not security operations. That’s a security theater.
Let’s break down the metrics that actually matter when you’re evaluating whether your SIEM system is doing its job or just eating into your budget.
Why Measuring SIEM System Effectiveness Actually Matters
Before we dive into specific SIEM KPIs for SOC, let’s talk about why this isn’t just another checkbox exercise.
When you’re running security monitoring SIEM system operations, you’re dealing with three realities: limited analyst time, unlimited attack surface, and executive teams who want ROI in spreadsheet form. Without concrete metrics, you can’t optimize your log monitoring, you can’t justify headcount, and you can’t prove that your top SIEM tools are reducing risk.
What this really means is that metrics aren’t about creating fancy dashboards. They’re about making your SOC smarter, faster, and more defensible.

Core Metrics That Tell the Real SIEM System
Mean Time to Detect (MTTD)
This one is straightforward. How long does it take when an attack starts, to when your SIEM logs triggers an alert that gets noticed?
The average MTTD across industries sits around 207 days. Yes, days. If yours is measured in hours, you’re already ahead. If it’s measured in minutes for critical threats, you’re in the top tier.
But here’s what most people miss: MTTD isn’t just about your SIEM monitoring tools. It’s about log quality, correlation rules, and whether your analysts trust the alerts enough to investigate them immediately. A low MTTD with high false positives is meaningless.
Track this per threat category. Your MTTD for ransomware should be very different from your MTTD for credential stuffing attempts.
Mean Time to Respond (MTTR)
Detection is only half the battle. MTTR measures the gap between “we see the problem” and “we’ve contained the problem.”
For a well-tuned SIEM SOC, you want this under one hour for critical incidents. Anything over four hours means your response playbooks need work, your escalation paths are broken, or your analysts don’t have the tools to act quickly.
What affects MTTR? The usual suspects: alert fatigue, unclear runbooks, too many tools in the stack, and analysts who spend more time gathering context than actually responding. Your log monitor setup should feed directly into response workflows, not create extra investigation steps.
Alert-to-Incident Ratio
This is the metric that separates mature SOCs from alert factories. Out of 1,000 alerts, how many turn into actual incidents worth investigating?
If you’re below 10%, you’ve got a tuning problem. Your siem logs are either too noisy, your correlation rules are too sensitive, or you’re monitoring things that don’t matter.
Top-performing SOCs aim for 15-25% conversion rates. That means when an alert fires, there’s a decent chance it’s real. Analysts start trusting the system. Response times drop. Everyone is happier.
To improve this, focus on reducing false positives through better log monitoring configuration and smarter correlation. Don’t just turn off the noisy alerts. Understand why they’re firing and fix the root cause.
Log Source Coverage
You can’t detect what you can’t see. This metric tracks what percentage of your critical assets are sending siem logs to your platform.
Aim for 95%+ coverage of Tier 1 assets (domain controllers, crown jewel databases, internet-facing servers). Anything less and you’ve got blind spots an attacker will find.
But coverage isn’t just about quantity. Are you getting the right logs? Windows event logs without PowerShell logging enabled are nearly useless for detecting modern attacks. Your log monitor should track log quality, not just log volume.
Threat Detection Accuracy
This measures your true positive rate. When your SIEM monitoring flags something as malicious, how often is it actually malicious?
Calculate this by dividing confirmed true positives by total alerts investigated. If this number is below 40%, your analysts are spending most of their day chasing ghosts.
Improving accuracy means better threat intelligence feeds, tuned correlation rules, and regular validation against known attack patterns. The top SIEM tools give you frameworks for this, but you still need humans to validate and adjust.
Analyst Productivity Metrics
Here’s where it gets interesting. How many alerts can one analyst effectively handle per shift? How long does the average investigation take? What’s the case closure rate?
A productive SOC analyst should be able to investigate 15-25 alerts per eight-hour shift, assuming reasonable complexity. If your team is handling 50+ alerts per person, they’re either ignoring most of them or your log monitoring is generating too much noise.
Track time spent per investigation phase: initial triage, evidence gathering, analysis, and documentation. If analysts spend more time documenting than investigating, your workflows need streamlining.
Data Ingestion and Processing Metrics
Your SIEM cyber security software needs to actually ingest the logs you’re sending it. Track ingestion lag (how far behind real-time are your logs?), parsing errors, and data loss events.
For real-time security monitoring, you want ingestion lag under 60 seconds for critical log sources. Anything over five minutes means you’re operating partially blind.
Also watch your EPS (events per second) capacity. If you’re running at 80%+ of license capacity, you’re one security event away from dropping logs during an incident. Not great.
Rule Effectiveness Score
Not all correlation rules are created equal. Track which rules actually catch threats versus which ones just make noise.
For each detection rule, measure: total triggers, true positive rate, time to investigate, and incidents generated. Kill rules that consistently underperform. Your security monitoring SIEM should get smarter over time, not just bigger.
Elevate Threat Detection and Response with NetWitness® SIEM
-Correlate data across users, logs, and network for unified visibility.
-Detect advanced threats with AI-driven analytics and behavioral insights.
-Accelerate investigations using automated enrichment and guided workflows.

Putting These Metrics to Work
Numbers without action are just dashboard decoration. Here’s how to use these SIEM KPIs for SOC improvement:
Set baselines for your current state. You can’t improve what you don’t measure, and you can’t measure improvement without knowing where you started.
Review metrics weekly with your SOC team. Make adjustments based on what the data tells you. Monthly reviews with leadership to show trends and justify resource requests.
Most importantly, tie metrics to specific improvements. If MTTD is high, which log sources are you missing? If alert-to-incident ratio is low, which rules need tuning? Metrics should drive decisions, not just document failure.
The Bottom Line
Evaluating SIEM effectiveness isn’t about collecting every possible metric. It’s about tracking the numbers that tell you whether your SOC is actually protecting the organization or just keeping analysts busy.
Focus on detection speed, response time, alert quality, and analyst productivity. Everything else is noise. Get these right, and your log monitoring becomes a competitive advantage instead of a compliance checkbox.
Frequently Asked Questions
1. How to measure SOC effectiveness?
Measure detection and response times (MTTD and MTTR), alert quality (true positive rates), coverage of critical assets, and analyst productivity. The best SOCs combine technical metrics with business impact measures like prevented breaches and risk reduction.
2. What is the metric used to measure the effectiveness of a SIEM system?
There’s no single metric, but alert-to-incident ratio is often considered the most telling. It shows whether your SIEM generates actionable intelligence or just noise. Combine this with MTTD and log source coverage for a complete picture.
3. How to evaluate a SIEM?
Look at log ingestion capabilities, correlation accuracy, integration with your existing tools, analyst workflow efficiency, and total cost of ownership. Test it against known attack scenarios and measure how quickly it detects and surfaces threats.
4. Why is measuring SIEM effectiveness critical for SOC operations?
Without metrics, you can’t optimize analyst workflows, justify budget requests, or prove risk reduction. You also can’t identify gaps in coverage or tune out false positives systematically. Measurement turns security operations from reactive firefighting into strategic defense.
5. How can SIEM metrics help improve SOC analyst productivity?
Metrics identify bottlenecks in investigation workflows, reveal which alerts waste time, and show where automation could help. They also provide objective feedback for tuning correlation rules and reducing alert fatigue, letting analysts focus on real threats instead of false alarms.
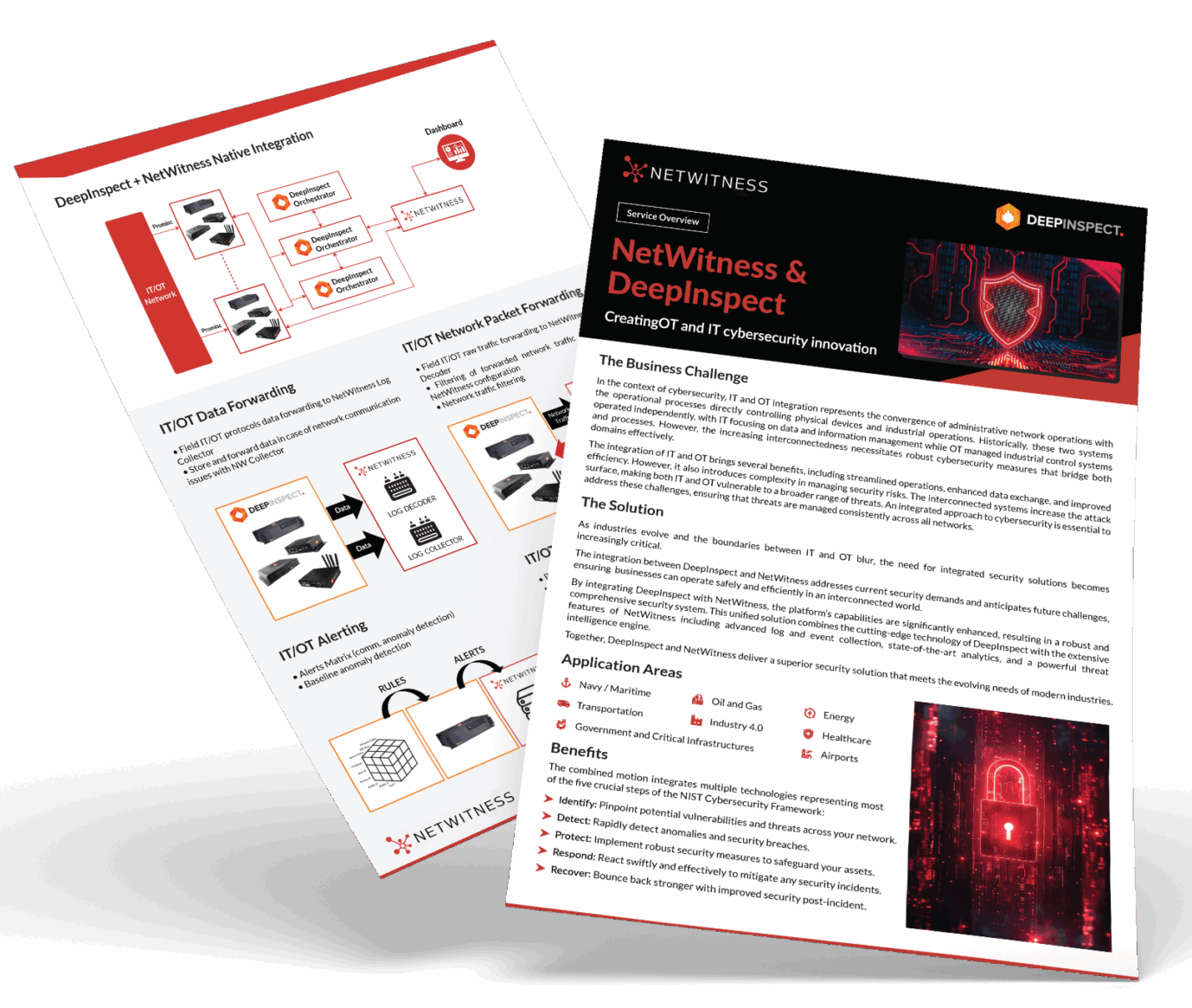
Unify IT and OT Threat Detection with NetWitness® and DeepInspect
-Correlate IT and OT telemetry for end-to-end operational visibility.
-Detect advanced threats across industrial and enterprise networks with protocol-level intelligence.
-Accelerate investigations using enriched OT context and unified analytics.
-Reduce blind spots and strengthen response across converged IT/OT environments.