Incident Response Process Explained
The incident response procedure is the planned process that businesses take to find, contain, eliminate, and get through cybersecurity events on behalf of their organization. The seven stages of this process stretch from preparation toward post-incident follow up and clearly define the responsibilities involved in managing cybersecurity events. If executed properly, the proper steps through an incident response process lower the time to respond to incidents, lessen the amount of data lost during an event, help ensure compliance with regulatory agencies, and allow for rapid recovery from a cybersecurity event.
Introduction
The Security Operations Centers (or SOCs) are the eyes and ears of an organization, providing continuous monitoring of its systems and networks. SOCs are the first responders to any incidents 24 hours a day and are responsible for determining the nature of unusual events occurring on Systems, Networks, and Applications.
Once a confirmed breach has been discovered, it will be escalated to the Incident Response Team (or IRT) for further investigation and remediation. This includes containment of the threat, total removal of the threat, and the establishment of safeguards to prevent its return.
SOCs and IRTs typically work together very closely when addressing any confirmed breach; however, the transition from detection to action is often where an organization may experience the most difficulty. In this guide, we outline in detail the complete process for incident response, showing how SOCs and IRTs interact with each other from the time that the incident is first detected until the recovery from the incident to the full operation level is completed.
Additionally, we discuss why having a structured approach to responding to a cyber security incident, from detection to the final resolution, is important in order to minimize the impact of an incident on the organization, minimize downtime due to the incident, and ultimately protect the organization.
Why Most Organizations Fail at Incident Response
Many organizations treat incident responses as reactive exercises. Plans exist on paper, but they are rarely tested under pressure. When a real incident occurs, teams scramble, decisions slow down, and mistakes compound.
Failure is not a lack of awareness. Most security leaders know they need incident response capabilities. The real issue is the gap between knowing what to do and being able to execute clearly defined incident response process steps when systems are already under attack.
The Hidden Costs of Poor Incident Response Planning
Poor planning creates problems that go far beyond the initial breach. Without documented cyber security incident response steps, every delay increases financial, operational, and reputational damage.
Common consequences include:
- Delayed containment allows attackers more time to move laterally, encrypt systems, or steal data
- Confusion across teams leads to duplicated effort and missed actions
- Forensic evidence is overwritten or destroyed during rushed remediation
- Regulatory deadlines are missed, increasing legal and compliance penalties
For SOC teams, the biggest risk is unclear escalation and ownership. When incident management roles and responsibilities are not defined, teams improvise under stress. That improvisation often becomes the most expensive part of the incident.
How Attackers Exploit Weak Incident Response Processes
Modern attackers understand how organizations respond to incidents. They design attacks specifically to exploit weak or untested response procedures.
Threat actors commonly take advantage of:
- Reduced staffing during nights, weekends, and holidays
- Multiple attack paths launched at once to overwhelm responders
- Long dwell times that allow them to study response patterns
- Poor coordination between SOC, IT, legal, and leadership teams
A fragmented incident response process gives attackers exactly what they need: time, confusion, and silence.
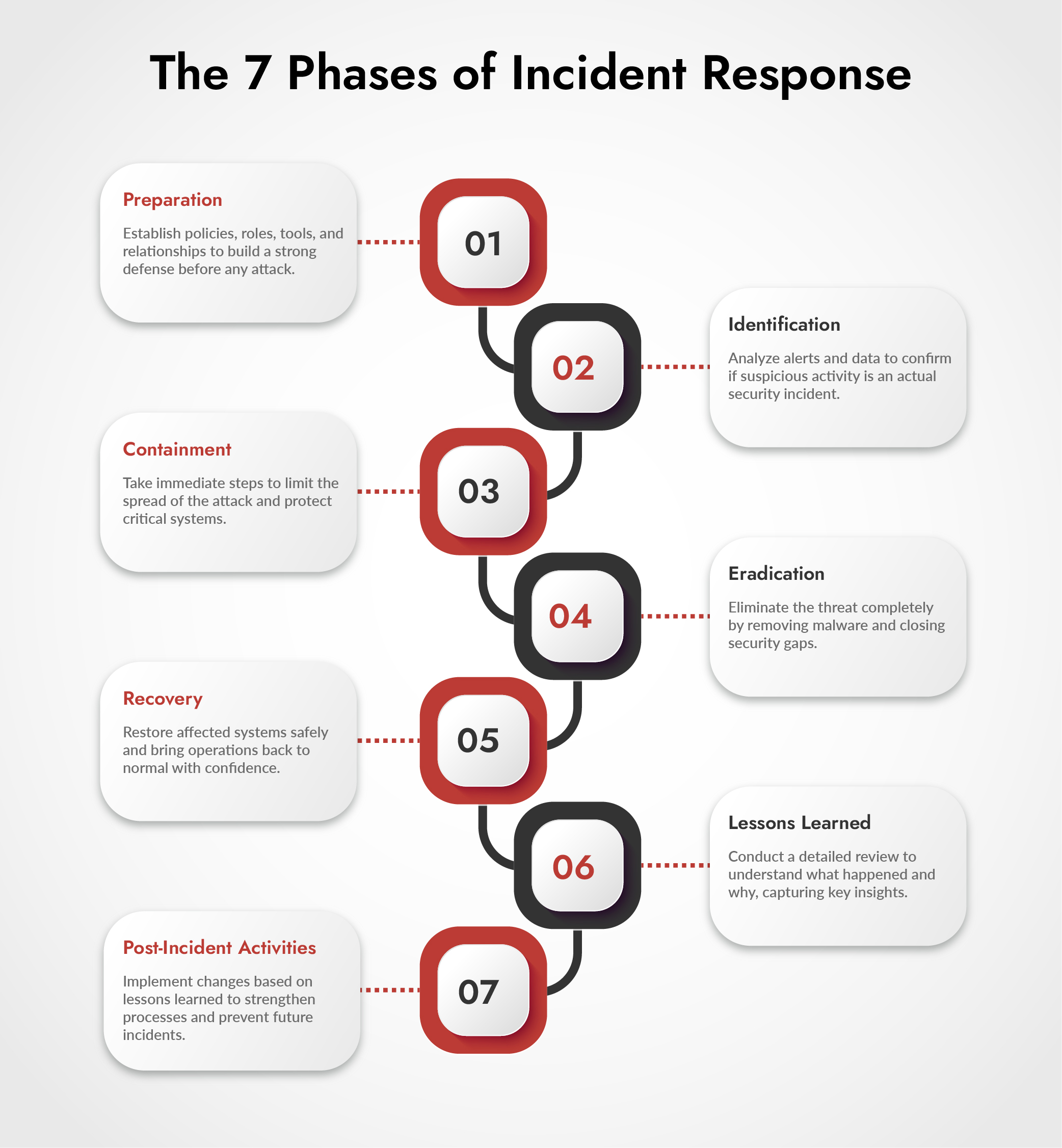
The 7 Phases of Incident Response Process
The way incidents will be handled from beginning to end is using a seven-phase structure (incident response phases). These phases have been proven, practical, and are intended to create order out of chaos, particularly when dealing with high-pressure situations.
Each phase builds on the previous one. Skipping steps or rushing execution weakens the entire response.
Phase 1 – Preparation (Building Your Defense Before War Begins)
Preparation separates organizations that survive cyber attacks from those that don’t. This security incident response phase happens before incidents occur, but it determines everything that follows.
Most cyber incident response companies fail here because preparation feels like over-engineering – until you desperately need it. Then it becomes the foundation that keeps everything else working.
Your preparation phase must address four critical areas:
- Policies that actually work under pressure – Clear decision-making authority, escalation procedures, and communication protocols that function during chaos
- Teams that know their roles instinctively – Cross-trained personnel who can execute without confusion during high-stress situations
- Technology that integrates seamlessly – Tools that share data and coordinate responses instead of creating information silos
- Relationships built before you need them – Established contacts with legal counsel, law enforcement, and regulatory bodies
Phase 2: Identification – Confirming a Real Security Incident
Identifying suspicious activity determines whether or not that suspicious activity is, indeed, a valid security incident and warrants taking formal response to it. By confirming the validity of a suspicious security incident, organizations can prevent expending time and effort on false positives while allowing for the timely escalation of verified threats (which allows security personnel to act quickly to mitigate an active or potential attack).
Identification of a suspicious security incident is based on the following:
- Alerts received from automated solutions such as SIEM, endpoint monitoring and network monitoring solutions
- Employee complaints of phishing, credential misuse and/or other unusual behavior
- Known threat intelligence and malicious attack signatures
- Analytic tools that evaluate abnormal behavior against baseline user behaviors
Based on this information, the Security Operations Centre (SOC) will determine whether they can take action on the incident independently or whether they need to escalate the incident to the formal incident response process.
Phase 3: Containment – Limiting Damage Quickly and Carefully
Containment focuses on stopping the attack from spreading while preserving evidence. This phase requires fast judgment and strong coordination.
Containment actions should follow predefined playbooks. Poorly planned containment can alert attackers and cause them to hide deeper in the environment, increasing investigation time and complexity.
Teams must balance:
- Speed of response
- Business impact of isolation actions
- Preservation of forensic data
Clear documentation during containment is essential for later review and regulatory reporting.
Fortify Cyber Defense with Threat Intel + Incident Response
Combine real-time threat intelligence with rapid incident response workflows.
Detect advanced threats before they strike — armed with enriched context and actionable alerts.
Respond faster and smarter with orchestrated, data-driven playbooks.
Build a resilient security posture that adapts to evolving cyber threats.

Phase 4: Eradication – Removing the Threat Completely
Eradication eliminates malicious activity and fixes the weaknesses that allow the attack to occur. This phase should only begin once investigators understand the scope of compromise.
Eradication typically includes:
- Removing malware and malicious tools
- Disabling compromised accounts and credentials
- Patching exploited vulnerabilities
- Rebuilding heavily affected systems from clean sources
Rushing eradication often leads to reinfection, extending the incident response process unnecessarily.
Phase 5: Recovery – Restoring Operations Securely
Recovery focuses on restoring systems and services without reintroducing risk. This is where incident recovery becomes a business-critical function, not just a technical task.
Recovery activities include:
- Gradual system restoration with heightened monitoring
- Validating restored data against clean backups
- Monitoring performance and stability
- Increasing visibility for early detection of recurring threats
Successful recovery balances speed with caution.
Phase 6: Improving the Response
Lessons learned turn an incident into a learning opportunity. These sessions should happen shortly after closure while details are still fresh.
Key outputs include:
- A clear incident timeline
- What worked and what failed
- Business impact analysis
- Specific improvements with owners and deadlines
This phase strengthens future cyber security incident response steps.
Phase 7: Post–Incident Monitoring – Preventing Recurrence
Post-incident monitoring ensures that lessons learned are implemented, not forgotten. This phase closes the loop.
Typical actions include:
- Updating response procedures
- Enhancing training and simulations
- Improving tooling and integrations
- Reporting improvements to leadership
Without this phase, the same mistakes will repeat.
Partner with NetWitness for Expert Incident Response Services
Having a mature incident response plan in place requires a lot of coordination and experience, as well as an understanding of the technology involved. NetWitness is here to assist organizations with their security incidents from beginning to end, as well as afterwards.
NetWitness provides both reactive and proactive incident response services such as Incident Response Retainers, Rapid Deployment, Red Team Engagements, Technical Assessments, and Incident Response Training. All of these services allow an organization to improve its readiness, decrease the impact of a security breach, and enhance its long-term resiliency through retainers, rapid deployment, technical assessments, and incident response training.
By partnering with NetWitness, your SOC and Incident Response teams will have the ability to respond effectively and efficiently, when it truly matters.
Frequently Asked Questions
1. What are the 7 phases of incident response process?
The seven phases are preparation, identification, containment, eradication, recovery, lessons learned, and post-incident activities. Each phase of incident response process serves a specific purpose while building toward the next, creating an integrated system for managing security incidents effectively.
2. How long should incident response steps take?
Response timelines vary dramatically based on incident complexity and organizational preparedness. Simple incidents might resolve in hours, while sophisticated attacks can take weeks or months. The key is establishing realistic response time objectives based on business requirements and regulatory obligations.
3. What’s the most critical phase in the incident response process steps?
Preparation is typically most critical in the incident response process steps because it establishes the foundation for everything that follows. Organizations investing heavily in preparation achieve 54% faster response times and 39% lower costs compared to those with reactive approaches.
4. How do you measure incident response effectiveness?
Track metrics including detection time, response time, containment success, and recovery duration. Compare these measurements to industry benchmarks and historical performance to identify improvement opportunities and demonstrate program value.
5. What tools are essential for effective incident response preparation ?
Essential tools include SIEM platforms for event correlation, NDR solutions for network threat detection, communication systems for team coordination, and forensic tools for evidence collection. Choose integrated platforms rather than point solutions to eliminate information silos.
Avoid Delays and Strengthen Response with NetWitness Guidance






