What is Incident Response in Cybersecurity?
Incident response in cybersecurity is the structured process organizations use to detect, contain, investigate, and recover from cyber incidents. Following clear phases – preparation, detection, containment, eradication, recovery, and lessons learned, teams can reduce downtime, limit financial and reputational damage, and improve overall resilience. Modern IR programs combine people, process, and technology, integrating endpoints, network, and cloud visibility with expert guidance to respond faster and smarter.
Why Should CISOs Care About Incident Response?
Cybersecurity breaches are inevitable. The question isn’t whether an incident will occur, but how quickly your organization can detect, respond to, and recover from it. Incident response in cybersecurity is the framework that makes this possible. For CISOs and IT leaders, it’s not just about technical mitigation; it’s about protecting operations, minimizing regulatory risk, and preserving stakeholder trust.
In 2024, breaches were increasingly complex, involving cloud misconfigurations, supply-chain attacks, and advanced ransomware campaigns. Organizations that lacked structured incident response plans faced longer downtime and higher remediation costs. A mature incident response in cybersecurity program ensures teams can act decisively, contain damage early, and gain actionable intelligence for future prevention.
What Are the Key Phases of Incident Response?
Understanding the phases of incident response is crucial for designing effective workflows and ensuring every team member knows their role.
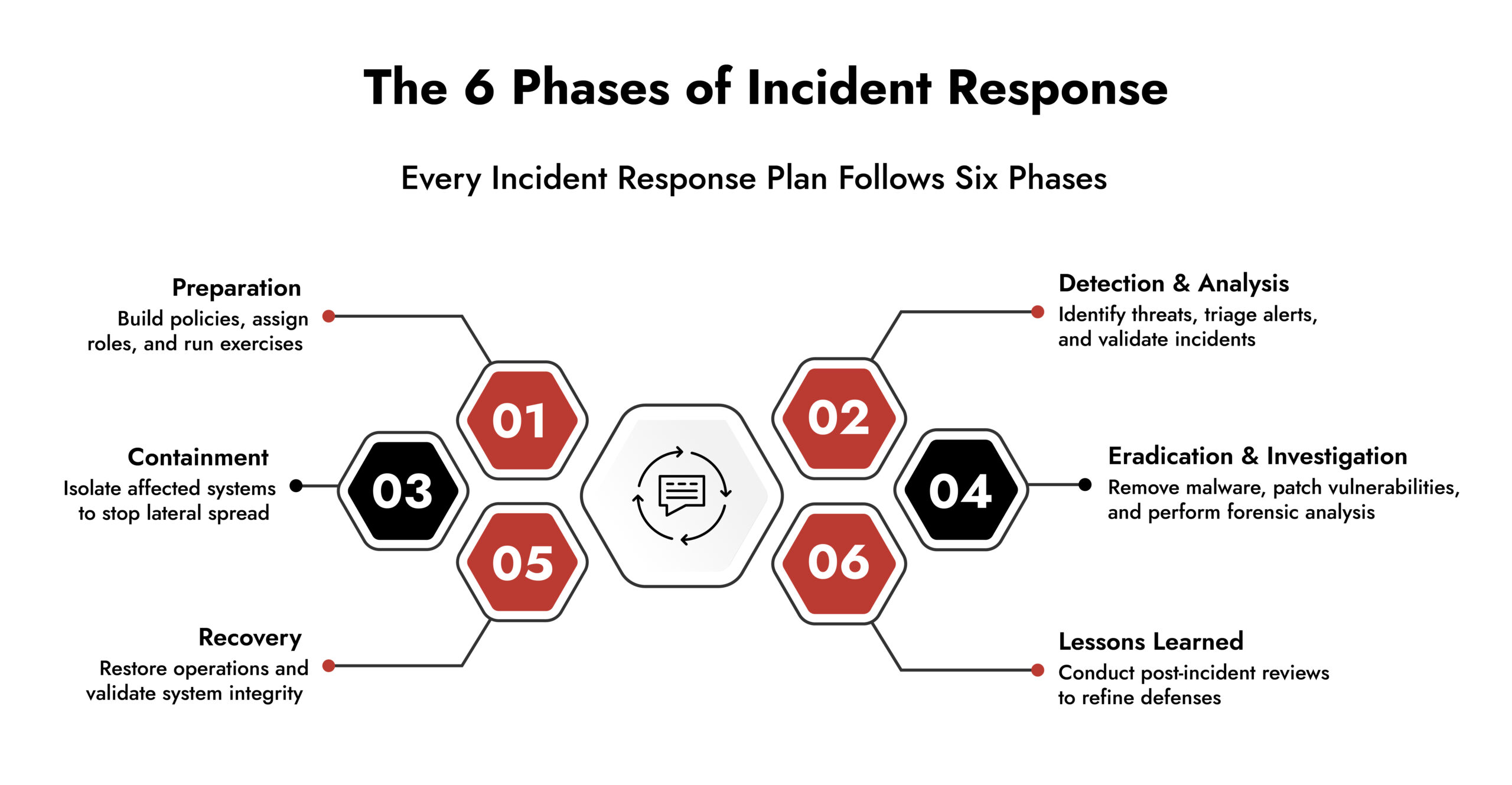
- Preparation – Preparation sets the foundation. It includes defining policies, assigning responsibilities, building monitoring and alerting systems, and conducting regular compromise assessments, tabletops, and Red Team exercises. Teams that invest in preparation respond faster and with more confidence because they already know what to do when a breach occurs.
- Detection and Analysis – Detection involves identifying unusual activity and confirming whether it represents a true security incident. Cyber threat analysis requires correlating alerts, prioritizing threats, and understanding potential impacts. Accurate detection reduces false positives and ensures resources focus on genuine threats.
- Containment – Once a threat is confirmed, containment isolates affected systems to prevent the attacker from spreading further. This can include network segmentation, endpoint isolation, or restricting user access. Effective containment buys time for forensic investigation without causing unnecessary disruption to the rest of the business.
- Eradication and Investigation – After containment, the threat must be removed and systems restored to a secure state. Investigation identifies the root cause, the attack vector, and any vulnerabilities exploited. Comprehensive forensics provides insight into how to prevent recurrence.
- Recovery – Recovery restores normal operations while continuing to monitor signs of residual threats. Incident response teams validate system integrity, confirm business continuity, and gradually bring systems back online.
- Lessons Learned – Every incident provides valuable insights. Lessons learned involve post-mortem analysis, updating incident response procedures, refining detection tools, and sharing knowledge across the organization. This phase ensures continuous improvement and strengthens overall cybersecurity posture.
Rapid, Expert Response with NetWitness® Incident Response Services
-Accelerate threat containment with experienced IR specialists.
-Investigate effectively using advanced forensics and analytics.
-Minimize business impact with fast, guided remediation.

How Does Incident Response Reduce Business Risk?
Incident response in cybersecurity directly addresses operational, financial, and reputational risks:
- Minimizing Downtime: Timely containment and recovery reduce the impact on critical business systems.
- Regulatory Compliance: A documented cybersecurity incident response plan helps demonstrate due diligence under GDPR, HIPAA, PCI DSS, and other regulations.
- Preventing Escalation: Proper response prevents attackers from moving laterally across your network and systems.
- Preserving Stakeholder Trust: Effective communication and swift action maintain confidence from clients, partners, and investors.
By reducing the consequences of attacks, organizations can maintain operational stability even in high-stakes environments.
What Common Challenges Do Organizations Face in Incident Response?
Many companies struggle to execute effective Incident Response due to several recurring challenges:
- Detection Gaps: Limited visibility across networks, cloud workloads, remote endpoints, and operational technology environments.
- Role Ambiguity: Unclear responsibilities among security, IT, legal, and communications teams can delay decision-making.
- Tool Overload: Multiple, siloed tools create alert fatigue, slowing down response times.
- Insufficient Testing: Plans that aren’t regularly exercised may fail when a real breach occurs.
- Knowledge Retention: High turnover or insufficient training can lead to inconsistent execution.
Addressing these gaps requires a combination of people, processes, and technology, supported by clear policies and continuous learning.
How Do You Build an Effective Incident Response Plan?
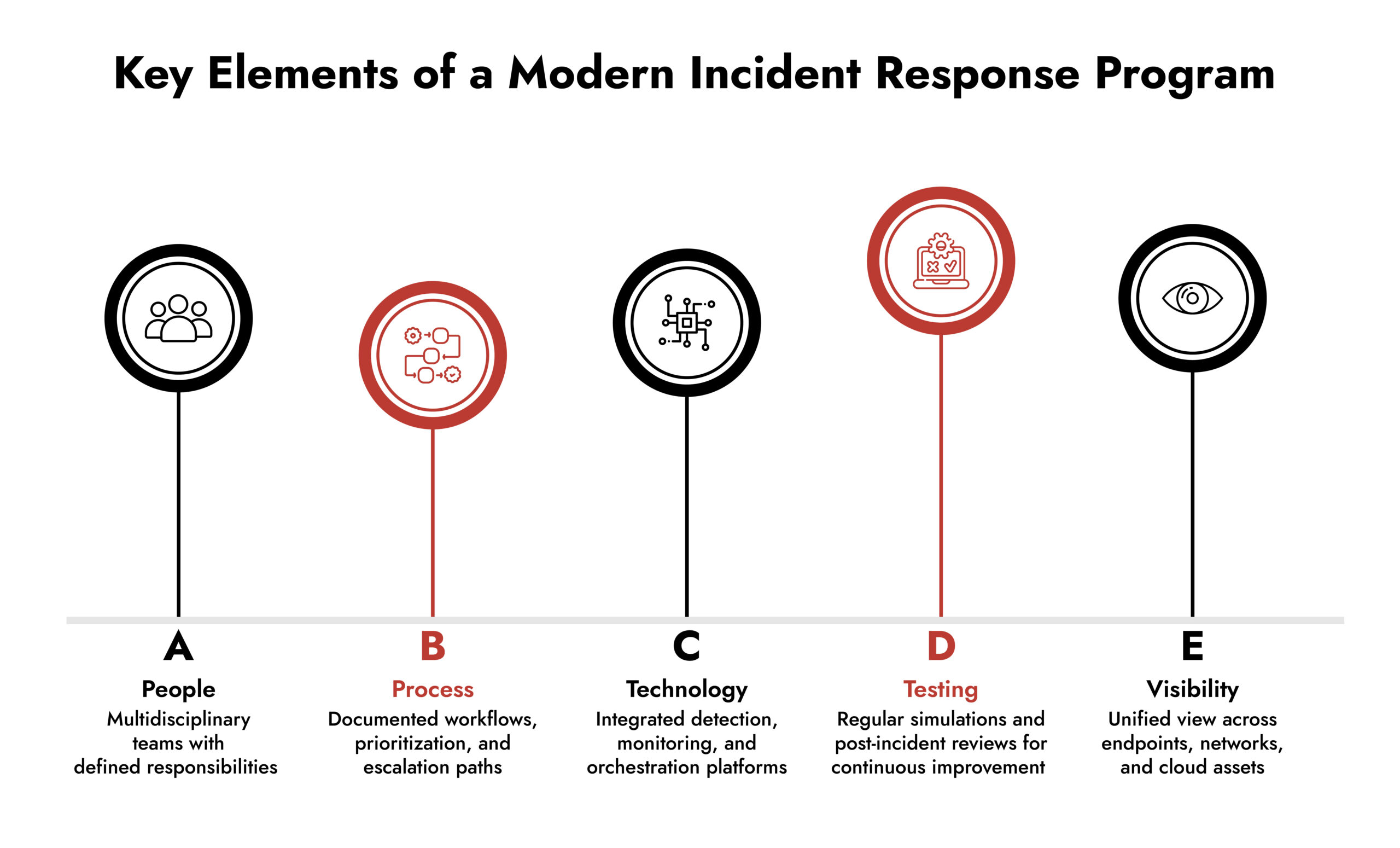
A strong cybersecurity incident response plan should integrate these key pillars:
- People – Multidisciplinary teams are essential. Include IT operations, security analysts (including dedicated threat hunters), legal, and communications. Clearly defined roles and escalation paths ensure that everyone knows their responsibilities during an incident.
- Process – Document workflows, accurately prioritize incidents by severity, and define escalation procedures. Include a testing schedule for tabletop exercises, red team simulations, and post-incident reviews.
- Technology – Deploy tools that provide visibility across endpoints, networks, and cloud services. Integration with monitoring, detection, and orchestration platforms ensures that alerts are actionable, and response steps are efficient.
- Testing and Continuous Improvement – An IR plan is a living document. Conduct exercises and post-incident reviews regularly to refine processes and tools. This keeps your team agile and prepared for evolving threats.
How Does NetWitness IR Support Effective Incident Response?
NetWitness IR is a product agnostic incident response service built on proven frameworks, operational discipline, and deep experience. This service can be engaged in support of NetWitness security products or to work alongside your existing security stack to bring clarity and resolution to critical cybersecurity situations. Unlike a reactive tool, NetWitness IR often becomes the point of discovery, surfacing hidden threats and giving teams a clear, actionable picture of what’s happening. With seasoned responders driving the process, it dramatically shortens detection-to-recovery timelines, helping organizations contain incidents faster, minimize disruption, and strengthen overall security posture.
- Rapid Engagement: Teams mobilize quickly to contain incidents, investigate root causes, and eradicate threats.
- 24/7 Readiness: Retainer services ensure that experienced responders are familiar with your environment before an incident occurs.
- Compromise Assessments: Identify stealthy threats already present in the network before they escalate.
- Training and Tabletop Exercises: Strengthen organizational readiness with realistic simulations and expert guidance.
- Integrated Visibility: NetWitness IR works with NDR, EDR, SIEM, and SOAR platforms to provide correlated insights and actionable intelligence.
By combining expertise, proactive assessments, and integrated tools, NetWitness IR helps CISOs reduce response times, minimize risk, and continuously improve security posture.
Conclusion: Turning Incident Response into a Strategic Advantage
Incident response in cybersecurity has become a core component of organizational resilience. By understanding the phases of incident response, addressing common operational challenges, and building a comprehensive cybersecurity incident response plan, CISOs can reduce downtime, minimize financial and reputational damage, and strengthen trust with stakeholders.
A mature incident response program doesn’t just react to threats; it anticipates them. Continuous testing and assessments, clear roles, integrated tools, and post-incident lessons ensure that each event makes your organization smarter, faster, and more prepared for the next challenge.
Services like NetWitness IR provide the visibility, expertise, and proactive support needed to accelerate containment, drive forensic investigations, and reinforce overall security posture. With the right strategy and tools in place, incident response services becomes more than a reactive process; it becomes a strategic advantage that empowers organizations to stay ahead of evolving cyber threats.
Frequently Asked Questions
1. Why is incident response in cybersecurity important?
It limits downtime, protects assets, ensures compliance, and strengthens overall security posture. Efficient incident response reduces financial, operational, and reputational damage.
2. Who is responsible for incident response?
The CISO leads IR strategy, supported by security analysts, IT teams, legal, and communications. External incident response services provide additional expertise when needed.
3. What are the main phases of incident response?
Preparation → Detection & Analysis → Containment → Eradication & Investigation → Recovery → Lessons Learned.
4. How do you create an incident response plan?
Identify critical systems, assign roles, document workflows, integrate monitoring tools, test regularly, and update the plan based on lessons learned.
5. What types of incidents require response?
All incursions require some response, the following require escalation: ransomware, phishing, insider threats, cloud misconfigurations, supply-chain compromises, and data exfiltration.
6. How often should incident response plans be tested?
At least annually, or whenever major systems, personnel, or regulatory changes occur. High-risk environments may benefit from semi-annual testing.




