What Is Network Detection and Response (NDR)?
Network Detection and Response (NDR) is a cybersecurity approach that continuously monitors network traffic to detect suspicious behavior and respond to threats in real time. NDR solutions analyze raw network data, including encrypted traffic patterns, to identify lateral movement, command-and-control activity, and data exfiltration that traditional security tools often miss.
NDR strengthens threat detection and response by providing deep network visibility and enabling faster investigation and containment of active attacks.
When a cyberattack unfolds, minutes matter — but in most security operations centers, those minutes are lost to chasing false positives, jumping between tools, and piecing together fragments of data.
Network Detection and Response (NDR) changes that. It gives security teams real-time visibility into network traffic and the ability to detect and respond to threats as they happen. Unlike traditional tools, NDR solutions focus on what attackers do once they are inside the network.
This isn’t about adding yet another dashboard to your already crowded screen. It’s about replacing blind spots with visibility and replacing guesswork with certainty. And when you see how NDR works in the NetWitness Platform, the difference becomes clear.
How NDR Solves the Blind Spots in Cybersecurity
SIEMs are great at collecting logs. EDRs excel at endpoint visibility. But neither sees the full scope of what happens in transit. This is why network security monitoring at the packet and flow level has become critical. Without it, attackers can move freely across internal systems without triggering traditional alerts.
Here’s the thing: once an attacker bypasses perimeter controls, their activity leaves traces in the network layer. Lateral movement, unusual data flows, encrypted command-and-control traffic all of it can be spotted if you’re looking at the right place, in the right way, at the right time.
That’s exactly how NDR works. It analyzes raw network traffic in real time, flags anomalies, and surfaces high-fidelity alerts your team can act on.
How NetWitness NDR Works
NetWitness NDR isn’t just another network monitoring tool. It’s an integrated platform that combines deep packet inspection, behavioral analytics, and automated response. Want a deeper dive into NetWitness NDR? Download the NetWitness Network Detection and Response Datasheet to see how full session reconstruction, forensic tools, and real-time analytics empower SOC teams to detect and stop attacks faster. To understand how NDR works in practice, it helps to follow the full lifecycle from traffic capture to response.
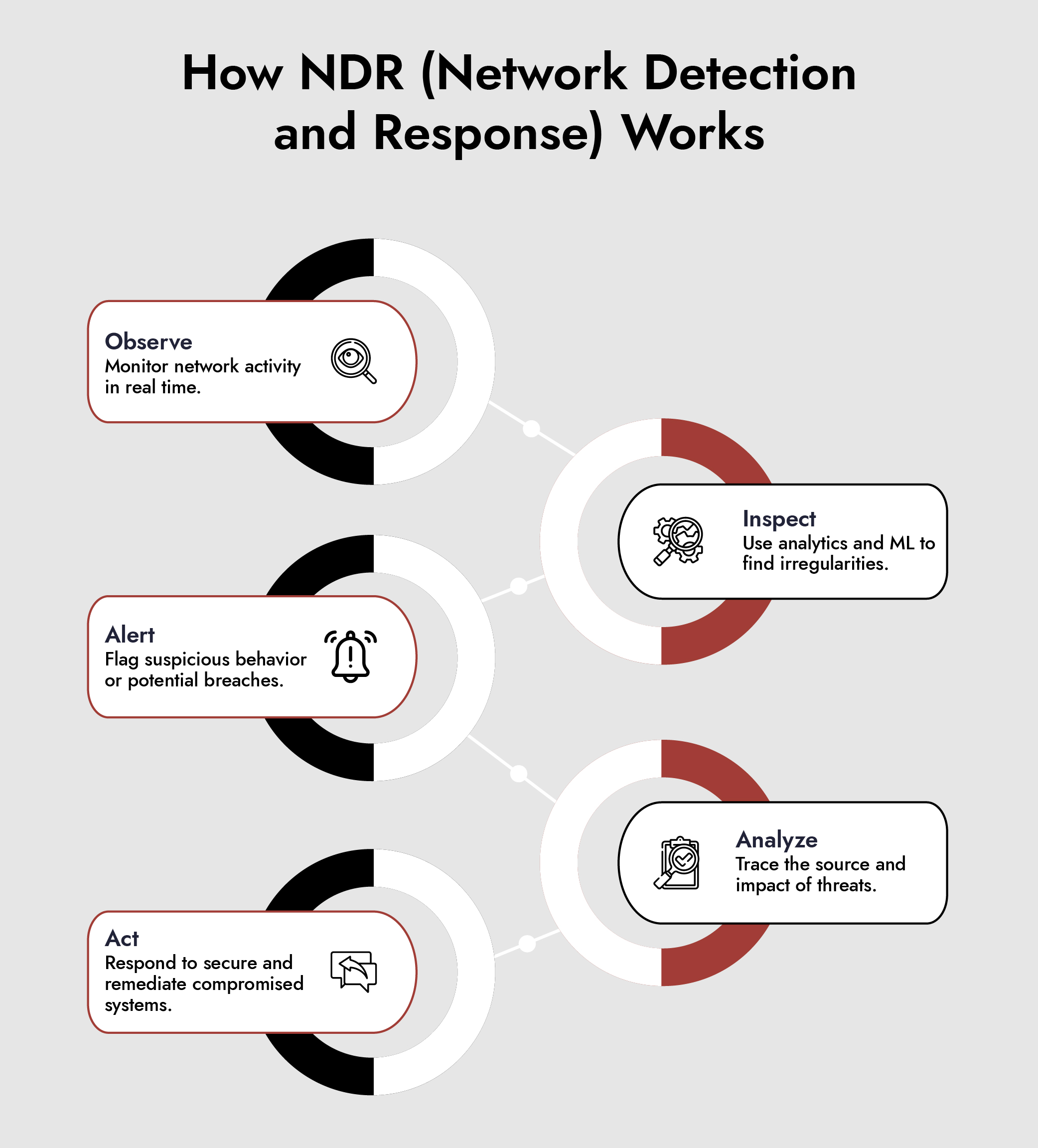
1. Full Packet Capture at Scale:
The process starts with complete visibility. NetWitness network detection and response taps into network traffic at strategic points, capturing both metadata and full packet data.
Why it matters:
- Metadata alone can flag unusual activity, but full packet capture gives forensic-level detail.
- You can replay and investigate traffic later if an alert is triggered days after the fact.
- Coverage includes both north-south traffic (external) and east-west traffic (internal lateral movement).
Example: A finance department workstation begins sending encrypted traffic to an IP in Eastern Europe outside business hours. Logs may miss it, but NDR security sees the raw flow.
2. Real-Time Analysis and Enrichment:
Captured data is immediately analyzed against multiple detection engines:
- Signature-based matching for known threats.
- Behavioral analytics for deviations from baselines.
- Machine learning models trained to detect zero-day tactics.
NetWitness enriches these detections with threat intelligence feeds and contextual metadata mapping IPs, domains, and protocols to known malicious activity.
This is not just “alerting.” It’s alerting with the story behind it.
3. Correlation Across the Security Stack:
Here’s where NetWitness NDR stands apart. Instead of living in its own silo, it integrates directly with SIEM and EDR data.
- A suspicious network alert can be matched with endpoint activity and log events.
- Correlated incidents provide analysts a single, unified view.
- This reduces false positives and reveals multi-stage attack chains.
4. Prioritized Alerts That Cut Through the Noise:
One of the biggest complaints SOC teams have is alert fatigue. NetWitness NDR scores and prioritizes alerts so analysts see the highest-risk issues first.
For example:
- A single port scan may be low priority.
- A port scan plus successful lateral movement attempt from the same source becomes high priority.
5. Guided and Automated Response
Once a threat is confirmed, NetWitness NDR enables direct action:
- Isolating affected assets.
- Blocking malicious IPs or domains.
- Triggering playbooks in integrated SOAR platforms.
This can be manual or fully automated, depending on the organization’s policies.
Proactive Network Threat Detection with NetWitness® NDR
-Spot threats fast with AI-driven analytics.
-See everything across your network and cloud traffic.
-Investigate efficiently with built-in forensic tools.
-Adapt and scale to meet growing security needs.

Why This Matters: Real-World Scenarios
Case 1: Ransomware Lateral Movement
A ransomware variant encrypts files on a single workstation, but before it can spread, NetWitness NDR detects abnormal SMB traffic to multiple servers. Analysts are alerted, isolate the workstation, and stop the attack in minutes.
Case 2: Insider Data Exfiltration
An employee with legitimate credentials uploads gigabytes of sensitive customer data to a personal cloud account. NetWitness flags the unusual data transfer size and destination. The SOC investigates before any compliance violation occurs.
NDR Cybersecurity Without Blind Spots
One of the key benefits of how NDR works in NetWitness is visibility into encrypted traffic.
While many solutions stop at the fact that traffic is encrypted, NetWitness uses advanced TLS fingerprinting and flow analysis to detect suspicious patterns without decrypting content maintaining privacy and security compliance.
It also works in hybrid environments. Whether your workloads run on-prem, in the cloud, or across multiple clouds, NetWitness can ingest and analyze traffic consistently.
The NetWitness Advantage Over Generic NDR
Plenty of vendors can monitor network traffic. Few can:
- Combine it with endpoint and log telemetry.
- Give forensic-level packet capture without choking performance.
- Offer guided investigation workflows so junior analysts can work like veterans.
NetWitness NDR is built for organizations that need depth without sacrificing speed.
Measuring the Impact
The value of network detection response isn’t just in detection, but in mean time to respond (MTTR) reduction.
With NetWitness, that reduction is even more significant because:
- Analysts don’t waste hours pivoting between tools.
- The investigation context is right there in one interface.
- Response can be triggered immediately.
Bringing It All Together
If you think about it, how NDR works in NetWitness is like having a 24/7 security camera for your entire network one that not only records, but flags suspicious activity, rewinds footage for investigation, and locks the door before the intruder gets too far.
From the moment data hits the wire to the final incident resolution, NetWitness NDR covers:
- Complete network visibility.
- Real-time threat detection.
- Context-rich correlation.
- Prioritized alerts.
- Rapid, informed response.
Conclusion: One Platform, End-to-End Control
Threats don’t wait. Neither should your detection and response.
NetWitness NDR turns every packet into actionable intelligence, giving your SOC the context and speed needed to stop attacks before they spread. In a world where attackers hide in plain sight, the ability to see, understand, and act in real time isn’t just a nice-to-have it’s the difference between a minor incident and a business-crippling breach.
If your network could talk, NetWitness NDR would be the translator, the investigator, and the first responder all in one.
Frequently Asked Questions
1. How NDR work differently from other security tools?
NDR focuses on analyzing network traffic patterns, both encrypted and unencrypted, rather than endpoints or logs alone. It identifies threats that evade endpoint agents and SIEM correlation rules.
2. Does NetWitness NDR require sensors on every device?
No. It uses network taps or span ports to capture traffic across the environment, meaning it doesn’t need software agents installed on endpoints.
3. How quickly can NetWitness NDR detect a threat?
In many cases, it can flag suspicious activity in seconds, especially when integrated with existing SIEM and threat intelligence feeds.
4. Is NetWitness NDR suitable for cloud and hybrid environments?
Yes. It’s built for on-prem, cloud, and hybrid infrastructures, ensuring visibility across all network layers.
5. Can NetWitness NDR automate responses?
Yes. Through its orchestration capabilities, it can trigger containment actions, block traffic, and run custom playbooks with minimal analyst intervention.
Strengthen Network Visibility with NetWitness® Network Traffic Security Assessment
-Uncover hidden threats through deep packet inspection and analytics.
-Identify vulnerabilities and blind spots before they’re exploited.
-Enhance detection and response with NDR-driven intelligence.






