Security information and event management (SIEM) tools have become non-negotiable for modern enterprises. If you’re protecting any kind of digital infrastructure, you need visibility into what’s happening across your network, and that’s exactly what SIEM tools deliver.
But here’s the thing: not all SIEM solutions are created equal. The market is flooded with vendors promising the world, and choosing the wrong platform can leave you drowning in alerts, burning through budget, or missing threats that matter. Let’s break down what actually makes a SIEM tool worth your investment.
What Are SIEM Tools?
Before we dive into features, let’s get clear on what we’re talking about. SIEM tools are centralized platforms that collect, analyze, and correlate security data from across your entire IT environment. They pull logs from firewalls, servers, applications, endpoints, cloud services, and basically anything that generates security-relevant data.
The main purpose of SIEM is simple: detect threats faster than they can do damage. These security information and event management services aggregate millions of events, spot patterns that indicate malicious activity, and alert your team when something needs attention. Think of it as your organization’s security nervous system.
The Three Main Roles of a SIEM
Every security event information management system handles three critical jobs:
Data aggregation and normalization. Your SIEM collects logs from dozens or hundreds of different sources, translates them into a common format, and stores them in one place. Without this, your security team would be checking individual systems one by one, which is impossible at scale.
Real-time threat detection. The platform continuously analyzes incoming data against known threat patterns, behavioral baselines, and correlation rules. When it spots something suspicious, it generates an alert.
Compliance and forensics. SIEM tools maintain detailed audit trails that help you meet regulatory requirements and investigate incidents after they happen. You can reconstruct exactly what occurred during a breach, which is crucial for both remediation and legal purposes.
Core Features of SIEM Tools
When you’re evaluating the best SIEM tools for your organization, focus on these capabilities:
Feature 1: Understanding Log and Event Data
SIEM solutions collect and analyze log data from servers, applications, firewalls, and network devices, aggregating everything into a centralized view of your security posture. This centralization matters because it lets security teams access and analyze data from multiple sources in one place instead of wasting time manually correlating events across scattered systems. The real power comes from real-time event correlation—when SIEM tools connect events from different sources, they reveal patterns indicating potential threats, like when failed login attempts, reconnaissance scanning, and privilege escalation combine to expose a coordinated attack.
Feature 2: Identifying and Analyzing Security Threats
SIEM solutions use machine learning and advanced analytics to detect and prioritize potential security incidents, helping organizations focus on threats that actually matter. Automation plays a big role here—when genuine threats are detected, SIEM tools can immediately block malicious IPs, isolate compromised endpoints, disable user accounts, or trigger predefined playbooks without waiting for human intervention. SIEM Integration with threat intelligence feeds adds context to raw alerts, telling you whether a detected IP address is associated with malware command-and-control servers, phishing campaigns, or nation-state actors so analysts can quickly prioritize genuine threats.
Feature 3: Ensuring Regulatory Compliance
SIEM solutions help organizations meet regulatory requirements like GDPR, HIPAA, and PCI DSS through audit trails and reporting features that demonstrate due diligence. These tools track and document security-related activities automatically, maintaining detailed records of all security-relevant events so auditors can see evidence that you’re actively monitoring for threats, responding appropriately to incidents, and maintaining proper access controls. Customizable compliance rule sets let organizations tailor their approach to specific requirements—healthcare needs HIPAA, retailers need PCI DSS, and companies handling European data need GDPR—with pre-built templates that adapt as regulatory landscapes evolve.
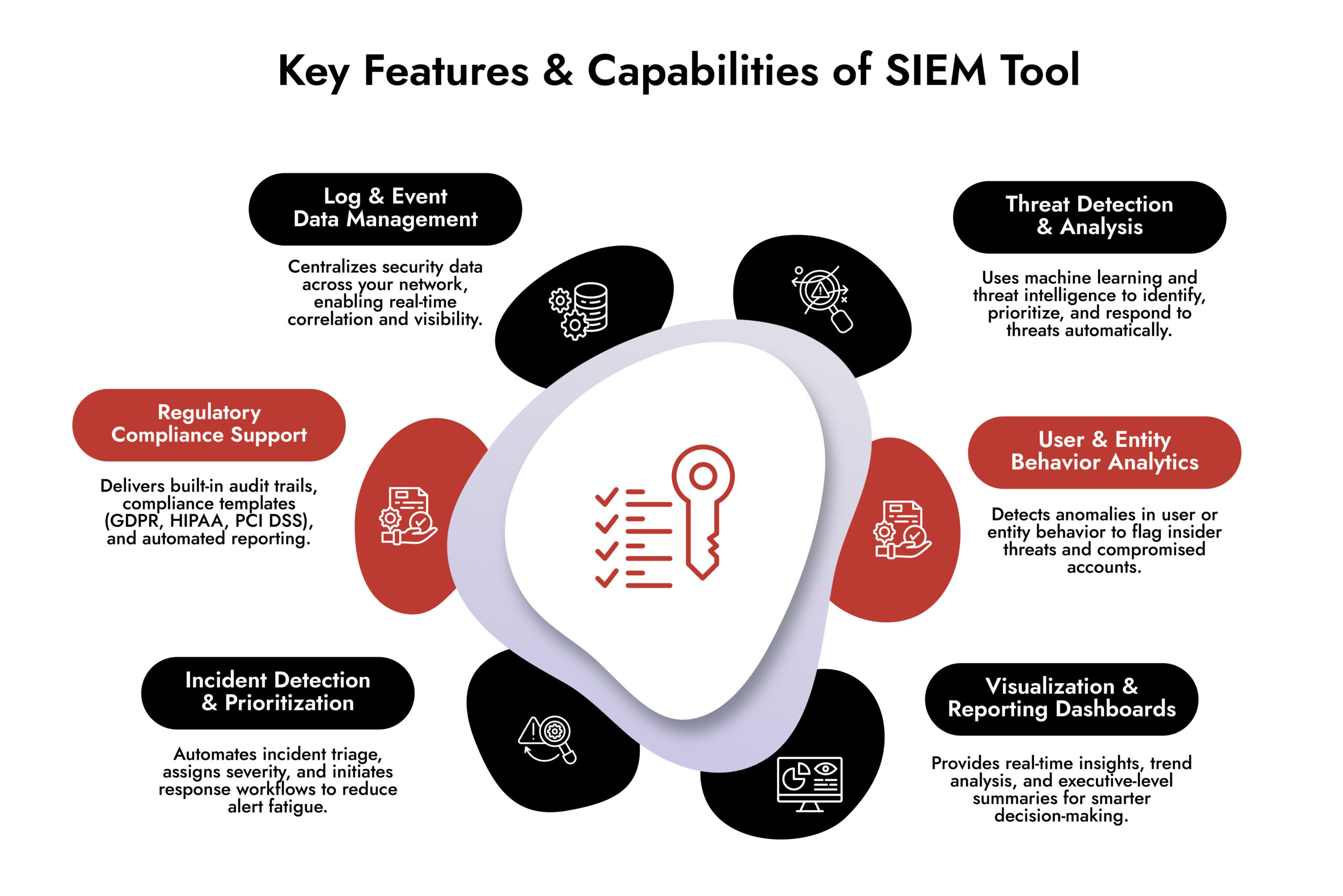
Feature 4: Monitoring User and Entity Behavior
SIEM solutions monitor user and entity behavior to catch anomalous activities that might indicate threats, including insider threats and unauthorized access attempts. Using machine learning and behavioral analytics, these tools establish baseline behavior for users and entities, then flag deviations—like when an employee who normally works 9-to-5 suddenly logs in at 2 AM from another country, or when a service account that usually queries the database starts exfiltrating large volumes of data. User and Entity Behavior Analytics (UEBA) continuously refines its understanding of normal behavior, getting better at distinguishing between legitimate unusual activities and genuine security threats while reducing false positives.
Feature 5: Incident Detection and Prioritization
SIEM solutions provide advanced capabilities for incident detection and prioritization when security teams are drowning in alerts—the average SOC receives thousands daily, but only a small percentage represent genuine threats. Automated incident response workflows enrich alerts with context, assign tickets based on severity, initiate containment actions, and begin forensic data collection without human intervention, ensuring consistent and rapid response regardless of when incidents occur. Integration with ticketing and remediation systems creates a complete incident response ecosystem where tickets are automatically generated with all relevant details, letting response teams track incidents through resolution and maintain complete records for compliance.
Feature 6: Visualization and Reporting
SIEM solutions offer customizable dashboards that present key metrics and KPIs so security teams can quickly assess their security operations and identify areas of concern. Real-time dashboards show what’s happening now—current alerts, ongoing incidents, system health—while historical reporting enables trend analysis to identify recurring issues and measure improvement over time. Role-based access control ensures different stakeholders get appropriate views: security analysts see detailed forensic data, SOC managers get operational metrics like mean time to detect and respond, and executives receive high-level risk summaries and compliance status.
Choose the Right SIEM with Confidence

Key Questions to Ask When Evaluating SIEM Vendors
When you’re shopping around, skip the marketing fluff and dig into specifics:
- What’s your average time from data ingestion to alert generation?
- How many native integrations do you support, and what’s the process for custom connectors?
- What’s your data retention capability, and how does that affect pricing?
- How do you handle software updates without disrupting SIEM monitoring?
- What level of support comes standard, and what costs extra?
- Can you provide customer references in my industry?
The Bottom Line
Choosing among SIEM tools isn’t just about checking feature boxes. You need a platform that fits your team’s skill level, integrates with your existing stack, scales with your growth, and actually reduces risk without creating operational nightmares.
The best SIEM tools make your security team more effective, not just busier. They surface real threats quickly, reduce alert fatigue, and provide the evidence you need for compliance and forensics. Everything else is noise.
Start by understanding your specific requirements: data volume, compliance mandates, team size, and budget constraints. Then evaluate solutions based on the capabilities we’ve covered here. The right security information and event management for enterprises system becomes the foundation of your entire security operation.
Frequently Asked Questions
1. What are SIEM tools?
SIEM tools are security platforms that collect, analyze, and correlate log data from across your IT environment to detect threats, investigate incidents, and support compliance requirements.
2. What are the core features of a SIEM tool?
Core features include log aggregation and normalization, real-time threat detection, correlation engines, alerting mechanisms, compliance reporting, forensic investigation capabilities, and integration with other security tools.
3. What are the three main roles of a SIEM?
The three main roles are: collecting and normalizing security data from multiple sources, detecting threats through real-time analysis and correlation, and supporting compliance through audit trails and reporting.
4. What is the main purpose of SIEM?
The main purpose is to detect security threats faster by providing centralized visibility into all security events across an organization’s IT infrastructure, enabling rapid response before threats cause significant damage.
Elevate Threat Detection and Response with NetWitness® SIEM
-Correlate data across users, logs, and network for unified visibility.
-Detect advanced threats with AI-driven analytics and behavioral insights.
-Accelerate investigations using automated enrichment and guided workflows.





