How are SASE vendors shaping the future of network security?
SASE vendors are redefining network security by delivering cloud-native platforms that unify networking and security services. By combining zero-trust security, secure connectivity, and threat protection into a single framework, SASE enables scalable, consistent network security solutions for cloud-first and remote environments.
The future of the network security as explored by the major vendors of SASE is not just about the implementation of a new framework. It is about knowing the way network protection is changing. Organizations must advance to adapt to the distributed, cloud first, mobile workforce, or the future of network security is determined by that ability. This change is being forefronted by providers of SASE, which is providing integrated solutions that integrate networking and security to form a single cloud-native system.
The scale of this shift is hard to ignore. Around 65% of organizations have already adopted SASE or plan to adopt it, underscoring how quickly traditional network security models are being replaced. Network security, data security or user access has never been as crucial as it is now. Separate traditional models of the perimeter are incapable of keeping up with the adoption of clouds, remote work and the proliferation of mobile devices. That is where Secure Access Service Edge (SASE) comes in as a paradigmatic model.
SASE vendors are a change in structure to a cloud-native strategy, where networking and security are combined into a single framework. Compared to routing all traffic to a centralized data center, SASE implements security and networking at the edge, which is further to users, devices, and applications.
In essence, SASE is a zero trust attitude. All connections, devices, and user identities are assumed to be untrusted. Below, we will discuss SASE architecture, why SASE vendors are the best, as well as deconstructing why this strategy defines the future of network security.
The Rise of Remote Work
Remote work has become a standard operating model, offering flexibility but stretching traditional security boundaries beyond their limits.
Why Traditional Network Boundaries No Longer Apply
Before we get started, there are a few abbreviations that we’re going to go over to ensure full understanding.
Dissolving the Perimeter:
The office perimeter used to be the main layer of defense. That perimeter no longer exists. Employees now access corporate data from personal devices and unsecured networks, creating new vulnerabilities.
Device Proliferation:
Remote and hybrid workforces rely heavily on unmanaged devices. Securing these devices, especially those accessing sensitive data, is a major challenge.
Network Complexity:
Instead of traffic flowing through a central data center, users now connect directly to cloud services. This shift demands a distributed, intelligent model that includes network traffic analysis for visibility and control.
Data Exposure Risks:
Unsecured channels, shadow IT, and misconfiguration increase the risk of data leaks and compliance breaches.
Rising Insider Threats:
Reduced oversight in remote setups can make insider risks harder to detect.
New Authentication Demands:
Modern identity access frameworks must authenticate users securely, from anywhere, on any device.
Scalability and Performance:
Legacy systems weren’t designed to handle millions of remote connections simultaneously.
SASE steps here, offering a cloud-native structure that secures identities, devices, and connections at scale.
Key Components of SASE Architecture
SASE architecture is composed of several key components that collectively work to enhance both security and network performance. These components bring together various security and networking functionalities into a unified framework, providing a holistic approach to safeguarding digital resources and enabling efficient access for users.
1. Cloud-Native Security Services:
These include next-gen firewalls, antivirus, anti-malware, and intrusion prevention – all delivered via the cloud. This ensures consistent protection across users and devices while enabling real-time updates and shared threat intelligence.
2. Software-Defined Wide Area Networking (SD-WAN):
SD-WAN optimizes wide-area network performance by routing traffic intelligently. It ensures reliability and low latency, even for remote users accessing cloud apps. Many organizations look for the best software-defined wide area network for unified SASE to combine performance with security.
3. Zero Trust Network Access (ZTNA):
ZTNA applies a “never trust, always verify” model that authenticates and authorizes every connection before granting access, minimizing risk and preventing lateral movement.
4. Data Loss Prevention (DLP):
DLP protects sensitive data from unauthorized access or leaks. It ensures data privacy and compliance, especially in remote and hybrid setups.
5. Firewall as a Service (FWaaS):
FWaaS enforces policies, filters traffic, and blocks threats – all from the cloud. It eliminates on-premises hardware and simplifies policy management.
6. Secure Web Gateways (SWG):
SWGs safeguard users against malware, phishing, and data exfiltration while maintaining uniform web access policies.
Together, these features define the best SASE platform – one that integrates SD-WAN, DLP, ZTNA, and FWaaS to ensure both performance and security at a scale.
Understanding the Role of SASE Vendors
SASE vendors deliver the cloud-native platforms that make all of this possible. They integrate networking and security functions into a single, scalable system. Leading vendors offer SD-WAN, zero trust, cybersecurity orchestration, and advanced threat protection under one umbrella.The best SASE intrusion prevention solutions detect threats before they enter the network, making them essential for cloud-first environments.
When evaluating SASE vendors, organizations should consider:
- Cloud-based security services (firewalls, intrusion prevention, DLP, SWG).
- Integration capabilities with cloud providers.
- Scalability for growing networks.
- Threat intelligence and analytics.
- Vendor reputation and innovation.
These providers play a key role in defining the future of network security by enabling businesses to protect assets wherever users connect from.
Proactive Network Threat Detection with NetWitness® NDR
-Spot threats fast with AI-driven analytics.
-See everything across your network and cloud traffic.
-Investigate efficiently with built-in forensic tools.
-Adapt and scale to meet growing security needs.

Why SASE Matters for Modern Security
SASE isn’t just a buzzword; it’s the foundation for the future of network security system . SASE vendors provide businesses with an opportunity to work safely within the distributed environments by combining networking with security in the cloud. They do away with several point solutions and develop a flexible and global-scale framework.
SASE providers provide quality connectivity, effective administration, and constant security against the diverse threats with cloud-native security solutions, data loss prevention, and SD-WAN. When considering the most appropriate intrusion prevention to use in SASE networks, companies should consider those that scan encrypted traffic, implement the principle of zero trust, and enhance telemetry. Finally, the choice of the most effective intrusion prevention system to use in unified SASE is to ensure that threats are eliminated at the edge, rather than after they target the critical assets. 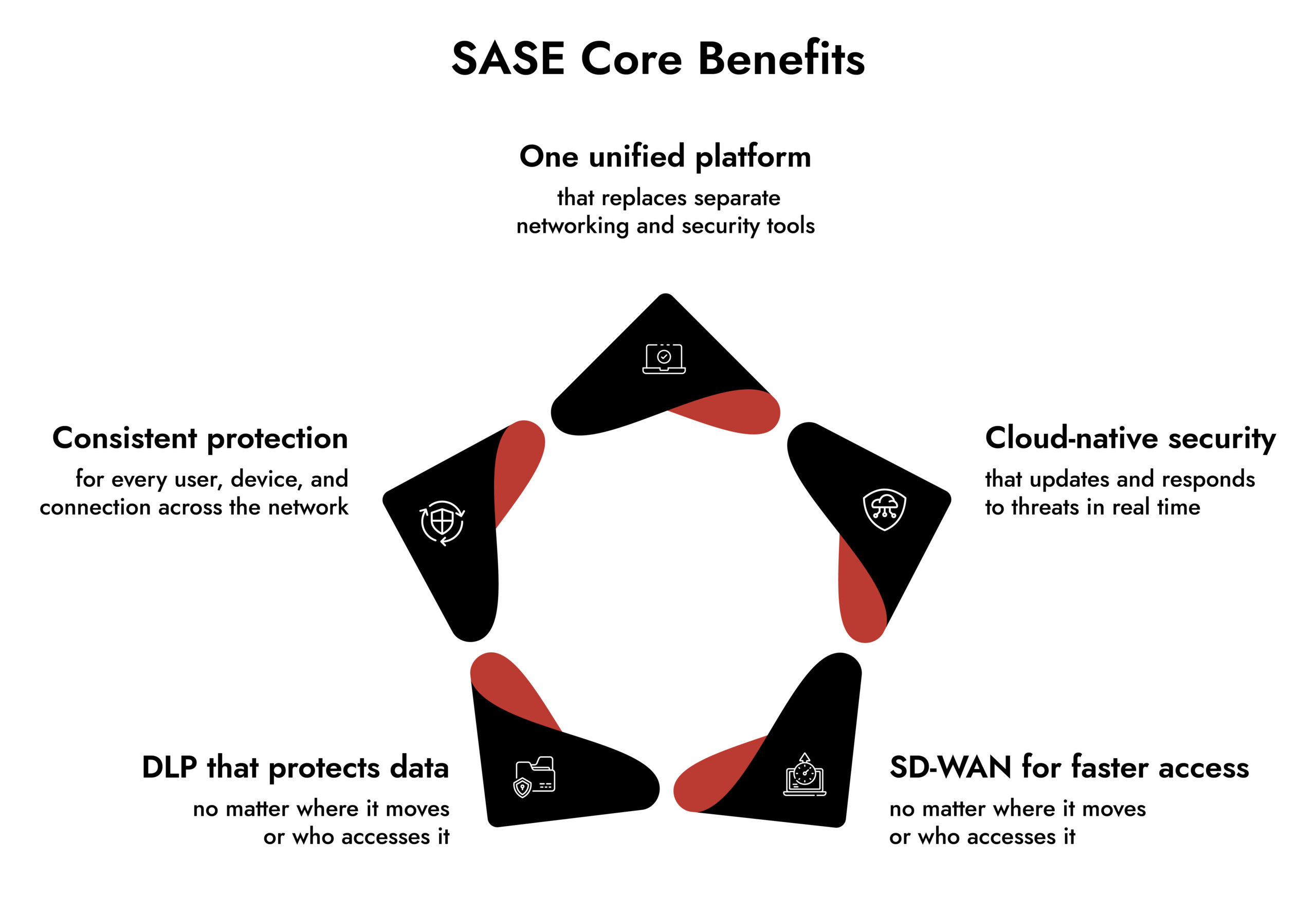
NetWitness and SASE Vendors
NetWitness bridges a critical visibility gap that can emerge in SASE environments. When security operations centers (SOCs) rely heavily on cloud-based systems, network visibility can be limited.
NetWitness SASE handles this issue by adding packet integrations with SASE vendors like Palo Alto Networks, Symantec by Broadcom, and Netskope to provide full visibility even in cloud-first and encrypted settings. This innovation reflects the NetWitness dedication to keeping up with the future of network security system and making organizations not lose visibility or control by modernizing.
Contact NetWitness today to learn more about how integrations with SASE vendors can strengthen your visibility, performance, and compliance across the entire digital infrastructure.
Conclusion
The future of network security is being shaped by how effectively organizations adapt to cloud-first, distributed environments. As traditional perimeters fade, SASE network security offers a practical way forward by unifying networking and security into a single, scalable model. This shift is not about adding another layer of tools. It is about rethinking how network security in networking is delivered and enforced.
The best SASE vendors are enabling this transition by embedding zero-trust security directly into SASE networks, ensuring access decisions are identity-driven and continuously verified. By replacing fragmented point solutions with integrated network security systems, SASE providers help organizations reduce complexity while improving visibility and control across users, devices, and applications.
For enterprises and network security providers for small business alike, SASE delivers consistent network security and cyber security without sacrificing performance or flexibility. As threats evolve and networks continue to decentralize, SASE is becoming the foundation for modern network security solutions. Organizations that align with the best SASE providers today will be better positioned to secure their networks tomorrow.
Frequently Asked Questions
1. What is SASE in network security?
SASE in network security is a cloud-based model that combines networking and network security solutions into a single platform, protecting users, devices, and applications across distributed environments.
2. Why is SASE important for the future of network security?
SASE matters because modern network security in networking must support cloud, remote work, and scale. It delivers consistent network security and cyber security without relying on legacy perimeters.
3. How is Zero Trust integrated within SASE architectures?
Zero-trust security is built into SASE networks by continuously verifying identity, device posture, and access context before allowing connections.
4. How does SASE differ from traditional network security?
Traditional network security depends on centralized hardware. SASE replaces this with cloud-delivered network security systems enforced at the edge.
5. What are key capabilities offered by SASE vendors?
The best SASE vendors provide secure connectivity, identity-based access, threat protection, and centralized policy control through unified network security solutions.
Integrating SASE with NetWitness: Achieve Complete Visibility and Control
Discover how integrating Secure Access Service Edge (SASE) tools with NetWitness empowers your SOC with unified detection, contextual awareness, and automated response across cloud and hybrid environments.






