Deep Packet Inspection (DPI) Explained
Deep packet inspection is a type of network examination that scrutinizes the entire contents of packets while they move through the network, rather than solely focusing on headers or flow metadata. Through the integration of packet capture, protocol-aware examination, and analysis of PCAP files, DPI allows security teams to identify harmful activities, probe incidents, and recreate sessions with comprehensive network context. Organizations need both when compliance requires long-term log retention and security teams must proactively detect and respond to advanced, multi-stage attacks.
Introduction
Network security rarely fails because teams lack tools. It fails because they lack visibility at the moment it matters.
The majority of contemporary attacks do not reveal their presence. They merge with genuine network traffic, employ reliable protocols, and operate stealthily until identification is challenging or too late. This is the area where deep packet inspection remains essential. It’s more than merely a trendy term. It is an effective method to observe what is genuinely traveling through the network.
This blog provides a practical perspective on deep packet inspection, its functionality in actual settings, and the reasons platforms such as NetWitness still depend on comprehensive packet capture and network inspection to facilitate detection, investigation, and response.
What Is Deep Packet Inspection?
At its core, deep packet inspection (DPI) is the ability to analyze packet contents beyond headers and flow data. Instead of stopping at source, destination, and port, DPI examines payloads, protocol behavior, and session context.
That distinction matters.
Traditional inspection methods can tell you that traffic exists. Deep packet inspection monitoring tells you what that traffic is doing and whether it makes sense in the context of your environment.
A practical example:
An outgoing HTTPS connection on port 443 appears standard on the surface. DPI indicates that the session employs improperly formatted TLS handshakes, abnormal certificate chains, and varying packet sizes. Those indications do not ensure harmful intent, but they are sufficient to warrant further examination. By utilizing stored PCAP files, an analyst can recreate the session and ascertain whether it indicates command-and-control behavior or a misconfigured application.
This is where DPI shifts from theory to operational value.
Why Packet Capture is Non-Negotiable for DPI
Not all deep packet inspection tools are built the same way. The biggest architectural difference is whether inspection is backed by full packet capture or limited metadata extraction.
Metadata answers high-level questions:
- Who communicated with whom
- When the session occurred
- How much data moved
But investigations often require more.
With full packet capture, teams can:
- Reconstruct sessions byte by byte
- Validate exploit payloads
- Confirm data exfiltration attempts
- Support incident reports with evidence, not assumptions
NetWitness retains packets by default, allowing analysts to pivot from detection to validation using the same dataset. This ability to replay sessions from PCAP files becomes critical during incident response, regulatory review, or internal investigations.
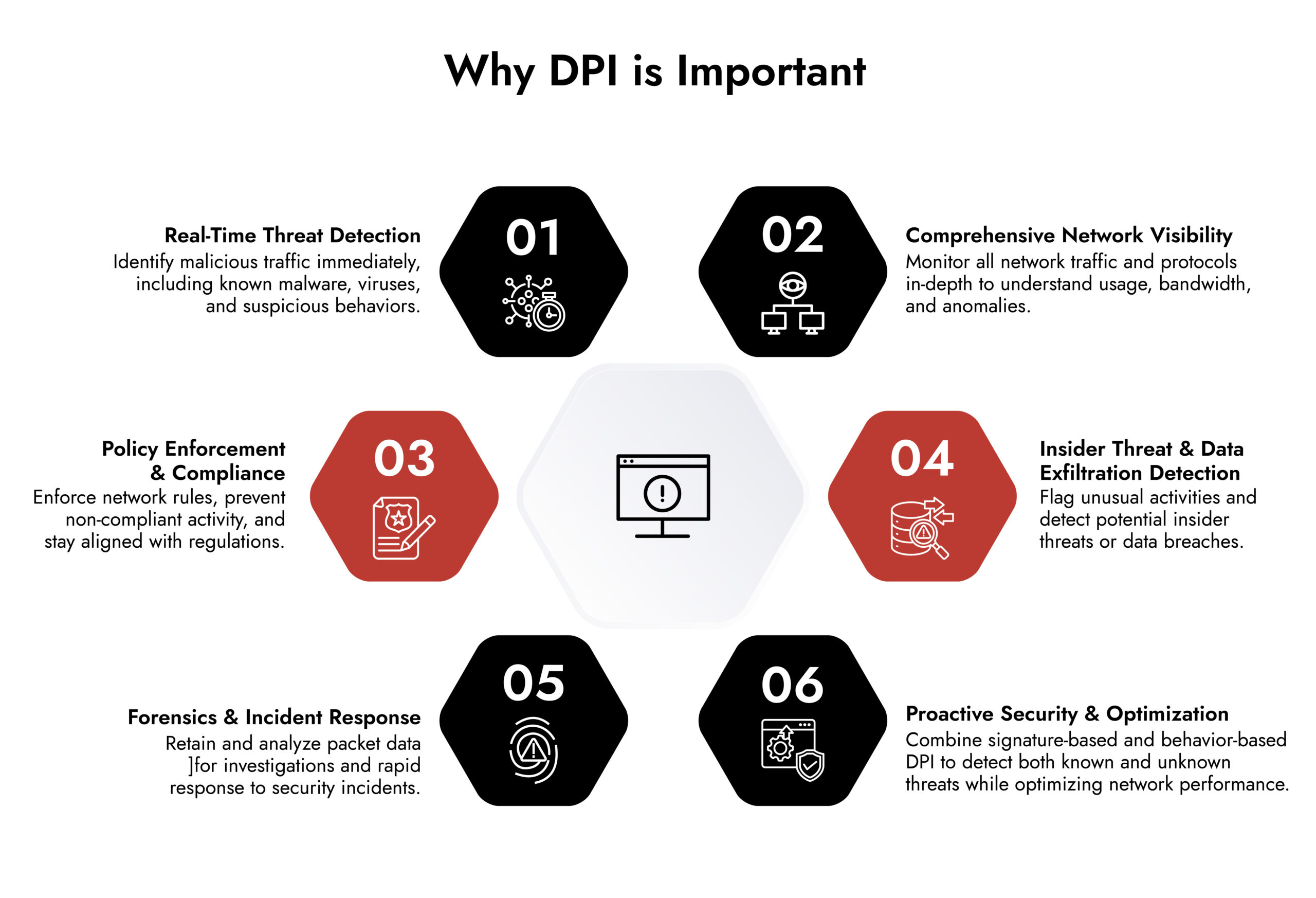
Deep Packet Inspection in NetWitness
NetWitness uses deep packet inspection monitoring as a foundational capability rather than an isolated feature.
The platform combines:
- Protocol-aware inspection across hundreds of protocols
- Signature-based and behavior-based analysis
- Full packet retention for retrospective investigation
Signature-Based Deep Packet Inspection
Signature-based DPI compares packet contents against known threat patterns. This method is effective for identifying established malware, exploit kits, and previously observed attack infrastructure.
It is precise, fast, and limited by design.
Signatures work best when threats are already understood. They struggle when attackers change tooling or abuse legitimate services.
Behavior-Based Deep Packet Inspection
Behavior-based DPI focuses on how network traffic behaves over time.
Examples include:
- Unusual protocol usage on standard ports
- Unexpected session persistence
- Traffic patterns that diverge from historical baselines
This approach is particularly effective for detecting unknown threats, including lateral movement and stealthy data staging activity. When combined with packet capture, behavior-based inspection provides both detection signals and investigative depth.
Configuring Deep Packet Inspection in NetWitness
There’s a persistent belief that deep packet inspection monitoring inevitably degrades performance. In reality, performance impact depends on how inspection is applied.
NetWitness allows teams to:
- Prioritize inspection for high-risk traffic paths
- Focus on specific protocols or segments
- Tune inspection depth based on operational needs
This selective approach ensures network inspection remains targeted. DPI doesn’t need to inspect everything equally. It needs to inspect the right traffic at the right time.
False positives are addressed the same way experienced SOC teams handle any detection logic: tuning, validation, and iteration. DPI is no different.
Real-World Use Cases for Deep Packet Inspection
Detection of Malware and Analysis of Command-and-Control
Numerous contemporary malware types utilize encrypted channels to avoid basic examinations. DPI identifies irregularities in session activities, whereas packet capture enables analysts to verify if questionable traffic indicates beaconing or legitimate application activity.
Insider Threat and Data Leakage
When substantial amounts of data flow unexpectedly, deep packet inspection assists in determining how and where that movement took place. Replaying sessions from PCAP files offers insights that flow data by itself cannot provide.
Network Forensics and Incident Reconstruction
During investigations, time matters. DPI-backed network inspection allows teams to answer questions quickly:
- What data was accessed?
- How was it transmitted?
- Was the activity successful?
NetWitness supports session reconstruction by default, reducing reliance on assumptions during high-pressure incidents.
Proactive Network Threat Detection with NetWitness® NDR
-Spot threats fast with AI-driven analytics.
-See everything across your network and cloud traffic.
-Investigate efficiently with built-in forensic tools.
-Adapt and scale to meet growing security needs.

Why DPI Still Matters According to Industry Data
Industry research continues to reinforce the role of packet-level visibility:
These findings point to a simple conclusion: without packet-level visibility, investigations stall.
How NetWitness Extends DPI Across the SOC
NetWitness does not treat deep packet inspection as a standalone capability.
- NetWitness Network provides packet capture and protocol-aware inspection.
- NetWitness UEBA applies behavioral analytics to DPI-enriched data.
- NetWitness Endpoint correlates host-level activity with observed network traffic.
- NetWitness Orchestrator uses DPI context to automate response workflows.
This integration allows analysts to move laterally across telemetry sources without losing context.
Best Practices for Effective Deep Packet Inspection
Experienced teams approach DPI pragmatically:
- Keep inspection rules current and relevant
- Tune based on observed traffic, not assumptions
- Retain PCAP files where forensic depth is required
- Align inspection policies with compliance obligations
DPI works best when it is treated as an investigative capability, not just a detection checkbox.
Final Thoughts
Deep packet inspection is not new. What has changed is how attackers operate and how much visibility teams need to respond effectively.
When combined with full packet capture, DPI provides the context required to move from alerts to answers. NetWitness builds on this foundation by preserving packets, enriching metadata at capture time, and enabling analysts to see exactly what happened on the wire.
That level of visibility remains difficult to replace and easy to underestimate until it’s gone.
Frequently Asked Questions
1. What is packet inspection?
Packet inspection is the process of examining network packet headers and data to identify traffic type, source, and potential threats.
2. What is deep packet inspection?
Deep packet inspection (DPI) analyzes the full content of network packets to detect malicious activity, enforce policies, and monitor network usage in real time.
3. What is the difference between DPI and IPS?
DPI analyzes packet contents to detect threats, while IPS (Intrusion Prevention System) uses this analysis to actively block or prevent malicious traffic.
4. What is DPI and SPI?
DPI (Deep Packet Inspection) examines the full packet data for advanced analysis, while SPI (Stateful Packet Inspection) focuses on monitoring connection states and packet headers for basic filtering.
Threat Intelligence: The Key to Higher Security Operation Performance
Unlock the full potential of your Security Operations Center with deeper visibility, faster detection, and smarter response. This whitepaper explores how modern threat intelligence elevates SOC maturity and helps organizations stay ahead of evolving adversaries.






