Key Takeaways
- Contemporary cyber assaults advance through identifiable phases, yet inadequate threat detection enables attackers to traverse laterally and remain unnoticed.
- The most perilous and extended stage of the threat lifecycle occurs post-compromise, rather than during initial access.
- Limited visibility throughout the network, endpoint, identity, and cloud levels boosts the effectiveness of attackers
- Effective threat detection depends on context, not alert volume.
- Security teams that align detection to attacker behavior shorten dwell time and limit impact.
Introduction
Threat detection fails quietly. Not because teams lack tools, but because modern attacks rarely announce themselves. They blend into normal operations, move slowly, and exploit visibility gaps that most enterprises still underestimate.
Here is the uncomfortable truth. Most breaches don’t start with a dramatic exploit. They start with something small that no one flags as dangerous. A missed alert. An uninspected connection. An identity that behaves almost normally. When threat detection doesn’t fire early, attackers gain time. And time is what turns an intrusion into a business impact.
This article analyzes the progression of attacks when threat detection flaws are present, why they can go unnoticed for extended periods, and the implications for cybersecurity risk evaluation in actual organizational settings.
The Threat Lifecycle Explained
The threat lifecycle describes how a cyberattack unfolds from entry to impact. It isn’t theoretical. Incident response data from 2024 shows attackers still follow consistent behavioral patterns, even as tools evolve.
Strong threat detection interrupts this lifecycle early. Weak detection lets it run its course.
The stages of a cyberattack typically include:
- Initial access
- Establishing persistence
- Privilege escalation
- Lateral movement
- Command and control
- Data exfiltration or disruption
Each stage creates detection opportunities. Miss a few, and attackers operate freely.
Stage 1: Initial Access Rarely Triggers Alarms
Initial access usually looks boring. That’s the problem.
Attackers rely on phishing, credential reuse, exposed services, or trusted third parties. In 2024, Verizon DBIR reported that stolen credentials remain the top entry vector in confirmed breaches.
At this point, threat detection struggles because activity appears legitimate.
Common entry methods include:
- Valid user credentials with normal login patterns
- MFA fatigue attacks that succeed once
- VPN or SaaS access from previously unseen locations
- Compromised vendor accounts
Most cybersecurity solutions still focus on malware signatures here. That’s insufficient. Cyber threat detection must evaluate behavior, not just payloads.
Stage 2: Persistence Hides in Plain Sight
Persistence keeps attackers alive after access. This phase often lasts weeks.
Attackers register new OAuth apps, create scheduled tasks, modify startup scripts, or add cloud access keys. None of this looks malicious in isolation.
Without mature threat detection, persistence mechanisms remain invisible because:
- Logs exist but lack correlation
- Identity changes don’t trigger alerts
- Cloud control plane activity goes unanalyzed
This is where cybersecurity awareness inside security teams matters as much as tools. If analysts don’t expect persistence to look ordinary, they will miss it.

Stage 3: Privilege Escalation Exploits Assumptions
Privilege escalation does not always need exploits. Attackers frequently exploit misconfigurations, excessive access rights, or reused tokens.
This phase is successful when threat detection concentrates on exploits rather than modifications to entitlements.
Examples include:
- Service accounts with broad access
- Role escalation in cloud IAM
- Abuse of legacy admin groups
Cybersecurity risk assessment often documents these issues, but detection rarely enforces them continuously.
Stage 4: Lateral Movement is Quiet, Not Noisy
Lateral movement feels like the phase security teams should catch. Yet it’s one of the most missed.
Why? Because attackers use built-in tools – SMB, RDP, SSH, API calls. No malware is required.
Effective threat detection here requires:
- Session context, not just flow logs
- Correlation across hosts and identities
Cyber threat detection services that rely only on endpoints miss east-west activity entirely.
Stage 5: Command and Control Blends with Business Traffic
Modern command-and-control traffic doesn’t beacon loudly. It uses HTTPS, DNS over HTTPS, cloud platforms, and SaaS APIs.
Without deep inspection and behavioral baselining, threat detection can’t distinguish malicious control traffic from legitimate business use.
Encryption without inspection equals blindness.
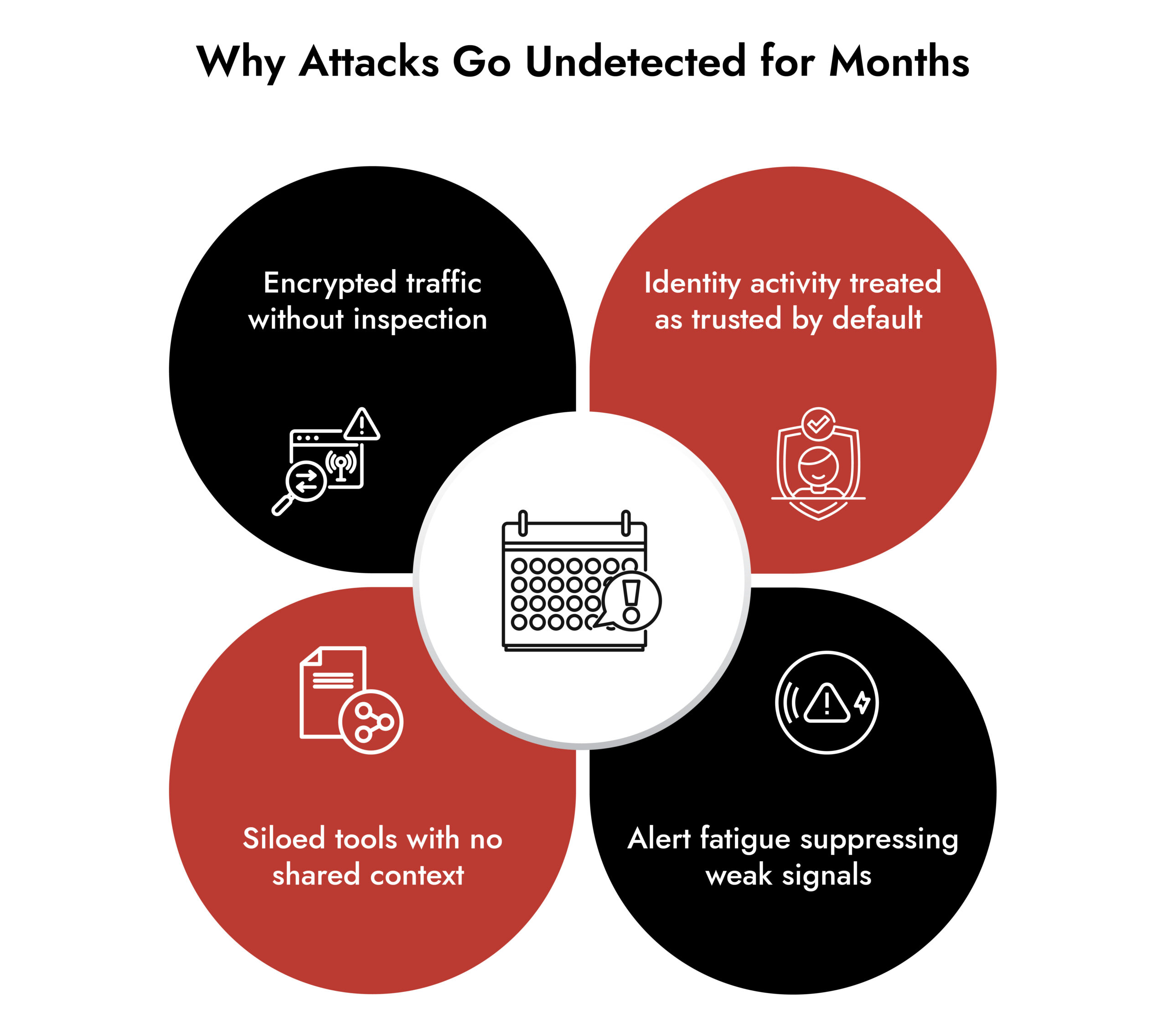
Stage 6: Impact Happens Last, Not First
Data theft, ransomware, and operational disruption come at the end. By then, attackers understand the environment better than defenders.
At this point, threat detection turns into incident response.
This is why cyber threat detection services must focus on early lifecycle stages, not just impact indicators.
360° Cybersecurity with NetWitness Platform
– Unrivaled visibility into your organization’s data
– Advanced behavioral analytics and threat intelligence
– Threat detections and response actionable with the most complete toolset

Why Traditional Threat Detection Models Fail
Many organizations still treat threat detection as an alert generation. That model no longer works.
The failure points are consistent:
- Detection rules tied to known malware
- Overreliance on endpoint-only telemetry
- Minimal visibility into cloud and identity layers
- No mapping between alerts and attack stages
Cybersecurity solutions must detect behaviors across the entire lifecycle, not isolated events.
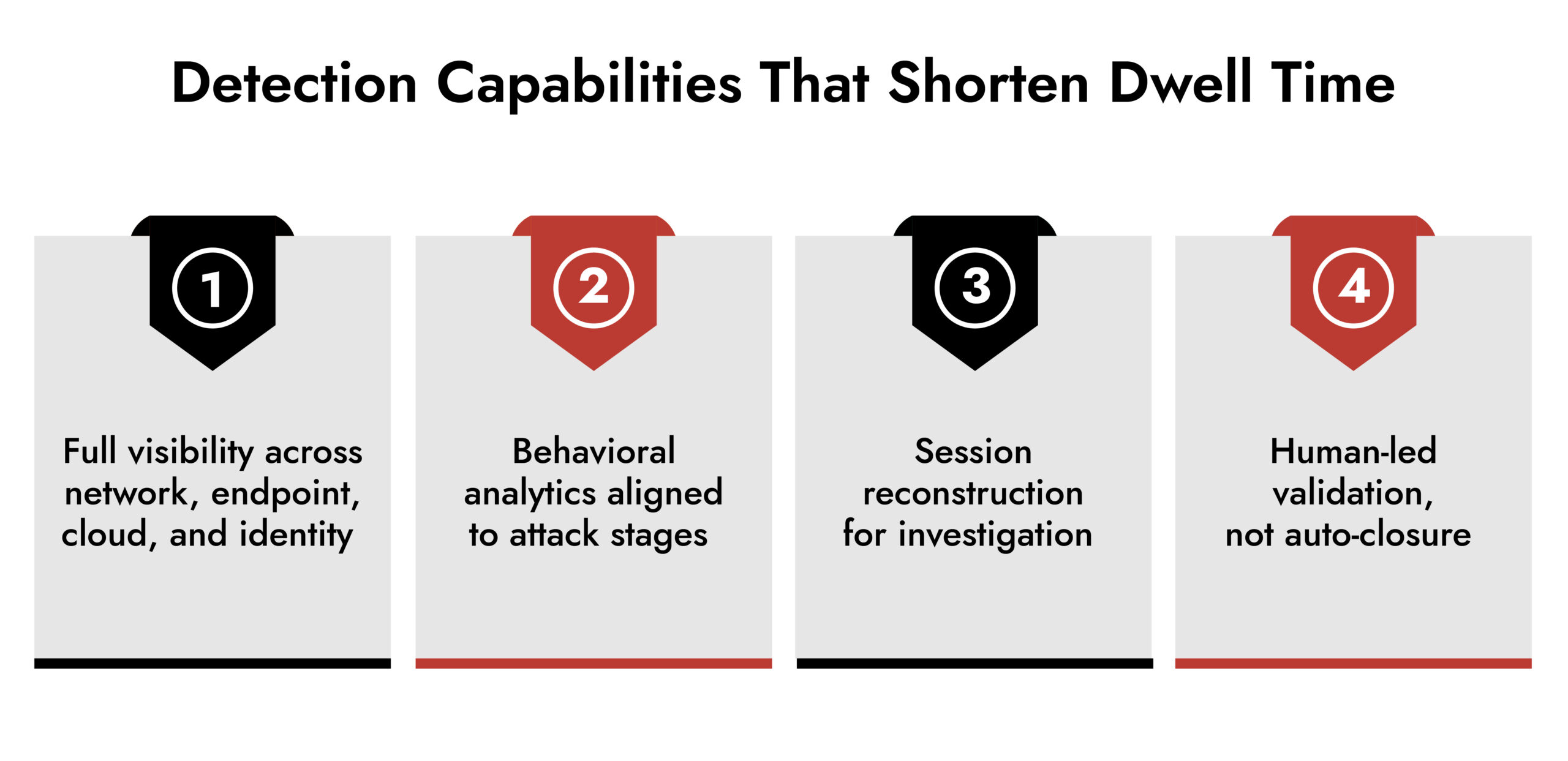 Where NetWitness Fits in the Threat Lifecycle
Where NetWitness Fits in the Threat Lifecycle
NetWitness Threat Detection and Response focus on visibility and context across the full attack lifecycle.
Rather than treating detection as isolated alerts, the platform aligns telemetry to attacker behavior. Network traffic, endpoint activity, logs, and cloud signals feed into a unified view.
This approach supports threat detection where it matters most:
- Early-stage credential abuse
- Lateral movement across network segments
- Encrypted command-and-control activity
- Persistent attacker behavior over time
For organizations evaluating cybersecurity solutions, this lifecycle-based model aligns detection to how attacks actually progress, not how tools prefer to alert.
What This Means for Cybersecurity Leaders
Here’s the reality. You don’t lose to attackers because they’re invisible. You lose because detection happens too late.
Improving threat detection isn’t about adding another tool. It’s about aligning detection to attacker behavior and validating it continuously through realistic cyberattack scenarios.
Strong cybersecurity awareness inside security teams matters as much as technology. So does an honest cybersecurity risk assessment that accounts for visibility gaps, not just controls paper.
Conclusion: Detect Earlier or Respond Forever
Attackers don’t need sophistication. They need time.
Every gap in threat detection and response gives them more of it. When detection aligns to the full threat lifecycle, attacks collapse early. When it doesn’t, security teams spend their time responding instead of preventing them from doing so.
The goal isn’t zero alerts. It’s fewer surprises.
Frequently Asked Questions
1. What is the threat lifecycle in cybersecurity?
The threat lifecycle outlines the phases of a cyberattack, ranging from initial entry to consequences. Effective threat detection observes behavior throughout all phases, not solely during malware execution.
2. How do attackers maintain persistence without detection?
Intruders exploit genuine system functionalities such as scheduled tasks, OAuth applications, and cloud access tokens. Ineffective threat detection does not link these activities to malicious intent.
3. Why do many attacks go undetected for long periods?
Many attacks depend on legitimate credentials and secure traffic. Without behavioral threat detection and comprehensive visibility, actions seem typical.
4. How does poor visibility accelerate attack progression?
Restricted visibility of the network, identity, or cloud hinders timely detection. This enables attackers to advance laterally and increase their privileges without detection.
5. What are the main stages of an undetected cyberattack?
First entry, sustainment, elevation of privileges, lateral navigation, command and governance, and ultimate effect. Every phase provides chances for threat detection if visibility is present.
6. How do threat detection services reduce dwell time?
Services for detecting threats that analyze behavior from various telemetry sources recognize attacker patterns quickly, reducing dwell time and minimizing damage
Rolling the Dice: Ransomware in the Gaming Industry
Discover how ransomware attacks hit gaming companies, how attackers moved laterally, and why network visibility is key. Learn real-world lessons and strategies to detect, respond, and protect critical systems.






