Why is automated threat response important in cybersecurity?
Automated threat response is important because modern cyber attacks operate at machine speed, leaving little time for manual intervention. Security automation enables faster containment, reduces attacker dwell time, and helps organizations respond effectively to evolving cybersecurity threats. Organizations need both when compliance requires long-term log retention and security teams must proactively detect and respond to advanced, multi-stage attacks.
Introduction
Most security teams are preparing for the wrong enemy.
They’re still planning for attacks that wait, hesitate, and leave time for investigation. That world is gone. Today’s cyber attack doesn’t pause while an analyst opens a dashboard. It doesn’t care about shift schedules, alert queues, or ticket workflows. It executes at machine speed, adapts in real time, and escalates without permission.
The most dangerous threats in cybersecurity are no longer operated step by step by humans. They are autonomous systems designed to find weaknesses, exploit them instantly, and move laterally before anyone realizes something is wrong. By the time a human response begins, the damage is already in motion.
This is the uncomfortable truth many organizations avoid: manual threat response alone is structurally incapable of stopping modern attacks. Not because teams are unskilled. Not because tools are missing. But because humans cannot outpace software that is built to operate faster than thought.
Automated threat response is not a trend, an efficiency play, or a cost saver. It is a survival requirement in a threat landscape dominated by automation, scale, and speed.
Attackers have Shifted Gears
Here’s the thing: cyber threats used to be noisy. Early malware made a lot of noise because it didn’t try very hard to hide. Security teams could spot anomalies, investigate, and respond.
That’s not how things work today. Modern cybersecurity threats slip through defenses quietly:
- Attackers use machine-learning-driven tools.
- Malware adapts its behavior to avoid detection.
- Automated exploitation frameworks scan and assault targets around the clock.
These aren’t human hackers slowly poking around during business hours. These are autonomous processes engineered for speed and scale. They never sleep. They never get tired. They iterate faster than an analyst can click “investigate.”
In this landscape, manual threat response doesn’t just struggle—it’s fundamentally mismatched to the problem.
What are Autonomous Attacks?
Before we go deeper, let’s define this clearly.
Autonomous attacks are cyber threats that operate with minimal human intervention. These can include:
- Worms that propagate across networks on their own.
- Botnets that scan for vulnerabilities and exploit them automatically.
- AI-powered malware that alters execution paths to evade detection.
Autonomous attacks are not just faster than traditional attacks. They’re unpredictable. They don’t wait for an opportunity. They create opportunities.
They leverage automation against defenders in the same way businesses automate customer support or supply chains. That symmetry changes the playing field.
What stops an autonomous attack? Speed. The answer isn’t more logs or more alerts. It’s response that’s just as swift and adaptive.
Manual Threat Response Can’t Wait
In a typical security operation, a human analyst receives an alert, decides whether it’s legitimate, investigates context, determines impact, and then takes action. That’s a fine process when threats are infrequent and simple.
But with security threats multiplying, manual workflows hit three limits:
- Latency: Every extra minute between detection and response is a window attackers exploit.
- Scale: Humans can’t process thousands of alerts per hour at full fidelity.
- Complexity: Modern attacks involve multiple stages—reconnaissance, exploitation, lateral movement—which require speed beyond human reaction times.
Let’s put this in perspective. Attackers running scripts can scan thousands of IPs per second. A manual triage that takes minutes gives adversaries ample time to dig deeper, escalate privileges, and cover their tracks.
Automated Threat Response: What it is?
So what’s the alternative? Automated threat response.
This isn’t about firing off scripts blindly. It’s about integrating detection, decision making, and action into a feedback loop that happens in near real time.
The key components include:
Cyber Threat Detection
Cyber threat detection is the first step. It involves identifying anomalies, suspicious behavior, or confirmed indicators of compromise. Detection feeds intelligence into the response system.
At this stage, systems look for patterns that match known threats as well as behavioral deviations. These are the signals that trigger automated workflows.
Decision Logic
Once a threat is detected, response automation uses predefined decision logic to determine whether to act. This can range from moderate measures like quarantining a device to more aggressive containment actions across the network.
This decision logic can be:
- Rules-based (if X and Y, then do Z)
- Machine-learning driven (adaptive decisions based on historical outcomes)
- Hybrid models (human overrules with contextual input)
Action
This is where automation makes its biggest impact. Instead of waiting for a human, the system executes actions that can include:
- Isolating affected endpoints
- Blocking suspicious IP addresses
- Revoking credentials that show anomalous use
- Triggering deeper forensic scans
Good automated threat response is surgical. It aims to neutralize the threat while keeping the business running.
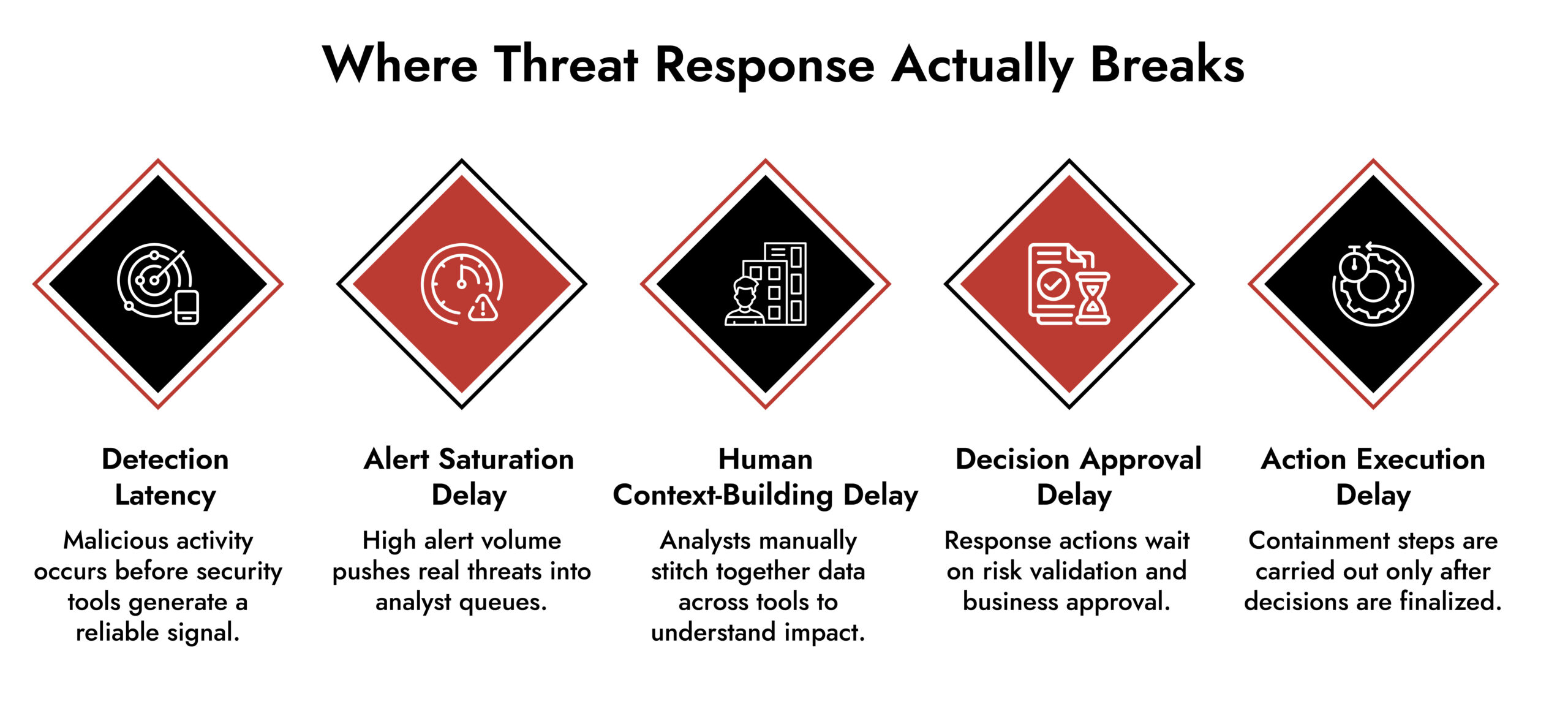
Why Automated Response is No Longer Optional?
Here’s the central point: as threats evolve, defenders must evolve faster. The traditional model assumed alerts lead to human action. It assumed context is slow and deliberate because that’s how humans think.
But that assumption no longer holds. Autonomous attacks operate on machine time. They move without delays. They leap across security boundaries in milliseconds.
In that world:
- Manual response is too slow.
- Reactive playbooks are too rigid.
- Siloed tools are too fragmented.
What’s needed is a system that can detect and respond continuously, with minimal human latency.
Rolling the Dice: Ransomware in the Gaming Industry
Discover how ransomware attacks hit gaming companies, how attackers moved laterally, and why network visibility is key. Learn real-world lessons and strategies to detect, respond, and protect critical systems.

How Automated Threat Response Works in Practice?
Let’s walk through an example.
Imagine a user’s credentials are compromised. A threat actor attempts to access internal resources from an unusual location.
Without automation:
- SIEM generates an alert.
- Analyst escalates to incident response.
- Action taken after investigation.
This can take hours—during which the attacker moves laterally.
With automated threat response:
- Detection engine flags an anomalous login attempt.
- Decision logic scores the event as high risk.
- The system automatically triggers a response to block access from that source.
- Endpoint isolation and MFA enforcement are enacted.
- Analysts are notified with full context for review.
The difference is not just speed. It’s containment before damage escalates.
That’s why security automation isn’t about replacing humans. It’s about giving them a fighting chance against threats that operate faster than humans can react.
Common Misconceptions
Let’s clear up a few misunderstandings I hear all the time.
Myth: Automation is only for big companies.
No. The need for speed transcends size. Smaller organizations often lack large security teams. Automation compensates for limited resources.
Myth: We can automate everything.
No system is perfect. Not every alert should trigger an immediate block. Smart automated response includes guardrails, escalation paths, and human oversight where appropriate.
Myth: Automation means we remove analysts.
This is backwards. Automation frees analysts to focus on high-value investigations instead of chasing every alert.
Threats That Benefit Most from Automated Response
Not all threats are created equal. Some will always need deep human analysis. But several categories benefit enormously from automated risk mitigation:
Fast-Moving Exploits
Zero-day exploits and rapid scanning operations sweep networks for weaknesses. Speed matters. Automated containment limits exposure.
Brute Force and Credential Stuffing
These attacks generate massive volumes of attempts over short periods. Automated detection and throttling dramatically reduce risk.
Lateral Movement
Once inside, adversaries try to pivot. Automated segmentation and isolation tools can disrupt these flows instantly.
Suspicious Behavior Patterns
Some threats show clear deviations from normal patterns. Automated systems can spot and act on these with near-zero latency.
In each case, manual approaches lag behind the threat timeline.
How to Build Effective Automated Response?
Security automation sounds good on paper. But success depends on thoughtful implementation.
Start with these principles:
1. Align Automation with Business Context
Automated actions must understand business priorities and business context. A response that shuts down an entire department’s access might stop a threat but also halt operations. Decide what’s acceptable and where stricter policies apply.
2. Integrate Across Tools
Automation only works if detection and response tools speak to each other. That means integrating SIEM, EDR, network controls, identity systems, and cloud security into a unified workflow.
3. Define Clear Playbooks
Don’t wing automation. Design playbooks that outline how the system should respond to specific threats. These should be tested and refined regularly.
4. Include Analyst Oversight
Automation shouldn’t be a black box. Provide teams with visibility into decisions and outcomes so they can improve rules, understand behavior, and fine-tune responses.
5. Measure and Learn
Track how quickly threats are neutralized, how many false positives occur, and the impact on operations. This feedback loop improves both automation and overall security posture.
Building a Security Culture
Here’s something executives often miss: automated threat response isn’t just technology. It’s a cultural shift.
Teams need to think differently about risk, trust, and control. Security automation requires confidence in tools, clarity in policy, and commitment to continuous improvement.
That’s where cybersecurity awareness programs pay off. When every part of the organization understands why response speed matters, automation becomes an enabler, not a threat.
The Future of Threat Response
We’re already seeing automation infused with AI and advanced analytics. That amplifies both detection and response capabilities. The ultimate goal isn’t to fire a command and forget it. It’s to create systems that learn, adapt, and coordinate in real time.
In the future, automated threat response will:
- Predict attacker moves rather than just react
- Orchestrate cross-domain actions across endpoints, network, and cloud
- Surface context so analysts spend time on insight, not noise
This isn’t science fiction. Some enterprises are already on that path.
Final Take
Threats in cybersecurity have evolved. They operate autonomously, attacking relentlessly around the clock. Traditional, manual responses are too slow and too brittle.
Automated threat response, grounded in solid detection and integrated decision logic, is no longer optional. It’s the baseline for any effective security program. Security automation doesn’t replace human expertise. It amplifies it. It gives your team the time and context they need to stay ahead.
If you’re still relying on manual workflows and fragmented tools, it’s time to take stock. The future of cyber threat security is automated, contextual, and responsive in real time.
Waiting isn’t a strategy. Speed is.
Frequently Asked Questions
1. What is automated threat detection and response?
It’s a system that identifies cyber threats, evaluates risk, and triggers coordinated actions without waiting for manual intervention, reducing response time and limiting damage.
2. What are autonomous attacks in cybersecurity?
Autonomous attacks are threats that operate with minimal human control. They use automation and adaptive techniques to scan, exploit, and propagate across networks at machine speed.
3. How does automated threat response work?
It combines real-time detection, decision logic, and prebuilt actions to contain or neutralize threats quickly. Tools analyze data, decide on risk, and execute responses based on playbooks and policies.
4. Which threats benefit most from automated response?
High-velocity threats like brute-force attacks, zero-day exploit scans, lateral movement by malware, and suspicious behavior patterns benefit greatly because speed matters in stopping them.
5. Why is automated threat response no longer optional?
Because modern attacks move faster and scale wider than humans can respond to manually. Automation reduces latency, improves consistency, and allows security teams to operate at the speed attackers have already adopted.
FIN13: Inside a Fintech Cyber Attack
FIN13 is one of today’s most disruptive threat groups targeting fintech organizations with precision and persistence. This whitepaper breaks down their full attack chain—from reconnaissance and credential theft to lateral movement, data exfiltration, and evasion techniques. Gain insights into their TTPs, discover detection opportunities across the kill chain, and learn how NetWitness empowers faster response and mitigation.






