Key Takeaways
- Cloud threats move fast, so your detection tools need real-time visibility into identities, configurations, workloads, and data movement across every service you use.
- Misconfigurations and compromised credentials cause most cloud breaches, which makes behavior baselines and continuous configuration monitoring essential.
- The strongest setups centralize data from both on-prem and cloud environments into one unified platform, allowing SIEM, NDR, and SOAR to operate together rather than as disconnected tools.
- Effective cloud threat detection is never static. Quarterly assessments and continuous tuning keep coverage aligned with new services, attack patterns, and evolving risks.
Introduction
Moving your infrastructure to the cloud doesn’t mean leaving security threats behind. If anything, the attack surface gets bigger and more complex. You’re dealing with multiple access points, shared responsibility models, and environments that change by the minute. That’s why knowing what to look for in cloud threat detection tools isn’t optional anymore.
The Reality of Cloud Security Threats
Here’s the thing: traditional security tools weren’t built for cloud environments. They expect static networks with defined perimeters. But clouds don’t work that way. Your resources spin up and down automatically. Your users connect from everywhere. Your data moves between services constantly.
This creates blind spots. An attacker compromises an API key, and suddenly they’re moving laterally through your environment. A misconfigured S3 bucket exposes customer data. An insider downloads sensitive files before their access gets revoked. These scenarios happen fast, and you need cloud security threat detection that keeps pace.
What Makes Cloud Threat Detection Different
Cloud threat detection cyber security operates in a fundamentally different context. You’re not just watching network traffic at a firewall. You’re monitoring API calls, identity behaviors, container activities, serverless functions, and configuration changes across multiple cloud services.
The best threat detection software for cloud environments focuses on a few critical areas:
Identity and Access Patterns: Most cloud breaches start with compromised credentials or an unsecured Bucket. Your tools need to baseline normal user behavior and flag anomalies. Did someone suddenly access resources they never touch? Is a service account making API calls at 3 AM? These patterns matter.
Configuration Drift: Misconfigurations result in the majority of cloud breaches than advanced attacks. The threat detection tool you have must be continuously scanning on security vulnerabilities such as excessively liberal IAM roles, open-air storage, or databases that are publicly exposed.
Workload Behavior: What’s running in your cloud? Expected behaviors should also be on containers, VMs, and serverless functions. The thing is when a container opens outbound connections to the unfamiliar IPs all of a sudden, it is worth digging into it.
Data Movement: Where is your sensitive data exposed? The threat detection on cloud surfaces involves monitoring data exfiltration activities, abnormal volumes of downloads, and unauthorized service to service data transfers.
Essential Features for Cloud Threat Detection Tools
When you’re evaluating options, some features separate the useful from the essential:
Real-Time Visibility: Threats don’t wait for batch processing. You need continuous monitoring across all your cloud resources with minimal latency. The time between compromise and detection matters.
Context-Aware Alerts: Not every anomaly is a threat. Good tools understand your environment well enough to reduce false positives. They correlate multiple signals before alerting, so you’re not drowning in noise.
Automated Response Capabilities: Threat detection and remediation should connect directly. When you detect a compromised account, can you automatically revoke sessions? If you spot a misconfigured resource, can you fix it immediately?
Multi-Cloud Support: Unless you’re living in a single-cloud world (and most aren’t), your tools need to work across AWS, Azure, GCP, and whatever else you’re using. Unified visibility matters. 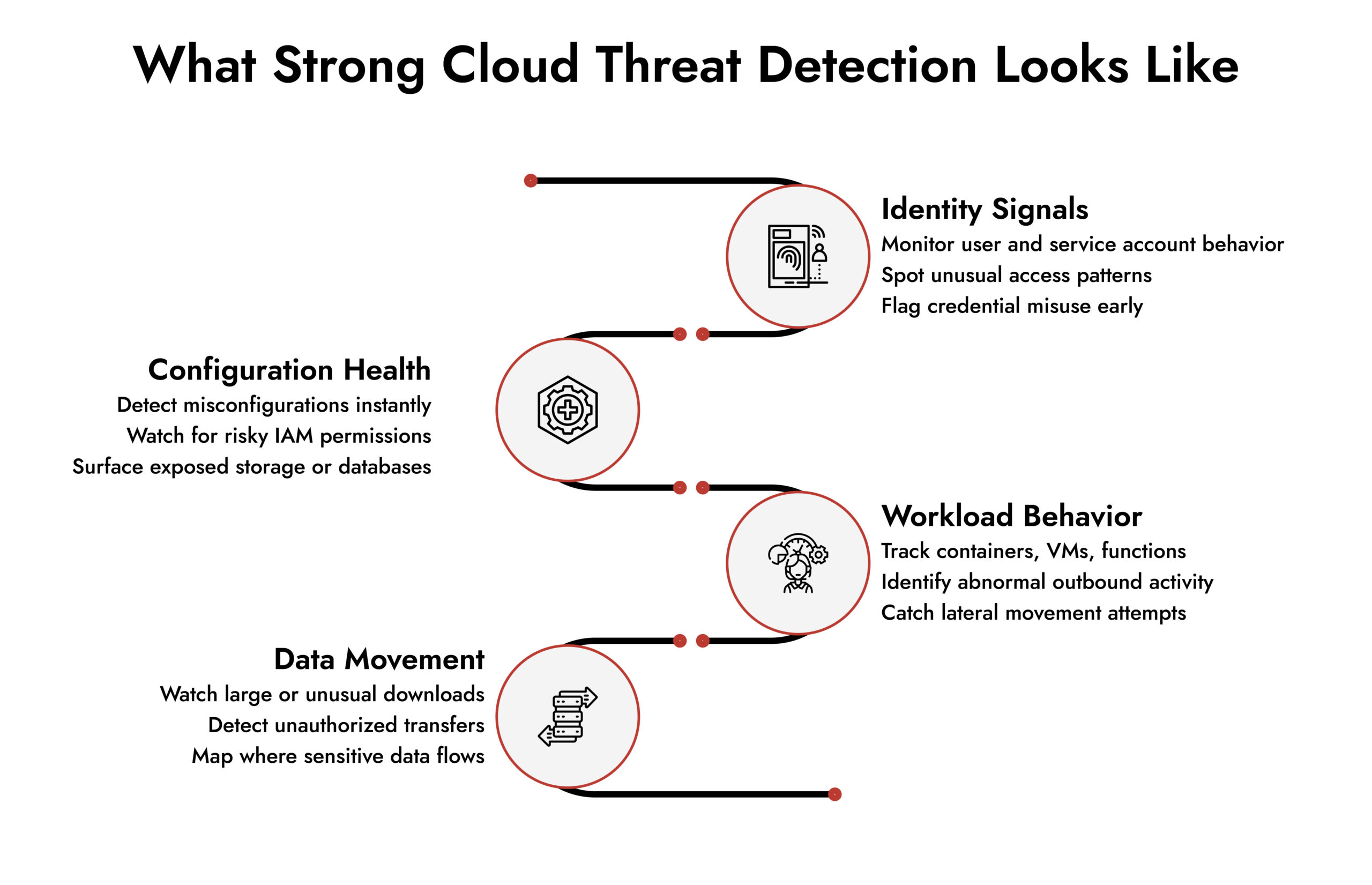
Cloud SIEM Integration: The Command Center
Cloud SIEM integration pulls everything together. Your Security Information and Event Management system becomes the central nervous system for cloud security. It ingests logs from all your cloud services, correlates events, and helps your team investigate incidents.
But here’s what makes a good SIEM for cloud different: it needs to handle the scale. Cloud environments generate massive log volumes. Your SIEM should process this efficiently without breaking your budget or overwhelming your analysts.
Look for SIEMs that offer pre-built detection rules for cloud-specific threats. Things like unusual IAM policy changes, suspicious Lambda invocations, or abnormal data access patterns. These out-of-the-box detections give you immediate value while you tune custom rules for your environment.
NDR and SOAR: Force Multipliers
Network Detection and Response (NDR) is a second layer used to identify threats in the cloud environment. It examines network traffic activities to identify the lateral movement, data exfiltration, and command and control communications. NDR can detect suspicious patterns in metadata analysis and machine learning even in encrypted traffic.
Security Orchestration, Automation and Response (SOAR) solution combines your detection power and uses it with automation. As your cloud threat detection tools detect a possible incident, SOAR security is able to automatically collect additional information, add threat intelligence to alerts, and run response playbooks.
With the combination of these systems, it forms a feedback loop. Threat detection devices detect anomalies, SIEM security correlates and prioritizes them, NDR provides the network context and SOAR automates the response. The other component complements the other component.
360° Cybersecurity with NetWitness Platform
– Unrivaled visibility into your organization’s data
– Advanced behavioral analytics and threat intelligence
– Threat detections and response actionable with the most complete toolset

What This Really Means for Your Security Posture
Investing in proper threat detection software isn’t just about checking a compliance box. It’s about reducing the time attackers can operate undetected in your environment. Security researchers call this “dwell time,” and in cloud environments, it can be dangerously short before significant damage occurs.
The right cloud threat detection tools give you two critical advantages: speed and scale. Speed means detecting and responding to threats in minutes instead of days. Scale means covering your entire cloud footprint without needing to manually monitor every service.
You also gain consistency. Human analysts can’t watch everything 24/7. Automated threat detection cyber security doesn’t sleep, doesn’t take vacations, and doesn’t miss patterns buried in millions of log entries.
How Often Should You Assess Your Cloud Threat Detection?
Your cloud environment isn’t static, so your threat detection shouldn’t be either. Assess your capabilities quarterly at minimum. New services get added. Attack techniques evolve. Your threat models change.
Each assessment should cover:
- Detection rule effectiveness and false positive rates
- Coverage across all cloud services in use
- Integration health between security tools
- Response time metrics from detection to remediation
- Gaps in visibility or monitoring
But assessment isn’t just a quarterly exercise. Continuous improvement matters. When you miss detecting a threat during a test or exercise, that’s valuable information. When a new cloud service gets deployed, detection coverage should expand automatically.
The Bottom Line
Cloud security threat detection requires purpose-built tools that understand cloud-native architectures. You need visibility into identities, configurations, workloads, and data movement. You need intelligence that reduces alert fatigue. And you need integration between detection and response systems so threats don’t linger.
The threat landscape keeps evolving. Your detection capabilities need to evolve with it. Start with comprehensive visibility, add intelligent detection, enable automated response, and continuously refine based on what you learn. That’s how you build cloud security that actually works.
Frequently Asked Questions
1. What is threat detection for cloud environments?
Threat detection for cloud environments is the continuous process of monitoring cloud infrastructure, applications, and data to identify potential security threats in real-time. It analyzes activities like API calls, user behavior, configuration changes, and network traffic to spot anomalies that could indicate attacks, breaches, or security policy violations.
2. Why is cloud threat detection important?
Cloud environments present unique security challenges with distributed resources, shared responsibility models, and dynamic infrastructure. Without proper threat detection, attackers can exploit misconfigurations, compromised credentials, or vulnerabilities to access sensitive data or disrupt operations. Cloud threat detection provides the visibility and speed needed to identify and stop threats before they cause significant damage.
3. What features should I look for in cloud threat detection tools?
Essential features include real-time monitoring across all cloud services, behavior-based anomaly detection, automated threat response capabilities, multi-cloud support, integration with SIEM platforms, pre-built detection rules for cloud-specific threats, and context-aware alerting that minimizes false positives while highlighting genuine risks.
4. How do NDR and SOAR integrate with cloud threat detection?
Network Detection and Response (NDR) enhances cloud threat detection by analyzing network traffic patterns to identify lateral movement and data exfiltration attempts. SOAR platforms integrate with threat detection tools to automate incident response workflows, enriching alerts with threat intelligence and executing remediation playbooks automatically when threats are detected.
5. How often should cloud threat detection be assessed?
Cloud threat detection capabilities should be formally assessed at least quarterly to ensure they cover new services, address evolving threats, and maintain effectiveness. However, continuous monitoring of detection metrics like false positive rates, response times, and coverage gaps should happen ongoing, with immediate adjustments when new cloud services are deployed or threat patterns emerge.
Autonomous AI Defenders for a Smarter SOC






