When a cyberattack strikes, time isn’t on your side. Every moment you delay identifying and containing an attacker adds to the amount of time needed to expel them and repair the mess they made. Every minute an advanced persistent threat (APT) is allowed to roam your networks increases the potential for financial, reputational, and regulatory ruin. That’s why investing in incident response services has become essential.
But with so many incident response vendors claiming fast, expert-led defense, how do you find the right one for your enterprise?
Let’s break it down.
Why Incident Response Services Matter in Cybersecurity?
Cyber threats are evolving. In 2023 alone, notable supply chain breaches like the MOVEit attack impacted thousands of organizations, exposing millions of records. The Identity Theft Resource Center (ITRC) reported 3,205 data compromises in 2023, up 78% year-over-year.
In IBM’s 2023 Cost of a Data Breach Report, the global average breach cost reached $4.45 million, the highest ever. Companies that responded in under 200 days saved approximately $1 million per breach compared to those that took longer.
Breaches aren’t just technical problems; they’re strategic threats. Your response defines your resilience. But resilience doesn’t happen by accident, it’s built on visibility, readiness, and action.
You can’t stop what you can’t see. That’s why incident response in cybersecurity focuses on baselining your visibility across your environment – what’s exposed, what’s vulnerable, and what’s hiding in plain sight.
Then comes readiness: your team’s ability to respond when it counts. Services like Red Teaming, Compromise Assessments, and CARE aren’t just nice to have, they’re critical for understanding how fast and effectively you can react when a breach hits. Incident response management powered by NetWitness supports all three pillars, helping organizations move from reactive to resilient.
What to Look for in Professional Incident Response Service Providers?
Not all incident response service providers deliver equal value. Before signing on, evaluate prospects against these benchmarks:
1. 24/7 Availability & Accelerated SLAs
A breach rarely waits for business hours. Around-the-clock coverage is table stakes. What really matters is who picks up the phone when it rings – an entry-level responder logging a ticket or a seasoned expert who can start triaging immediately?
Guaranteed response times matter, but rapid triage, root cause analysis, and actionable containment guidance matter more. Look for teams that can shorten your Mean Time to Contain (MTTC) and Mean Time to Recover (MTTR). That’s where NetWitness stands apart: we’re nimble, experienced, and built to guide you from alert to resolution with clarity and speed.
2. Deep Threat Expertise
When your network is under attack, you don’t need theory, you need battle-tested defenders. The best incident response service providers have seen it all: ransomware takedowns, insider threats, APTs, and zero-day exploits. They bring real-world experience and direct access to top-tier talent when it counts.
3. Multi-Environment Forensics
Today’s hybrid and cloud environments demand flexibility. Your incident response service provider should be capable of performing forensic analysis across networks, endpoints, SaaS and cloud workloads. Whether it’s AWS logs or misconfigured firewalls, they should be able to adapt seamlessly.
4. Intelligence-Driven Response
Leading incident response vendors go beyond containment, they leverage real-time threat intelligence to understand attacker TTPs (tactics, techniques, and procedures). This speeds up containment and improves proactive defenses against future incidents.
5. Communication That Scales
During a breach, communication breakdowns can make or break your response. The right incident response management partner provides executive-ready summaries, technical debriefs for SOC teams, and regulatory-ready documentation.
How to Identify Weak Incident Response Vendors?
Avoid incident response service providers that:
- Use outsourced call centers with no access to senior responders
- Rush to mitigation instead of understanding the root cause
- Rely solely on automation or generic AI tools without context
- Lack understanding of proactive preparedness measures
Rapid, Expert Response with NetWitness® Incident Response Services
-Accelerate threat containment with experienced IR specialists.
-Investigate effectively using advanced forensics and analytics.
-Minimize business impact with fast, guided remediation.

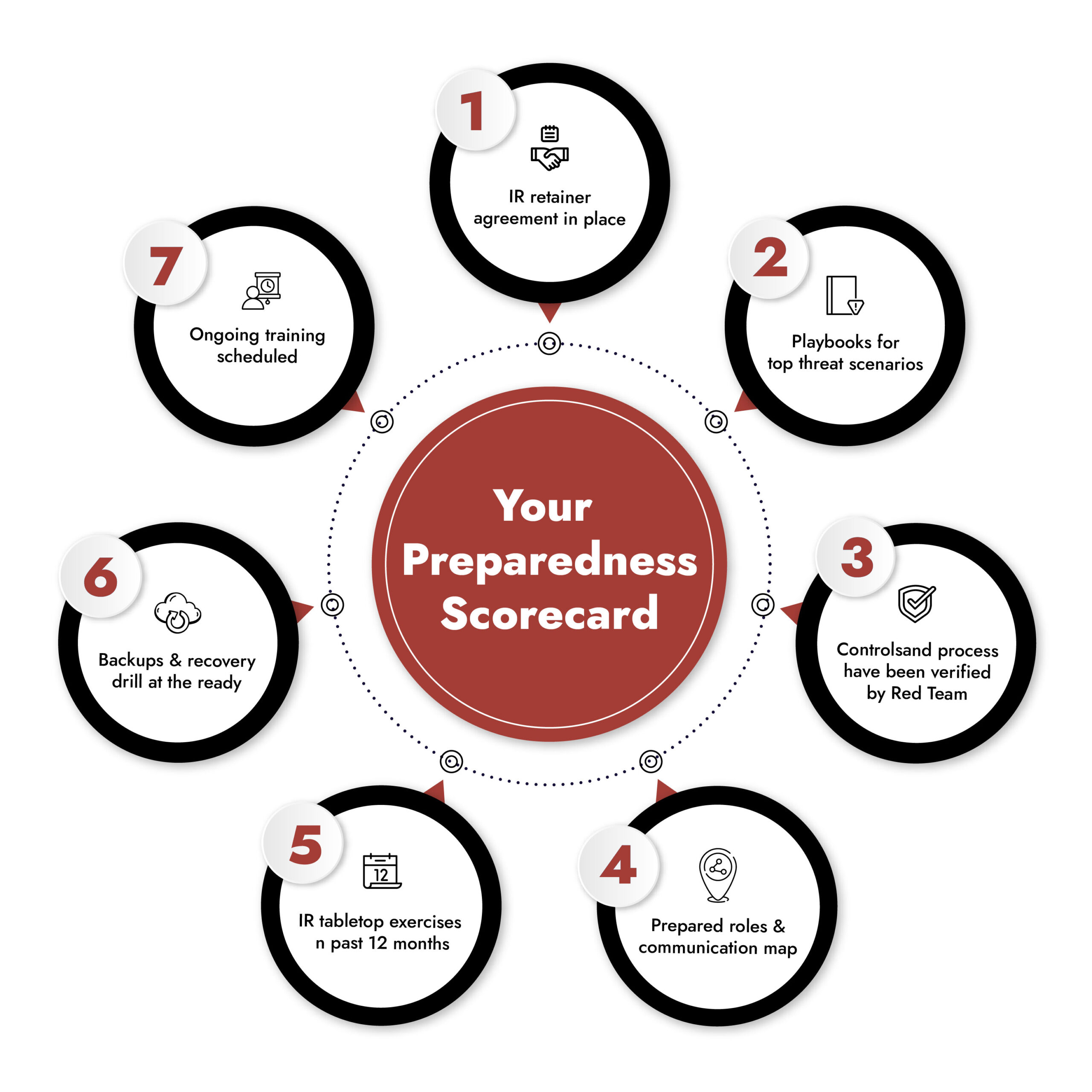
Building Internal Readiness for Effective Incident Response Management
Even the best incident response in cybersecurity won’t help if your internal readiness is weak. Here’s your checklist:
- Defined ownership across legal, IT, and PR teams
- Runbooks and playbooks for common scenarios like ransomware or data exfiltration
- A tested Incident Response (IR) Plan – clearly defining roles, timelines, and escalation points
- Regular simulations and live-fire exercises
- Clear communication protocols for internal and external updates
- Annual tabletop drills with business stakeholders
- Off-site, tested data backups for critical systems
Incident response isn’t one-and-done; it’s a continuous process built on testing, education, and partnership.
Download E-Book “Fortifying Cyber Defense: The Synergy of Threat Intel & Incident Response”
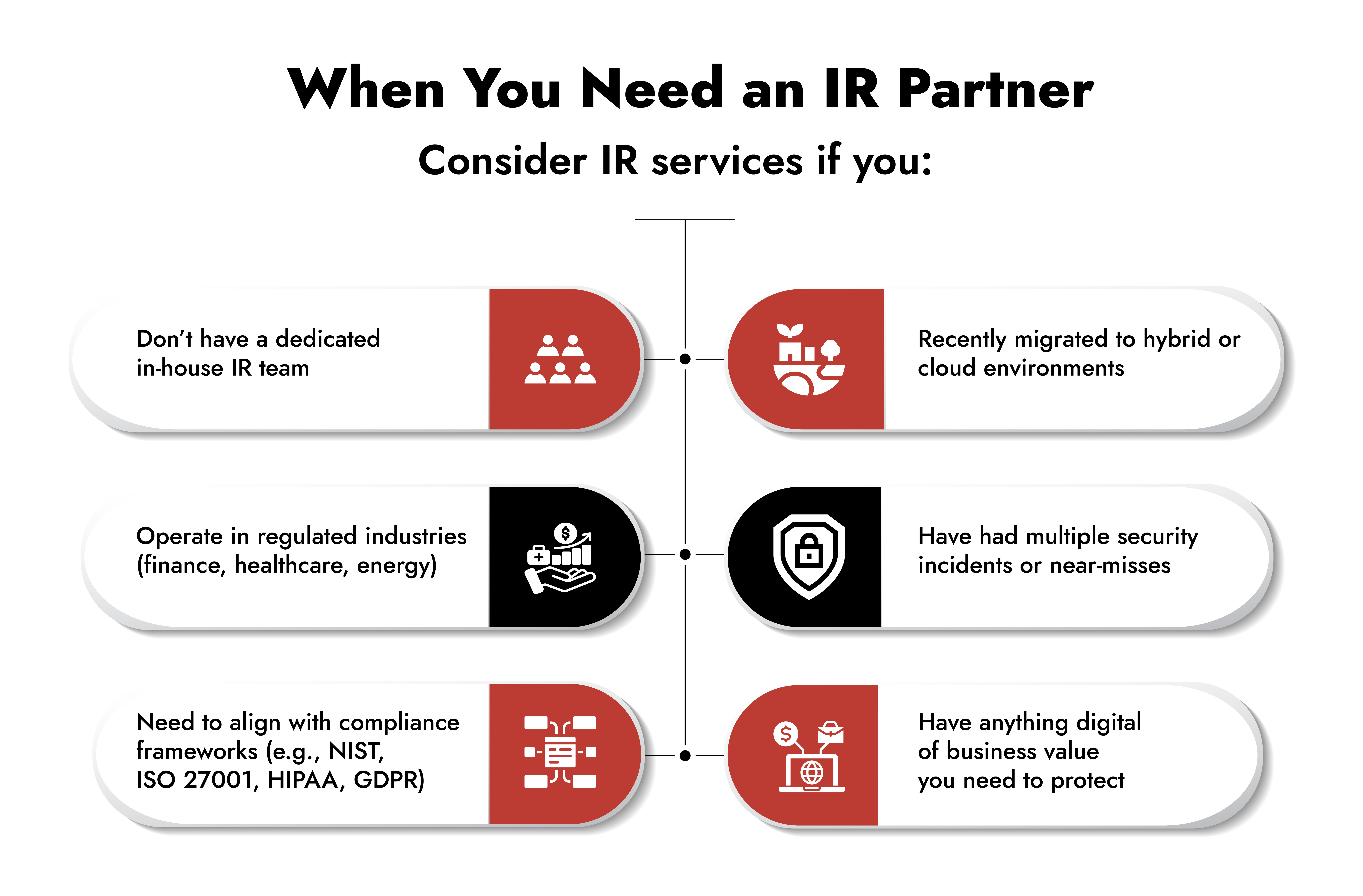
Why Do You Need Incident Response Services?
Cyber threats are faster, smarter, and more targeted than ever. From ransomware and zero-day exploits to insider threats, organizations face an evolving risk landscape. And when a breach does occur, time is your biggest enemy.
Professional cybersecurity incident response services help enterprises:
- Identify, Contain and Mitigate attacks faster
- Minimize business disruption
- Preserve forensic evidence
- Communicate effectively with regulators and stakeholders
In short, they reduce chaos when things go wrong and help you bounce back stronger.
Using Incident Response Services Proactively
Too many organizations wait until it’s too late. Incident response management is most effective when applied proactively:
- Retainers: Lock in guaranteed response times and expert access
- Threat Hunting: Identify hidden threats before they escalate
- IR Plan Development: Build or refine your strategy with expert input
- Simulations: Test readiness through red/blue team drills
- Strategic Reviews: Evaluate your tech stack for detection and response gaps
Think of this as strengthening your cyber immune system, not just buying insurance.
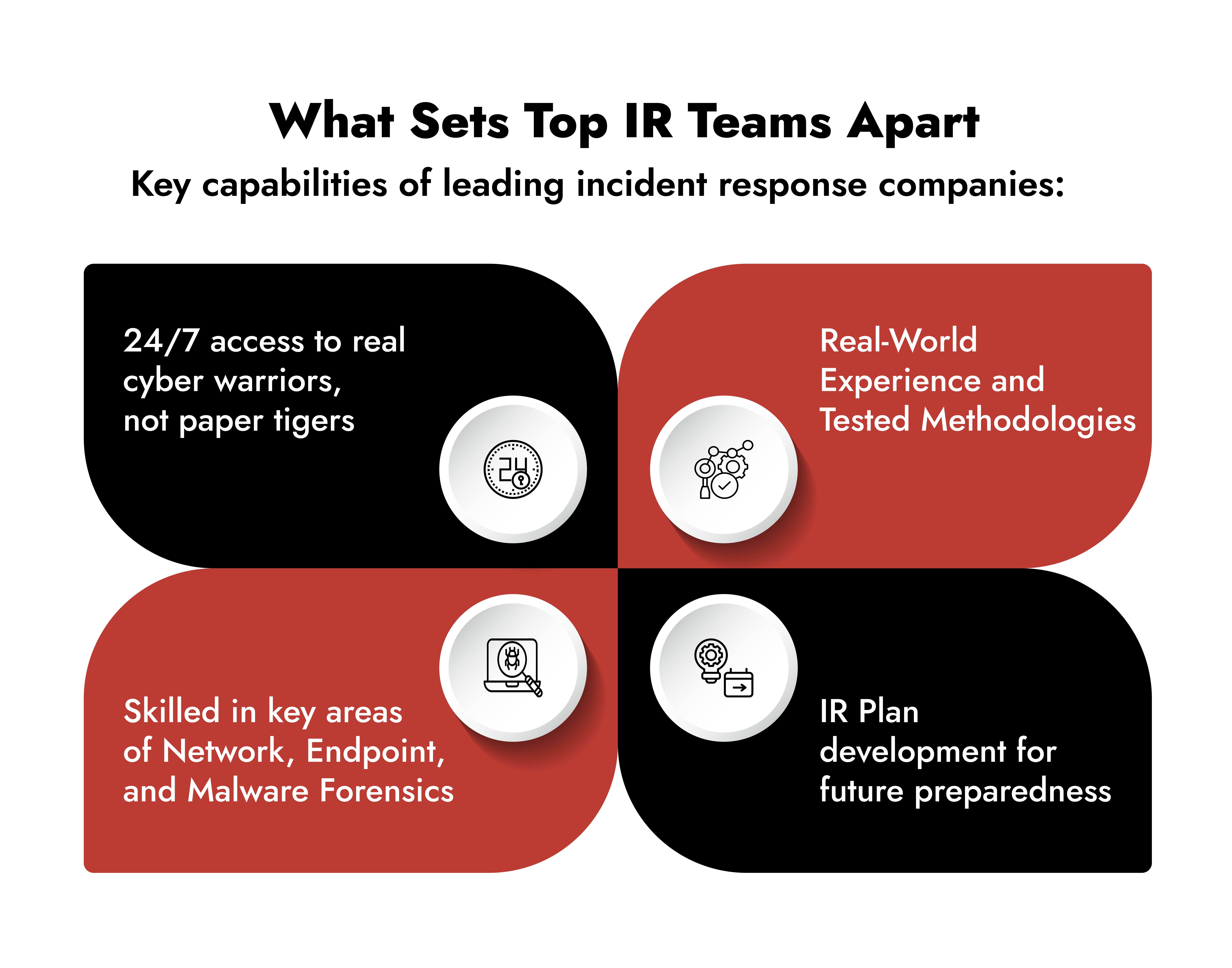
NetWitness: A Proven Partner Among Leading Incident Response Service Providers
Here’s how NetWitness delivers value through its incident response services:
- Global Expertise – Incident responders, forensic analysts, and malware specialists with multi-industry experience
- Comprehensive Coverage – Unified visibility across endpoint, network, and cloud data
- Proactive IR Programs – Readiness assessments, threat hunting, and IR plan development
- Integrated Platform – Access to telemetry and threat intelligence from the broader NetWitness ecosystem
In short, NetWitness doesn’t just respond, it helps enterprises predict, prepare, and prevent.
Final Thought
Your incident response management strategy is only as strong as the people and partners behind it. Choose a service that does more than react, choose one that strengthens your entire cyber defense posture.
When the stakes are highest, the right incident response service provider won’t just put out fires, they’ll help you build a system that doesn’t catch fire in the first place.
Frequently Asked Questions
1: How do professional incident response services differ from in-house teams?
Professional incident response services bring deep specialization—tools, threat intel, and forensic skills—that most internal teams don’t have. They’re also more objective during high-pressure investigations.
2: Should we have an IR retainer even if we haven’t had a breach?
Yes. Retainers ensure immediate access to experts and predictable SLAs, which means you get prioritized support during a crisis, reducing response times and costs. Plus, you often get additional services like plan reviews or quarterly assessments.
3: What tools are used for incident response?
Common tools include SIEM platforms, forensic suites, endpoint detection tools, and threat intelligence feeds. Many incident response vendors integrate automation to speed up containment and analysis.
4: Can you explain the difference between critical incident response services and other emergency services?
Critical incident response services handle major cyber incidents that threaten business continuity or data integrity. Unlike general emergency services, they focus on cybersecurity threats and use specialized tools and frameworks to investigate digital intrusions.
5: What are the main responsibilities of a critical incident response team?
A critical incident response team is responsible for identifying, containing, eradicating, and recovering cyberattacks. They also perform root-cause analysis, preserve evidence, and help improve future response plans.




