What is an Incident Response Plan?
An incident response plan (IRP) is a documented, structured approach outlining how an organization identifies, contains, investigates, and recovers from cybersecurity incidents.
At its core, the plan ensures your security team knows exactly what to do when a threat occurs – who is responsible, what tools to use, and how to communicate across teams and leadership.
Every organization knows a cyberattack is not a matter of if, but when. What separates a minor disruption from a full-scale breach often comes down to one thing – the incident response plan. A well-structured plan not only minimizes damage but also helps teams recover faster, preserve evidence, and strengthen defenses against future threats.
Here’s the thing: security incidents today unfold at machine speed. Without a clear, rehearsed plan, even the most advanced SOCs lose precious minutes trying to coordinate, communicate, and contain. This guide breaks down the five essential steps of an incident response plan, explains why each phase matters, drawn from frameworks like NIST and real-world enterprise experience – all through the lens of the NetWitness IR Team’s expert-led approach
Why Does Incident Response Plan Matter?
A strong cybersecurity incident response plan does three things:
- Reduces operational and financial impact.
- Preserves digital forensics for post-incident analysis.
- Strengthens the overall security posture through lessons learned.
NIST’s Computer Security Incident Handling Guide (SP 800-61) remains the global reference for structuring IR plans but adapting it to your unique business context is where the real value lies — something NetWitness IR excels at through tailored, expert-led engagements.
5 Key Steps Incident Response Plan
Step 1: Preparation – The Foundation of Effective Response
Preparation defines how ready your organization is to respond to a cyber incident before it even happens.
This step includes everything from building your incident response team and defining roles to ensuring your tools – SIEM, NDR, EDR, and SOAR – are integrated and tested. Teams should have up-to-date contact lists, predefined communication channels, and quick access to critical playbooks.
Key actions:
- Establish governance and assign clear ownership for incident response.
- Maintain an asset inventory to understand your attack surface.
- Conduct tabletop and red team exercises regularly.
- Validate data visibility across endpoints, networks, and cloud environments.
- Use compromise and other assessments to find vulnerabilities in your program.
The best run security programs often mandate an incident response retainer from a 3rd party that specializes in Incident Response. Effective retainer programs integrate 3rd party and organizational resources around the topics above. NetWitness fields an independent, expert-led Incident Response team that helps organizations build, test, and utilize IRPs.
Step 2: Identification – Detecting and Confirming the Incident
Identification is about quickly detecting abnormal activity, verifying its authenticity, and determining its scope.
An alert is not always an incident – analysts must differentiate false positives from true threats. The faster this happens, the lower the damage. A robust incident response plan framework defines how alerts are triaged and what qualifies as a “security incident.”
Best practices for identification:
- Correlate alerts using SIEM and NDR tools to reduce noise.
- Use threat intelligence feeds to validate suspicious indicators.
- Document every potential incident with timestamped evidence.
The most effective SOCs rely on unified visibility – correlating data from networks, endpoints, and cloud workloads. NDR solutions like the NetWitness platform enhance his stage by enabling analysts to distinguish between routine alerts and high-priority threats through behavioral analytics and contextual correlation.
Step 3: Containment – Limiting the Damage
Containment focuses on isolating affected systems and preventing the spread of the incident.
Containment involves actions like disconnecting compromised endpoints or restricting network access. Your containment strategy may require more nuance as the goal is to keep the adversary from acting on their objectives without alerting them that you know they are there.
Incident response best practices for containment include:
- Segment infected systems to disable lateral movement.
- Apply temporary firewall rules or blocklists.
- Preserve volatile data for forensic analysis before system resets.
Strategically, this phase depends on speed and visibility. NetWitness Incident Response helps responders isolate compromised systems quickly while preserving critical evidence for further analysis, enabling both immediate action and post-incident learning.
How NetWitness IR Accelerates Every Phase of Incident Response
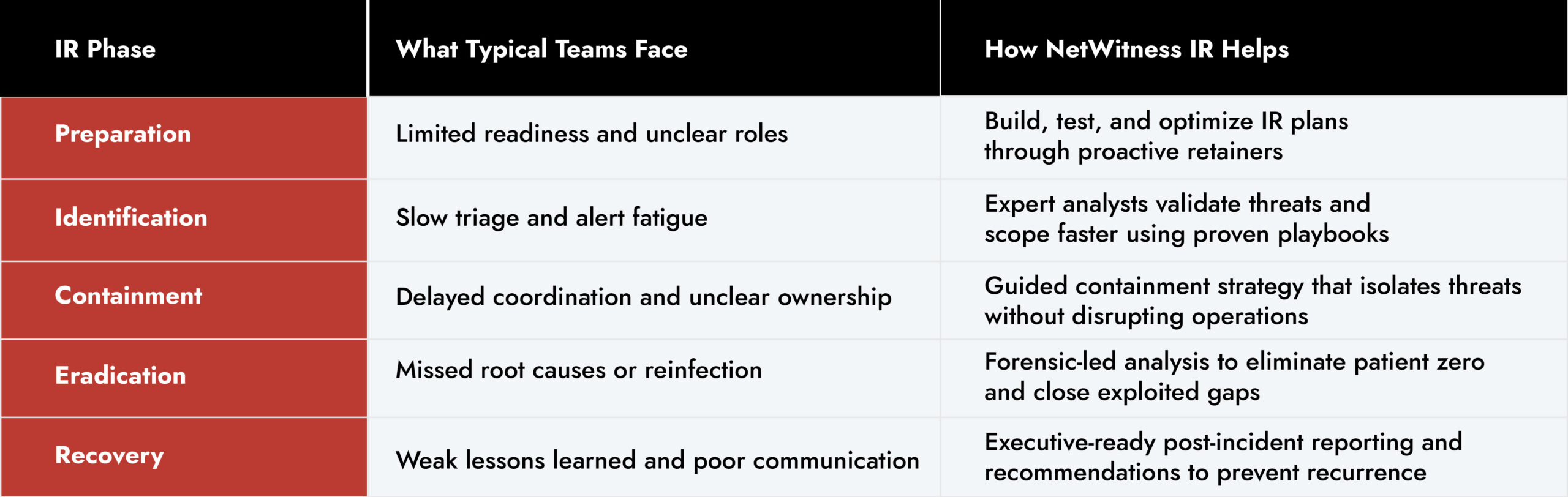
Step 4: Eradication and Recovery – Restoring Trust and Operations
Eradication removes the root cause of the breach, while recovery focuses on safely restoring systems and verifying normal operations.
After isolating the threat, responders identify patient zero, develop a timeline of events, eliminate malware, close exploited vulnerabilities, and restore clean backups. Once systems are back online, they must be closely monitored for any residual signs of compromise.
Checklist for this stage:
- Conduct vulnerability scans and patch exploited systems.
- Rebuild compromised servers or reimage endpoints.
- Validate recovery with continuous monitoring and testing.
- Communicate status updates to leadership and stakeholders.
Enterprise teams often integrate advanced analytics and historical data correlation to verify eradication success – areas supported by products like the NetWitness platform.
Step 5: Turning Incidents into Insights
The final step of an incident response plan is to analyze what happened, why it happened, and how to prevent it next time.
This phase transforms a crisis into a catalyst for maturity. Post-incident reviews should be mandatory, involving all key stakeholders, from technical teams to executives.
Recommended actions:
- Conduct a post-mortem within two weeks of resolution.
- Review logs, communication gaps, and decision points.
- Update playbooks and detection rules based on findings.
- Train teams on newly identified tactics, techniques, and procedures (TTPs).
Organizations that document lessons learned consistently build resilience. Many integrate this phase with their threat intelligence programs, ensuring that new insights enhance both detection models and future IR readiness.
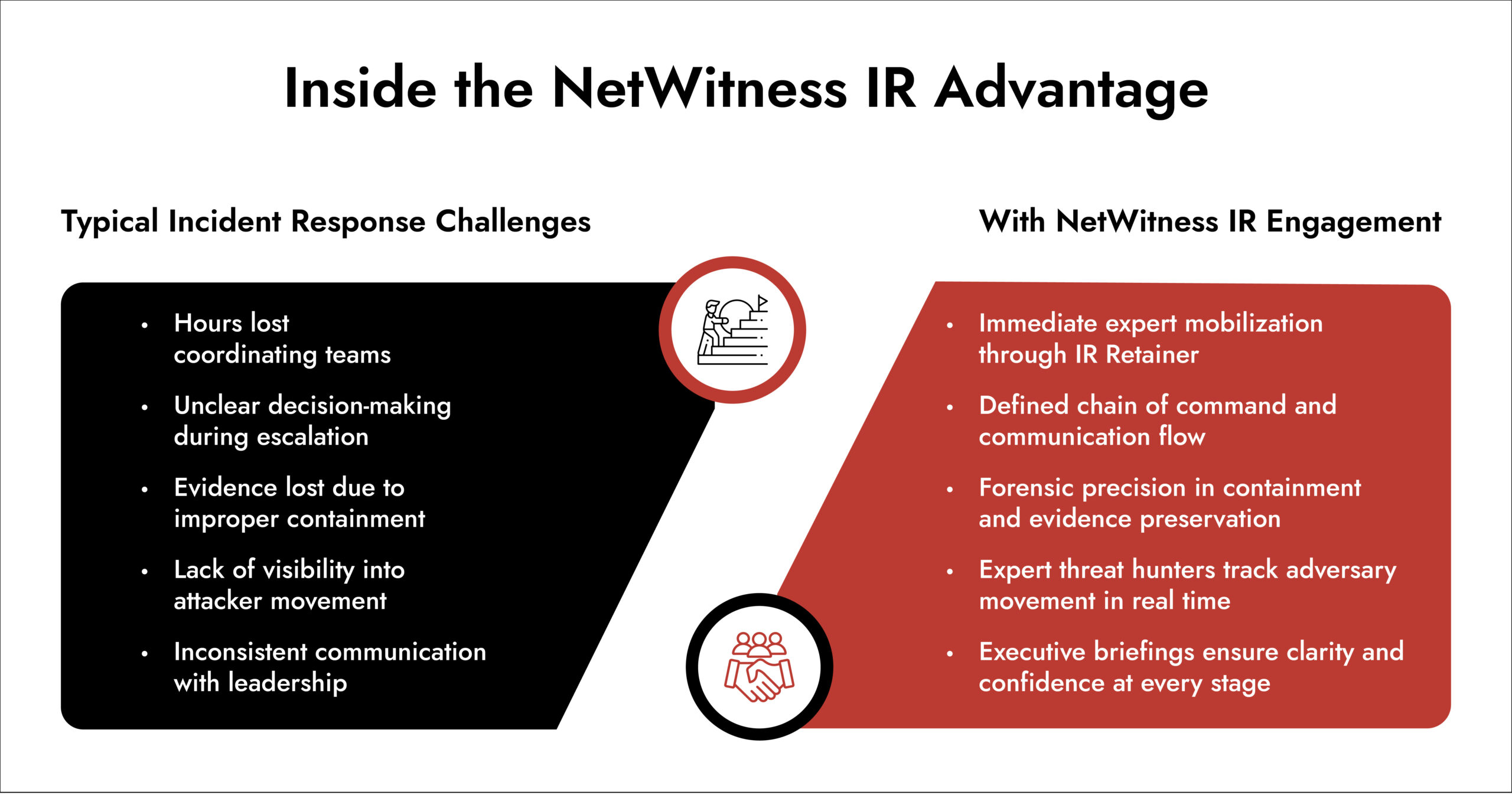
Conclusion
An effective incident response plan isn’t static. It evolves as your business, threat landscape, and technology stack change. The goal isn’t just to react, it’s to anticipate, prepare, and be resilient.
When every second counts, visibility and coordination matter most. That’s where intelligent detection, extensive investigation, and expert-led Incident Response Services converge to make a measurable difference.
NetWitness IR, built on proven framework, discipline, and experience, delivers independent, expert-led proactive and reactive Incident Response services. Don’t wait for a breach, leverage NetWitness IR to protect your critical systems and turn every security incident into a strategic advantage.
Rapid, Expert Response with NetWitness® Incident Response Services
-Accelerate threat containment with experienced IR specialists.
-Investigate effectively using advanced forensics and analytics.
-Minimize business impact with fast, guided remediation.

Frequently Asked Questions
1. Why is an incident response plan important?
It ensures your organization can respond quickly and effectively to cyber incidents, reducing financial, reputational, and operational damage. A well-structured plan defines responsibilities, accelerates containment, and improves recovery outcomes.
2. What are the 5 incident response steps?
The five key steps are preparation, identification, containment, eradication and recovery, and post-incident insights. Each step forms a structured cycle that strengthens your organization’s ability to detect, respond, and adapt.
3. Who is responsible for incident responses in an organization?
Typically, the responsibility lies with the Incident Response Team (IRT), including SOC analysts, IT leads, and CISOs. However, effective response requires cross-department coordination involving communication, legal, and executive functions.
4. What should an incident response plan include?
A complete cybersecurity incident response plan includes defined roles and responsibilities, communication protocols, technical procedures for each phase, documentation templates, and escalation criteria for major incidents.
5. How often should an incident response plan be updated?
Organizations should review and test their IR plan at least bi-annually or after any major incident, infrastructure change, or new regulatory requirement. Regular updates ensure the plan reflects evolving threats and technologies.
6. How do you know your Incident Response plan will work?
Organizations should test their IR plan at least once a year if not more. Such tests can reveal weaknesses in the plan or gaps in your teams’ abilities. Regular testing helps you generate a performance baseline which can be improved to ensure your IR plan is effective. Services like NetWitness’s Controlled Attack and Response Exercise (CARE) are designed to mimic real-world attacks, so you can see how your IR plan responds in the worst-case scenario.
7. How do SIEM and NDR tools help with incident response?
SIEM systems centralize log data and provide event correlation, while NDR tools analyze network behavior to detect anomalies. Together, they enhance visibility, reduce noise, and help responders validate and contain threats faster.




