When a cyber event occurs, your most scarce resource is time, while clarity becomes your greatest asset. However, achieving clarity requires intentional effort, cultivated through a systematic incident response process. In the realm of incident response in cybersecurity, that clarity comes from following a structured path built around the 3 Pillars of the Incident Response Investigation.
These pillars are not merely steps on a checklist, they are interrelated practices that determine whether your team handles an incident confidently or stumbles through costly missteps.
In this blog, we’ll explore what each of the 3 pillars of incident response looks like in practice, why they matter, and how to align them with your enterprise cyber incident response plan.
Why a Structured Cyber Incident Response Plan Fails Many Enterprises?
Even organizations with mature cybersecurity programs that are familiar with the 3 pillars of incident response investigation struggle to move swiftly from alert to action. Why?
Because most incident response efforts stall at the surface: responding to what’s obvious without fully understanding what’s happening underneath. Investigations become reactive, containment is partial, and remediation feels like a whack-a-mole.
The result? Dwell time stretches. Attackers stay active longer than they should. And recovery becomes more costly than it needs to be.
Here’s the thing: effective IR isn’t just about plugging holes. It’s about understanding the blast radius, isolating the threat, and ensuring it doesn’t come back.
Let’s break that down through the 3 pillars of the incident response investigation.
3 Pillars of Incident Response Investigation
Pillar 1: Situational Awareness – The Foundation of Every Incident Response Process
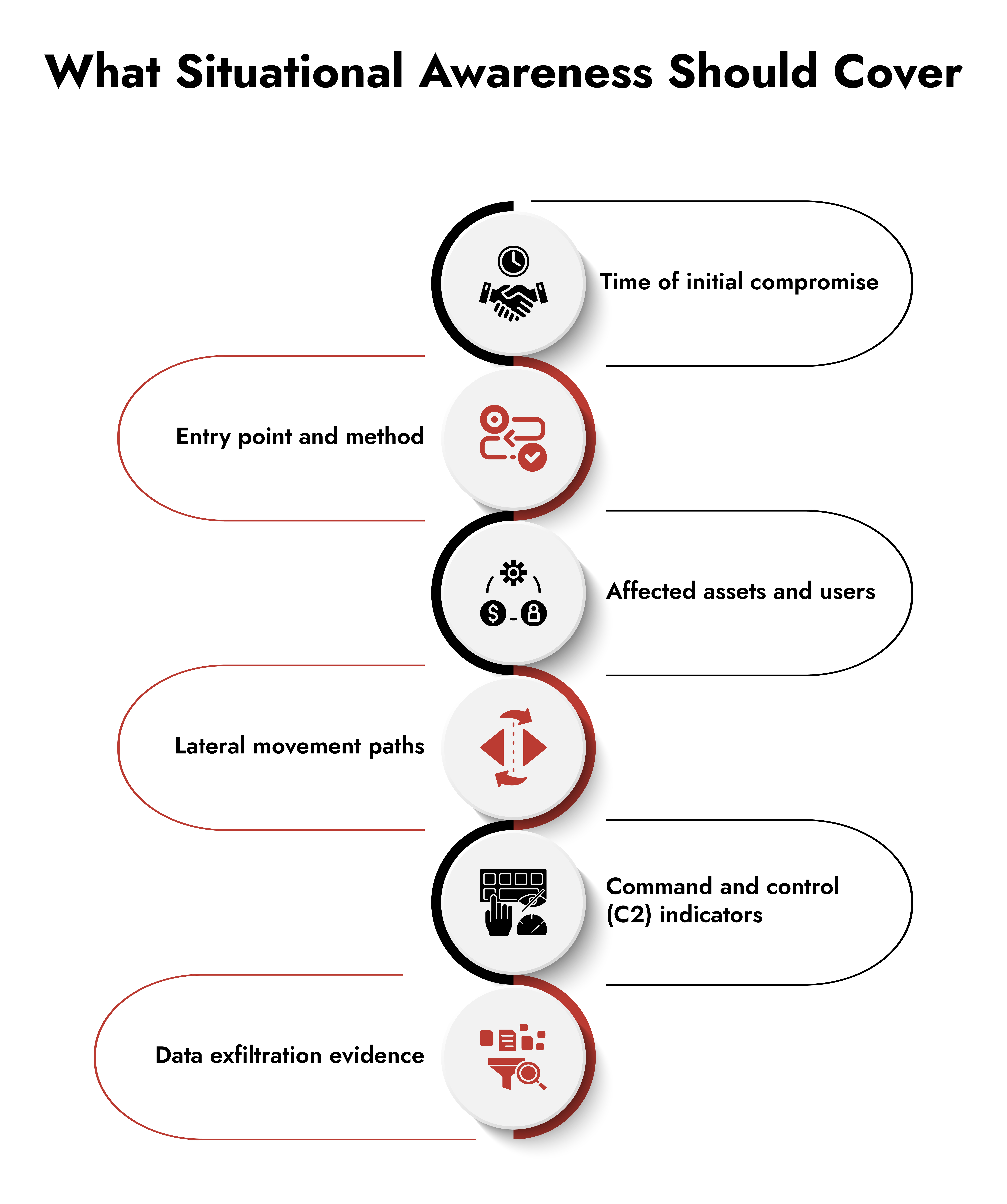
Situational awareness is the foundation of any high-functioning Incident Response investigation. You can’t contain what you don’t fully understand.
This phase is all about gathering context:
- What systems are involved?
- What data might be affected?
- How is the attacker moving laterally, if at all?
- What is the scope and impact?
Modern incident response teams use data from endpoints, networks, and cloud environments. This helps them create a real-time view of threats. Full-packet capture, session reconstruction, and threat intelligence all play a part in understanding the adversary’s behavior.
Pillar 2: Containment – Controlling the Blast Radius
Once the incident is fully scoped, the second step of the 3 pillars of incident response comes into play: containment. That means isolating affected systems and cutting off adversary access without crippling business operations in the process.
There is a balance here – you need to act fast, but not recklessly.
Common containment actions include:
- Disabling compromised accounts
- Segregating affected network segments
- Blocking malicious IPs or domains at the firewall
- Deploying endpoint isolation protocols
What separates strong incident response management from weak ones is the ability to contain threats surgically, minimizing disruption while preventing escalation.
This is where the value of predefined incident response playbooks and automated response actions becomes clear. Teams that can trigger containment protocols based on threat type don’t have to reinvent the wheel every time.
Containment isn’t just an IT responsibility, it’s a business continuity move.

Pillar 3: Expulsion, Eradication, and Recovery – The Remediation Phase of Incident Response
Once you’ve established situational awareness and achieved containment, what comes next isn’t just routine remediation, it’s a focused campaign to expel the attacker, eradicate their presence, and restore your enterprise with confidence.
Attacker Expulsion: Kicking Out the Intruder
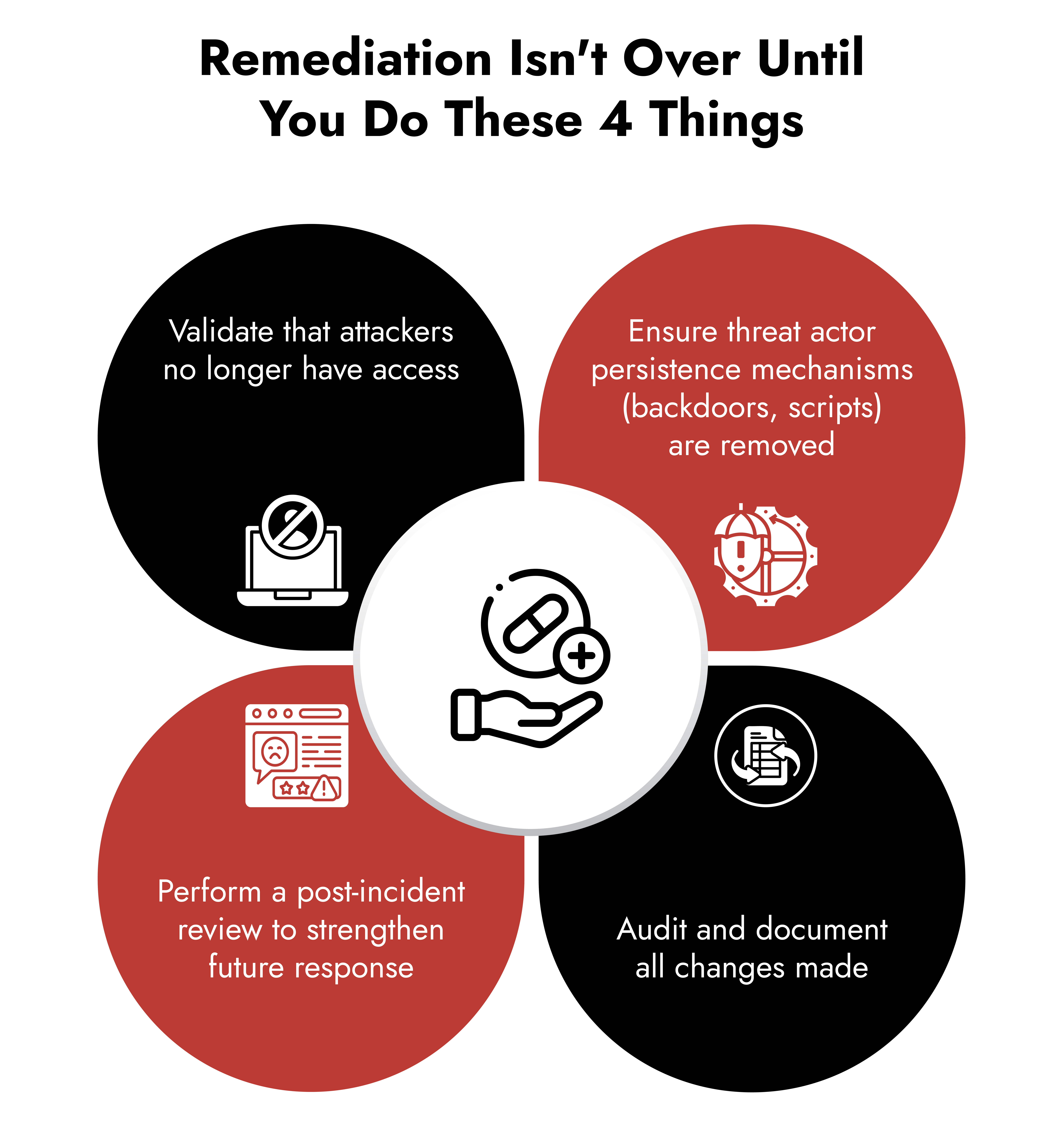
First, ensure that the adversary no longer has any access to your environment. This requires coordinated actions across accounts, endpoints, and network controls:
- Disable compromised accounts and credentials.
- Block malicious IPs, domains, and C2 infrastructure that attackers leveraged.
- Find and remove all persistence mechanisms (scheduled tasks, registry modifications, implants, scripts).
- Use forensic and network tools to confirm the attacker cannot re-enter the system.
Eradication: Cleaning Up and Closing Doors
With access blocked and the attacker expelled, the next step is deep cleaning—eliminating all traces and root causes of compromise:
- Malware and artifact removal through host and network forensics
- Vulnerability management to patch the root causes, not just symptoms
- Threat intelligence integration to update detection rules
Recovery: Validating and Restoring for the Future
The goal is not just “back to business,” but “back to better business.” Recovery ensures your systems are clean, secure, and your defenses are stronger than before:
- Restore clean backups and validate system integrity
- Conduct post-incident monitoring for reinfection or lingering threats
- Document lessons learned and updated your cyber incident response plan
- Revise playbooks to strengthen future readiness
This phase closes the loop of the incident response process, setting the tone for institutional learning and long-term resilience.
How NetWitness Strengthens Enterprise Incident Response Investigations?
At this stage, many organizations face a tough question: “Do we have the internal expertise and tooling to handle this ourselves, or do we need support?”
This is where NetWitness Incident Response services offer value beyond the typical outsourced incident response team.
Here’s what NetWitness brings to the table:
- 24×7 global IR readiness with SLA-backed response times
- Access to elite responders with experience across ransomware, supply chain attacks, and APTs
- Deep investigation capabilities, powered by the NetWitness Platform’s full-packet capture and session reconstruction tools
- Collaboration across your IT, security, and compliance teams to align response actions with business impact
Instead of flying blind or overreacting, NetWitness helps enterprises respond with precision and confidence. It is not just about reacting, it’s about investigating smarter, containing faster, and recovering stronger.
You can explore more here: NetWitness Incident Response Services
Final Thoughts: Why These 3 Pillars Still Matter
Attackers adapt. Yet, the basics of IR remain constant.
When dealing with a credential compromise, ransomware, or insider threats, a clear plan is essential. Focus on situational awareness, containment, and remediation. This approach will help your team limit damage and learn quickly.
The 3 Pillars of the Incident Response Investigation aren’t just for the SOC. They’re essential for decision-makers who want faster, smarter responses that don’t just restore operations but improve them.
Rapid, Expert Response with NetWitness® Incident Response Services
-Accelerate threat containment with experienced IR specialists.
-Investigate effectively using advanced forensics and analytics.
-Minimize business impact with fast, guided remediation.

Frequently Asked Questions
1. What are the 3 pillars of the incident response investigation?
The 3 pillars of incident response are situational awareness (understanding the scope of the threat), containment (preventing further spread), and remediation (eliminating root causes and securing systems). These are the core elements of a successful incident response process.
2. Why should a cyber incident response plan follow these pillars in order?
Each pillar builds on the previous one. Skipping steps lead to blind spots, poor containment, and incomplete remediation.
3. How is remediation different from containment in incident response?
Containment stops the attack’s progress by isolating affected systems. Remediation addresses the underlying cause – patching vulnerabilities, restoring clean backups, and strengthening defenses.
4. What are the steps of a strong remediation plan?
An effective plan includes:
- Identifying and removing persistence mechanisms
- Patching exploited vulnerabilities
- Resetting credentials and access
- Rebuilding or cleaning systems
- Documenting actions and lessons learned
5. What happens if you ignore the 3 pillars of incident response in cybersecurity?
Extended dwell time, recurring breaches, and higher recovery costs due to a lack of structured incident response management.




