IoT Risk Management: Managing Digital Risk in the New Era
While there are many advantages to digital transformation, there is also a great deal of digital risk, particularly as businesses quickly embrace cloud, mobile, analytics, AI, and an ever-growing array of IoT devices. IoT is growing at an exponential rate, with global IoT-connected devices projected to grow to 40 billion by the year 2030, likely overtaking traditional IT assets and producing enormous amounts of data while connecting the digital and physical worlds across businesses. However, most enterprises lack visibility and control over their internet of things settings, which can lead to overwhelming security vulnerabilities, unmanaged devices, and ambiguous ownership.
Fortunately, two key shifts are significantly improving IoT management efficiency:
- Edge computing, which unifies IoT management on a single platform.
- New standards and frameworks that provide structure to the IoT ecosystem.
This is starting to solve these issues. Organizations will require flexible, modern solutions to properly manage IoT risks as security and configuration management improve, and AI-enabled and autonomous IoT systems evolve.
Introduction to IoT Risk
The fast expansion of the Internet of Things (IoT) has connected billions of devices, bringing efficiency and convenience while also posing substantial security dangers. With many gadgets exchanging sensitive data and controlling important activities, vulnerabilities are easily exploited to gain access to confidential information or disrupt crucial systems. This makes IoT setups very appealing to targets, necessitating a proactive, well-structured approach to security. Here’s how you can achieve this:
- Make incident response a key component of IoT security.
- Establish a specialized incident response team with distinct roles and duties.
- Perform frequent risk evaluations to locate weaknesses in linked devices.
- Offer continuous training to enable stakeholders to manage IoT-related threats effectively.
- Actively oversee IoT risks to safeguard sensitive information and ensure operational continuity against emerging threats in the continually growing Internet of Things.
Understanding IoT Devices
IoT devices are physical items equipped with sensors, software, and connections that can gather, process, and exchange data in a variety of settings, including smart homes and healthcare, as well as manufacturing and industrial systems. Their diversity and ubiquitous presence make them attractive targets for attackers, particularly when security procedures are lax or inconsistent.
Strong security measures like data encryption, access control, and timely patching are crucial to preventing unwanted access and exploitation because many IoT devices have low computing power and memory, making standard security solutions impractical. Understanding these unique vulnerabilities and proactively safeguarding IoT devices can help organizations improve their overall security posture and respond more effectively to emerging threats.
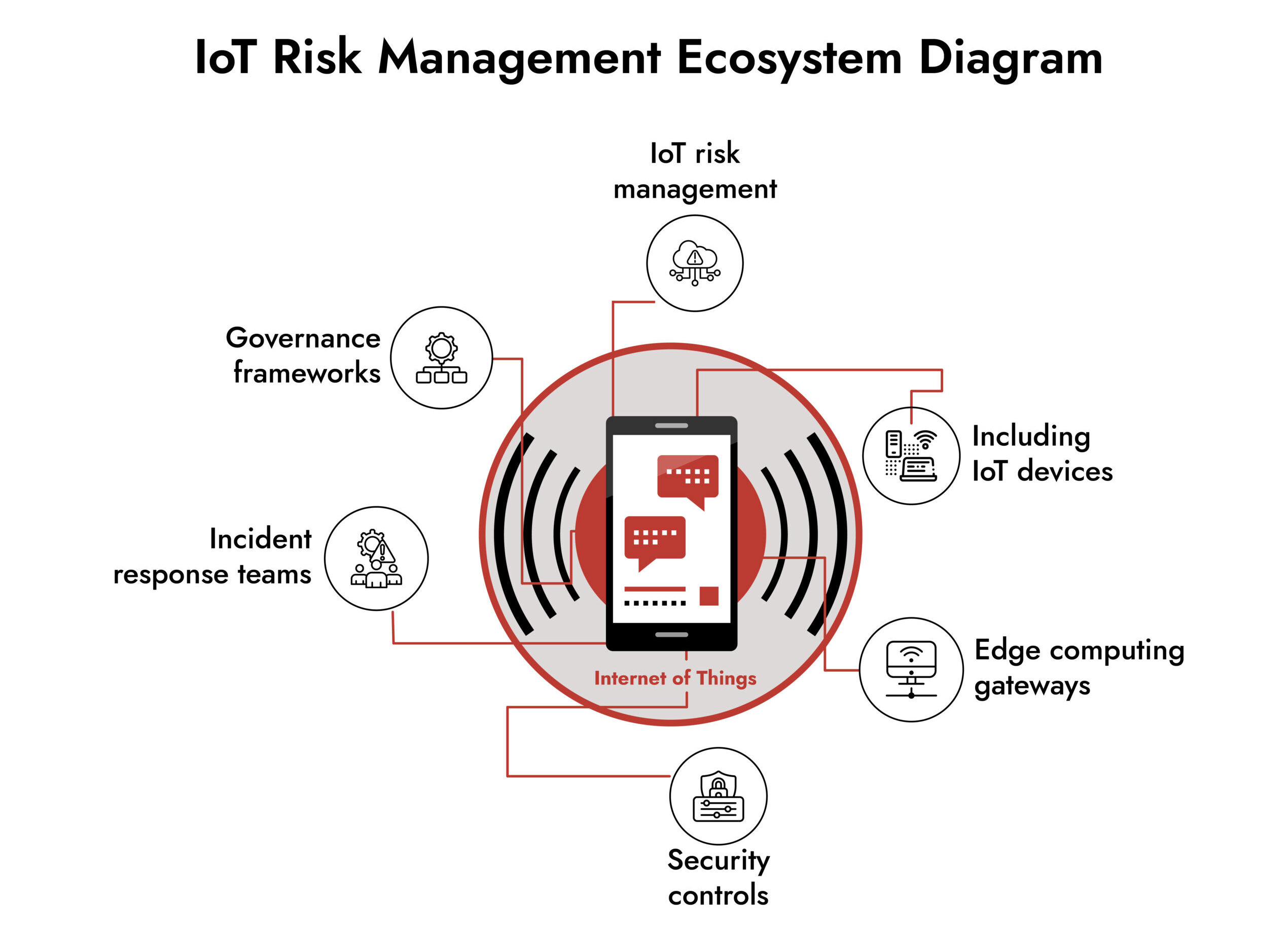
IoT Edge Computing and IoT Devices
IoT developed largely outside the oversight of IT, security, and risk teams, because operational groups traditionally procured and managed these mission-critical systems with a focus on uptime and safety, not security. Many devices lack the CPU, storage, or patching capabilities required for contemporary protection because they were designed for isolated, decades-long deployments. In OT/ICS, where specialized protocols and compartmentalized systems make unified administration practically difficult, this fragmentation is particularly evident.
Key challenges:
- Devices often cannot be easily patched or secured over time.
- OT/ICS environments use highly specialized, inconsistent protocols.
- Siloed systems operate outside IT’s visibility and control.
- Traditional security tools don’t fit low-power, long-lived devices.
By adding a gateway layer between devices and data centers, IoT edge computing enables local processing, discovery, authentication, and security controls at the device level. These gateways offer centralized monitoring with automated threat detection using cloud analytics to spot anomalies or known-bad activities, handle a variety of protocols, and lower bandwidth requirements. By facilitating innovation and scalable device management, open platforms like EdgeX Foundry and commercial edge solutions further improve this strategy, assisting enterprises in streamlining the fragmented IoT landscape of today and becoming ready for billions of future devices.
What edge computing enables:
- Local, real-time processing, and security controls.
- Discovery, authentication, and unified device management.
- Support for diverse/proprietary IoT and OT protocols.
- Automated detection and response to device-level threats.
- Scalable, low-latency operations for future IoT growth.
Fortify Cyber Defense with Threat Intel + Incident Response
Combine real-time threat intelligence with rapid incident response workflows.
Detect advanced threats before they strike — armed with enriched context and actionable alerts.
Respond faster and smarter with orchestrated, data-driven playbooks.
Build a resilient security posture that adapts to evolving cyber threats.

Incident Response for IoT
Organizations employ incident response services as a structured method for identifying, containing, and resolving cyber issues. This is particularly important for IoT setups because of the quantity of linked devices and the possible consequences of a breach. Threats are promptly detected, confined before they spread, and addressed with the least amount of disturbance when an efficient response framework is in place. 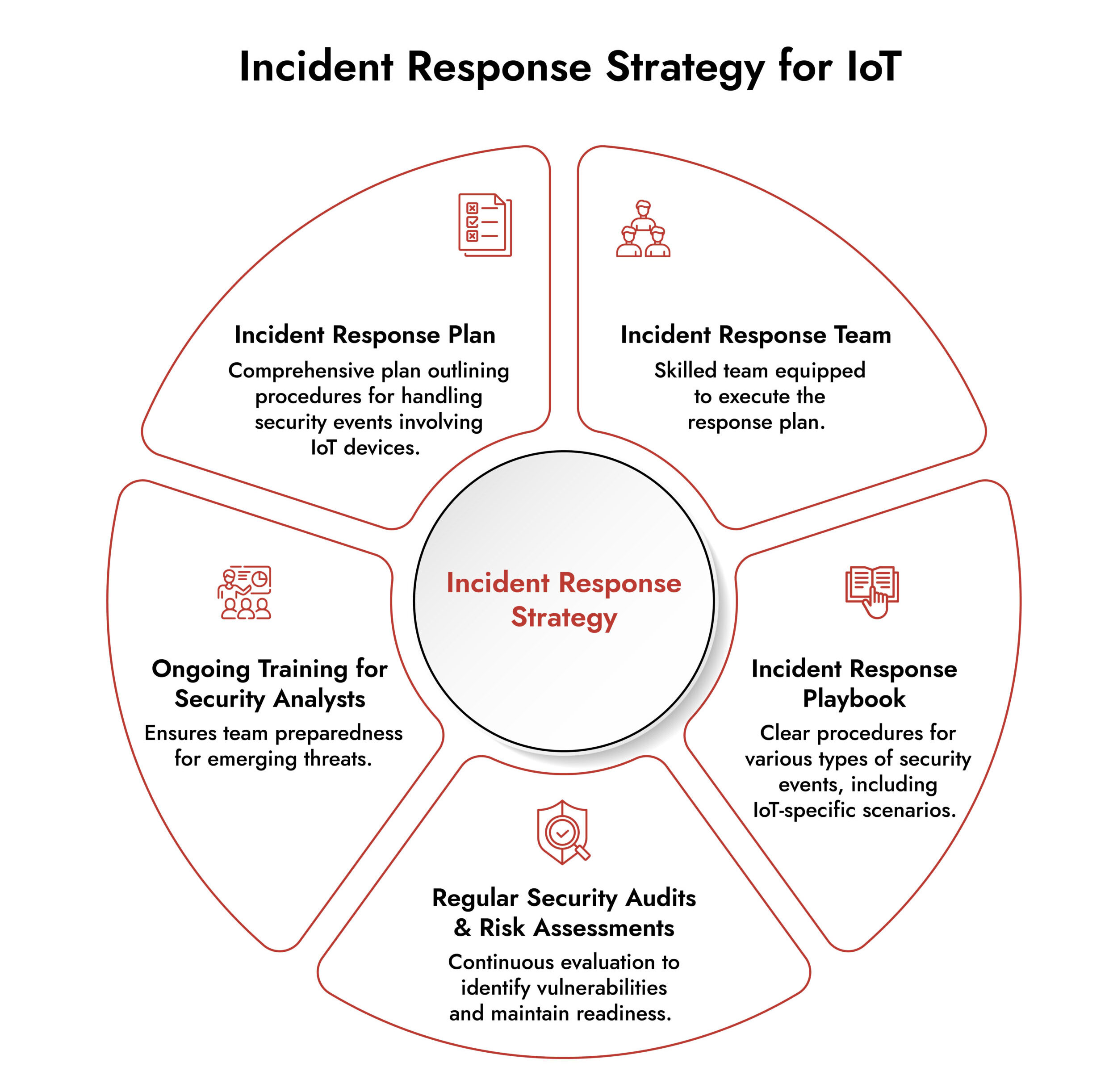
What sets NetWitness Incident Response Services apart
- Deep Cybersecurity, incident response, network, and host technology expertise to holistically design and build your security monitoring program or SOC.
- Capacity to comprehensively identify security programs and control shortcomings using IR expertise to produce comprehensive improvement plans.
- Incident detection and breach response services to help detect, understand, and respond to attacks at scale, in the cloud, and in remote / OT networks.
- Get expert help to use threat intelligence. Improve your detection methods and strengthen your response processes. This will make your team faster, more coordinated, and stronger during active threats.
Governance and Compliance
Robust governance guarantees the safe deployment, management, and retirement of IoT devices. Consistent controls, monitoring, and response readiness are required by industry rules, GDPR, HIPAA, and other compliance standards.
The Future Looks Bright for Emerging Technologies
IoT development can seem overwhelming, but enterprises can keep ahead of changing dangers with the proper partner and organized response tactics. As IoT ecosystems continue to grow, NetWitness Incident Response Service helps security teams remain resilient, respond more quickly, and gain trust.
Avoid Delays and Strengthen Response with NetWitness Guidance





