Threat Detection Trends 2026 Insights
- The industry has long moved beyond static alerting, and by 2026 continuous investigation has become the standard approach to cyber security threat detection and response.
- Generative AI will increase the speed of cyberattacks while simultaneously transforming the area of defensive automation.
- SOCs will rely on unified data – network, endpoint, cloud, identity – to cut dwell time.
- Exposure management, not just event detection, will drive early intervention.
- Organizations that integrate cyber threat detection investigation and response under one platform will lead.
Introduction
The rapid pace of cyber threats has outstripped the capability of many security teams to respond. By 2026, the gap will have widened even further. Teams are already stretched thin. Detection is getting more and more complex. Every environment – cloud, hybrid, OT, and SaaS – needs ongoing insight and context, as opposed to on-demand scanning.
Global investment shows the urgency of this pressure. Cybersecurity Ventures expects annual spending on security technologies to surpass $520 billion by 2026, which is nearly double of what organizations spent 5 years back. The takeaway is simple: risk is outpacing the ability of teams to keep up manually.
A modern operating model will place intelligence at its center. As organizations work across mixed environments, the current detect-and-alert model will be inadequate. The next step is an integrated threat detection, investigation, and response model utilizing automation, artificial intelligence, and human expertise.
This article explores cybersecurity predictions 2026, top seven threat detection and response trends that will shape the state of cybersecurity predictions 2026 and assist technical leaders in preparing for that future.
7 Trends Shaping the Future of Threat Detection and Response
1. AI Will Transform Both Cyber Attacks and Defenses by 2026
By the year 2026, sophisticated AI will fundamentally alter the tactics of attackers and the responses of defenders. Threat actors will make use of generative AI to execute targeted spear phishing campaigns, impersonate staff, and execute low-noise intrusions. This means defenders won’t be able to use only signatures or heuristics to defend against attackers.
The scale of AI’s dimension will be a shift of equal magnitude. For instance, a McKinsey study in 2025 revealed that AI will be expanding the cybersecurity total addressable market towards $2 trillion, underscoring how important intelligent automation will be in the future of threat detection and response.
The definition of a threat detection platform will evolve into one that incorporates behavioral analytics, identity signals, and automated investigation-related workflows. NetWitness is already leading this shift with a unified threat fabric that blends network, endpoint, and cloud visibility, an approach destined to become the industry norm after 2026.
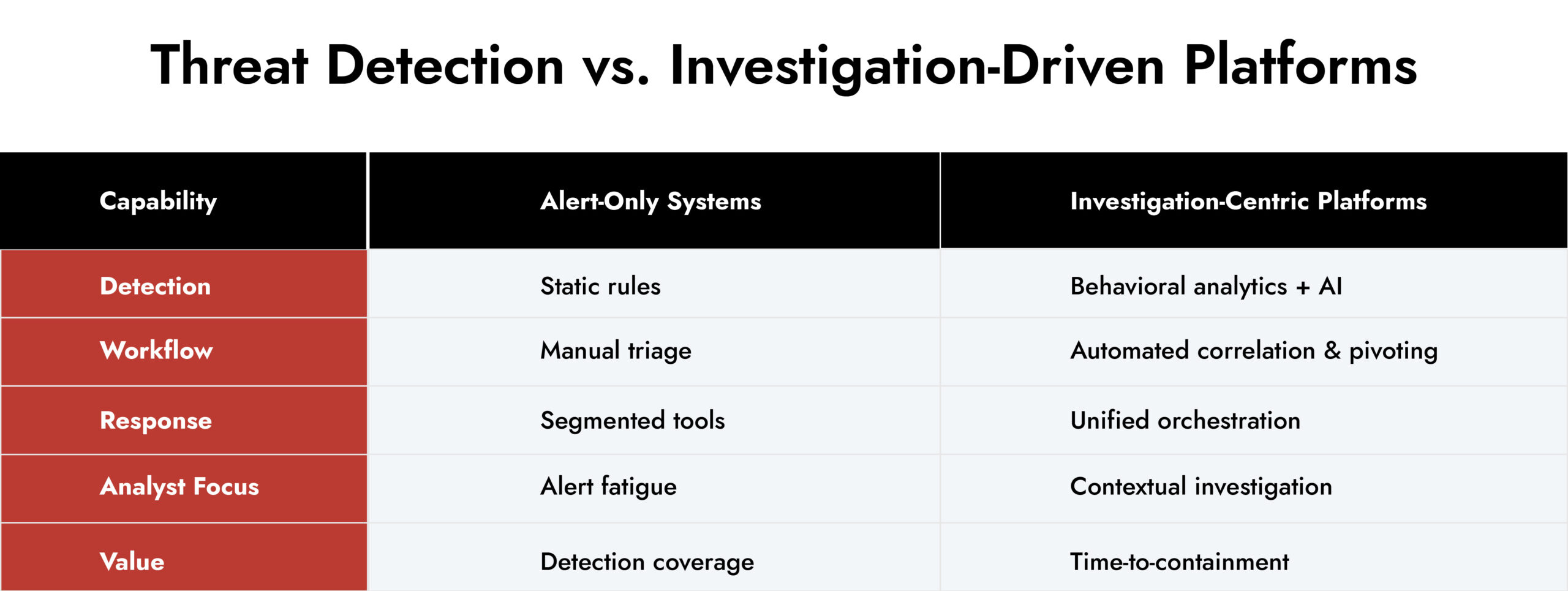
2. Threat Detection Platforms Will Develop into Full Investigation Engines
No later than 2026, the definition of “threat detection platform” will not be realistic for describing a platform that is not just an alert engine. The definition has grown into an ecosystem that supports investigations from the first indicator to containment. Gartner’s predictions for security operation tools in 2025 anticipate increased investment into capabilities that support investigation.
Modern SOCs demand platforms that provide data from endpoint, network, identity, and cloud in order to provide investigative capabilities. NetWitness’s unified threat detection architecture offers a platform for analysts to pivot swiftly across domains and work from one pane of glass.
3. Cloud, SaaS, and Edge Visibility will Define Detection Maturity
The traditional network perimeter is disappearing, and our detection model must change with this. By 2026, effective threat detection and response must have visibility to cloud workloads, SaaS applications, edge/OT devices, and network flows.
A sophisticated and capable threat detection platform is required to gather data from a variety of sources and correlate information across domains to identify lateral movement and identity misuse within cloud-native environments.
4. Continuous Exposure Management will Replace Traditional Scanning
Organizations will be moving to identify vulnerabilities proactively instead of waiting for the crisis to reveal them. Continuous Threat Exposure Management (CTEM) will evolve from periodic scans into real-time visibility.
Threat detection platforms will aggregate misconfiguration, identity, and privilege drift data into the detection workflows. This changes threat detection and prevention from a reactive practice into a proactive readiness engagement. 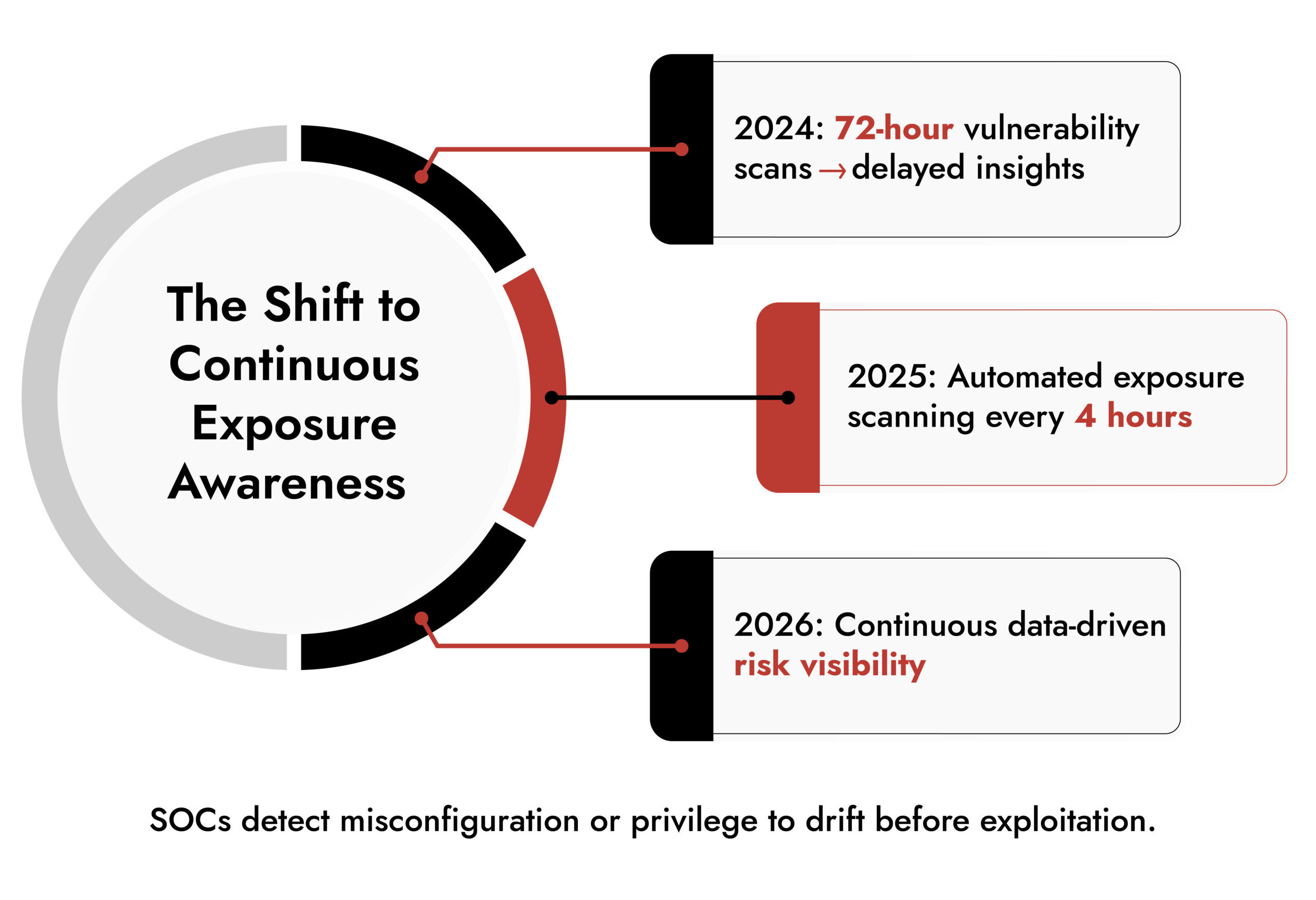 5. SOC Workflows Will Shift from Alerting to Forensic in One Motion
5. SOC Workflows Will Shift from Alerting to Forensic in One Motion
The traditional hand-off from detection to investigation to containment slows down response time. In a 2025 SOC survey by ISACA, teams that embedded investigation capabilities in detection tooling reduced time-to-contain by 38%.
In 2026, the best SOCs will value speed and context over the sheer volume of alerts. NetWitness’s investigation-first architecture brings detection and insider workflows together on a single platform, enabling containment and remediation cycles in less time.
6. OT and IoT Detection Will Become Required for Cyber Resilience
Industrial systems, IoT devices, and edge assets are no longer secondary, they are primary attack patterns.
By 2026 threat detection & response must ingest data from OT/IoT/edge domains and correlate this data with IT signals. If you have visibility gaps here, this is where adversaries will be exploiting those gaps. Make sure you have a plan to capture this domain now and not after the breach.
360° Cybersecurity with NetWitness Platform
– Unrivaled visibility into your organization’s data
– Advanced behavioral analytics and threat intelligence
– Threat detections and response actionable with the most complete toolset

7. Success of the SOC Will Be Measured by Metrics, Not Alert Volume
The era of measuring success by alert volume is over. More money and more tools won’t translate into better outcomes. By 2026, SOCs will be judged on business impact: MTTD, dwell time, and cost per incident avoided.
With cybersecurity spending surpassing $520B and AI pushing the market toward $2T, executives will expect detection platforms to prove efficiency and ROI, not empty alert counts.
To stay relevant, detection platforms must deliver business-aligned dashboards, forensic-grade workflows, and metrics that tie directly to outcomes. Anything less will be left behind.

Conclusion
2026 will be the year when detection, investigation and response converge – not just in theory but in practice. Trends we’ve seen show that AI-enabled threats and ongoing risk exposure are important. Unified visibility and metrics-driven SOCs also matter. These trends point to one key idea: successful outcomes depend on speed and context.
If your current strategy still focuses on alert volume or separate tools, you need to rethink your approach. Do an honest self-check of your investigation workflows. Identify where they are slow, where you lack visibility, and where metrics do not match business goals. Platforms like NetWitness are lighting the way: unified, investigation-centric with data.
You need to take action, and soon. Find the weak links now. Focus on the responses to these seven trends using your tools. Create your own workflow that covers detection and containment. You will be moving away from a reactive posture and towards a proactive one, and ahead of potential problems.
Frequently Asked Questions
1. What are the top cybersecurity trends for 2026?
Top trends will include using artificial intelligence for detection and response as a main approach. There will be autonomous response capabilities. There will be a focus on identities and credentials. Unified visibility will be important across cloud and on-premises domains. Continuous management of exposure will be a priority. Extensibility to edge, operational technology, and IoT environments will be key. A metrics-based approach will guide security operations centers.
2. How will AI impact threat detection and response by 2026?
AI will shift from assistive to foundational detection and response. Platforms will use AI to sort alerts, assign risk scores, suggest investigation paths, and start containment. This will reduce manual work and speed up responses.
3. Why is automation important in modern threat detection?
Human capacity has become incapable of managing the sheer volume and increasing sophistication of attacks. Automation is fundamental to improving detection capabilities, facilitating continuous response workflows and producing reliable outcomes. With automation, your SOC is better positioned to manage the volume and complexity of current threat environments.
4. How are SIEM, SOAR and NDR evolving?
These technologies’ convergence is taking place. Security Information and Event Management (SIEM) is now a solution that uses data and behavior to detect threats. Security Orchestration Automation Response (SOAR) is shifting to a framework for better investigation. Network Detection and Response (NDR) is growing into a system that provides visibility across networks, clouds, and edge devices. Together, these entail a tightly integrated ecosystem for threat detection and response.
5. What are the five main threats to cyber security today?
The top five threats are misuse of credentials and identities, generative AI phishing, and manipulation of judgment. They also include misconfigurations and drift in cloud accounts, infiltration of operational technology, IoT, and edge devices. Lastly, there are automated attacks that mix advanced techniques with social engineering.




