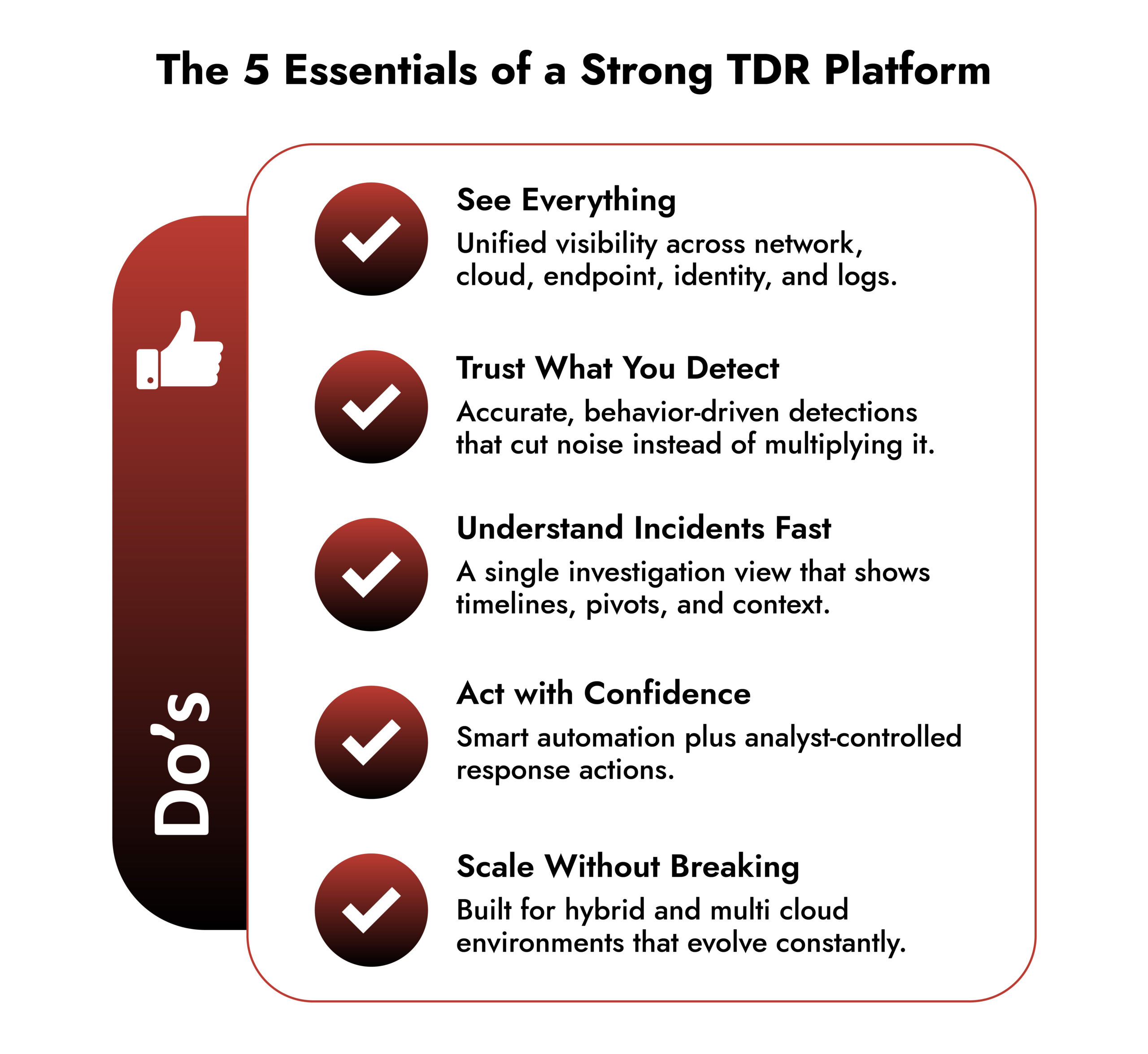
Quick Takeaway for Buyers
• Look for a TDR tool that cuts noise instead of multiplying alerts.
• Choose the platform that shows you what’s happening, not what might be happening.
• Pick the solution that makes investigations faster, not harder.
• Go with the tool that fits into your stack without forcing redesigns.
• Select the vendor that proves value early, not after months of tuning.
Security teams are drowning in alerts. The average SOC analyst faces thousands of signals daily, and most turn out to be false positives. Meanwhile, real threats slip through the cracks because traditional rule-based systems can’t keep up with sophisticated attackers.
This is where modern threat detection and response solution come in. But here’s the thing: not all TDR platforms are created equal. Some promise the moon and deliver noise. Others integrate poorly with your existing stack. And many require so much manual tuning that your team spends more time maintaining the tool than hunting threats.
So how do you cut through the marketing speak and find a threat detection and response solution that actually works? Let’s break it down with a practical checklist based on what matters most.
Understanding Threat Detection Methods
Before diving into your buying guide for threat detection, you should know the four main methods of threat detection that modern platforms use:
Signature-based detection looks for known malware patterns. It’s fast and reliable for documented threats but useless against zero-day attacks.
Anomaly-based detection establishes baseline behavior and flags deviations. This catches novel threats but can generate false positives if not properly tuned.
Behavioral analysis monitors how users, applications, and systems actually behave over time. It spots subtle patterns that indicate compromise, even when attackers use legitimate credentials.
Threat intelligence compares your network activity against external databases of known threat actors, IOCs, and attack patterns.
The best threat detection platforms combine all four methods. But behavioral analysis powered by AI is quickly becoming the differentiator that separates effective solutions from legacy ones.
Core Features to Demand in Your TDR Solution
When you’re building your threat detection solution checklist, these capabilities should be non-negotiable:
Behavioral Analytics for Detection
Traditional signature-based tools miss what they don’t recognize. Behavioral analytics changes the game by learning what normal looks like in your environment and spotting deviations that indicate compromise.
What this really means is: the system gets smarter over time without constant manual rule updates. It detects lateral movement, credential abuse, and low-and-slow attacks that rule-based systems miss entirely. If a product doesn’t have genuine AI behavioral analytics (not just pattern matching labeled as AI), keep looking.
Insider Threat Detection and Response
External attackers get most of the headlines, but insider threats cause serious damage. Your identity threat detection and response solutions need to monitor user behavior for both malicious actors and well-meaning employees who accidentally create risk.
This means tracking access patterns, data exfiltration attempts, privilege escalation, and unusual activity times. The system should differentiate between a developer pulling data for legitimate work and someone downloading sensitive files they never accessed before right before their exit interview.
Behavioral Indicators of Compromise
Here’s where context matters. Instead of generic alerts saying “suspicious login detected,” you need high-quality behavioral Indicators of Compromise that correlate multiple anomalies. For example: a user logs in from a new location, accesses systems they rarely use, then attempts lateral movement to financial databases.
Context-aware detection dramatically reduces the time from detection to remediation because your SOC team immediately understands the threat instead of investigating each signal separately.
Automatic False Positive Reduction
Alert fatigue kills SOC efficiency. When analysts spend 80% of their time chasing false positives, they burn out fast and real threats get missed.
Look for threat detection and response tools that use AI to automatically filter noise. The system should learn what’s actually risky in your environment versus what’s just unusual but harmless. This single feature can transform SOC workload from overwhelming to manageable.
Integration: The Make-or-Break Factor
Should TDR solutions integrate with other security tools? Absolutely. In fact, integration capabilities might be the most important item on your checklist.
A threat detection and response platform that sits in isolation is nearly worthless. You need seamless connections to your SIEM, endpoint protection, identity management, and cloud security tools. Otherwise, you’re creating information silos that prevent comprehensive threat visibility.
Pay special attention to how well solutions integrate with your existing infrastructure. If you’re heavily invested in Microsoft tools, for example, look for platforms that connect effortlessly with Microsoft Defender, Entra ID, and Azure Sentinel. This maximizes your existing investments while streamlining operations.
Ask vendors specific questions about integration effort. How long does implementation take? What APIs are available? Can the system automatically ingest and correlate data from your other security tools? If they dodge these questions, that’s a red flag.
360° Cybersecurity with NetWitness Platform
– Unrivaled visibility into your organization’s data
– Advanced behavioral analytics and threat intelligence
– Threat detections and response actionable with the most complete toolset

SOC Efficiency: From Theory to Practice
How can a TDR solution improve SOC efficiency? Here are the practical ways that matter:
Process automation eliminates repetitive tasks. Your system should automatically enrich alerts with context, correlate related events, and even trigger initial response actions without human intervention.
High-context, natural language alerts mean junior analysts can understand and act on threats without escalating everything to senior staff. Instead of “Event ID 4625 detected on host,” you get “Finance manager attempted failed logins to HR database from unrecognized device.”
Adaptability without constant tuning keeps the system effective as your organization changes. New employees, applications, and infrastructure shouldn’t require manual reconfiguration. The system should automatically learn and adjust.
Proactive threat detection shifts your stance from reactive to preventive. By identifying threats before they escalate, you stop incidents instead of just responding to them.
Deployment and Ramp-Up Reality Check
Ease of deployment matters more than vendors admit. Some “comprehensive” solutions take six months to properly configure and require dedicated staff just to maintain.
Look for platforms that offer quick time-to-value. You should see meaningful threat detection within weeks, not quarters. Minimal disruption during onboarding means your existing security operations continue functioning while the new system comes online.
Ask about threat detection training too. Does the vendor provide real guidance or just documentation? Will they help your team learn the platform, or are you on your own after installation?
Value Beyond the Base Product
The best vendors offer value-add services that extend your team’s capabilities: advanced threat hunting expertise, proactive support, tailored implementation, and ongoing optimization. These services shouldn’t feel like upsells but rather like genuine partnerships to maximize your security posture.
Cost Efficiency: Total Ownership Matters
Price tags mislead. A cheaper solution that requires three full-time staff to maintain costs more than a pricier platform that runs itself. Consider total cost of ownership: licensing, implementation, training, maintenance, and ongoing operational overhead.
The right threat detection solution should reduce overall security costs by improving efficiency, preventing incidents, and maximizing your existing tool investments.
Making Your Decision
Start by documenting your current pain points. Are you drowning in false positives? Missing insider threats? Struggling with tool integration? Unable to detect advanced persistent threats?
Use this as your foundation for building a threat detection solution checklist specific to your needs. Then evaluate vendors against concrete criteria, not marketing promises. Request proof-of-concept deployments in your actual environment. Test the integration claims. Measure false positive rates. Get your SOC team’s honest feedback before committing.
For large, complex enterprises dealing with massive data volumes and sophisticated threats, solutions like NetWitness Threat Detection & Response offer capabilities specifically designed for scale.
Why is NetWitness the Right TDR Solution For You?
NetWitness excels at full spectrum visibility through unified data collection from network traffic, endpoint telemetry, cloud environments, and threat intelligence sources. The platform’s unified system impact analysis reconstructs complete attack timelines, showing lateral movement, privilege escalation, and data exfiltration across your entire infrastructure. With lightweight agent architecture, rapid incident correlation, and security orchestration that automates routine tasks, NetWitness delivers the intelligent hunting capabilities and streamlined workflows that make complex investigations manageable for enterprise SOCs.
Conclusion
Choosing the right platform isn’t about finding the most features or the biggest name. It’s about finding the solution that makes your security team more effective at the job they’re already doing. The best threat detection and response tools work so well that they become invisible infrastructure your team relies on without constantly fighting against.
Frequently Asked Questions
1. How to choose a threat detection solution?
Assess your security needs and existing infrastructure, then evaluate solutions based on detection accuracy, integration capabilities, and false positive rates. Request proof-of-concept testing in your environment and prioritize platforms with AI behavioral analytics, automatic false positive reduction, and seamless integration with your current security stack.
2. What are the 4 methods of threat detection?
The four methods are signature-based detection (known malware patterns), anomaly-based detection (deviations from baseline), behavioral analysis (monitoring user and system behavior), and threat intelligence (comparing against known threat databases). Modern platforms combine all four, with behavioral analysis becoming crucial for sophisticated attacks.
3. What core features should a buyer look for in a TDR solution?
Essential features include AI behavioral analytics, insider threat monitoring, behavioral indicators of compromise with contextual correlation, automatic false positive reduction, seamless security tool integration, process automation, natural language alerts, and adaptability without constant manual tuning.
4. How can a TDR solution improve SOC efficiency?
TDR solutions improve efficiency through process automation, intelligent false positive filtering, contextual alerts that speed investigations, proactive threat detection, and unified visibility across data sources. This reduces alert fatigue, eliminates manual correlation tasks, and lets analysts focus on genuine threats.
5. Should TDR solutions integrate with other security tools?
Yes, integration is critical. Isolated TDR solutions create information silos and limit threat visibility. Look for platforms that connect with your SIEM, endpoint protection, identity management, cloud security tools, and threat intelligence feeds to maximize existing investments and detect sophisticated multi-system attacks.




