When a sophisticated adversary manages to breach your perimeter, preventive controls alone won’t stop the damage. That’s why threat detection and response remain one of the most critical pillars of enterprise cybersecurity.
By applying continuous monitoring, analytics and automated reactions, organizations gain visibility into what’s happening in real time and the ability to act before the attacker completes their mission. What this really means is you shift from being passive to actively controlling the window of opportunity attackers have.
In the sections that follow, we’ll break down what threat detection and response actually involve, what makes them effective and how you can build or optimize them in your environment.
What is Threat Detection and Response?
Threat detection and response refer to the set of capabilities, processes and technologies that monitor indicators of compromise or malicious activity, analyze them for severity and context, and enable timely mitigation or containment.
In practice, it spans the lifecycle of an attack: detection → investigation → containment → remediation → recovery.
Organizations deploy a threat detection platform (or solution) to collect telemetry across endpoints, networks and logs; apply analytics (behavioural, statistical, and threat-intelligence driven); generate alerts or findings; and trigger response actions. Response may include isolation, blocking, forensic capture, or workflow hand-off to incident response teams.
According to industry research, many organizations struggle with dwell time and detection coverage, highlighting why threat detection and response must be actively managed rather than assumed.
Why does Threat Detection and Response matter now?
Because your attack surface is bigger than ever: cloud infrastructure, remote work, hybrid networks, encrypted traffic and insider threats. And the adversary doesn’t wait for you to patch, update or build a fresh strategy. What matters is how quickly you detect, analyze and respond.
Here are key reasons:
- Attackers often operate inside your network for days or weeks before being spotted. Without effective detection and response, you give them free reign.
- Detection alone isn’t enough, response is the multiplying factor that turns visibility into action.
- Regulatory pressures, ransomware economics and shift-left security require you to prove not just prevention but detection and response capability.
- Technology stocks are increasingly complex; visibility gaps exist. A mature threat of detection and response posture helps close those gaps.
In short, if your controls fail (and they will), your ability to detect and respond fast becomes your defining security capability.
What Components Make up a Threat Detection and Response Capability?
A complete threat detection and response capability comprises data collection, analytics and detection, investigation workflows, response orchestration, and feedback loops for improvement.
Let’s break that down:
1. Data collection and visibility
- Telemetry from endpoints (process, registry, file changes)
- Network traffic capture (including metadata, full-packet capture)
- Log and event ingestion from identity, cloud, applications, network devices
- Threat intelligence feeds and context enrichment
A recent white paper noted organisations capturing full-packet and endpoint behavioural analytics improve detection of advanced threat actors.
Visibility without collection is blind.
2. Analytics and detection
- Behavioural analysis (deviations from normal baselines)
- Threat-intelligence correlation (known adversary tools/TTPs)
- Statistical anomaly detection and machine learning
- Rule-based signature detection where appropriate
For example, network detection solutions highlight full-packet capture plus behavioural analytics as key features.
What counts: high-fidelity alerts with low noise.
3. Investigation and triage
- Alert enrichment with context (asset, user, risk profile)
- Session reconstruction or process tree building to trace kill chain
- Forensic data capture for deeper analysis or legal/insurance requirements
A study showed many organisations lacked the ability to investigate attacks very quickly.
Speed and clarity matter.
4. Response orchestration and action
- Automated or manual containment (isolate host, block traffic)
- Workflows for remediation, user notification, legal/regulatory containment
- Integration with broader security stack (SIEM, SOAR, endpoint security, network detection)
The “response” element means you don’t just observe, you act.
5. Continuous improvement
- Post-incident review: what worked, what missed
- Tune detection rules, adjust workflows
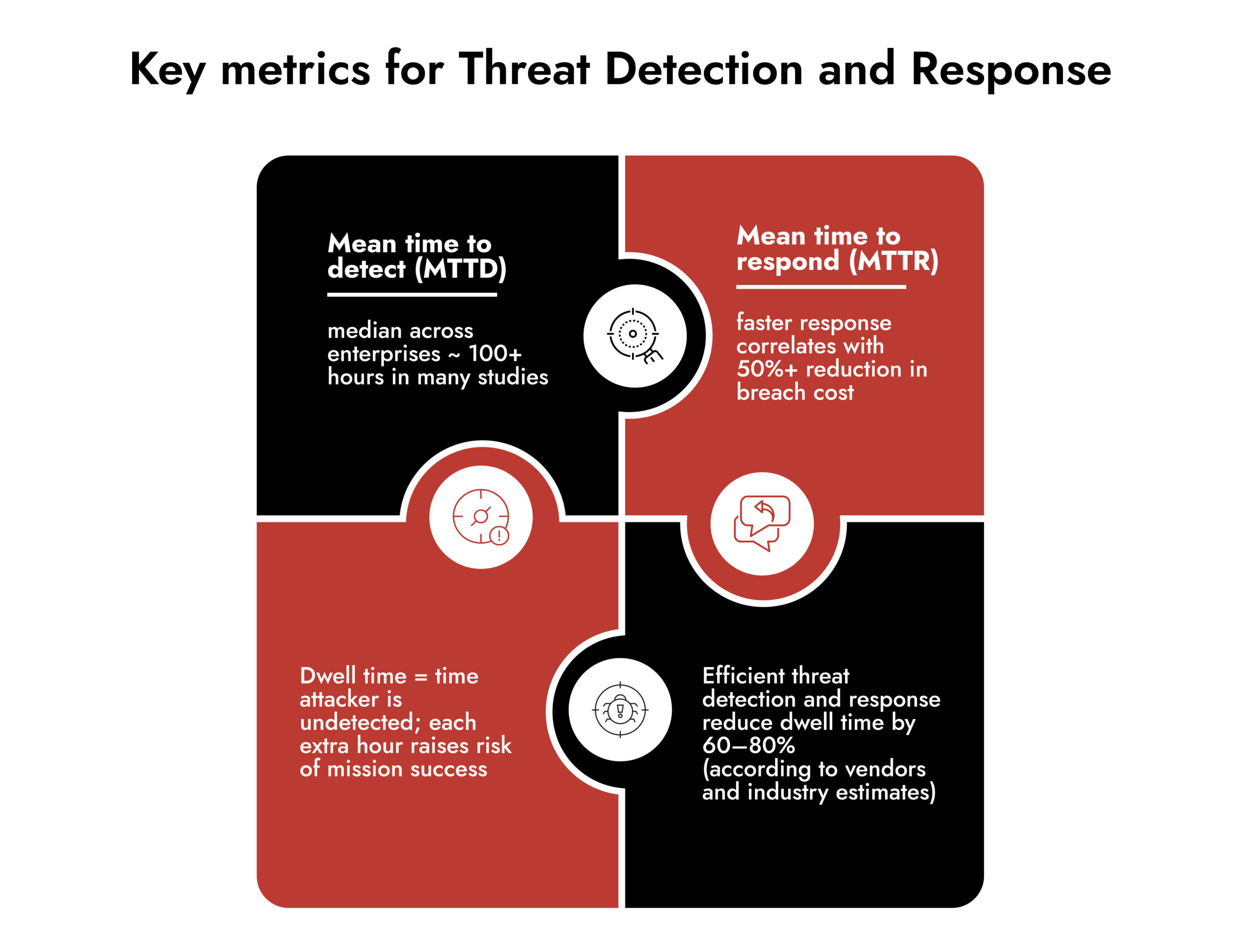
- Metrics: mean time to detect (MTTD), mean time to respond (MTTR), dwell time
Without improvement, your threat detection and response capability stagnates.
The faster you detect and respond, the less time the attacker has, and the less damage they can do.
What types of Threat Detection Solutions exist and how do they differ?
There are multiple styles of threat detection tools – endpoint detection and response (EDR), network detection and response (NDR), log-/event-based analytics and full-stack threat detection platforms. Each covers a different slice of visibility and together they form a comprehensive approach.
Here’s a breakdown:
| Solution type | Primary focus | Strengths |
| EDR (Endpoint Detection & Response) | Host-based telemetry, process, user behaviour | Good for detecting compromised devices, insider threats |
| NDR (Network Detection & Response) | Network traffic, full-packet capture, metadata | Strong for lateral movement, encrypted traffic, hidden adversaries |
| SIEM/Log analytics | Aggregated logs/events from apps, identity, infrastructure | Useful for correlation across the stack and compliance |
| Threat detection platform (holistic) | Unified visibility across endpoints, network, logs | Enables broad detection and response from one pane |
When you combine these, you strengthen your unified threat detection and response posture. For example, you might catch a compromised host via EDR and then use NDR to trace lateral movement while your SIEM correlates with suspicious login events.
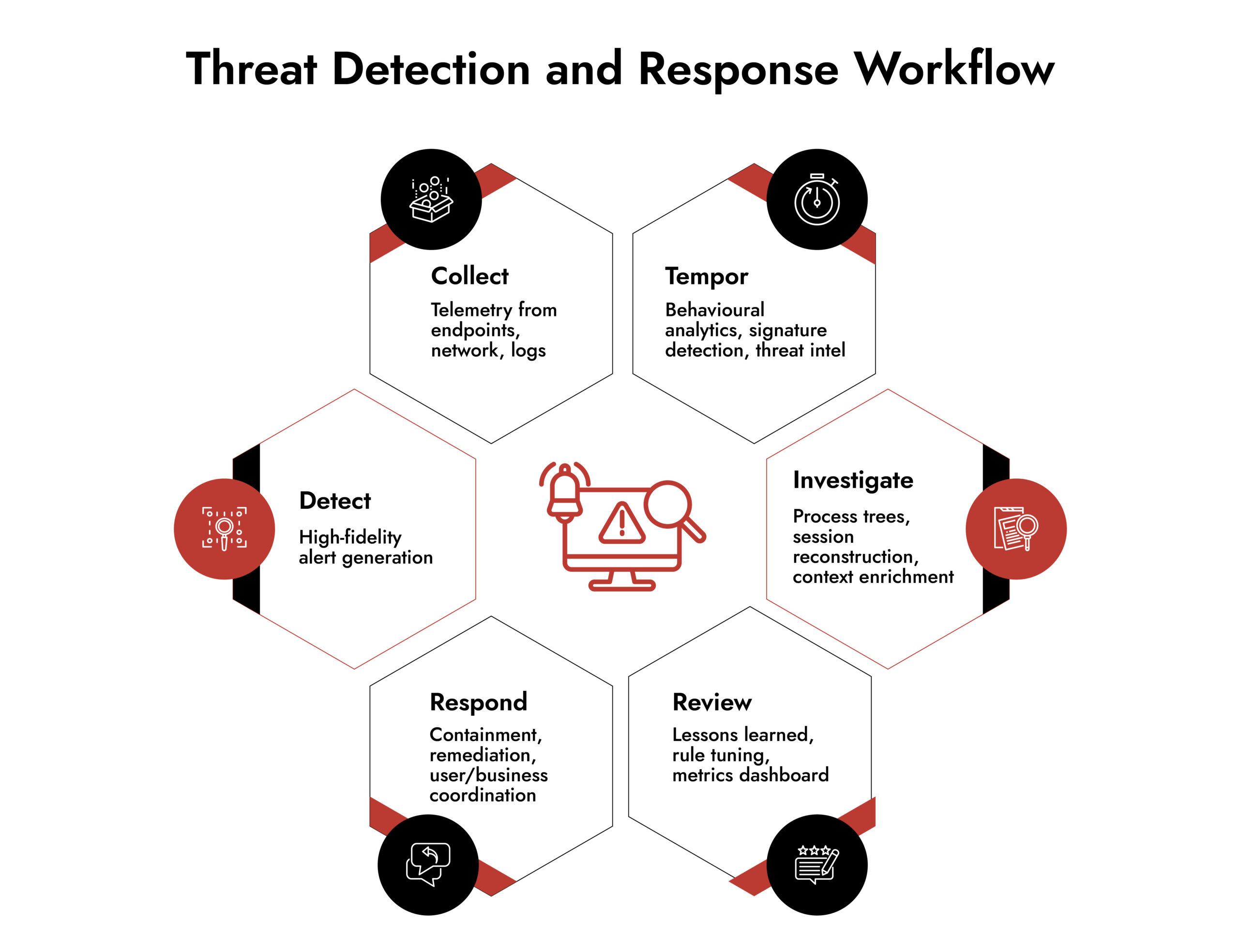
This workflow highlights that threat detection and response are not linear but iterative. You loop back to improve.
How to Evaluate or Build a Threat Detection and Response Program?
If your goal is to strengthen threat detection and response, here are practical steps:
- Assess visibility gaps. Map what telemetry you lack (e.g., east-west network traffic, cloud workload logs, off-network endpoints).
- Define key metrics. Choose MTTD, MTTR, number of alerts requiring manual investigation, and detection coverage.
- Select appropriate tooling. Ensure your threat detection platform, tools or services offer endpoint, network and log coverage, analytics and rapid response workflows.
- Integrate workflows. The tools must feed into investigation, orchestration and remediation processes. Tooling alone won’t suffice.
- Build investigation capability. Train analysts to use context, trace kill chains, reduce noise and focus on real threats.
- Run simulations and measure outcomes. Use tabletop exercises or red/purple team testing to validate detection and response capability.
- Continuous improvement. Post-incident reviews must feed into tuning of detection logic, response playbooks and tool configurations.
An important insight: many organizations underestimate the challenge of setting up threat detection and response capability. It isn’t just about buying a “solution” but aligning people, processes, technology and measurement.
What to watch out for
- Alert fatigue: Too many false positives reduce trust in the system and slow response.
- Coverage gaps: Missing telemetry (e.g., cloud workloads, encrypted traffic) means blind spots.
- Slow investigation: If investigation takes hours or days, the attacker will already have moved.
- Fragmented tooling: If EDR, NDR, logs, SIEM and SOAR don’t integrate, the hand-off between detection and response breaks down.
- Reactive posture: Treating detection and response as an afterthought means you’ll fall behind the adversary’s pace.
Monitoring these risks will keep your threat detection and response program pragmatic and aligned with business risk.
360° Cybersecurity with NetWitness Platform
– Unrivaled visibility into your organization’s data
– Advanced behavioral analytics and threat intelligence
– Threat detections and response actionable with the most complete toolset

Conclusion
Effective threat detection and response give you the ability to spot attacker activity as quickly as possible, move from visibility to action and continuously improve your defensive posture. Investing in telemetry, analytics, investigation of workflows and response orchestration isn’t optional, it’s mandatory if you want to reduce dwell time and minimize damage. As you build or evolve in your program, keep the workflow tight, metrics visible and improvement ongoing. If you’d like to explore how to align your detection and response capability with your enterprise risk profile, let’s talk.
Frequently Asked Questions
1. What is threat detection and response?
Threat detection and response refer to the combined capability of monitoring for malicious activity, investigating it and executing structured responses to mitigate or remediate threats.
2. Why are threat detection and response important?
It’s important because preventive controls alone cannot block all attacks, and long attacker dwell time increases the risk of mission success. A strong threat detection and response capability reduces dwell time and loss.
3. What technologies are used for threat detection and response?
Technologies include endpoint detection tools (EDR), network detection solutions (NDR), log/event analytics (SIEM), threat-intelligence feeds, behavioral analytics, full-packet capture and response orchestration platforms.
4. How does threat detection differ from incident response?
Threat detection focuses on identifying malicious activity and generating alerts; incident response covers the actions taken after detection to contain, remediate and recover from the incident. They are complementary parts of the same lifecycle.
5. What are common use cases of threat detection and response?
Use cases include detecting insider threats, spotting lateral movement, catching living-off-the-land tools, uncovering cloud workload compromise, investigating ransomware early and rapidly containing advanced persistent threats.