5 Routine Checks for Incident Response Management
- Tune detection tools to align with your incident detection and response process.
- Review your incident response retainer for clarity and speed of activation.
- Rehearse roles and communication protocols within your incident management response team.
- Validate forensic data sources – endpoint, network, and logs – for accessibility and retention.
- Conduct lessons-learned reviews to refine your security incident response process.
Introduction
No organization is ever completely safe from cyber threats. Attackers adapt faster than most defenses, and the difference between minor disruption and major damage often comes down to one thing: how strong your incident response management really is.
The companies that recover quickly aren’t always the ones with the biggest budgets, they are the ones that test, refine, and evolve their response processes as rigorously as their detection capabilities.
Here is how the best teams stay a few moves ahead of attackers through five essential checks.
Five Checks Every IR Team Should Run
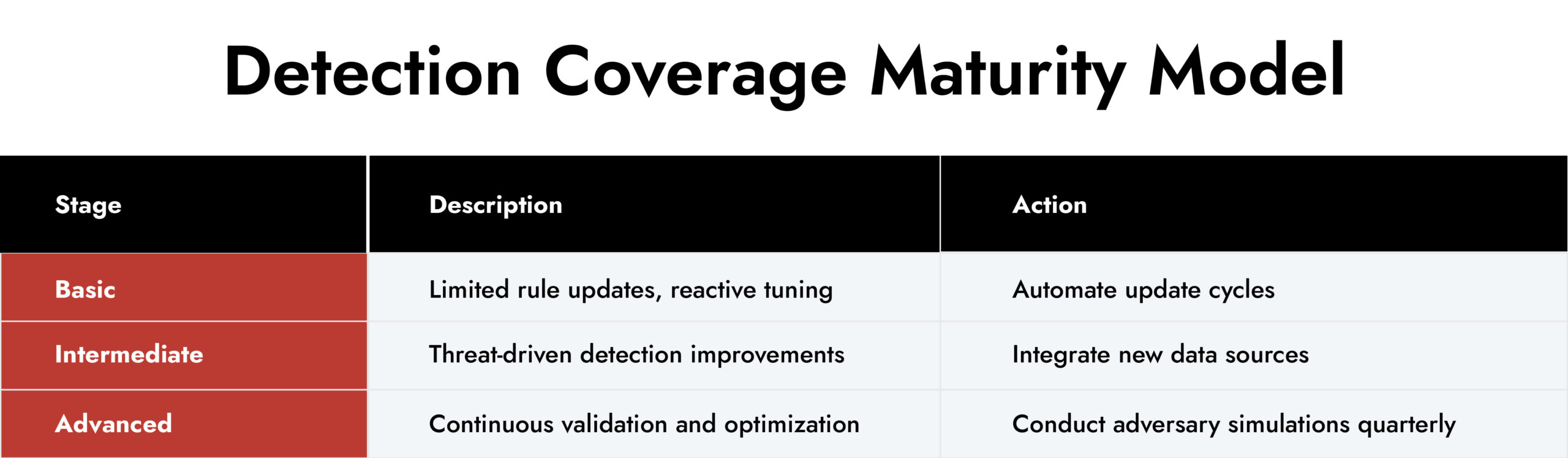
Check 1: Threat Detection Coverage
Visibility is the foundation of incident detection and response. You can’t respond to what you can’t see. Routine audits ensure that detection rules, log sources, and telemetry pipelines are current and actually working. Regular compromise assessments can be the best way to validate the effectiveness of these platforms and processes.
Start by actively hunting for anomalous behaviors as seen by your NDR, SIEM, and EDR platforms, validating your network and endpoint data sources, ensuring full coverage across on-premises, hybrid, and cloud environments. Then, map those detections against frameworks like MITRE ATT&CK to find blind spots, missing data sources, or outdated rules.
Teams that consistently hunt attackers and tune detection coverage accordingly can identify anomalies before they escalate into breaches.
Quick actions:
- Conduct regular compromise assessments and detection validation exercises
- Map alerts and detections to MITRE ATT&CK tactics
- Update log sources, and rules, parsers based on findings and any gaps
- Review and decommission obsolete correlation rules
- Integrate threat intelligence to remain up-to-date on the latest APT’s
Check 2: Response Process Relevance
A well-defined security incident response process loses value if it’s outdated. Threat patterns evolve quickly – ransomware, phishing, and supply chain attacks do not look like they did a few years ago.
Regularly update your response processes to reflect new tactics, new stakeholders, and updated communication protocols. Each revision should include the latest:
- Threat landscape for your organization
- Mitigations to the latest attacker TTP’s
- Escalation paths are accurate and current
- Regulatory and legal steps are aligned with recent compliance changes
- External contact lists (partners, law enforcement, IR retainers) are verified
When incident response processes evolve alongside the threat landscape, incident response teams can act fast without improvising under stress.
Check 3: Team Readiness and Training
Even the best detection systems fail if the team behind them isn’t prepared. Routine, realistic training ensures your incident management response team can handle high-pressure incidents with coordination and confidence.
Tabletop exercises and Red Team – Controlled Attack and Response simulations expose gaps in communication, escalation, and containment strategies. They also reinforce muscle memory, so analysts know exactly what to do when alerts spike or an active breach occurs.
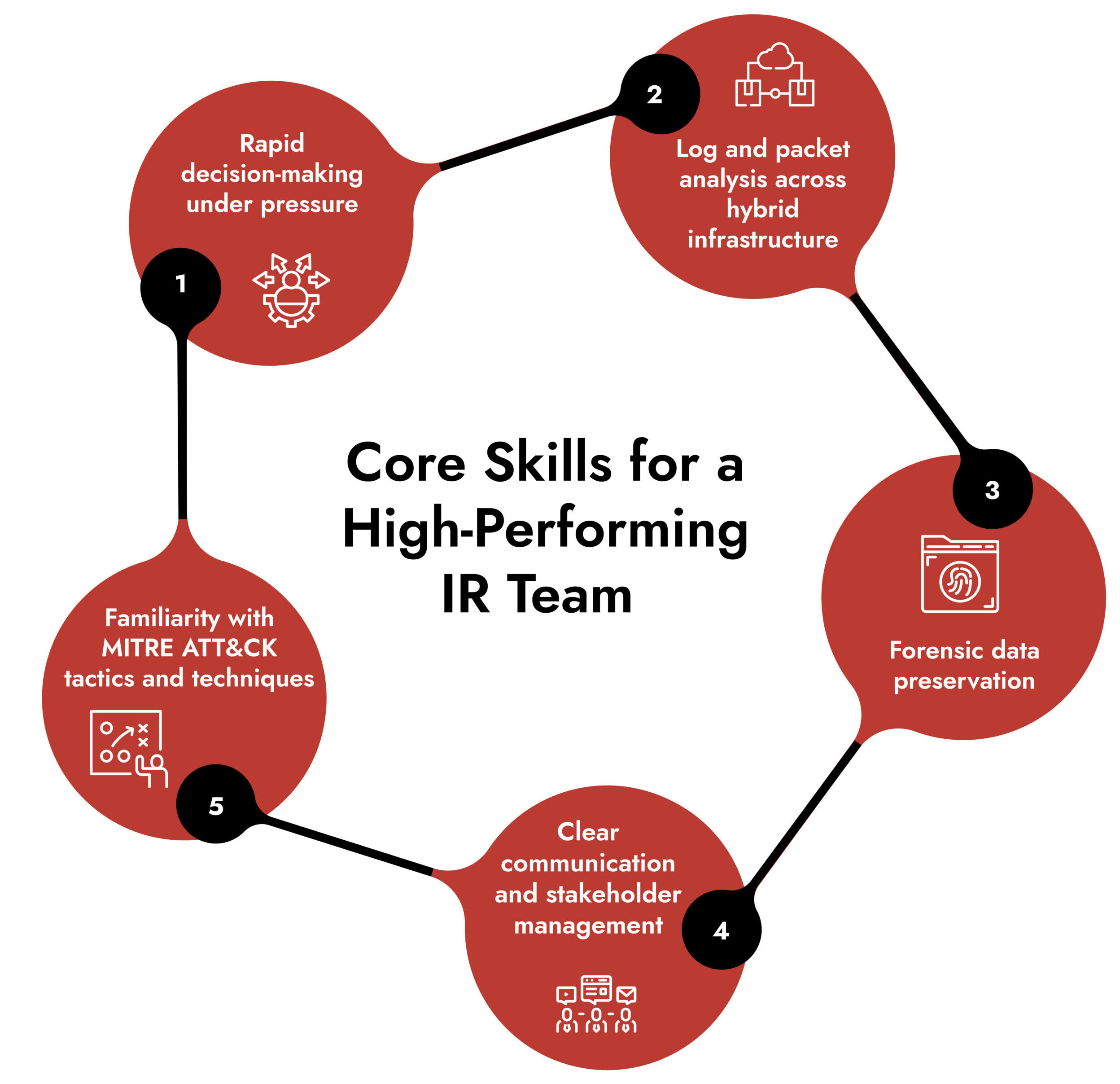
Practicing against real world attack scenarios is the best way to baseline and improve incident response program performance. Make training a habit, not an event. Continuous improvement is the only real guarantee of readiness.
Check 4: Containment and Recovery Speed
Fast detection means little without fast containment. Measuring and improving Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR) helps determine how quickly your team can isolate and remediate threats.
In many cases, organizations maintain an incident response retainer with a specialized incident response company. This ensures that when an attack happens, expert responders can step in immediately, bringing the experience and perspective needed to reduce downtime and data loss.
To stay ahead, make sure you have a trusted 3rd party on retainer so you can surge resources when time is of the essence and expertise can make the difference.
Check 5: Post-Incident Learning and Optimization
A strong cybersecurity incident management program closes the loop after every event. Post-incident reviews aren’t just about documenting what went wrong, they’re about identifying where improvements will have the biggest impact.
Each review should include:
- Missed indicators and response bottlenecks
- Incident response Process adherence and deviations
- Communication gaps during escalation
- Recommendations for new detections, controls, or automations
The goal is continuous refinement. Every alert, incident, or near-miss becomes an opportunity to strengthen your future response posture.
Rapid, Expert Response with NetWitness® Incident Response Services
-Accelerate threat containment with experienced IR specialists.
-Investigate effectively using advanced forensics and analytics.
-Minimize business impact with fast, guided remediation.

Building Long-Term Resilience with NetWitness IR
When time is critical, experience matters most. NetWitness Incident Response service helps organizations investigate, contain, and recover from cyberattacks with speed and precision, backed by years of threat intelligence and forensic expertise.
NetWitness IR provides:
- Services for incident detection and breach of response that assist in identifying, comprehending, and addressing large-scale, on premise, cloud-based, and remote/OT network attacks.
- In-depth knowledge of cybersecurity, incident response, networks, and host technologies to develop your security monitoring program or SOC in a comprehensive manner.
- Testing, assessment, and education to improve the effectiveness of your whole security ecosystem, with full-scope, objective-led, adversarial simulations that replicate the tactics, methods, and procedures (TTPs) of actual threat actors.
Beyond immediate crisis response, NetWitness helps security teams evolve their programs – updating processes and playbooks, improving detection coverage, and training teams to quickly and appropriately respond in today’s modern hybrid environments.
In short, it’s not just about recovering from incidents, it’s about building resilience before the next one.
Conclusion
Attackers exploit routine weaknesses: missed updates, outdated playbooks, and slow responses. Performing these five checks – on detection coverage, incident response process relevance, team readiness, containment speed, and post-incident learning – keeps your incident response management program proactive instead of reactive.
The more often you test and refine, the fewer surprises you’ll face when an incident hits.
Want to strengthen your organization’s response readiness? Explore how NetWitness Incident Response can help your team detect, contain, and recover faster while building long-term resilience.
Frequently Asked Questions
1. What is incident response management?
Incident response management is the organized process of evaluating how your security program identifies, contains, eradicates, and recovers from cybersecurity incidents. It ensures faster decision-making, minimal damage, and continuous improvement in defense capabilities.
2. What are the five checks for incident response management?
They include validating detection coverage, reviewing response processes, strengthening team readiness, measuring containment speed, and driving continuous post-incident improvement.
3. How does incident response management help stay ahead of attackers?
It shortens the gap between detection and containment, limits attacker dwell time, and strengthens organizational readiness. Over time, this builds resilience and reduces the overall impact of cyber threats.
4. What role do incident response services play?
Incident response Service providers can help increase your response speed and effectiveness by quickly surging highly experienced DFIR resources when you need them the most. The best IR providers can also help with proactive monitoring, process updates, testing and training to help improve security program maturity.




