Enterprise networks generate an immense volume of data every second. Hidden within this constant flow of packets are critical security indicators – unauthorized access attempts, malicious communications, and insider threats that traditional perimeter defenses often lack. Network traffic analysis transforms this raw network data into actionable intelligence, providing security teams with the visibility needed to detect, investigate, and respond to sophisticated cyber threats.
What is Network Traffic Analysis?
At its core, network traffic analysis is the systematic process of capturing, monitoring, and interpreting network communications to identify anomalies, detect threats, and optimize performance. It goes far beyond simple up/down status checks or packet sniffing.
Rather than examining every packet capture, network traffic analysis focuses on metadata like IP addresses, ports, protocols, and traffic volume, and uses analytics and machine learning to detect unusual patterns.
These deviations often reveal the earliest signs of malicious activity:
- An employee’s credentials used from an unusual geography.
- Data leaving the network at odd hours in unexpected volumes.
- Devices establishing hidden connections with suspicious domains.
Put simply, NTA transforms routine traffic into actionable intelligence.
Key Benefits of Network Traffic Analysis
1. Faster Threat Detection:
Traditional tools struggle for threat detection like advanced persistent threats (APTs) or insider abuse because these threats blend into legitimate traffic. NTA narrows the mean time to detect incidents by spotting subtle anomalies invisible to endpoint or perimeter defenses.
2. Stronger Forensics and Incident Response:
When a breach occurs, NTA provides the historical record needed to reconstruct attacker behavior. Analysts can trace lateral movement, compromised accounts, and data flows with precision, cutting investigation times significantly.
3. Compliance and Audit Readiness:
Frameworks like PCI DSS, HIPAA, and GDPR emphasize continuous monitoring and thorough logging of activity within sensitive environments. While they don’t specifically require network capture, tools like NTA make it easier to meet these obligations by providing tamper-resistant visibility and verifiable audit trails.
4. Operational Insights Beyond Security:
Security leaders gain unexpected value: identifying bandwidth hogs or reducing unnecessary cloud costs. For many enterprises, this dual benefit helps justify investment.
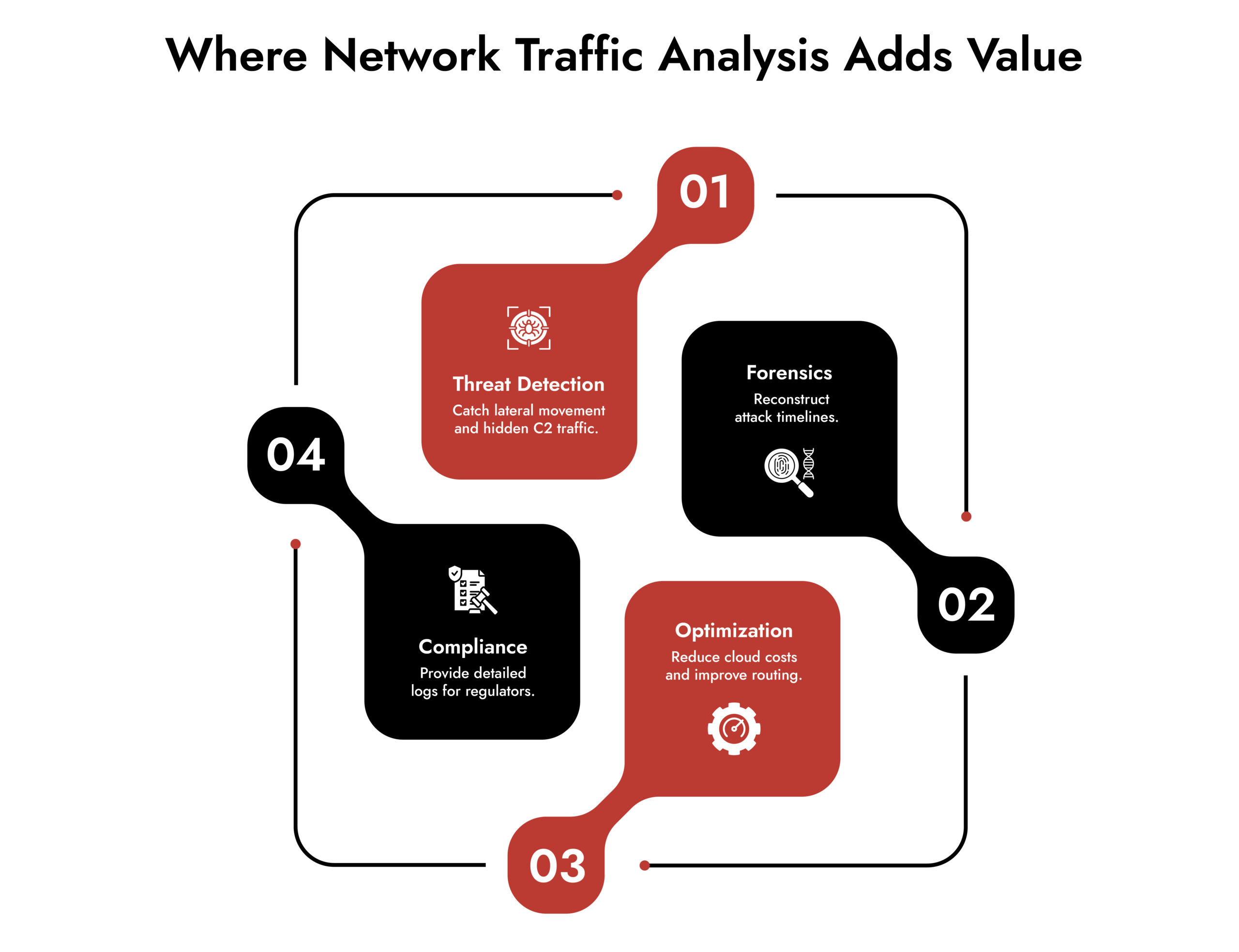
Real-World Use Cases for Network Traffic Analysis
- Detecting Lateral Movement: Attackers who breach one endpoint often spread quietly. NTA identifies unusual east-west traffic between internal servers, revealing these movements.
- Spotting Data Exfiltration: Whether through unauthorized file transfers or hidden tunneling, NTA surfaces data leaving the network that shouldn’t.
- Exposing Command-and-Control Traffic: Communications with foreign rogue servers usually leave signatures of flow patterns even when encrypted.
- Performance and Optimization: Network traffic analysis enables the IT teams to identify the potential areas of congestion and underutilized assets and enhance the cost and user experience.
How Network Traffic Monitoring Tools Work?
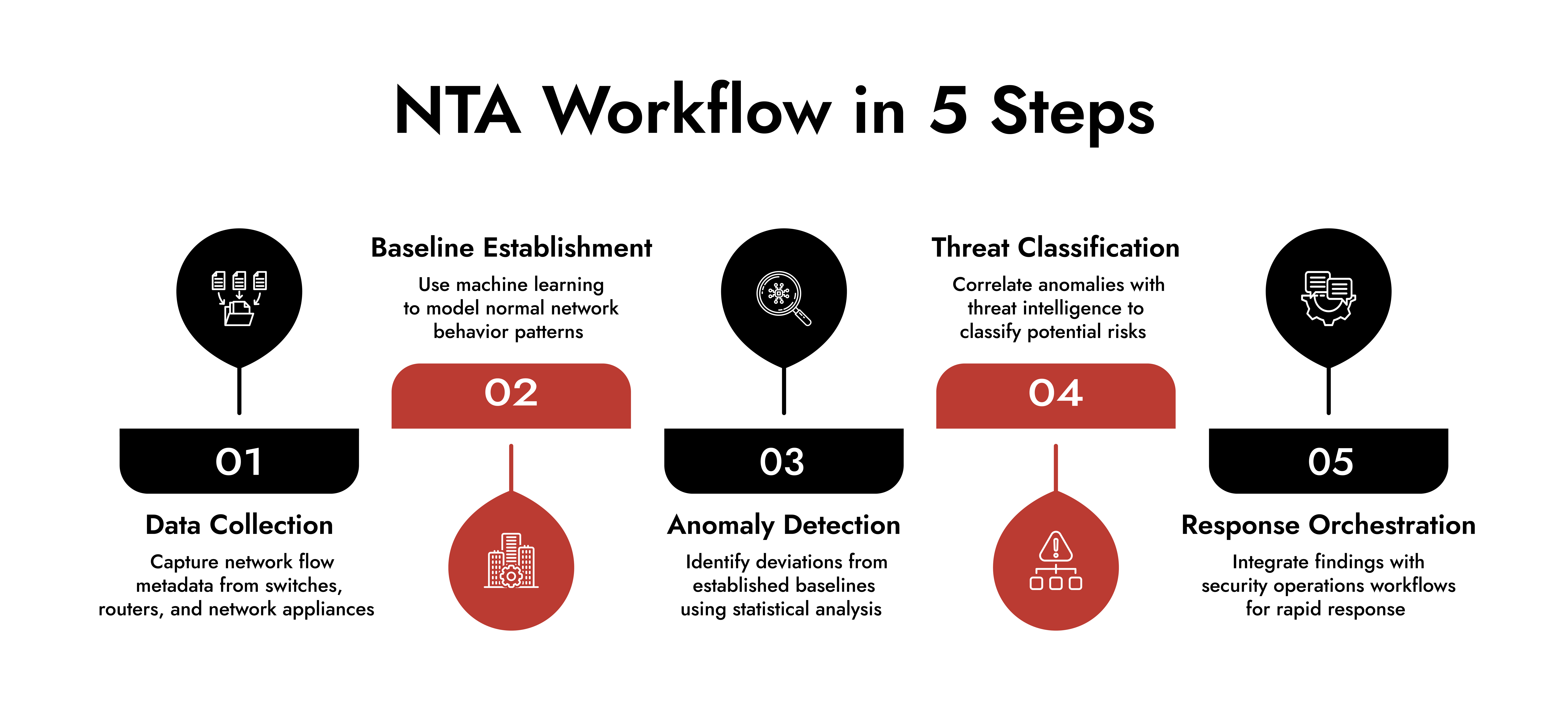
Modern network traffic monitoring tools make it possible to see and analyse network traffic at enterprise scale without capturing or storing every packet. Modern network traffic analysis tools use a combination of methodologies:
- Volume-Based Monitoring: Measures overall bandwidth and usage trends, highlighting spikes or drops that may signal trouble.
- Flow-Based Monitoring: Groups packets into flows (e.g., NetFlow, sFlow, IPFIX) to reveal conversations between devices and flag suspicious relationships.
- Baseline and Anomaly Detection: Machine learning models learn what “normal” looks like for a given network and trigger alerts when deviations appear.
- Integration with Security Operations: Network traffic analysis data feeds SIEMs, SOAR platforms, and threat intelligence sources, ensuring insights become part of broader defense workflows.
This layered approach makes it possible to monitor and analyze enormous data volumes without drowning security teams in noise.
Why Network Traffic Analysis Matter for Enterprise Security?
1. Enhanced Threat Detection Capabilities:
Traditional security solutions often struggle with advanced persistent threats (APTs) and insider attacks that operate within legitimate network channels. NTA fills this critical gap by providing continuous monitoring of network behavior patterns. When attackers establish footholds within enterprise networks, their activities generate distinctive traffic patterns – unusual communication frequencies, connections to suspicious domains, or abnormal data flows that NTA solutions can detect.
The importance of network traffic analysis becomes evident when considering that a high number of successful breaches involve lateral movement within networks – activity that perimeter security tools cannot detect. By monitoring internal network communications, network traffic analysis provides the visibility needed to identify these advanced attack techniques.
2. Proactive Security Posture:
Network traffic analysis allows proactive threat hunting, in which suspicious patterns are traced before turning into a full-scale incident. The NTA can be used to explore the possible threats, see the scale of attack, and carry out containment in a timely manner by the security teams.
The technology has also been thoughtful of requirements in compliance with network presence logs that are detailed and provide forensic possibilities in cases of incident investigation. There are also cases where NTA data is used to assist security teams to reconstruct the timeline of an attack, what systems were impacted, and how much data may have been exposed.
Challenges of Network Traffic Analysis and How to Overcome Them
1. Scale and Data Volume:
Enterprise networks develop terabytes of daily traffic. The data are overwhelming in the absence of the correct tooling. Metadata-based collection and smart analytics are the answer to this, and it does not have to store each packet.
2. Encrypted Traffic:
Most of the internet traffic is encrypted thus causing a lot of fear of blind spots. However, network traffic analysis does not require payloads, only network traffic metadata and behavioral analysis are required to detect suspicious traffic, even on encrypted networks.
3. Alert Fatigue:
Badly adjusted systems bombard analysts. To deploy effectively, it is necessary to set the baselines, refine the thresholds, and incorporate alerts into larger workflows to remain focused on action signals.

NetWitness NDR: Enterprise-Grade Network Traffic Analysis
NetWitness Network Detection and Response (NDR) is unique in its depth and usefulness. The solution constantly handles network traffic, develops behavioral profiles of devices and users, and applies more complex analytics to indicate deviations. NetWitness provides the capability to not only perform deep packet inspection but also high-speed metadata analysis to enable security teams to find links between individual data artifacts and broader threat campaigns.
Key strengths include:
- Deep Packet + Metadata Analysis: Both detailed and high-speed visibility.
- Automated Alerting: Prioritizes incidents with real business impact.
- Flexible Deployment: Works across cloud, hybrid, and on-prem networks.
- Efficient Investigations: Provides evidence-rich insights without slowing network performance.
Platforms like NetWitness save time for high-stakes enterprise teams by providing rapid insights, not overwhelming dashboards. The goal: making complex network traffic translation simple enough to fuel decisive action without creating alert fatigue.
Strengthen Network Visibility with NetWitness® Network Traffic Security Assessment
-Uncover hidden threats through deep packet inspection and analytics.
-Identify vulnerabilities and blind spots before they’re exploited.
-Enhance detection and response with NDR-driven intelligence.

Conclusion: The Strategic Value of Network Traffic Analysis
As enterprise environments grow more distributed, knowing how to see network traffic and analyze it in context becomes critical to effective security. Enterprise networks will only grow more distributed and complex. Perimeter defenses and endpoint tools are still necessary, but they can’t provide the continuous visibility required to catch sophisticated threats.
The importance of network traffic analysis lies in its ability to uncover what is happening inside the network, where attackers hide and where compliance risks lurk. The global network traffic analysis market reflects this growing importance, with projections showing growth from $3.16 billion in 2023 to $5.76 billion by 2028. This expansion indicates widespread recognition of NTA’s value in addressing sophisticated cyber threats that traditional security tools struggle to detect. For CISOs, the decision to invest in NTA isn’t about adding another tool; it’s about ensuring that every security decision is backed by evidence.
If your organization is ready to gain that visibility, consider how solutions like NetWitness NDR can help translate network data into actionable defense.
Frequently Asked Questions
1. How does network traffic analysis differ from traditional intrusion detection systems?
Network traffic analysis focuses on behavioral patterns and flow metadata rather than signature-based detection. While traditional IDS tools rely on known attack patterns, NTA uses machine learning to identify anomalous behavior that may indicate unknown threats, providing better detection of advanced persistent threats and zero-day attacks.
2. What network infrastructure changes are required to implement NTA?
Most modern NTA solutions integrate with existing network infrastructure through flow exports (NetFlow, sFlow, IPFIX) from switches and routers. Implementation typically requires configuring flow of export on network devices and deploying collection appliances but doesn’t require significant architectural changes to existing networks.
3. How does NTA handle encrypted network traffic?
NTA analyzes metadata and flow patterns rather than packet content, making it effective even with encrypted traffic. The solution examines communication patterns, timing, data volumes, and connection behaviors that remain visible regardless of encryption, allowing detection of malicious activities within encrypted channels.
4. What types of threats can network traffic analysis detect that other tools miss?
NTA excels at detecting lateral movement, command-and-control communications, data exfiltration, insider threats, and advanced persistent threats that operate within legitimate network channels. It’s particularly effective at identifying slow, low-volume attacks that evade traditional security tools through behavioral analysis.
5. How quickly can network traffic analysis tools detect and alert threats?
Modern NTA platforms can process network flows in real-time with sub-second latency for threat detection. However, detection speed depends on the complexity of the threat pattern – obvious anomalies trigger immediate alerts, while subtle behavioral changes may require minutes to hours of pattern analysis to confirm threats.
Proactive Network Threat Detection with NetWitness® NDR
-Spot threats fast with AI-driven analytics.
-See everything across your network and cloud traffic.
-Investigate efficiently with built-in forensic tools.
-Adapt and scale to meet growing security needs.






