Here’s the thing: most cyberattacks aren’t flashy smash-and-grab jobs. They’re quiet, calculated, and designed to blend into the background noise of your IT systems. And make no mistake—the background noise is deafening. The average enterprise generates hundreds of gigabytes of security logs per day across firewalls, endpoints, applications, and cloud workloads. Buried inside that mess might be a single entry that reveals a ransomware payload, a rogue insider, or a stolen credential being used at 3 a.m.
That’s where SIEM solutions earn their reputation. They aren’t just log collectors. They are pattern hunters, context builders, and early-warning radars for modern security teams. Without SIEM, your analysts are staring at raw logs. With SIEM, they’re staring at a storyline—who attacked, how, and what to do about it.
How is SIEM Solution Different from Just “Log Management”?
A lot of teams confuse SIEM with simple log management. But here’s the expert truth: logs without correlation are just haystacks; SIEM turns them into needles you can actually see.
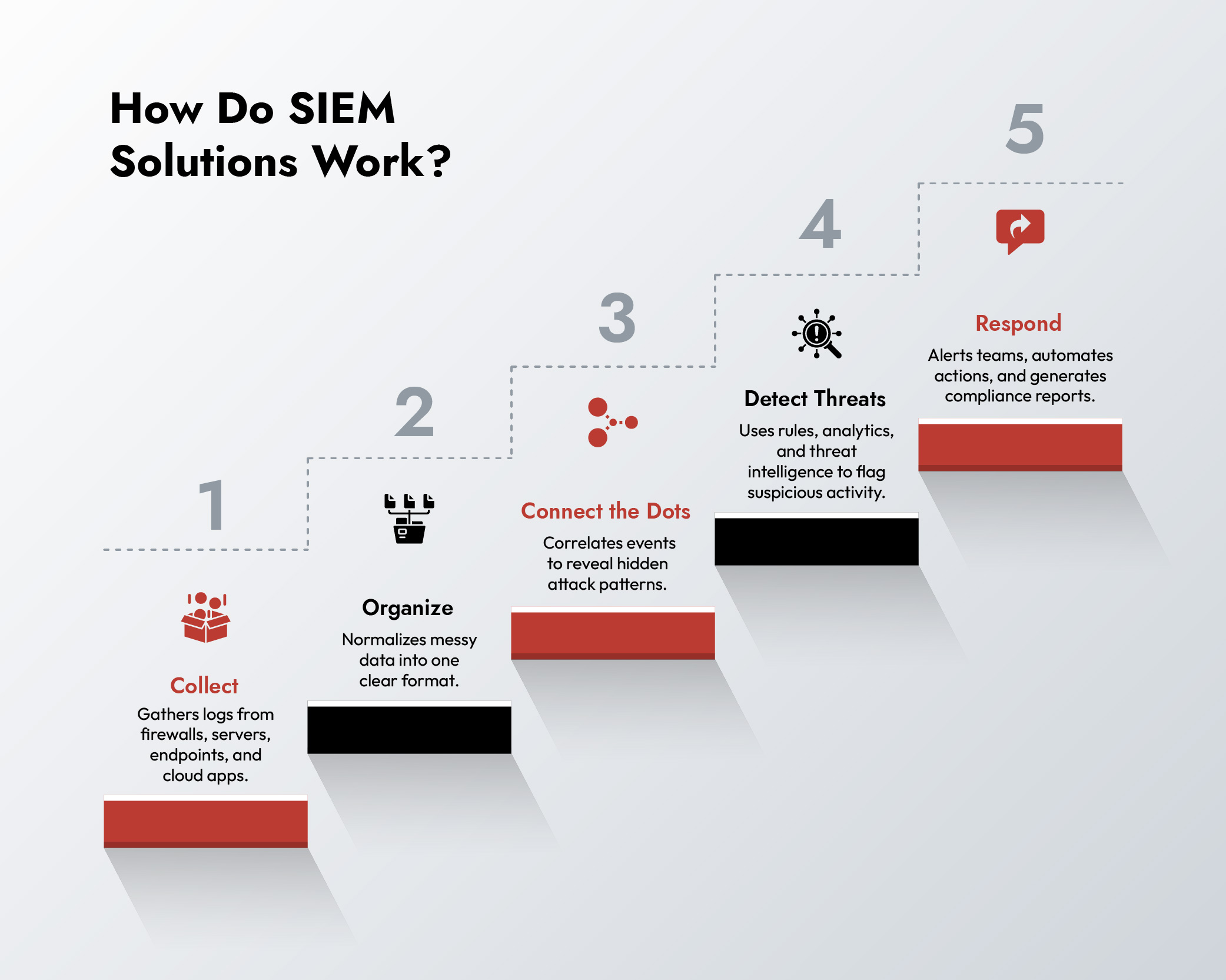
SIEM tools don’t just dump data into a warehouse. They:
- Ingest from everywhere: firewalls, IDS/IPS, servers, cloud apps, endpoints, OT systems.
- Normalize the chaos: stripping different log formats into a common structure.
- Correlate across time and context: tying login failures, privilege escalation, and data exfiltration into one coherent attack chain.
That correlation is the difference between spotting an insider threat in hours versus discovering it months later when your data is already on the dark web.
How Do SIEM Solutions Actually Detect Threats?
Detection isn’t magic—it’s layered. A properly tuned SIEM combines rules, analytics, and intelligence feeds to spot trouble others miss.
- Correlation Rules: If ten failed logins happen in under a minute from a foreign IP, that’s not bad typing—that’s brute force. SIEM connects those dots.
- Behavioral Analytics: SIEM tracks normal baselines. When your CFO downloads 20GB of HR data at midnight, it knows that’s not “business as usual.”
- Threat Intelligence: By integrating with external feeds, SIEM tools know if an IP connecting to your server belongs to a botnet in Russia or a Tor exit node.
Alerts without context are noise; SIEM makes them evidence.
What Happens After SIEM Sounds the Alarm?
Here’s where weak implementations fail. A good SIEM cybersecurity doesn’t just scream “something’s wrong.” It guides response:
- Smart Alerting: Instead of 10,000 pings, it escalates the 200 that actually matter.
- Automated Playbooks: Through SOAR integrations, some SIEM solutions can isolate an endpoint or block traffic before human hands are on deck.
- Forensic Timelines: Analysts get a narrative—who logged in, what they touched, and when they escalated privileges.
- Compliance-Ready Reports: PCI, HIPAA, GDPR—all prebuilt so your SOC isn’t wasting cycles making auditors happy.
The net effect? From overwhelm to focus. From firefighting to control.
What Are the Key Benefits of SIEM Solutions?
Here’s where the benefits of SIEM solution investment really stack up:
- Visibility at Scale: Attackers rely on blind spots. SIEM strips those away by giving SOCs a panoramic view across hybrid and multi-cloud environments.
- Faster Mean Time to Detect (MTTD): Breaches that once sat unnoticed for 200+ days can now be flagged in minutes. That delta is the difference between a contained incident and a multimillion-dollar breach.
- Operational Efficiency: Instead of analysts drowning in log files, they focus on high-value investigations. Repetitive triage tasks get automated.
- Audit Simplification: Compliance stops being a time sink because reports are baked into the system.
Remember this line: a single prevented breach pays for SIEM ten times over.
Elevate Threat Detection and Response with NetWitness® SIEM
-Correlate data across users, logs, and network for unified visibility.
-Detect advanced threats with AI-driven analytics and behavioral insights.
-Accelerate investigations using automated enrichment and guided workflows.

Why Are Managed SIEM Solutions Becoming the Default Choice?
Here’s the harsh reality: most organizations buy SIEM, deploy it, and then let it rot. Correlation rules get stale. Integrations break. Analysts ignore alerts.
That’s why managed SIEM solutions are exploding. Instead of owning the heavy lifting, you outsource to specialists who:
- Keep correlation rules constantly updated.
- Monitor threats 24/7 without burnout.
- Deliver tuned, contextual alerts straight to your SOC.
For mid-size enterprises especially, managed SIEM is the difference between “we tried SIEM and failed” and “we actually stopped an insider exfiltration attempt before it hit the cloud.”
What Are the Hidden Challenges of SIEM Solutions?
It’s not all glory. Any security information and event management deployment faces hurdles:
- Integration Complexity: Plugging in legacy systems can feel like forcing square pegs into round holes.
- False Positives: Poorly tuned SIEMs overwhelm teams with noise.
- Cost Sprawl: Log ingestion and storage can balloon fast if retention policies aren’t managed.
The insider truth: SIEM is only as good as the people and processes around it. Buy the tool, but also invest in tuning, training, and governance.
Where Are SIEM Tools Headed Next?
The next generation of SIEM is already reshaping the market:
- AI and Machine Learning: Moving beyond static rules into adaptive threat detection.
- UEBA Integration: Spotting insider threats by modeling normal behavior and flagging deviations.
- SOAR Coupling: Taking SIEM from “alert system” to “automated responder.”
- Cloud-Native SIEM: Designed for the hybrid, multi-cloud reality instead of on-prem retrofits.
Call it SIEM 2.0, call it XDR convergence—the point is clear: tomorrow’s SIEM isn’t just about watching; it’s about acting.
Final Word
SIEM solutions work because they transform noise into knowledge. They cut through the flood of events, surface the signals that matter, and give organizations a fighting chance against attackers who thrive in complexity.
Whether you run it in-house or choose managed SIEM solutions, the outcome is the same: visibility, speed, and resilience. In today’s threat landscape, those aren’t “nice-to-haves.” They’re survival essentials.




