Security teams rely on SIEM platforms to stitch together events across their entire environment. SIEM collects data, correlates incidents, and triggers alerts fast enough to keep pace with sophisticated threats. But here’s the thing: SIEM alone doesn’t give you the packet-level truth about what really happened. That’s where network log analysis enhanced by Network Detection and Response (NDR) comes in.
Network log analysis is the connective tissue that grounds every alert in hard evidence. When paired with NDR, it delivers not only a timeline of activity but also the full content and context of every packet. For CISOs and SOC leaders dealing with sprawling cloud workloads, remote endpoints, and relentless attackers, monitoring logs is only the start, you also need to see what moved across the wire.
Why Network Log Analysis Still Matters with SIEM
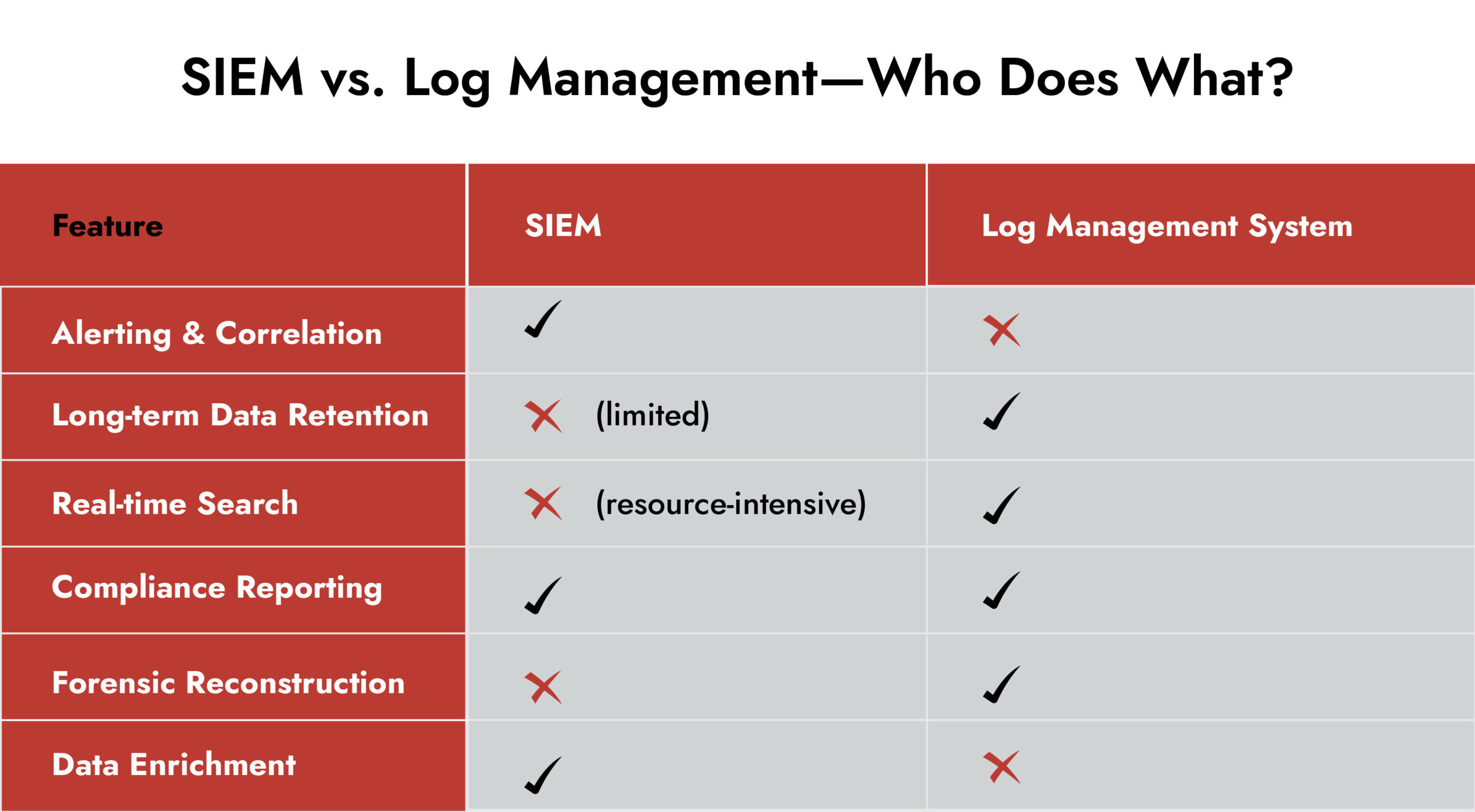
Modern SIEM solutions ingest enormous volumes of logs, normalize them, and correlate events into a single view. That’s invaluable, but it can’t replace network log analysis for several reasons:
- Aggregation ≠ Analysis: SIEM summarizes data for performance. Packet details and subtle anomalies are often abstracted out.
- Storage Trade-offs: Many deployments limit retention, so low-level activity may vanish before an investigation begins.
- Alert Fatigue: Quiet, multi-stage attacks may never trigger an automated alert.
Pairing SIEM log management with NDR-driven network log analysis ensures you retain the full story, not just the headlines.
Redefining Network Log Analysis with NDR
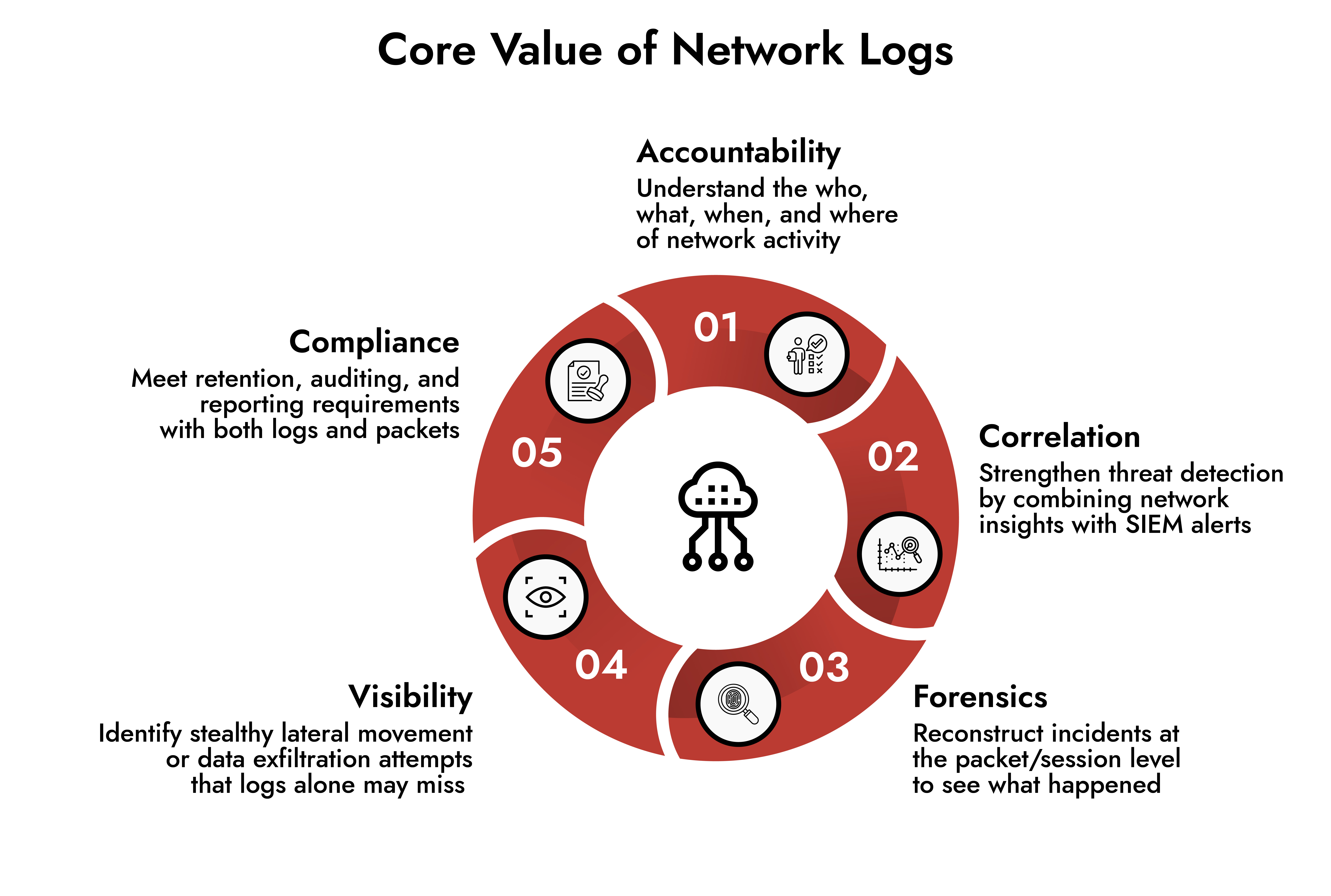
Traditionally, network log analysis referred to parsing logs from routers, firewalls, and switches. That still matters, but NDR changes the game.
NDR sensors capture packets and extract rich metadata – flows, payloads, and session details, while simultaneously feeding your SIEM. This creates a multi-layer view:
- Logs show who connected and when.
- NDR shows what moved and how.
Together, they give analysts the confidence to validate alerts and hunt hidden threats.
Proactive Network Threat Detection with NetWitness® NDR
-Spot threats fast with AI-driven analytics.
-See everything across your network and cloud traffic.
-Investigate efficiently with built-in forensic tools.
-Adapt and scale to meet growing security needs.

Security teams rely on SIEM platforms to stitch together events across their entire environment. SIEM collects data, correlates incidents, and triggers alerts fast enough to keep pace with sophisticated threats. But here’s the thing: SIEM alone doesn’t give you the packet-level truth about what really happened. That’s where network log analysis enhanced by Network Detection and Response (NDR) comes in.
Network log analysis is the connective tissue that grounds every alert in hard evidence. When paired with NDR, it delivers not only a timeline of activity but also the full content and context of every packet. For CISOs and SOC leaders dealing with sprawling cloud workloads, remote endpoints, and relentless attackers, monitoring logs is only the start, you also need to see what moved across the wire.
Why Network Log Analysis Still Matters with SIEM
Modern SIEM solutions ingest enormous volumes of logs, normalize them, and correlate events into a single view. That’s invaluable, but it can’t replace network log analysis for several reasons:
- Aggregation ≠ Analysis: SIEM summarizes data for performance. Packet details and subtle anomalies are often abstracted out.
- Storage Trade-offs: Many deployments limit retention, so low-level activity may vanish before an investigation begins.
- Alert Fatigue: Quiet, multi-stage attacks may never trigger an automated alert.
Pairing SIEM log management with NDR-driven network log analysis ensures you retain the full story, not just the headlines.

Redefining Network Log Analysis with NDR
Traditionally, network log analysis referred to parsing logs from routers, firewalls, and switches. That still matters, but NDR changes the game.
NDR sensors capture packets and extract rich metadata – flows, payloads, and session details, while simultaneously feeding your SIEM. This creates a multi-layer view:
- Logs show who connected and when.
- NDR shows what moved and how.
Together, they give analysts the confidence to validate alerts and hunt hidden threats.
When Network Log Analysis with NDR Makes the Difference
Imagine your SIEM reports a privileged account making an unusual outbound connection. Without NDR-backed network log analysis, you can’t answer questions that matter:
- Did the event follow repeated failed logins?
- Did packet captures confirm data exfiltration?
- Was it a scheduled process or a human command?
Only by combining packet capture with log correlation can you reconstruct the full timeline.
Role of Log Management Systems
Strong log management systems remain the foundation of effective network log analysis. They handle:
- High-volume collection and indexing.
- Long-term retention for compliance and retrospection.
- Tamper-proof storage for legal defense.
- Flexible querying for ad-hoc investigations.
A dedicated log management tool ensures packet-level insights from NDR and high-fidelity logs from SIEM log management stay accessible long after an incident.
How NetWitness NDR Complements SIEM for Deeper Network Log Analysis
NetWitness unifies SIEM and NDR into one investigative environment where network log analysis thrives:
- Full-Packet and Metadata Integration – Analysts move seamlessly from an alert to the underlying packets and related logs.
- Contextual Reconstruction – Packet data combined with log events tells the entire attack story.
- Retrospective Hunting – Search weeks or months of packets and logs for indicators of compromise.
- Custom Retention Policies – Align storage with compliance mandates and internal security needs.
This synergy means your team can pivot from a SIEM alert to NDR packet evidence in seconds, reducing mean time to detect and respond. 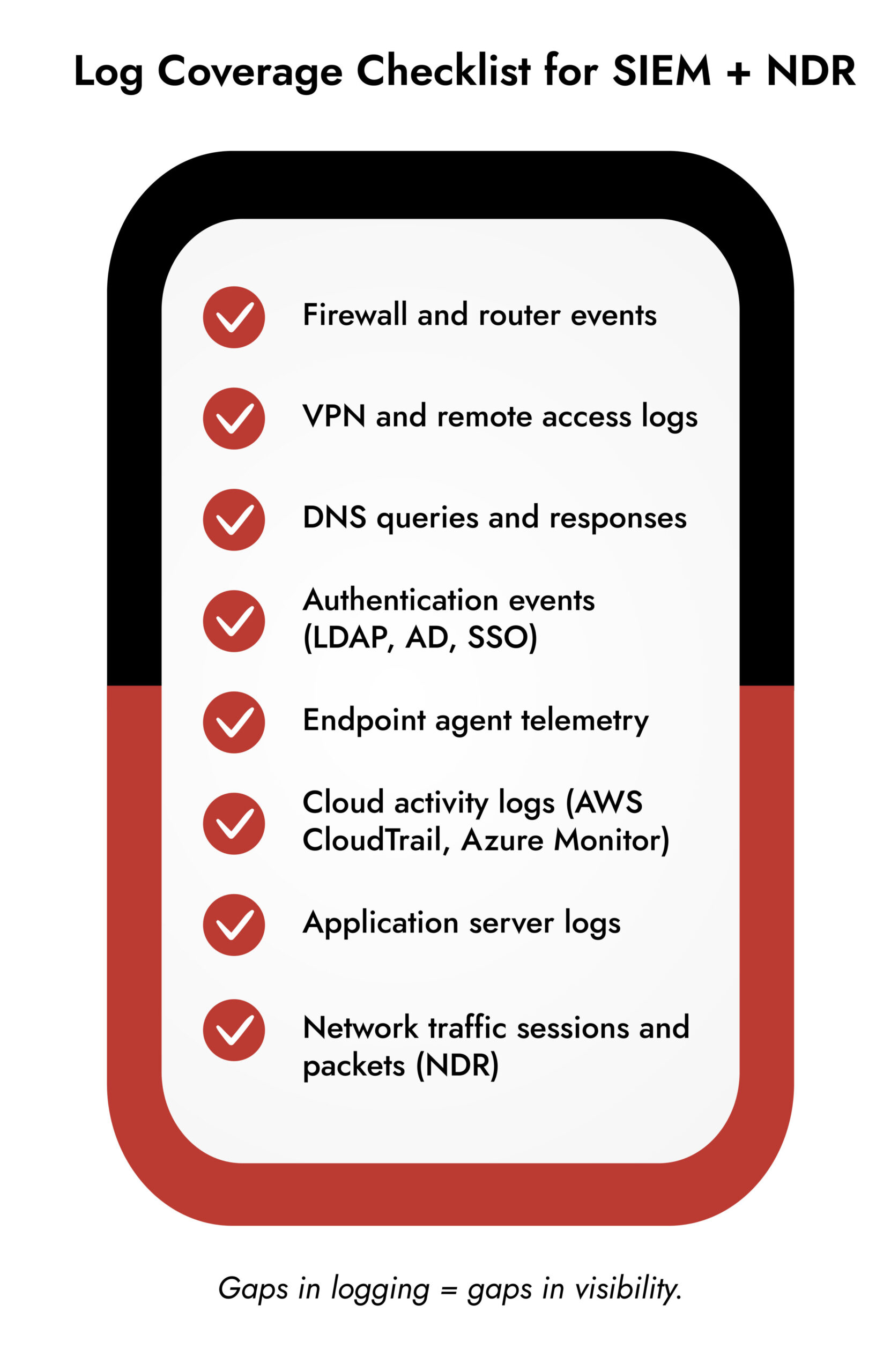
Best Practices for Effective Network Log Analysis
- Centralize Intelligently: Feed NDR packet captures and all critical logs into a unified SIEM SOC view.
- Set Retention Policies: Store both logs and packet data long enough to match attacker dwell times.
- Baseline Normal Behavior: Use network log analysis to map typical traffic, then flag deviations.
- Correlate Across Domains: Combine network packets, endpoint telemetry, and cloud logs for full context.
- Invest in Training: An NDR management tool can take you far, but an analyst’s judgment is still the last line of defense.
Final Thought: Logs and Packets Together Tell the Truth
Dashboards are summaries. The reality of an intrusion lives in packets and raw logs.
With SIEM for correlation and NDR for deep inspection, network log analysis becomes the SOC’s most reliable truth source. It may not be flashy, but when an investigation turns critical, you’ll be glad those packets and logs were captured, stored, and ready to tell the full story.
Frequently Asked Questions
1.How does network log analysis enhance SIEM detection?
By pairing logs with NDR packet data, analysts see not just that an alert fired, but exactly what traversed the network.
2. How long should SIEM data be retained?
At least 90 days in SIEM for active hunting and one year or more in log management systems for forensics and compliance.
3. Difference between SIEM and log management?
SIEM correlates and alerts; log management systems collect, store, and let you query raw data that both SIEM and NDR rely on.
4. Can network log analysis speed response?
Absolutely. Access to enriched logs and packets enables faster validation, cutting detection and response times.
Simplify Log Management and Threat Detection with NetWitness® Logs
-Centralize and analyze logs from across your environment in one platform.
-Detect threats faster with real-time visibility and automated correlation.
-Reduce noise through advanced filtering and context-driven analytics.





