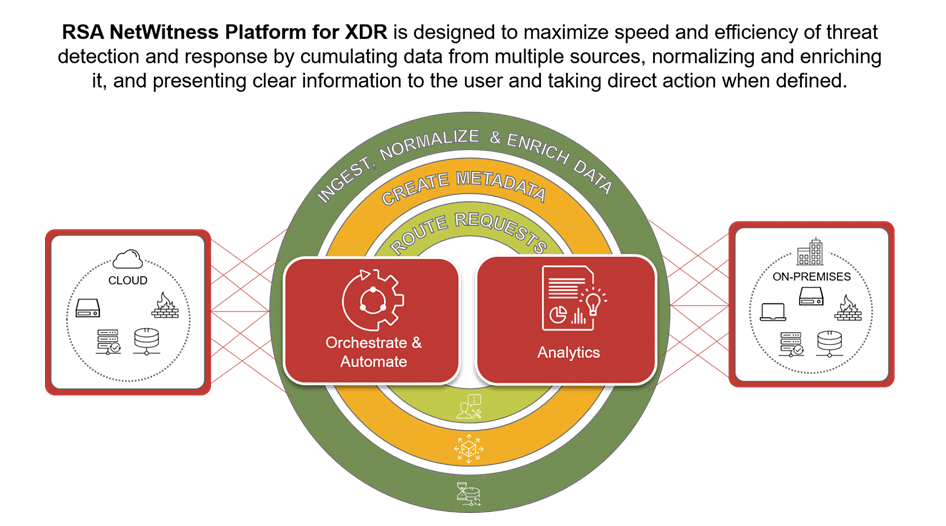
What is XDR?
RSA defines XDR as an approach to cybersecurity that extends detection and response from the user, through the network, to the cloud to provide security operations teams with threat visibility wherever data and applications reside. XDR products combine network detection and response (NDR), endpoint detection and response (EDR), behavior analytics, and security orchestration, automation and response (SOAR) capabilities into a single, cohesive incident detection and response platform to make it easier for security teams to neutralize today’s advanced threats.
It’s important to note that the market for XDR is in its infancy, and therefore, definitions of XDR can vary.
Why is XDR getting so much attention?
XDR aims to help security operations teams overcome many of the obstacles hindering their ability to quickly detect sophisticated threats, including:
- Incomplete visibility across the network, endpoints, and cloud-based infrastructure and applications
- Inconsistent security data and an overwhelming number of alerts coming from a growing portfolio of siloed security products
- A lack of tools to help correlate and prioritize alerts
By combining what have traditionally been point security solutions (or solutions that only address one component, such as EDR, NDR, UEBA or SOAR) in a single platform, XDR products attempt to break down the silos that have created so much complexity for security teams and make it easier for them to quickly and proactively detect, investigate and respond to advanced threats. XDR products speed detection and response by centralizing and normalizing security data from disparate systems (e.g., combining similar metrics, scrubbing for duplicate data, and combining it all into a single metadata store); automatically correlating this data and any other security alerts into incidents; and providing a centralized (and more automated) incident response capability.
Wait a minute: Doesn’t evolved SIEM make a lot of the same promises? If so, what’s the difference between XDR and evolved SIEM?
You’re right: Evolved SIEM and XDR platforms share common goals, including accelerating threat detection and response and making life easier for security analysts. The difference: XDR is purely focused on advanced threat detection and response, while an evolved SIEM like RSA NetWitness Platform combines XDR capabilities with log management, retention and compliance capabilities. An evolved SIEM collects logs; an XDR platform doesn’t. This blog does a nice job of explaining the differences between XDR, evolved SIEM and traditional, log-centric SIEMs.
If XDR platforms don’t take logs into account, does that mean I’m not getting full visibility?
If you’re getting network packets and endpoint data, then by and large those data sources should give you a majority of the information you need to detect and investigate threats. That said, some organizations still want to include logs in their threat detection efforts.
So which should I choose: evolved SIEM or XDR?
If your organization already has a log management and retention tool for compliance purposes, you may not need an evolved SIEM solution for threat detection and response. XDR may suffice.
What features or capabilities should I seek in an XDR solution?
As noted earlier, industry analysts list XDR’s primary requirements as normalizing and centralizing data; correlating security data and alerts into incidents; and providing a centralized incident response capability. If you’re considering an XDR solution that doesn’t meet these three fundamental requirements, then it’s not really XDR.
Similarly, if you’re considering an XDR solution that fundamentally only provides NDR or EDR capabilities, then again, it’s not truly an XDR platform. SANS maintains that any primary detection and investigation platform should offer the following:
- A wide range of investigative tools and forensic artifacts, including network traffic, endpoint processes, files, and events.
- A strong user and entity behavior analytics (UEBA) capability—one that ties user behavior monitoring into the other types of event and system analyses being performed.
- Remediation capabilities, including blocking network addresses, flagging assets for follow-up and quarantining endpoint systems, that can be implemented quickly.
Beyond those basics, analyst firms recommend seeking an XDR platform with either an open architecture or strong integration capabilities to ensure that it can interoperate with your organization’s existing security controls.