Key Takeaways
- TDR (Threat Detection and Response) unifies visibility across endpoints, networks, and cloud environments to deliver centralized threat detection and automated response.
- NDR (Network Detection and Response) focuses on monitoring network traffic and detecting lateral movement, insider activity, and hidden threats across hybrid environments.
- EDR (Endpoint Detection and Response) identifies and isolates endpoint-based threats like ransomware, credential theft, and fileless attacks.
- Each solution serves a unique layer of visibility, but integrated platforms like NetWitness TDR connect all three for faster, data-driven investigation and response.
- Enterprises using unified threat detection and response solutions like NetWitness reduce mean time to detect (MTTD) by up to 60% and investigation time by 40%.
Introduction
Threats no longer stay confined to a single endpoint, network, or cloud. They move laterally, exploit blind spots, and blend into normal traffic until it’s too late. That’s why most mature security operations today rely on Threat Detection and Response (TDR) – an integrated approach that connects signals from Network Detection and Response (NDR) and Endpoint Detection and Response (EDR) systems into one cohesive defense strategy.
Each of these solutions – TDR, NDR, and EDR – plays a distinct role. But many teams are still confused about where one ends and the other begins. Understanding their differences isn’t just about definitions; it’s about knowing how to deploy them together for faster detection, deeper visibility, and more efficient incident response.
Let’s break it down.
What Is Threat Detection and Response (TDR)?
Threat Detection and Response (TDR) is an integrated cybersecurity approach that combines network, Logs, endpoint, and cloud telemetry to detect, investigate, and respond to threats across the entire attack surface.
Threat Detection and Response acts as the unifying layer – the brain connecting NDR and EDR insights. Instead of managing disjointed alerts from multiple tools, TDR provides centralized visibility, automated correlation, and guided response actions.
A threat detection and response solution like NetWitness TDR consolidates data from across the infrastructure -packet captures, endpoint, logs, and behavioral analytics – to surface only the alerts that matter. This context speeds up investigation, improves accuracy, and eliminates alert fatigue.
Why TDR matters:
- Cross-domain visibility: Detects threats spanning network and endpoint activity.
- Unified analytics: Reduces false positives by correlating multiple signals.
- Faster response: Automates playbooks to contain and remediate incidents.
- Operational efficiency: Enables security teams to focus on priorities, not noise.
What Is Network Detection and Response (NDR)?
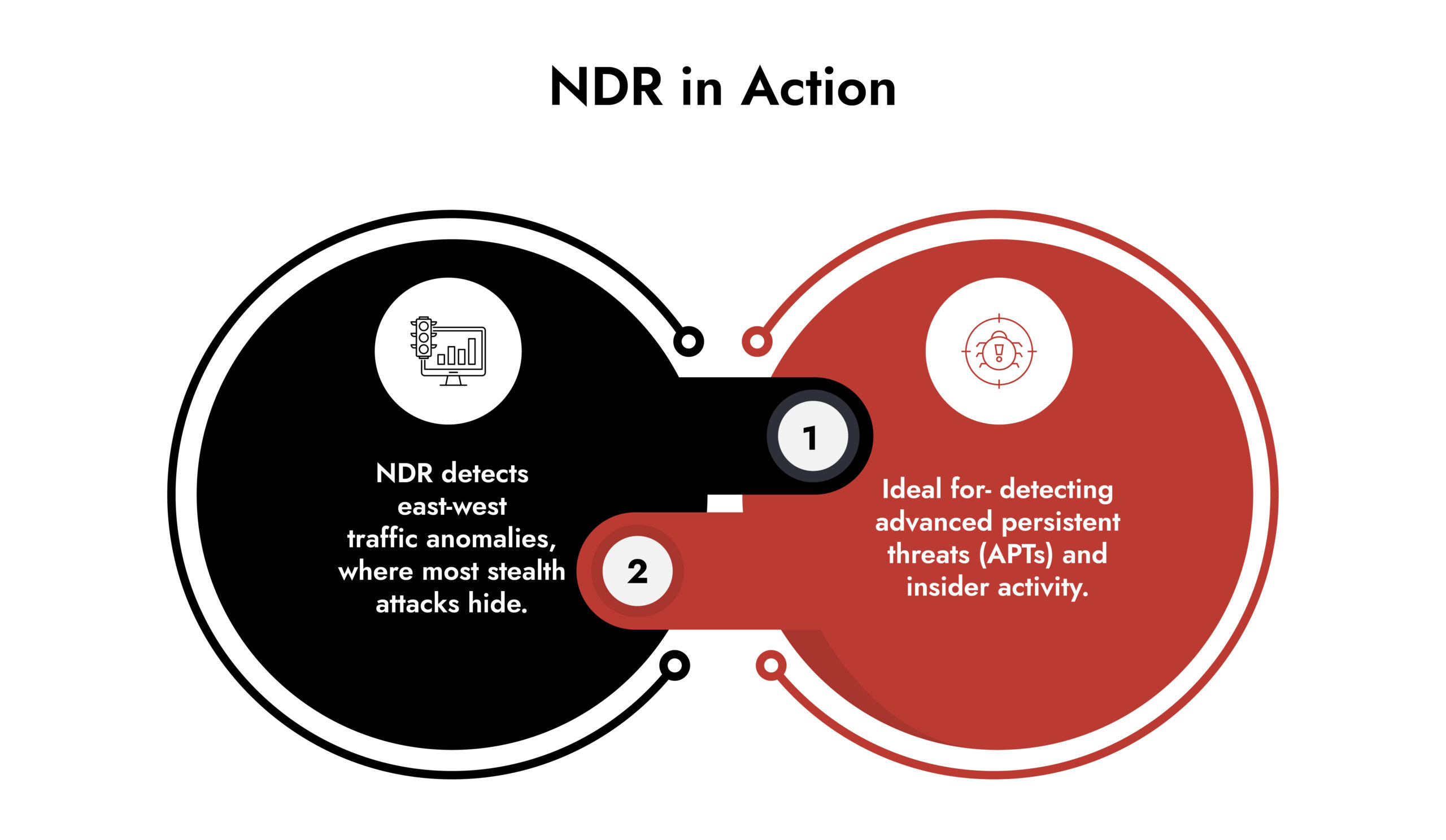
Network Detection and Response (NDR) monitors network traffic in real time to identify suspicious behavior, detect lateral movement, and investigate threats that bypass traditional security controls.
While firewalls and intrusion prevention systems inspect traffic at the perimeter, NDR tools continuously analyze internal North-South, East-West as well as cloud network communications. By capturing and inspecting packets, NDR provides visibility into encrypted traffic, unmanaged devices, and cloud workloads that often evade endpoint monitoring.
In platforms like NetWitness NDR, detection is powered by advanced analytics, threat intelligence, and behavioral modeling, allowing analysts to see the complete path of an attack and respond before it spreads.
Key capabilities of network detection and response solutions:
- Full-packet capture and session reconstruction for forensic visibility.
- AI-driven anomaly detection that flags abnormal data flows.
- Integration with SIEMs and SOAR tools for automated containment.
- Cloud and on-premise coverage for hybrid environments.
What Is Endpoint Detection and Response (EDR)?
Endpoint Detection and Response (EDR) focuses on detecting and responding to threats on endpoint devices such as laptops, servers, and virtual machines.
EDR collects process data, memory activity, and system behavior to spot malicious activity at the device level – things traditional antivirus often misses.
Endpoint detection and response solutions like NetWitness EDR provide deep visibility into fileless attacks, ransomware behavior, and abnormal user activity. They enable security analysts to isolate infected systems, trace attack origins, and remediate faster.
Core strengths of EDR:
- Monitors real-time endpoint behavior and process execution.
- Supports rapid isolation and rollback of compromised assets.
- Correlates endpoint telemetry with network indicators for a richer context.
- Enhances digital forensics and incident response readiness.
Proactive Network Threat Detection with NetWitness® NDR
-Spot threats fast with AI-driven analytics.
-See everything across your network and cloud traffic.
-Investigate efficiently with built-in forensic tools.
-Adapt and scale to meet growing security needs.

TDR vs NDR vs EDR: What’s the Difference?
The key difference between TDR, NDR, and EDR lies in the scope and data source. EDR focuses on endpoints, NDR monitors network traffic, and TDR unifies both, delivering a holistic view of threats across the enterprise.
Here’s how they differ at a glance:
| Capability | EDR | NDR | TDR |
| Primary focus | Endpoint behavior and processes | Network traffic and communications | Unified detection and response |
| Data sources | Logs, memory, processes | Packets, flow data, DNS | Aggregated data from EDR, NDR, and SIEM |
| Detection scope | Localized to endpoints | Covers internal/external traffic | End-to-end attack correlation |
| Response action | Isolate device, remove malware | Block traffic, alert SOC | Automate cross-domain containment |
| Best for | Ransomware, insider threats | APTs, lateral movement | Coordinated detection and response |
How Do TDR, NDR, and EDR Work Together?
TDR, NDR, and EDR complement each other by connecting endpoint, network, and cloud insights into one workflow. Together, they create a proactive security posture capable of identifying, analyzing, and neutralizing threats in real time.
Here’s how the ecosystem works:
- NDR detects unusual network traffic (e.g., a command-and-control connection).
- EDR confirms the endpoint behavior, showing which process initiated it.
- SIEM ties in log and identity activities to complete the timeline.
- TDR correlates signals, prioritizes the threat, and triggers an automated response.
This integration shortens investigation cycles, improves SOC productivity, and ensures faster containment across the entire infrastructure.
Why NetWitness is at the Core of Unified Detection and Response
NetWitness delivers an integrated Threat Detection and Response (TDR) platform that unites Network Detection and Response (NDR), SIEM, Endpoint Detection and Response (EDR) into a single, cohesive system for complete visibility and control.
Unlike siloed tools that flood analysts with disconnected alerts, NetWitness TDR provides full-packet visibility, endpoint telemetry, and behavioral analytics – all correlated through a single data model. This means security teams can see how an attack unfolds across every vector and respond with precision.
How NetWitness enhances detection and response:
- Unified visibility: One console to monitor endpoints, networks, and cloud assets.
- Advanced analytics: Machine learning and behavioral detection aligned with MITRE ATT&CK.
- Faster investigations: Deep forensics, automated correlation, and guided response workflows.
- SOC integration: Tight interoperability with SIEM, SOAR, and threat intelligence feeds.
- Proven reliability: Used by global enterprises and government agencies to reduce dwell time and improve threat response speed.
What this really means is that NetWitness doesn’t just connect NDR and EDR, it operationalizes detection and response at enterprise scale. It turns fragmented data into actionable intelligence, enabling analysts to focus on the threats that truly matter.
360° Cybersecurity with NetWitness Platform
– Unrivaled visibility into your organization’s data
– Advanced behavioral analytics and threat intelligence
– Threat detections and response actionable with the most complete toolset

Conclusion
Modern threats don’t respect boundaries, and neither should detection. TDR, NDR, SIEM and EDR are no longer standalone tools, they’re interlocking pieces of a unified defense strategy.
What this really means is that the most resilient organizations don’t just detect threats; they understand them in context – across endpoints, networks, and the cloud – and respond before business impact occurs.
A unified threat detection and response solution like NetWitness TDR helps teams achieve that by connecting every signal, surfacing the right alerts, and enabling rapid, confident action when it matters most.
Frequently Asked Questions
1. What is the difference between TDR, NDR, and EDR?
TDR integrates detection and response across all domains, while NDR focuses on network traffic and EDR on endpoint activity. Together, they provide comprehensive visibility and faster incident resolution.
2. How do TDR, NDR, and EDR complement each other?
They connect different layers of the environment. NDR identifies suspicious traffic, EDR traces it to a device, and TDR unifies the context for efficient investigation.
3. Which solution is best for enterprises: TDR, NDR, or EDR?
Enterprises benefit most from using all three together. TDR serves as the overarching layer that maximizes the value of NDR and EDR investments.
4. How do TDR, NDR, and EDR solutions integrate with a SOC?
They feed correlated alerts and contextual intelligence into SOC workflows, improving threat triage, response automation, and analyst efficiency.
5. What features should buyers look for in each solution?
- For TDR: cross-domain correlation and automation.
- For NDR: full-packet visibility and anomaly detection.
- For EDR: behavioral analytics and rapid isolation.





