What is Red Teaming in Cybersecurity?
Red Teaming is a type of cybersecurity, in which experts imitate the techniques of actual attackers to determine the effectiveness of a particular organization in detecting, responding to, and recovering the assets after the danger has occurred. Contrary to conventional audits or pen tests, Red Team exercises subject people, processes, and tools to actual attacks and reveal vulnerabilities in cybersecurity incident response and build a solid security posture.
Cyber threats have now become much more than the generic malware or basic phishing mail. The contemporary enemies are fast, sophisticated and patient. However, most organizations still use incident response playbooks developed to only support theoretical attacks and not real-world adversary techniques. Such a lack of harmony gives a false sense of preparedness.
Red Teaming changes that. In cybersecurity, Red Team is real and uses the real-world tactics, techniques, and procedures (TTPs) to test all elements of your security program. Their drills do not simply point out areas of weakness, but they make your teams think, adapt and act in the real adversarial environment. By adding Red Team exercises into your incident response planning services transforms your playbook from a compliance document into an operational battle plan.
Why Traditional Incident Response Playbooks Fall Short
Most incident response playbooks are structured around generic threat models. They define:
- Alert escalation workflows.
- Containment and eradication steps.
- Roles and responsibilities during incidents.
- Communications protocols for legal, PR, and leadership teams.
These are essential—but they’re not enough. Playbooks often assume a linear, predictable attack scenario. Real adversaries don’t follow templates. They chain together overlooked vulnerabilities, exploit human error, and move laterally across systems defenders assume are isolated. Until tested under real-world pressure, those assumptions stay hidden—and dangerous.
There’s another critical flaw: over-reliance on technology-driven security events.
Organizations are drowning in tools—SIEMs, EDRs, XDRs, AI-powered platforms—all promising turnkey protection. But here’s the hard truth: if you think technology alone will save you, you’re already a headline waiting to happen — “Company Breached Despite Millions Spent on Security Tools.”
Tools are force multipliers. They help good teams move faster and smarter. But they don’t replace judgment, coordination, or fast decision-making under fire. The organizations that hold the line are the ones who test their tools, their people, and their playbooks—regularly and ruthlessly.
That’s where Red Teaming comes in. The red team responsibilities go far beyond finding vulnerabilities—they assess how resilient your defenses are when under live attack.
What Sets Red Teaming Apart
Unlike traditional penetration tests that focus on identifying vulnerabilities, Red Team assessment emulates real adversaries with clear objectives:
- Breach the organization’s perimeter stealthily.
- Escalate privileges and gain persistence.
- Move laterally within the environment.
- Access and exfiltrate sensitive data.
- Avoid detection throughout their mission.
Their engagements are structured, but their tactics are creative and adaptive, mirroring the dynamic approaches used by sophisticated threat actors. They do not merely test security controls; they test the organization’s entire defensive ecosystem, including technology, processes, and people.
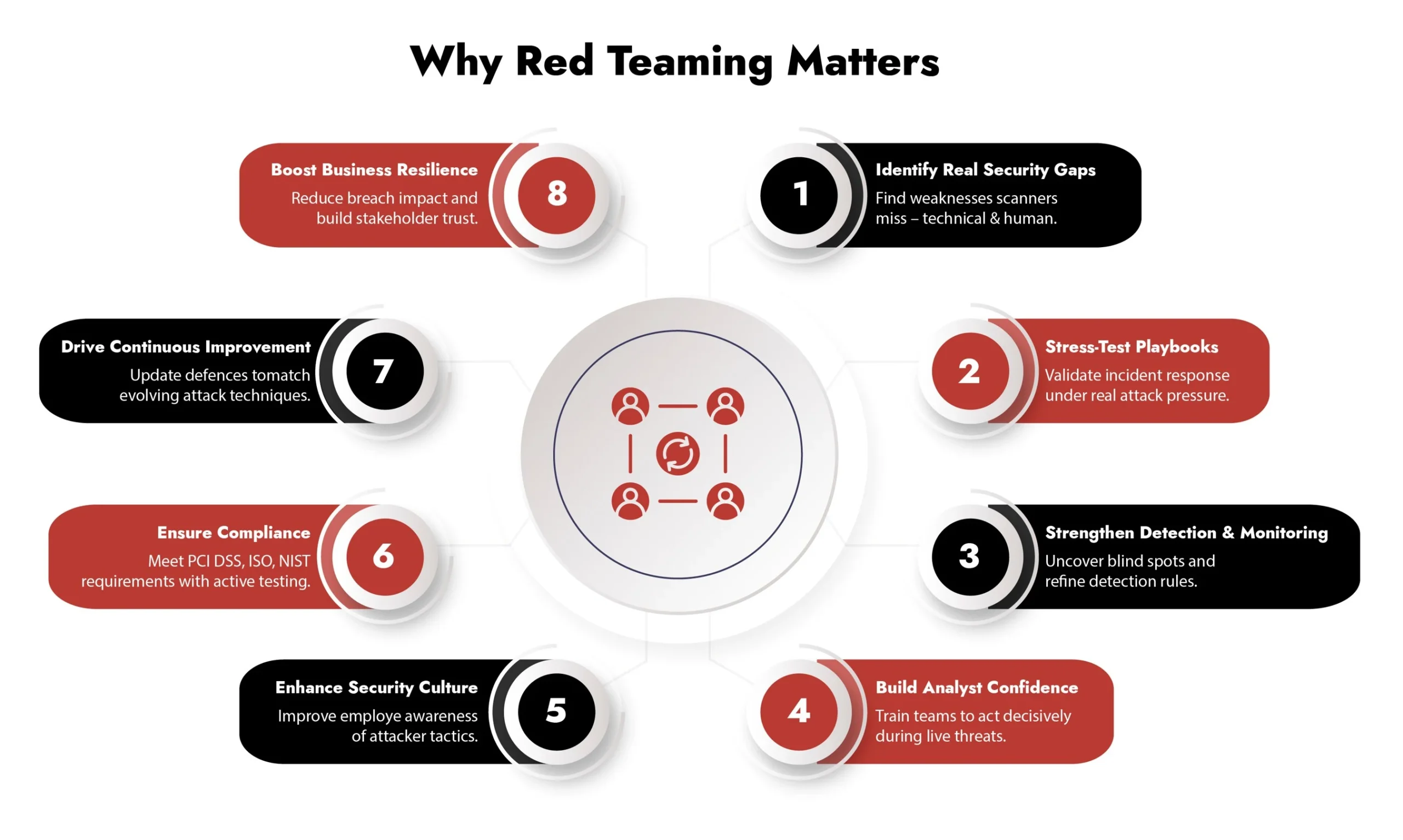
8 Ways Red Teaming Enhances Your Incident Response Playbook
1. Reveal Hidden Vulnerabilities (and Actionable Exposures)
Red Teams identify weaknesses that routine vulnerability scans miss. These include:
- Misconfigured firewalls.
- Insecure API endpoints.
- Legacy systems with unpatched exploits.
- Weak Active Directory hygiene.
- Poor password management practices.
They also probe human weaknesses—phishing, social engineering, careless clicks—showing how attackers slip through when people let their guard down. These findings strengthen the foundation of your incident response services by focusing remediation where it matters most.
More importantly, they uncover actionable exposures: the low-hanging fruit real attackers love. These aren’t abstract risks. They’re unlocked doors—exposed credentials, forgotten admin panels, or a password stuck to the CEO’s screen.
Red Teams find them before someone with worse intentions does.
2. Validate and Strengthen Your Incident Response Playbook
A major benefit of Red Teaming is stress-testing your incident response playbook:
- Do your analysts detect stealthy lateral movements?
- Can SOC teams escalate unusual alerts quickly?
- Are containment decisions delayed by approval bottlenecks?
- Do communication protocols work under high-pressure incidents?
Red Team exercises provide clear answers, highlighting process gaps that tabletop exercises cannot uncover.
3. Enhance Detection and Monitoring Capabilities
Red Teams expose blind spots in incident response solutions.
Red Teams expose blind spots in detection logic. They force defenders to move beyond signature-based alerts to behavior-based detections.
For example:
- SIEM rules that ignore unusual but benign-looking activities.
- EDR configurations missing advanced privilege escalation techniques.
- Lack of monitoring around network segmentation or jump servers.
Addressing these findings significantly improves detection and response maturity.
4. Improve Analyst Confidence and Decision-Making
Red Team exercises train analysts to:
- Recognize subtle adversary tactics.
- Prioritize and correlate weak signals under pressure.
- Contain and remediate attacks decisively.
- Communicate risks clearly to leadership during crises.
This practical exposure builds confidence no classroom training can replicate.
5. Build a Security-Conscious Organizational Culture
By simulating phishing and social engineering attacks, Red Teams raise employee awareness. Staff learn how attackers exploit daily behaviors, fostering vigilance that strengthens your incident response services overall defense posture.
6. Support Regulatory Compliance
Frameworks such as PCI DSS, ISO 27001, and NIST CSF require evidence of active security testing. Red Team reports demonstrate proactive defense, improving audit outcomes and enhancing client trust.
7. Enable Continuous Improvement
Assailants are in a state of change. Frequent Red Team exercises keep your incident response retainer and playbook updated with them, including updating detection rules, workflows, and escalation rules. Red Teaming makes your incident response playbook, detection rules, and security workflows updated on a regular basis. This is a cyclic process of improving your organization to keep ahead of the new threats.
8. Strengthen Business Resilience and Reputation
The final advantage of Red Teaming is a lesser impact of breaches, as well as organizational resilience. The clients, partners and regulators will be assured that your security has gone through methods of dealing with actual adversaries and not merely the compliance checklists. A proven, tested, and constantly updated incident response playbook increases the resilience and develops trust among clients, partners, and regulators.
Rapid, Expert Response with NetWitness® Incident Response Services
-Accelerate threat containment with experienced IR specialists.
-Investigate effectively using advanced forensics and analytics.
-Minimize business impact with fast, guided remediation.

5 Steps of a Red Team Exercise
Every exercise begins with clear scoping. Objectives, systems under test, rules of engagement, and success criteria are defined. This ensures safety, focus, and meaningful outcomes.
2. Reconnaissance
Reconnaissance in Red Teaming goes beyond scanning external assets. Unless the engagement is black-box testing, it starts with internal data provided by the customer.
- The Red Team lead collects network diagrams and system details to plan safely.
- Business-critical systems are defined up front and marked out-of-scope.
- The team looks for actionable exposures across people, processes, and technologies.
- Insights from this phase help craft targeted attacks like phishing or watering-hole scenarios—based on how users behave and which systems support less critical services.
The goal is to map realistic paths an attacker could take, without putting core operations at risk.
3. Exploitation
Using information from reconnaissance, the team executes attacks such as:
- Phishing to steal credentials.
- Exploiting web app vulnerabilities.
- Deploying malware to gain persistence.
Their goal is to breach defenses and escalate privileges without detection to assess the effectiveness of your incident response services.
4. Post-Exploitation
Here, the team:
- Moves laterally across the network.
- Accesses sensitive systems or data.
- Attempts privilege escalation.
- Tests persistence methods to maintain access.
This simulates the full impact a real attacker could achieve if undetected.
5. Reporting and Debrief
Findings are documented in detail. Reports include:
- Vulnerabilities exploited.
- Attack paths and techniques used.
- Detection and response gaps observed.
- Recommendations for immediate fixes and strategic improvements.
Debrief sessions ensure security, IT, and executive teams understand these insights clearly and align on next steps to improve your incident response playbook and detection strategy.
Red Team vs. Blue Team: A Collaborative Necessity
| Aspect | Red Team | Blue Team |
| Focus | Offensive emulation of real adversaries | Defensive monitoring and response |
| Objective | Identify weaknesses and test readiness | Protect systems, detect threats, and mitigate attacks |
| Approach | Stealth, creativity, adaptability | Visibility, control, structured workflows |
| Outcome | Recommendations to strengthen security | Active defense and response execution |
Both are essential. Red Teams find weaknesses; Blue Teams remediate them. Their combined efforts build a security posture attackers find increasingly difficult to breach.
Integrating Red Teaming into Incident Response Planning Services
Standalone Red Team exercises provide tactical insights. Integration with structured incident response planning services ensures:
- Exercises align with business-critical risks.
- Findings directly inform playbook updates.
- Follow-up tabletop sessions validate new workflows.
- Improvements are tracked to demonstrate tangible security maturity.
This integration transforms your incident response playbook into a living, evolving strategy rather than a static compliance document.
Conclusion: NetWitness Red Team Services – Your Cybersecurity Defense Partner
Attackers are innovating every single day and the defenders also need to track up. Red Teaming does not just involve high-end testing, but a change in attitude between waves of inquiry of compliance, to waves of inquiry of readiness to real adversaries. Making Red Team drilling part of your incident response plan creates playbooks that lead to decisive actions when you are under attack.
NetWitness Red Team services do not just entail superficial testing. Our experts bring years of experience in offensive security and current-state attack simulation methods to provide the realistic and holistic evaluation. We point out vulnerabilities that might be exploited by attackers, enhance threat detection and response processes, and enhance your security posture.
Working with NetWitness incident response team will provide you with practical knowledge, quantifiable changes, and resiliency to changing threats. By investing in Red Team services, you are changing your cybersecurity strategy to be more of a damage control strategy rather than a threat prevention strategy from the perspective that will keep your organization prepared to take on whatever the next challenge is.
Frequently Asked Questions
1. What is a Red Team Exercise in Cybersecurity?
A Red Team Exercise in cybersecurity simulates real-world cyber-attacks to evaluate the effectiveness of an organization’s security measures and identify vulnerabilities. It involves mimicking the tactics, techniques, and procedures of actual adversaries to test both technical security controls and human responses under realistic attack conditions.
2. How does a Red Team Exercise differ from a Penetration Test?
Red team exercises provide comprehensive adversarial simulation that tests entire organizational security postures, while penetration tests focus primarily on technical vulnerability identification. Red team exercises evaluate human factors, communication protocols, and incident response capabilities alongside technical security controls, creating more realistic assessments of actual attack scenarios.
3. What are the key steps in conducting a Red Team Exercise?
Key steps include planning and scope definition, reconnaissance and intelligence gathering, exploitation of identified vulnerabilities, post-exploitation activities like lateral movement and privilege escalation, and comprehensive reporting with actionable remediation recommendations. Each phase mirrors real-world attack methodologies while maintaining controlled conditions.
4. What is the Red Team Incident Response?
Red Team Incident Response refers to the integration of Red Team operations into the incident response process. Rather than simply testing defenses, Red Teams actively simulate attacks to help organizations refine their detection, containment, and recovery strategies. This collaboration transforms incident response from a reactive process into a proactive discipline—preparing teams to handle real adversaries with precision and confidence.
5. What is the Role of the Red Team?
The Red Team’s role is to think and act like an attacker. They use adversarial tactics to breach defenses, exploit weaknesses, and test how well an organization detects, responds, and recovers from attacks. Their goal isn’t to cause damage but to uncover gaps, challenge assumptions, and strengthen both the technical and human elements of cybersecurity readiness.





