In 2025, enterprise risk is defined by relentless cyber threats – from ransomware to advanced persistent threats (APTs), reputational damage, loss of IP, and supply chain compromises. The attack surface has expanded into cloud platforms, remote workforce, and third-party integrations, making response speed as critical as prevention.
For CISOs and IT security leaders, the question isn’t whether an incident will occur but how effectively the organization can detect, contain, and recover. Every hour of downtime can cost upward of $250,000, while customer trust depends on transparency and response quality. Yet most incident response teams still spend hours manually triaging alerts instead of containing threats.
The difference between chaos and control often comes down to the right incident response tools – integrated, automated, and built on proven frameworks.
Setting the Foundation: Incident Response Frameworks for the Enterprise
Before selecting tools, enterprises need a structured foundation. Incident response frameworks such as NIST and SANS provide consistency, reduce decision fatigue, and define the incident response steps needed to contain a breach.
NIST Framework:
- Preparation – Plans, playbooks, and team training.
- Detection & Analysis – Monitoring, alerting, and prioritization.
- Containment, Eradication, Recovery – Limiting impact, removing threats, and restoring operations.
- Post-Incident Activity – Lessons learned and resilience improvements.
SANS Framework: Expands further with detailed identification and lessons-learned phases, making it particularly valuable in compliance-heavy industries.
These frameworks anchor the incident response process, ensuring technology investments fit within structured, repeatable workflows.

The Modern Incident Response Toolchain
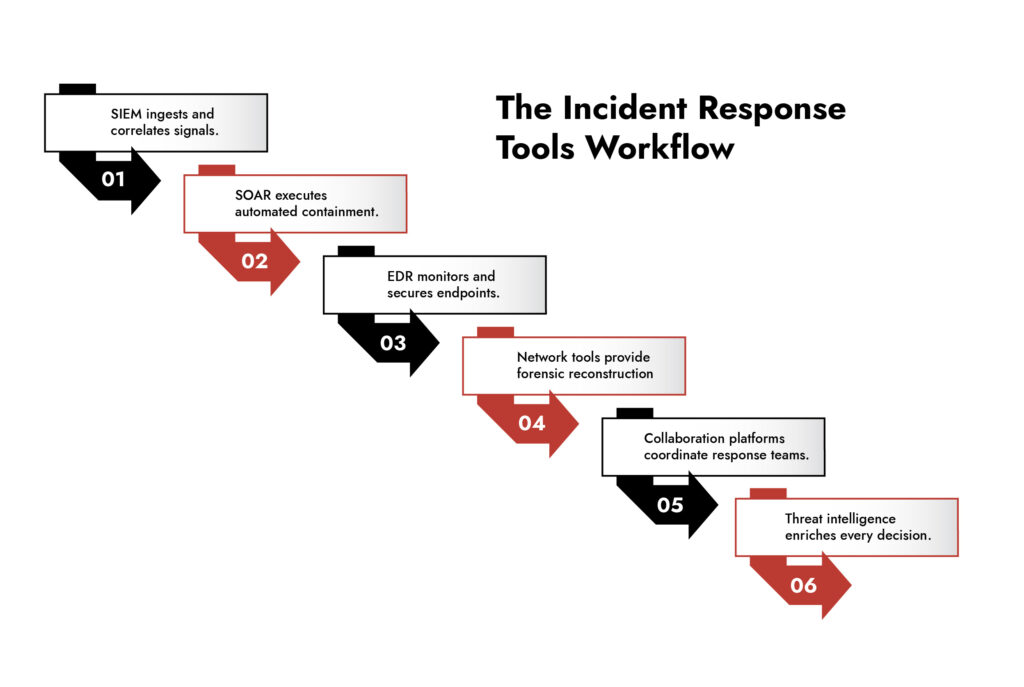
1. Security Information and Event Management (SIEM)
A SIEM centralizes log data from endpoints, networks, applications, and cloud systems. Advanced SIEMs use analytics and machine learning to detect anomalies, helping analysts prioritize threats.
- Enterprise Need: Hybrid-cloud compatibility, customizable dashboards, and integration with orchestration platforms.
- Value: Reduces alert fatigue by correlating and enriching events into actionable insights.
2. Security Orchestration, Automation, and Response (SOAR)
SOAR tools automate repetitive steps and orchestrate responses across systems. When integrated with SIEM, they execute playbooks that contain threats in minutes.
- Example: A phishing outbreak triggers automated workstation isolation, credential resets, and malicious domain blocks without analyst intervention.
- Advanced Capability: Dynamic playbooks that evolve with intelligence feeds.
3. Endpoint Detection and Response (EDR)
EDR provides continuous endpoint monitoring, flagging malicious processes and enabling quick isolation. With remote workforces expanding the attack surface, EDR has become essential.
- Key Features: Continuous real-time monitoring, advanced threat detection, automated response, and forensic investigation capabilities to protect endpoints against sophisticated cyberattacks.
- CISO Priority: Allows for assumed breach posture, enterprise reach, helps with encrypted traffic.
4. Network Traffic Analysis and Packet Capture
Network-level visibility is critical once attackers are inside. Packet capture tools help reconstruct attack chains, track lateral movement, and assess data exfiltration.
- Use Case: Better understand attacker behaviors even when they are subverting other tools and defenses or using LotL techniques.
- Enterprise Value: Forensic-grade evidence that satisfies regulators and supports legal action.
5. Incident Management and Collaboration Platforms
Technology alone will not contain an incident; teams need coordinated communication. Incident management platforms provide standardized workflows, audit trails, and real-time updates.
- Impact: Executives stay informed, legal teams access compliance documentation, and responders focus on remediation rather than reporting.
- Outcome: Aligned decision-making across departments and geographies.
6. Threat Intelligence Platforms
Real-time threat intelligence enriches investigations by providing context on indicators of compromise (IOCs) and attacker tactics.
- Benefit: Turns reactive response into proactive defense by identifying threats before they escalate.
- Result: Faster triage, reduced false positives, and smarter prioritization.
Putting It Together: How NetWitness Elevates Your Incident Response Plan
NetWitness Incident Response does not just plug into your stack; it empowers your incident response team at every critical stage with enterprise-grade capabilities:
- Unmatched Visibility: NetWitness captures comprehensive endpoint and network activity, providing the deep visibility needed for precise threat hunting and rapid incident response across hybrid environments.
- Unified Analytics Platform: All critical incident response data – across SIEM functionality, packet capture, endpoint telemetry, and threat intelligence – are accessible through a single console, streamlining analysis and accelerating containment decisions.
- Expert-Led Response: NetWitness combines advanced technology with seasoned incident response professionals who deploy within hours, delivering in-depth forensics, remediation guidance, and continuous improvement recommendations aligned with established incident response frameworks.
- Seamless Integration: The platform integrates with existing security tools and workflows, enhancing rather than replacing current investments while providing the advanced analytics needed for sophisticated threat detection.
NetWitness augments your incident response process at every phase, bridging capability gaps and accelerating response times, ensuring your organization is always prepared for evolving threats.
Conclusion: Incident Response as Competitive Advantage
The era when incident response was a technical afterthought is definitively over. In 2025, CISOs and security teams who invest in integrated, automated incident response tools grounded in robust frameworks are those who minimize business risk, reduce operational losses, and protect enterprise reputation in an increasingly hostile digital landscape.
Effective incident response has become a competitive differentiator, enabling organizations to maintain customer trust, meet regulatory requirements, and operate with confidence in digital-first business models. Assess your current incident response plan, verify your toolchain’s integration and automation capabilities, and consider how expert-led solutions like NetWitness can transform your security posture for tomorrow’s sophisticated threats. Explore NetWitness Incident Response.
よくある質問
1. How should CISOs decide which incident response tools to adopt?
Focus on proven integration capabilities, automation features, scalability for distributed environments, and robust compliance reporting, ensuring tools fit existing workflows and established incident response frameworks.
2. How do incident response tools operationalize my incident response plan?
They automate detection, standardize containment procedures, and streamline documentation, reducing human error and ensuring adherence to response best practices during high-stress incidents.
3. Are modern incident response tools effective against advanced persistent threats?
Yes, when properly integrated, they correlate endpoint, network, and intelligence data to detect, contain, and investigate even the most sophisticated adversaries and nation-state actors.
4. What ROI can large enterprises expect from incident response investments?
Measurable benefits include reduced incident dwell time, faster recovery, minimized regulatory exposure, and documented reductions in both direct breach costs and indirect business impact.
5. How does NetWitness continuously improve incident response readiness?
Through rapid deployment capabilities, advanced threat analytics, comprehensive coverage across attack vectors, and structured post-incident reviews, empowering teams with actionable insights to evolve their defenses proactively.



